CCNP350-401学习笔记(1-50题)
1、Which function does a fabric edge node perform in an SD-Access deployment?
A. Connects endpoints to the fabric and forwards their traffic.
B. Encapsulates end-user data traffic into LISP.
C. Connects the SD-Access fabric to another fabric or external Layer 3 networks.
D. Provides reachability between border nodes in the fabric underlay.
2、Refer to the exhibit.

Which privilege level is assigned to VTY users?
A. 1
B. 7
C. 13
D. 15
3、What is the difference between a RIB and a FIB?
A. The FIB is populated based on RIB content.
B. The RIB maintains a minor image of the FIB.
C. The RIB is used to make IP source prefix-based switching decisions.
D. The FIB is where all IP routing information is stored.
4、Which requirement for an Ansible-managed node is true?
A. It must have an SSH server running.
B. It must be a Linux server or a Cisco device.
C. It must support ad hoc commands.
D. It must have an Ansible Tower installed.
5、A client device fails to see the enterprise SSID, but other client devices are connected to it.
What is the cause of this issue?
A. The client has incorrect credentials stored for the configured broadcast SSID.
B. The hidden SSID was not manually configured on the client.
C. The broadcast SSID was not manually configured on the client.
D. The client has incorrect credentials stored for the configured hidden SSID.
6、Which two descriptions of FlexConnect mode for Cisco APs are true? (Choose two.)
A. APs that operate in FlexConnect mode cannot detect rogue APs
B. FlexConnect mode is used when the APs are set up in a mesh environment and used to bridge between each other.
C. FlexConnect mode is a feature that is designed to allow specified CAPWAP-enabled APs to exclude themselves from managing data traffic between clients and infrastructure.
D. When connected to the controller, FlexConnect APs can tunnel traffic back to the controller
E. FlexConnect mode is a wireless solution for branch office and remote office deployments
7、Which OSPF network types are compatible and allow communication through the two peering devices?
A. point-to-multipoint to nonbroadcast
B. broadcast to nonbroadcast
C. point-to-multipoint to broadcast
D. broadcast to point-to-point
8、Which NGFW mode blocks flows crossing the firewall?
A. tap
B. inline
C. passive
D. inline tap
9、Which statement about route targets is true when using VRF-Lite?
A. Route targets control the import and export of routes into a customer routing table.
B. When BGP is configured, route targets are transmitted as BGP standard communities.
C. Route targets allow customers to be assigned overlapping addresses.
D. Route targets uniquely identify the customer routing table.
10、How does Cisco TrustSec enable more flexible access controls for dynamic networking environments and data centers?
A. uses flexible NetFlow
B. assigns a VLAN to the endpoint
C. classifies traffic based on advanced application recognition
D. classifies traffic based on the contextual identity of the endpoint rather than its IP address
11、Refer to the exhibit

Which statement about the OPSF debug output is true?
A. The output displays OSPF hello messages which router R1 has sent or received on interface Fa0/1.
B. The output displays OSPF messages which router R1 has sent or received on all interfaces.
C. The output displays OSPF messages which router R1 has sent or received on interface Fa0/1.
D. The output displays OSPF hello and LSACK messages which router R1 has sent or received.
12、Which LISP infrastructure device provides connectivity between non-LISP sites and LISP sites by receiving non-LISP traffic with a LISP site destination?
A. PITR
B. map resolver
C. map server
D. PETR
13、Which two protocols are used with YANG data models? (Choose two.)
A. TLS
B. RESTCONF
C. SSH
D. NETCONF
E. HTTPS
14、Which HTTP status code is the correct response for a request with an incorrect password applied to a REST API session?
A. HTTP Status Code: 200
B. HTTP Status Code: 302
C. HTTP Status Code: 401
D. HTTP Status Code: 504
15、The login method is configured on the VTY lines of a router with these parameters.. The first method for authentication is TACACS
. If TACACS is unavailable, login is allowed without any provided credentials
Which configuration accomplishes this task? D

16、Which statement about multicast RPs is true?
A. RPs are required only when using protocol independent multicast dense mode.
B. RPs are required for protocol independent multicast sparse mode and dense mode.
C. By default, the RP is needed periodically to maintain sessions with sources and receivers.
D. By default, the RP is needed only to start new sessions with sources and receivers.
17、To increase total throughput and redundancy on the links between the wireless controller and switch, the customer enabled LAG on the wireless controller.
Which EtherChannel mode must be configured on the switch to allow the WLC to connect?
A. Active
B. Passive
C. On
D. Auto
18、Which feature does Cisco TrustSec use to provide scalable, secure communication throughout a network?
A. security group tag ACL assigned to each port on a switch
B. security group tag number assigned to each user on a switch
C. security group tag number assigned to each port on a network
D. security group tag ACL assigned to each router on a network
19、An engineer configures a WLAN with fast transition enabled. Some legacy clients fail to connect to this WLAN.
Which feature allows the legacy clients to connect while still allowing other clients to use fast transition based on their OUIs?
A. over the DS
B. 802.11k
C. adaptive R
D. 802.11v
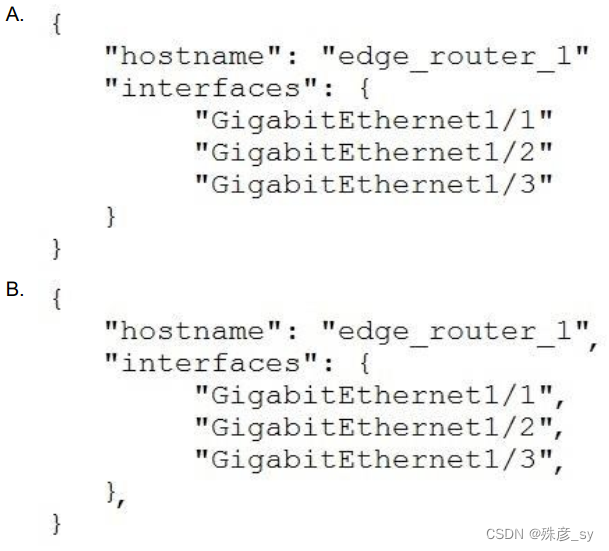
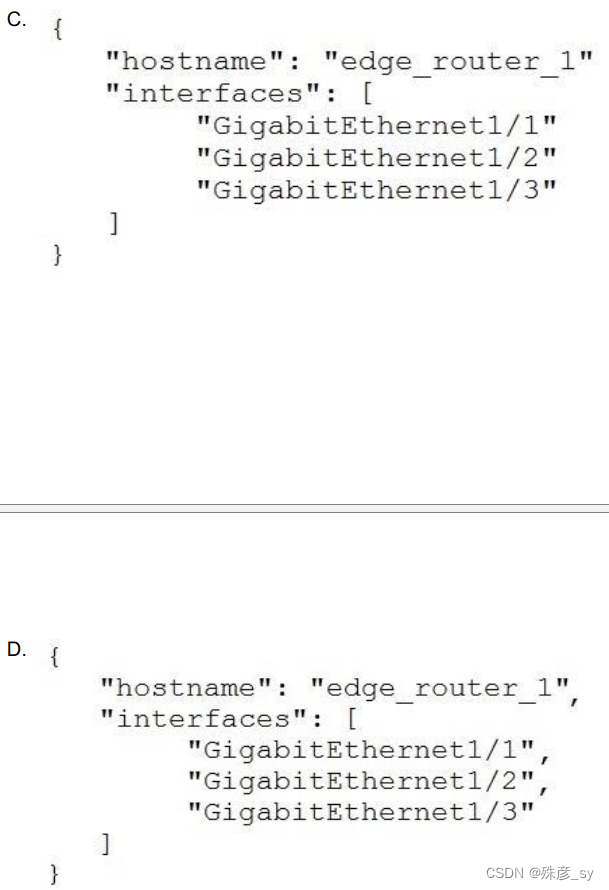
20、Which exhibit displays a valid JSON file? D
21、A network administrator is implementing a routing configuration change and enables routing debugs to track routing behavior during the change. The logging output on the terminal is interrupting the command typing process.
Which two actions can the network administrator take to minimize the possibility of typing commands incorrectly? (Choose two.)
A. Configure the logging synchronous global configuration command.
B. Configure the logging synchronous command under the vty.
C. Increase the number of lines on the screen using the terminal length command.
D. Configure the logging delimiter feature.
E. Press the TAB key to reprint the command in a new line
22、Which two pieces of information are necessary to compute SNR? (Choose two.)
A. transmit power
B. noise floor
C. EIRP
D. antenna gain
E. RSSI
23、Which statements are used for error handling in Python?
A. try/catch
B. catch/release
C. block/rescue
D. try/except
24、What are two benefits of virtualizing the server with the use of VMs in a data center environment? (Choose two.)
A. reduced rack space, power, and cooling requirements
B. smaller Layer 2 domain
C. increased security
D. speedy deployment
E. reduced IP and MAC address requirements
25、Which two steps are required for a complete Cisco DNA Center upgrade? (Choose two.)
A. automation backup
B. system update
C. golden image selection
D. proxy configuration
E. application updates
26、What is a benefit of data modeling languages like YANG?
A. They create more secure and efficient SNMP OIDs.
B. They provide a standardized data structure, which results in configuration scalability and consistency.
C. They enable programmers to change or write their own applications within the device operating system.
D. They make the CLI simpler and more efficient
27、Refer to the exhibit.
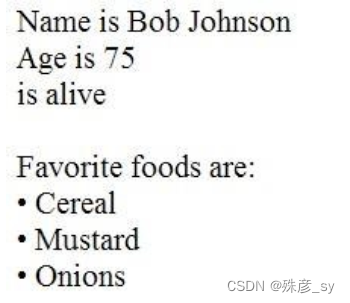
What is the JSON syntax that is formed from the data?
A. {Name: Bob Johnson, Age: 75, Alive: true, Favorite Foods: [Cereal, Mustard, Onions]}
B. {“Name”: “Bob Johnson”, “Age”: 75, “Alive”: true, “Favorite Foods”: [“Cereal”, “Mustard”, “Onions”]}
C. {‘Name’: ‘Bob Johnson’, ‘Age’: 75, ‘Alive’: True, ‘Favorite Foods’: ‘Cereal’, ‘Mustard’, ‘Onions’}
D. {“Name”: “Bob Johnson”, “Age”: Seventyfive, “Alive”: true, “Favorite Foods”: [“Cereal”, “Mustard”,
“Onions”]}
28、Based on this interface configuration, what is the expected state of OSPF adjacency?
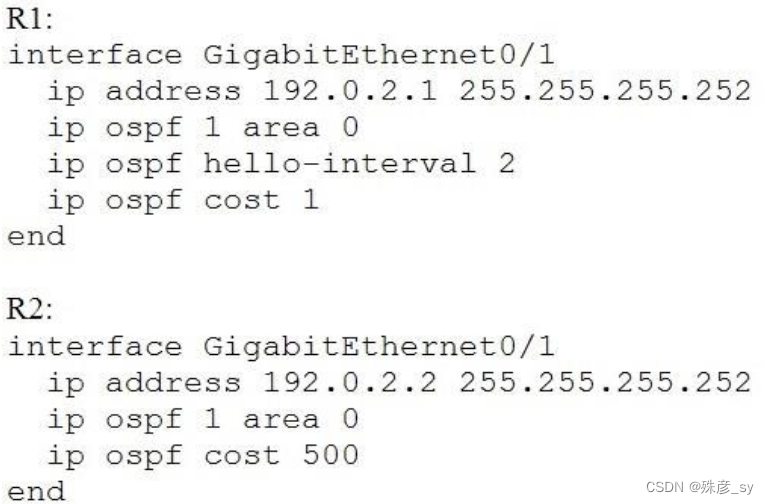
A. 2WAY/DROTHER on both routers
B. not established
C. FULL on both routers
D. FULL/BDR on R1 and FULL/BDR on R2
29、Refer to the exhibit.

Link1 is a copper connection and Link2 is a fiber connection. The fiber port must be the primary port for all forwarding. The output of the show spanning-tree command on SW2 shows that the fiber port is blocked by spanning tree. An engineer enters the spanning-tree port-priority 32 command on G0/1 on SW2, but the port remains blocked.
Which command should be entered on the ports that are connected to Link2 to resolve the issue?
A. Enter spanning-tree port-priority 4 on SW2.
B. Enter spanning-tree port-priority 32 on SW1.
C. Enter spanning-tree port-priority 224 on SW1.
D. Enter spanning-tree port-priority 64 on SW2.
30、Which JSON syntax is valid?
A. {“switch”: “name”: “dist1”, “interfaces”: [“gig1”, “gig2”, “gig3”]}
B. {/“switch/”: {/“name/”: “dist1”, /“interfaces/”: [“gig1”, “gig2”, “gig3”]}}
C. {“switch”: {“name”: “dist1”, “interfaces”: [“gig1”, “gig2”, “gig3”]}}
D. {‘switch’: (‘name’: ‘dist1’, ‘interfaces’: [‘gig1’, ‘gig2’, ‘gig3’])}
31、What are two common sources of interference for Wi-Fi networks? (Choose two.)
A. LED lights
B. radar
C. fire alarm
D. conventional oven
E. rogue AP
32、When using TLS for syslog, which configuration allows for secure and reliable transportation of messages to its default port?
A. logging host 10.2.3.4 vrf mgmt transport tcp port 514
B. logging host 10.2.3.4 vrf mgmt transport udp port 514
C. logging host 10.2.3.4 vrf mgmt transport tcp port 6514
D. logging host 10.2.3.4 vrf mgmt transport udp port 6514
33、Which behavior can be expected when the HSRP version is changed from 1 to 2?
A. No changes occur because the standby router is upgraded before the active router.
B. No changes occur because version 1 and 2 use the same virtual MAC OUI.
C. Each HSRP group reinitializes because the virtual MAC address has changed.
D. Each HSRP group reinitializes because the multicast address has changed.
34、Which protocol does REST API rely on to secure the communication channel?
A. HTTP
B. SSH
C. HTTPS
D. TCP
35、Refer to this output.
R1# *Feb 14 37:09:53.129: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/1, changed state to up
What is the logging severity level?
A. notification
B. emergency
C. critical
D. alert
36、Refer to the exhibit.
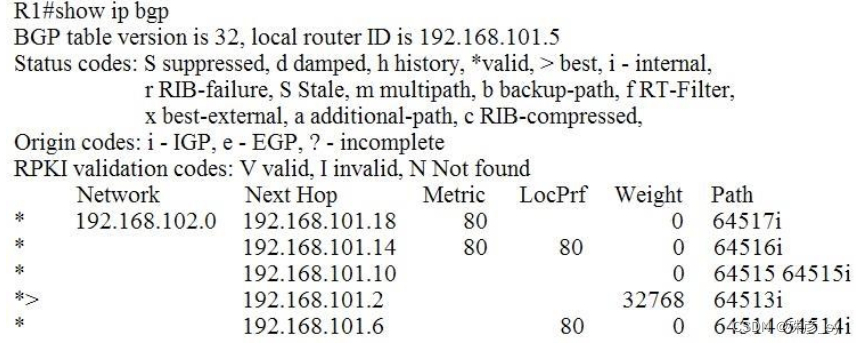
Which IP address becomes the active next hop for 192.168.102.0/24 when 192.168.101.2 fails?
A. 192.168.101.10
B. 192.168.101.14
C. 192.168.101.6
D. 192.168.101.18
37、Which PAgP mode combination prevents an EtherChannel from forming?
A. auto/desirable
B. desirable/desirable
C. desirable/auto
D. auto/auto
38、If a VRRP master router fails, which router is selected as the new master router?
A. router with the lowest priority
B. router with the highest priority
C. router with the highest loopback address
D. router with the lowest loopback address
39、Which QoS component alters a packet to change the way that traffic is treated in the network?
A. policing
B. classification
C. marking
D. shaping
40、Refer to the exhibit.
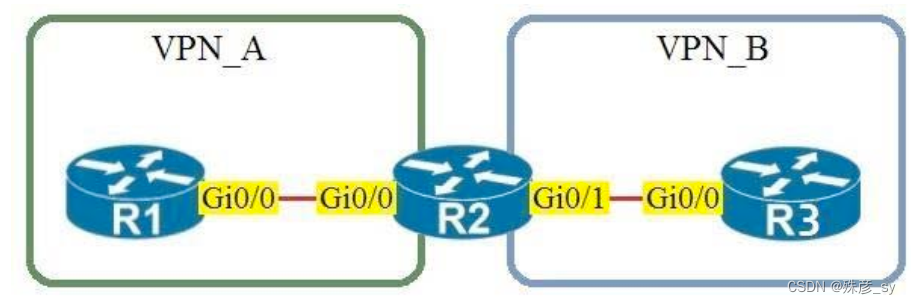
Assuming that R1 is a CE router, which VRF is assigned to Gi0/0 on R1?
A. default VRF
B. VRF VPN_A
C. VRF VPN_B
D. management VRF
41、Refer to the exhibit.
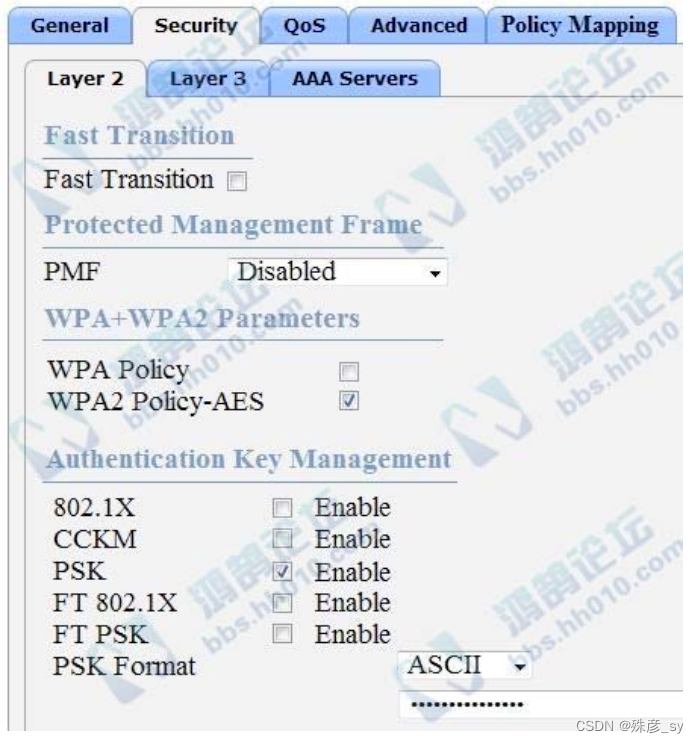
Based on the configuration in this WLAN security setting, which method can a client use to authenticate to
the network?
A. text string
B. username and password
C. RADIUS token
D. certificate
42、Which two mechanisms are available to secure NTP? (Choose two.)
A. IPsec
B. IP prefix list-based
C. encrypted authentication
D. TACACS-based authentication
E. IP access list-based
43、Which technology provides a secure communication channel for all traffic at Layer 2 of the OSI model?
A. SSL
B. Cisco TrustSec
C. MACsec
D. IPsec
44、Refer to the exhibit.
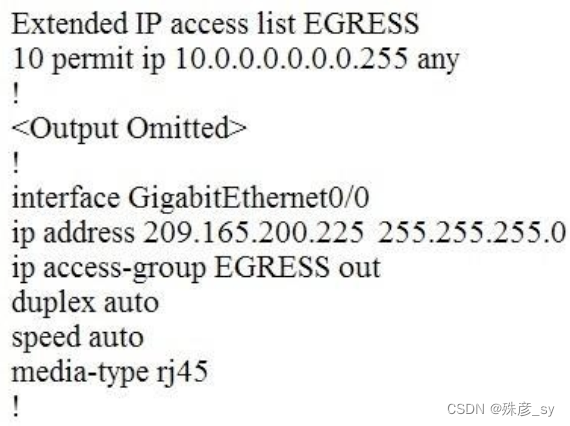
An engineer must block all traffic from a router to its directly connected subnet 209.165.200.0/24. The engineer applies access control list EGRESS in the outbound direction on the GigabitEthernet0/0 interface of the router. However, the router can still ping hosts on the 209.165.200.0/24 subnet.
Which explanation of this behavior is true?
A. Access control lists that are applied outbound to a router interface do not affect traffic that is sourced from the router.
B. After an access control list is applied to an interface, that interface must be shut and no shut for the access control list to take effect.
C. Only standard access control lists can block traffic from a source IP address.
D. The access control list must contain an explicit deny to block traffic from the router.
45、Which two methods are used by an AP that is trying to discover a wireless LAN controller? (Choose two.)
A. Cisco Discovery Protocol neighbor
B. querying other APs
C. DHCP Option 43
D. broadcasting on the local subnet
E. DNS lookup CISCO-DNA-PRIMARY.localdomain
46、Which IP SLA operation requires the IP SLA responder to be configured on the remote end?
A. UDP jitter
B. ICMP jitter
C. TCP connect
D. ICMP echo
47、Which statement explains why Type 1 hypervisor is considered more efficient than Type2 hypervisor?
A. Type 1 hypervisor is the only type of hypervisor that supports hardware acceleration techniques.
B. Type 1 hypervisor relies on the existing OS of the host machine to access CPU, memory, storage, and network resources.
C. Type 1 hypervisor runs directly on the physical hardware of the host machine without relying on the underlying OS.
D. Type 1 hypervisor enables other operating systems to run on it.
48、A client with IP address 209.165.201.25 must access a web server on port 80 at 209.165.200.225. To allow this traffic, an engineer must add a statement to an access control list that is applied in the inbound direction on the port connecting to the web servers.
Which statement allows this traffic?
A. permit tcp host 209.165.200.225 lt 80 host 209.165.201.25
B. permit tcp host 209.165.201.25 host 209.165.200.225 eq 80
C. permit tcp host 209.165.200.225 eq 80 host 209.165.201.25
D. permit tcp host 209.165.200.225 host 209.165.201.25 eq
49、In OSPF, which LSA type is responsible for pointing to the ASBR router?
A. type 1
B. type 2
C. type 3
D. type 4
50、Refer to the exhibit.

VLANs 50 and 60 exist on the trunk links between all switches. All access ports on SW3 are configured for VLAN 50 and SW1 is the VTP server.
Which command ensures that SW3 receives frames only from VLAN 50?
A. SW1(config)#vtp mode transparent
B. SW3(config)#vtp mode transparent
C. SW2(config)#vtp pruning
D. SW1(config)#vtp pruning
相关文章:

CCNP350-401学习笔记(1-50题)
1、Which function does a fabric edge node perform in an SD-Access deployment?A. Connects endpoints to the fabric and forwards their traffic. B. Encapsulates end-user data traffic into LISP. C. Connects the SD-Access fabric to another fabric or external La…...
基于微信小程序的新冠肺炎服务预约小程序
文末联系获取源码 开发语言:Java 框架:ssm JDK版本:JDK1.8 服务器:tomcat7 数据库:mysql 5.7/8.0 数据库工具:Navicat11 开发软件:eclipse/myeclipse/idea Maven包:Maven3.3.9 浏览器…...
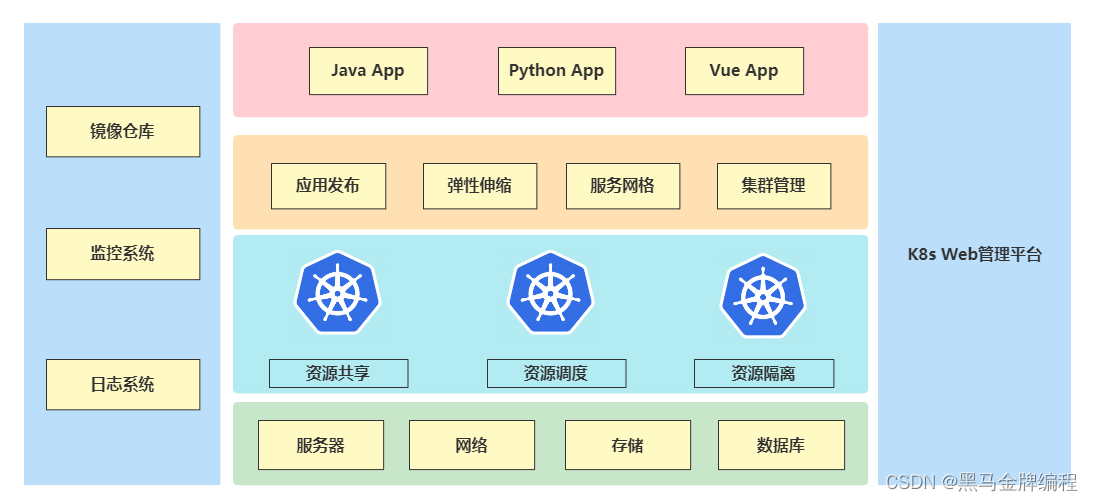
网站项目部署在k8s案例与Jenkins自动化发布项目(CI/CD)
在K8s平台部署项目流程 在K8s平台部署Java网站项目 制作镜像流程 第一步:制作镜像 使用镜像仓库(私有仓库、公共仓库): 1、配置可信任(如果仓库是HTTPS访问不用配置) # vi /etc/docker/daemon.json { "…...

网络原理 (1)
网络原理 文章目录1. 前言: 2. 应用层2.1 XML2.2 json2.3 protobuffer3. 传输层3.1 UDP3.1 TCP4. TCP 内部的工作机制 (重点)1. 确认应答 2.超时重传3. 连接管理3.1 建立联系 :三次握手3.2 断开连接 : 四次挥手4. 滑动窗口5. 流量…...

LeetCode-1139. 最大的以 1 为边界的正方形【前缀和,矩阵】
LeetCode-1139. 最大的以 1 为边界的正方形【前缀和,矩阵】题目描述:解题思路一:前缀和。前缀和来记录边长。解题思路二:0解题思路三:0题目描述: 给你一个由若干 0 和 1 组成的二维网格 grid,请…...
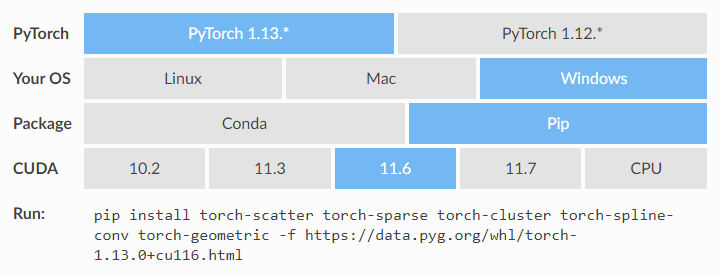
windows10/11,傻瓜式安装pytorch(gpu),在虚拟环境anaconda
安装anaconda地址 :Anaconda | The Worlds Most Popular Data Science Platform安装选项全默认点击next就行。查看支持cuda版本cmd命令行输入nvidia-smi。下图右上角显示11.6为支持的cuda版本。要是显示没有nvidia-smi命令。得安装nvidia驱动,一般情况都…...
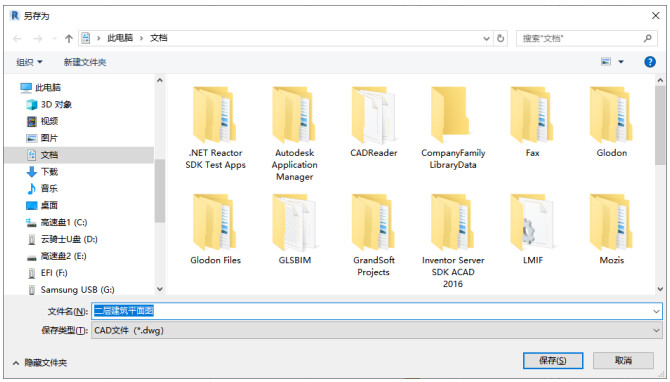
Revit导出PDF格式图纸流程及“批量导出图纸”
一、Revit导出PDF格式图纸流程 1、点击左上方“应用程序菜单”即“R”图标,进择“打印”选项。 2、在弹出的对话框中,需要设置图纸“打印范围”,选择“所选的视图/图纸选项”,点击“选择”,按钮,选择我们需…...
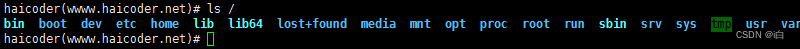
【自学Linux】 Linux文件目录结构
Linux文件目录结构 Linux文件目录结构教程 在 Linux 中,有一个很经典的说法,叫做一切皆文件,因此,我们在系统学习 Linux 之前,首先要了解 Linux 的文件目录结构。Linux 主要的目录有三大类,即根目录(/)&a…...

如何让APP在Google Play中成为特色
Google Play覆盖了 190 多个地区,数十亿的用户,所以开发者都会希望APP在应用商店中获得推荐位。 Google Play 上的精选热门应用类型:热门游戏或应用,畅销应用,安装量增长的应用,产生最多收入的应用。 那么…...

【C++】cin的处理过程
使用cin进行输入时,程序将输入视为一系列的字节,其中每个字节都被解释为字符编码。不管目标数据 类型是什么,输入一开始都是字符数据——文本数据。然后,cin对象负责将文本转换为其他类型。 为说明这是如何完成的,来看…...

读取Sentinel和Landsat 压缩包数据,直接进行波段重组、影像裁剪或者匀色镶嵌处理
波段重组在软件中查找:菜单栏-》影像基本处理-》波段处理-》波段重组,弹出如下对话框:根据对话框中的提示,输入需要处理的数据。注意:1、输入数据添加之后,需要点击其中任意一条数据,获取数据波…...

Yakit Web Fuzzer 终极能力强化:热加载 Fuzz
Background 在 HTB:BountyHunter 中,我们发现 Web Fuzzer 在使用中可以 “更强”,我们需要编写 Yak 脚本的事情,如果可以经过某些 Web Fuzzer 的优化,可以达到同样的效果。 在一个标签中,我们实现{{base6…...
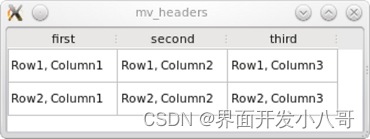
Qt新手入门指南 - 如何创建模型/视图(三)
每个UI开发人员都应该了解ModelView编程,本教程的目标是为大家提供一个简单易懂的介绍。Qt 是目前最先进、最完整的跨平台C开发工具。它不仅完全实现了一次编写,所有平台无差别运行,更提供了几乎所有开发过程中需要用到的工具。如今ÿ…...
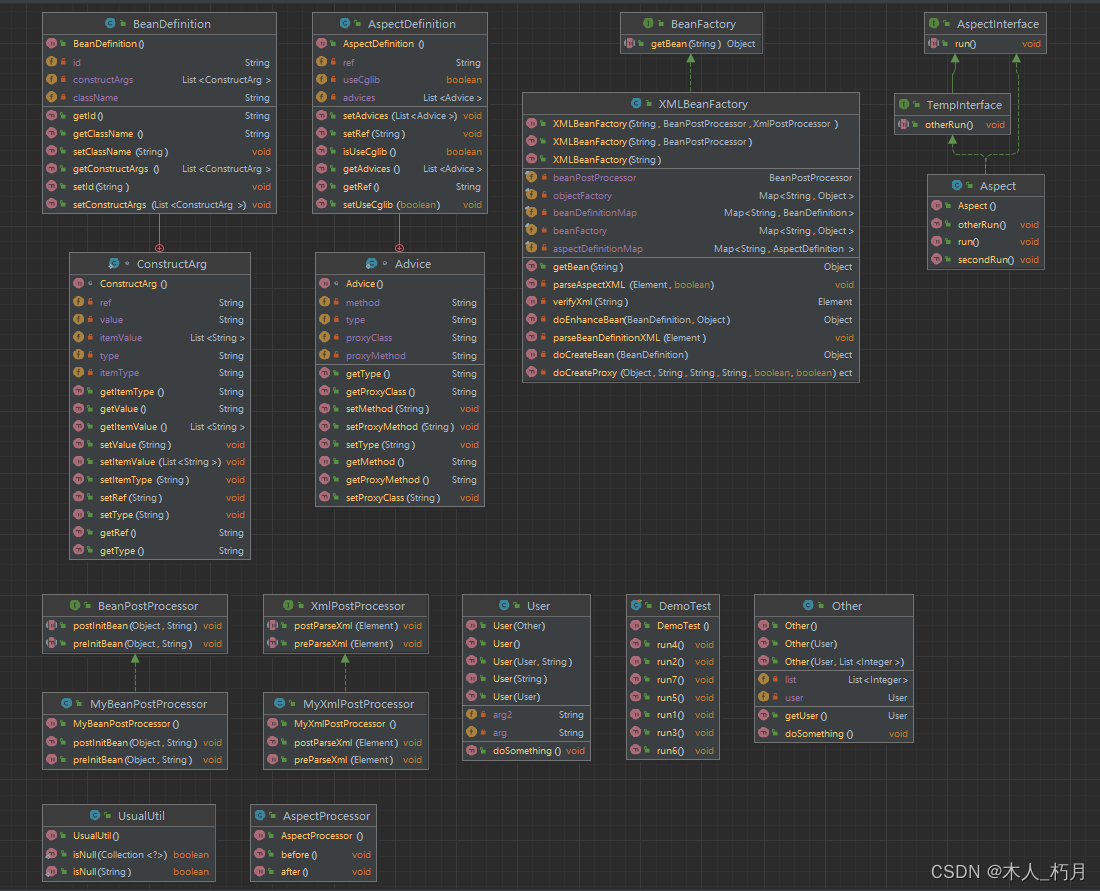
【Spring】手动实现简易AOP和IOC
前言 XML:通过Dom4j对XML进行解析和验证。 IOC:通过获取要创建对象的Class类型、构造函数后,通过反射来实现。 AOP:通过使用JDK动态代理和Cglib动态代理实现。 一、解析XML 1.1、解析bean标签 /*** 解析bean标签* param xmlBean…...
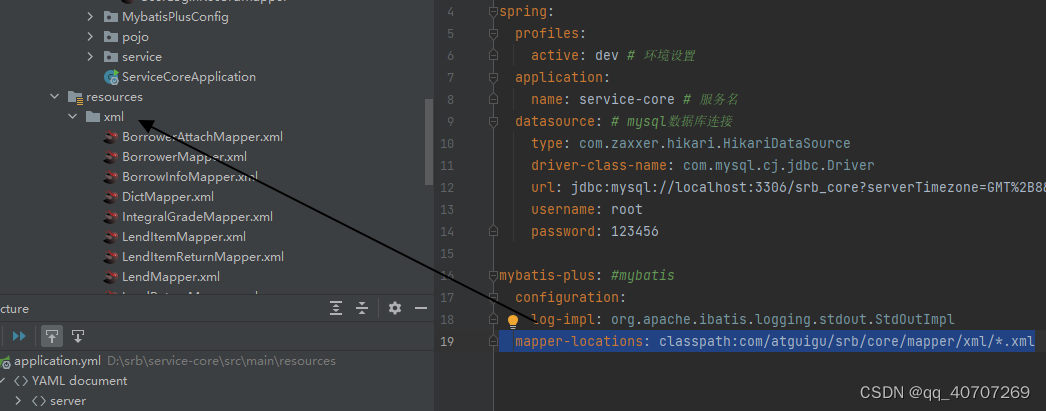
EasyExcel的使用
这里写目录标题先导入依赖最简单的写最简单的读項目开发中的一些操作xml一定要默認放先导入依赖 <dependencies><dependency><groupId>com.alibaba</groupId><artifactId>easyexcel</artifactId><version>2.1.7</version><…...
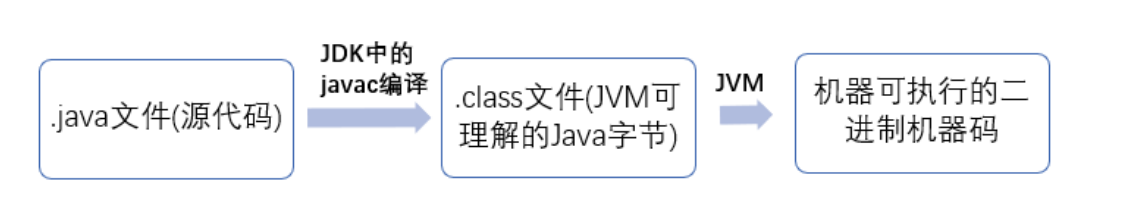
基础篇(-1)-java特点、JDK、JRE、JVM区别、字节码编译、跨平台、程序运行
文章目录1.Java的特点有哪些?2.JDK和JRE和JVM的区别3.Java为什么采用字节码编译?4.什么是跨平台?5.Java程序从源代码到运行需要三步?1.Java的特点有哪些? Java是一种编程语言,被特意设计用于互联网的分布式…...
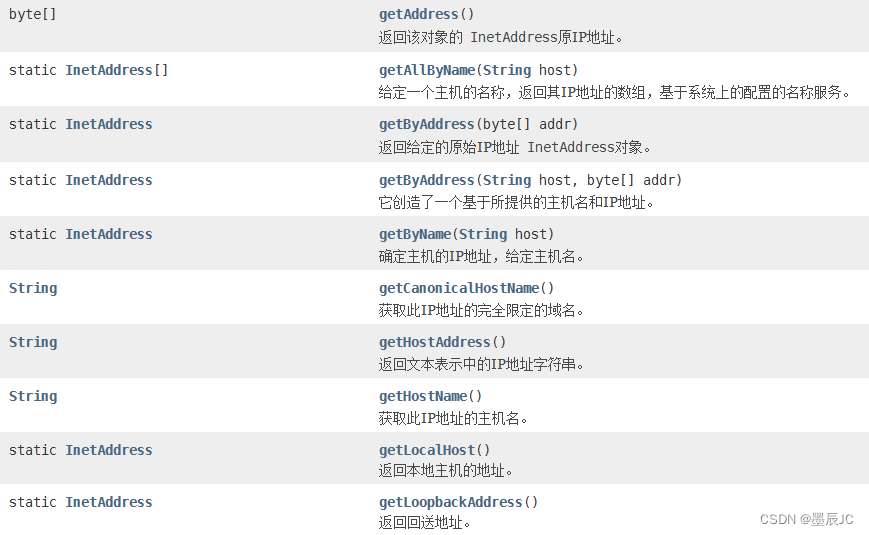
【网络编程】Java快速上手InetAddress类
概念 Java具有较好的网络编程模型/库,其中非常重要的一个API便是InetAddress。在Java.net 网络编程中中有许多类都使用到了InetAddress 这个类代表一个互联网协议(IP)地址。 IP地址是一个32(IPV4)位或128(…...

小小bat-day1-自动文件上传
前言:日常服务器备份文件或者生产设备等数据文件都统一保存至文件服务器,进行日志分析或者将生产文件CSV、图片等转存至数仓进行数据分析,尤其生产的部分数据是保存在个人电脑的PC端,数据杂,获取困难,手动整…...

2023年美赛D题公布
问题D:联合国可持续发展目标的优先次序背景联合国制定了17项可持续发展目标(SDGs)。实现这些目标最终会改善世界各地许多人的生活。这些目标并不是相互独立的。所以,在某些目标上的积极收获通常是有影响的(积极的或消极的,有时两者都有)。这种相互联系使…...
Gartner 再度预测2023低代码趋势,真的会赚钱吗?
2023年,从业者对低代码的发展充满了想象,人们认为,未来低代码的商业价值不可估量。 此话并非空穴来风。据Gartner的最新报告显示,到2023年,超过70%的企业将采用低代码作为他们发展战略的关键目标之一;到202…...
)
Java 语言特性(面试系列1)
一、面向对象编程 1. 封装(Encapsulation) 定义:将数据(属性)和操作数据的方法绑定在一起,通过访问控制符(private、protected、public)隐藏内部实现细节。示例: public …...
)
IGP(Interior Gateway Protocol,内部网关协议)
IGP(Interior Gateway Protocol,内部网关协议) 是一种用于在一个自治系统(AS)内部传递路由信息的路由协议,主要用于在一个组织或机构的内部网络中决定数据包的最佳路径。与用于自治系统之间通信的 EGP&…...

MVC 数据库
MVC 数据库 引言 在软件开发领域,Model-View-Controller(MVC)是一种流行的软件架构模式,它将应用程序分为三个核心组件:模型(Model)、视图(View)和控制器(Controller)。这种模式有助于提高代码的可维护性和可扩展性。本文将深入探讨MVC架构与数据库之间的关系,以…...

【论文笔记】若干矿井粉尘检测算法概述
总的来说,传统机器学习、传统机器学习与深度学习的结合、LSTM等算法所需要的数据集来源于矿井传感器测量的粉尘浓度,通过建立回归模型来预测未来矿井的粉尘浓度。传统机器学习算法性能易受数据中极端值的影响。YOLO等计算机视觉算法所需要的数据集来源于…...

服务器--宝塔命令
一、宝塔面板安装命令 ⚠️ 必须使用 root 用户 或 sudo 权限执行! sudo su - 1. CentOS 系统: yum install -y wget && wget -O install.sh http://download.bt.cn/install/install_6.0.sh && sh install.sh2. Ubuntu / Debian 系统…...
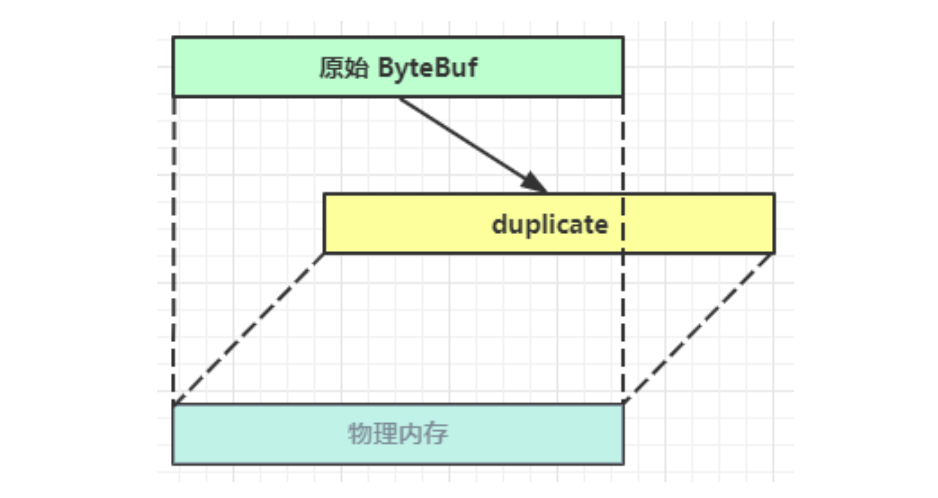
Netty从入门到进阶(二)
二、Netty入门 1. 概述 1.1 Netty是什么 Netty is an asynchronous event-driven network application framework for rapid development of maintainable high performance protocol servers & clients. Netty是一个异步的、基于事件驱动的网络应用框架,用于…...

SQL慢可能是触发了ring buffer
简介 最近在进行 postgresql 性能排查的时候,发现 PG 在某一个时间并行执行的 SQL 变得特别慢。最后通过监控监观察到并行发起得时间 buffers_alloc 就急速上升,且低水位伴随在整个慢 SQL,一直是 buferIO 的等待事件,此时也没有其他会话的争抢。SQL 虽然不是高效 SQL ,但…...

【Linux】Linux 系统默认的目录及作用说明
博主介绍:✌全网粉丝23W,CSDN博客专家、Java领域优质创作者,掘金/华为云/阿里云/InfoQ等平台优质作者、专注于Java技术领域✌ 技术范围:SpringBoot、SpringCloud、Vue、SSM、HTML、Nodejs、Python、MySQL、PostgreSQL、大数据、物…...

【JavaSE】多线程基础学习笔记
多线程基础 -线程相关概念 程序(Program) 是为完成特定任务、用某种语言编写的一组指令的集合简单的说:就是我们写的代码 进程 进程是指运行中的程序,比如我们使用QQ,就启动了一个进程,操作系统就会为该进程分配内存…...
R 语言科研绘图第 55 期 --- 网络图-聚类
在发表科研论文的过程中,科研绘图是必不可少的,一张好看的图形会是文章很大的加分项。 为了便于使用,本系列文章介绍的所有绘图都已收录到了 sciRplot 项目中,获取方式: R 语言科研绘图模板 --- sciRplothttps://mp.…...
