最新区块链论文速读--CCF A会议 ICSE 2024 共13篇 附pdf下载 (2/2)
Conference:International Conference on Software Engineering (ICSE)
CCF level:CCF A
Categories:Software Engineering/System Software/Programming Languages
Year:2024
Num:13
第1~7篇区块链文章请点击此处查看
8
Title:
GPTScan: Detecting Logic Vulnerabilities in Smart Contracts by Combining GPT with Program Analysis
GPTScan:结合GPT与程序分析检测智能合约逻辑漏洞
Authors:

Abstract:
Smart contracts are prone to various vulnerabilities, leading to substantial financial losses over time. Current analysis tools mainly target vulnerabilities with fixed control- or data-flow patterns, such as re-entrancy and integer overflow. However, a recent study on Web3 security bugs revealed that about 80% of these bugs cannot be audited by existing tools due to the lack of domain-specific property description and checking. Given recent advances in Large Language Models (LLMs), it is worth exploring how Generative Pre-training Transformer (GPT) could aid in detecting logic vulnerabilities. In this paper, we propose GPTScan, the first tool combining GPT with static analysis for smart contract logic vulnerability detection. Instead of relying solely on GPT to identify vulnerabilities, which can lead to high false positives and is limited by GPT's pre-trained knowledge, we utilize GPT as a versatile code understanding tool. By breaking down each logic vulnerability type into scenarios and properties, GPTScan matches candidate vulnerabilities with GPT. To enhance accuracy, GPTScan further instructs GPT to intelligently recognize key variables and statements, which are then validated by static confirmation. Evaluation on diverse datasets with around 400 contract projects and 3K Solidity files shows that GPTScan achieves high precision (over 90%) for token contracts and acceptable precision (57.14%) for large projects like Web3Bugs. It effectively detects ground-truth logic vulnerabilities with a recall of over 70%, including 9 new vulnerabilities missed by human auditors. GPTScan is fast and cost-effective, taking an average of 14.39 seconds and 0.01 USD to scan per thousand lines of Solidity code. Moreover, static confirmation helps GPTScan reduce two-thirds of false positives.
智能合约容易出现各种漏洞,久而久之会造成巨大的经济损失。当前的分析工具主要针对具有固定控制流或数据流模式的漏洞,例如重入和整数溢出。然而,最近一项关于 Web3 安全漏洞的研究表明,由于缺乏特定领域的属性描述和检查,大约 80% 的此类漏洞无法通过现有工具进行审计。鉴于大型语言模型 (LLM) 的最新进展,值得探索如何利用生成式预训练 Transformer (GPT) 来帮助检测逻辑漏洞。在本文中,我们提出了 GPTScan,这是第一个将 GPT 与静态分析相结合用于智能合约逻辑漏洞检测的工具。我们将 GPT 用作多功能代码理解工具,而不是仅仅依靠 GPT 来识别漏洞,因为这会导致很高的误报率,并且受到 GPT 预训练知识的限制。通过将每种逻辑漏洞类型分解为场景和属性,GPTScan 将候选漏洞与 GPT 进行匹配。为了提高准确率,GPTScan 进一步指示 GPT 智能识别关键变量和语句,然后通过静态确认进行验证。在包含约 400 个合约项目和 3K Solidity 文件的多种数据集上进行的评估表明,GPTScan 对代币合约的准确率高达 90% 以上,对 Web3Bugs 等大型项目的准确率也达到了可接受的水平(57.14%)。它有效地检测出了真实的逻辑漏洞,召回率超过 70%,包括 9 个人工审计人员遗漏的新漏洞。GPTScan 速度快、成本低,每千行 Solidity 代码平均扫描时间为 14.39 秒,成本为 0.01 美元。此外,静态确认可帮助 GPTScan 将误报率降低三分之二。
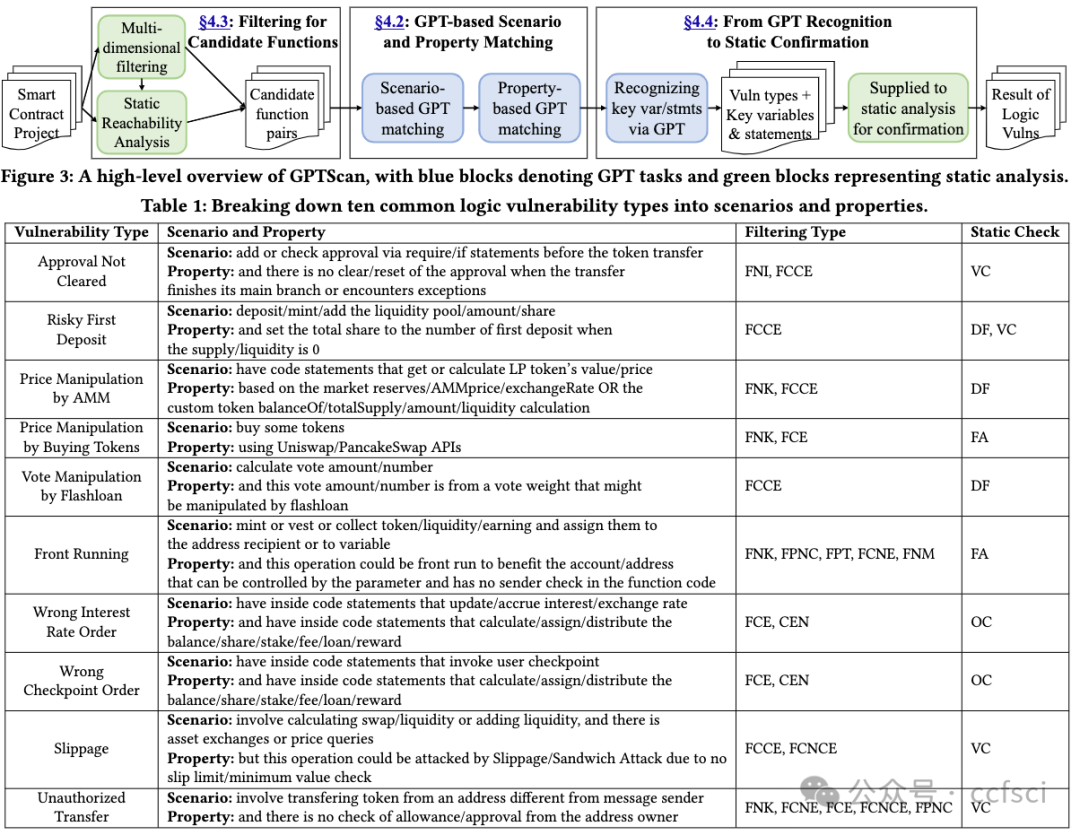
Filtering rules:
-
FNK: The Function Name should contain at least one Keyword.
-
FCE: The Function Content should contain at least one Expression.
-
FCNE: The Function Content should Not contain any Expression.
-
FCCE: The Function Content should contain at least one Combination of given Expressions.
-
FCNCE: The Function Content should Not contain any Combination of given Expressions.
-
FPT: The Function Parameters should match the given Types.
-
FPNC: The Function should be Public, and we will Not analyze it
-
with its Caller.
-
FNM: The Function should Not contain Modifiers that with access
-
control (e.g., onlyOwner).
-
CFN: The Callers of this Function will Not be analyzed.

Pdf link:
https://dl.acm.org/doi/10.1145/3597503.3639117
9
Title:
When Contracts Meets Crypto: Exploring Developers' Struggles with Ethereum Cryptographic APIs
当合约遇上xx货币:探索开发人员使用以太坊加密 API 的困境
Authors:

Key words:
Ethereum, Smart Contracts, Empirical Study, Cryptography, API Usability
以太坊、智能合约、实证研究、密码学、API 可用性
Abstract:
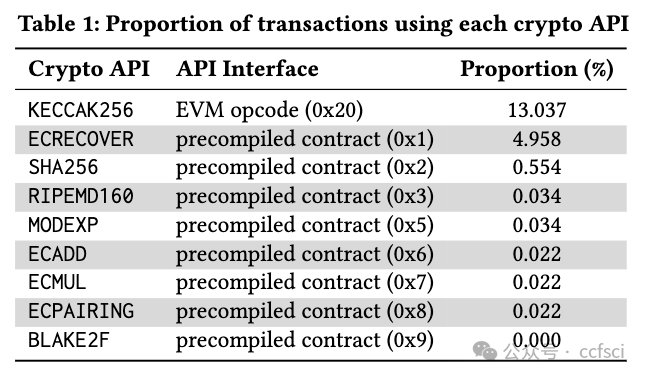
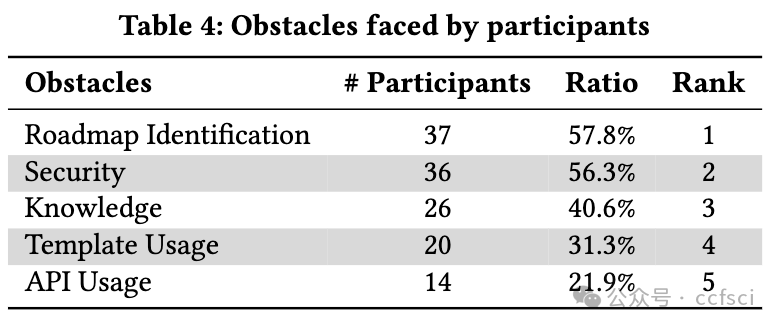
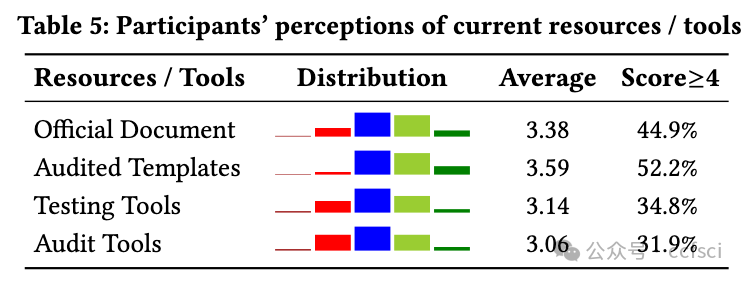
To empower smart contracts with the promising capabilities of cryptography, Ethereum officially introduced a set of cryptographic APIs that facilitate basic cryptographic operations within smart contracts, such as elliptic curve operations. However, since developers are not necessarily cryptography experts, requiring them to directly interact with these basic APIs has caused real-world security issues and potential usability challenges. To guide future research and solutions to these challenges, we conduct the first empirical study on Ethereum cryptographic practices. Through the analysis of 91,484,856 Ethereum transactions, 500 crypto-related contracts, and 483 StackExchange posts, we provide the first in-depth look at cryptographic tasks developers need to accomplish and identify five categories of obstacles they encounter. Furthermore, we conduct an online survey with 78 smart contract practitioners to explore their perspectives on these obstacles and elicit the underlying reasons. We find that more than half of practitioners face more challenges in cryptographic tasks compared to general business logic in smart contracts. Their feedback highlights the gap between low-level cryptographic APIs and high-level tasks they need to accomplish, emphasizing the need for improved cryptographic APIs, task-based templates, and effective assistance tools. Based on these findings, we provide practical implications for further improvements and outline future research directions.
为了将密码学的潜力发挥到极致,以太坊官方推出了一套密码学 API,用于在智能合约中实现基本的密码学操作,例如椭圆曲线操作。然而,由于开发人员不一定是密码学专家,要求他们直接与这些基本 API 交互已经导致了现实世界的安全问题和潜在的可用性挑战。为了指导未来的研究和应对这些挑战的解决方案,我们对以太坊密码学实践进行了首次实证研究。通过分析 91,484,856 笔以太坊交易、500 份加密相关合约和 483 篇 StackExchange 帖子,我们首次深入研究了开发人员需要完成的密码学任务,并确定了他们遇到的五类障碍。此外,我们对 78 位智能合约从业者进行了在线调查,以了解他们对这些障碍的看法并找出其根本原因。我们发现,超过一半的从业者在密码学任务中面临的挑战比智能合约中的一般业务逻辑更大。他们的反馈凸显了低级加密 API 与它们需要完成的高级任务之间的差距,强调需要改进加密 API、基于任务的模板和有效的辅助工具。基于这些发现,我们为进一步改进提供了实际意义,并概述了未来的研究方向。


Pdf link:
https://dl.acm.org/doi/10.1145/3597503.3639131
10
Title:
PrettySmart: Detecting Permission Re-delegation Vulnerability for Token Behaviors in Smart Contracts
PrettySmart:检测智能合约中代币行为的权限重新委托漏洞
Authors:

Key words:
Smart Contract, Permission Control, Vulnerability Detection
智能合约、权限控制、漏洞检测
Abstract:
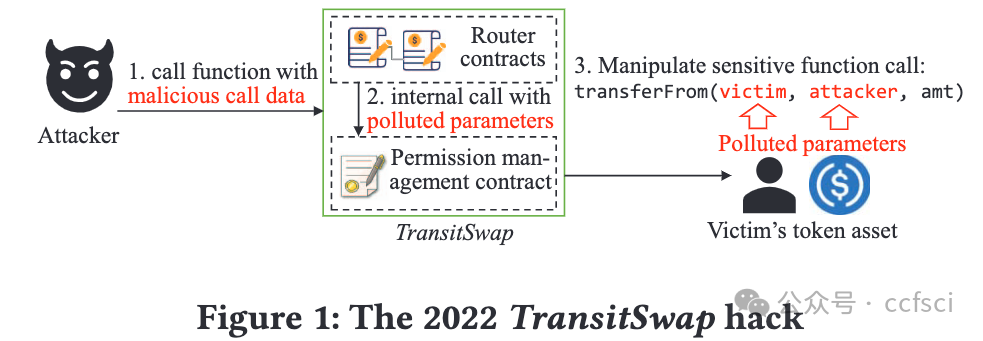
As an essential component in Ethereum and other blockchains, token assets have been interacted with by diverse smart contracts. Effective permission policies of smart contracts must prevent token assets from being manipulated by unauthorized adversaries. Recent efforts have studied the accessibility of privileged functions or state variables to unauthorized users. However, little attention is paid to how publicly accessible functions of smart contracts can be manipulated by adversaries to steal users' digital assets. This attack is mainly caused by the permission re-delegation (PRD) vulnerability. In this work, we propose PrettySmart, a bytecode-level Permission re-delegation vulnerability detector for Smart contracts. Our study begins with an empirical study on 0.43 million open-source smart contracts, revealing that five types of widely-used permission constraints dominate 98% of the studied contracts. Accordingly, we propose a mechanism to infer these permission constraints, as well as an algorithm to identify constraints that can be bypassed by unauthorized adversaries. Based on the identification of permission constraints, we propose to detect whether adversaries could manipulate the privileged token management functionalities of smart contracts. The experimental results on real-world datasets demonstrate the effectiveness of the proposed PrettySmart, which achieves the highest precision score and detects 118 new PRD vulnerabilities.
作为以太坊和其他区块链的重要组成部分,代币资产与各种智能合约都有交互。智能合约的有效权限策略必须防止代币资产被未经授权的对手操纵。最近的研究已经研究了特权函数或状态变量对未经授权用户的可访问性。然而,很少有人关注对手如何操纵智能合约的公开可访问函数来窃取用户的数字资产。这种攻击主要是由权限重新委托 (PRD) 漏洞引起的。在这项工作中,我们提出了 PrettySmart,一种用于智能合约的字节码级权限重新委托漏洞检测器。我们的研究首先对 43 万个开源智能合约进行了实证研究,结果表明,五种广泛使用的权限约束类型占据了所研究合约的 98%。因此,我们提出了一种推断这些权限约束的机制,以及一种识别可被未经授权的对手绕过的约束的算法。基于对权限约束的识别,我们建议检测对手是否可以操纵智能合约的特权代币管理功能。在真实数据集上的实验结果证明了所提出的 PrettySmart 的有效性,它获得了最高的精度分数并检测到 118 个新的 PRD 漏洞。
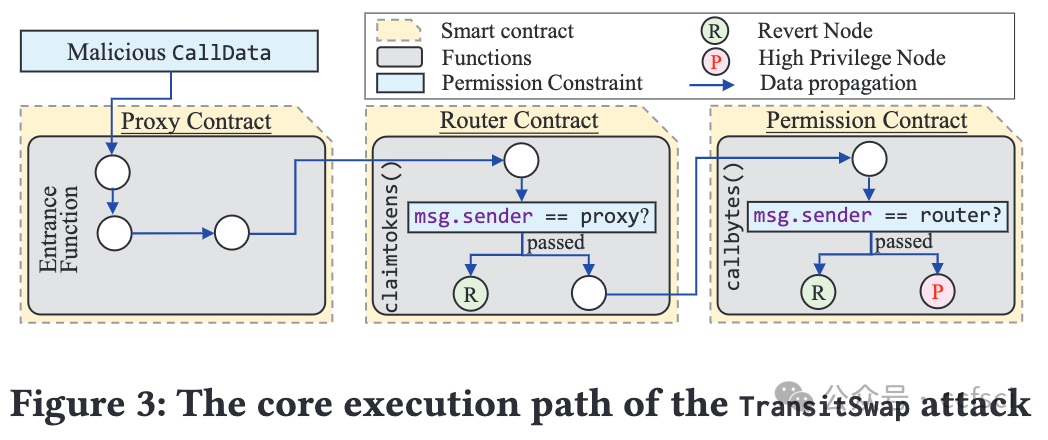

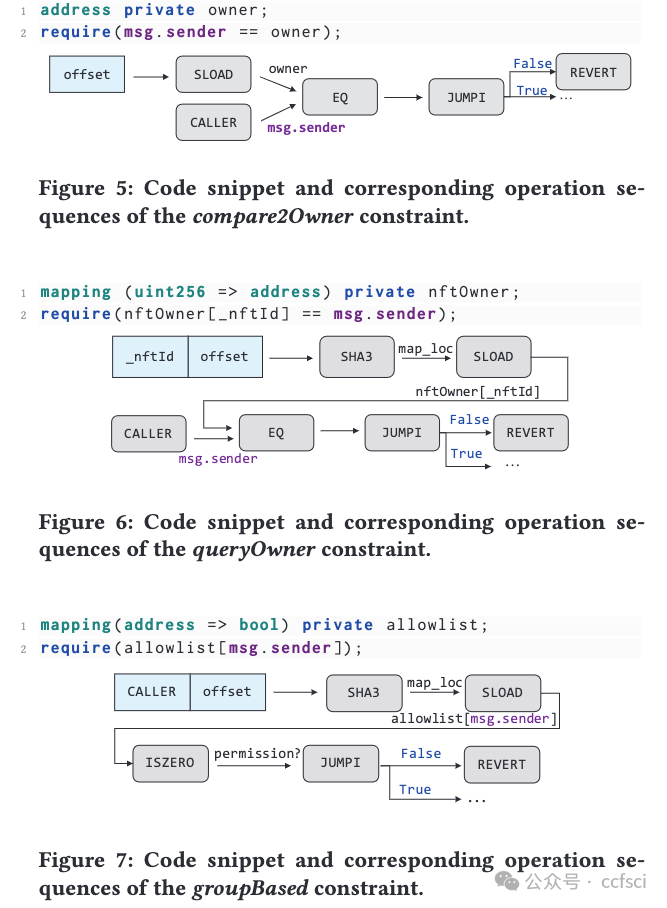
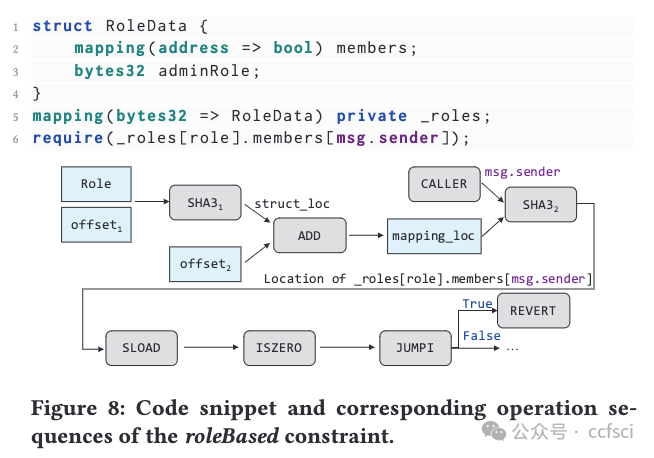

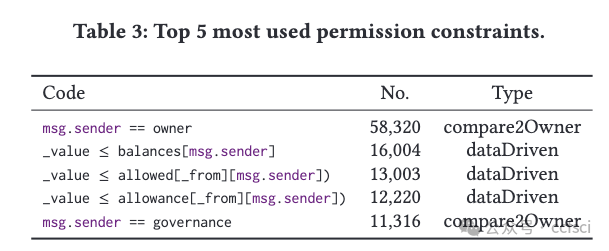

Pdf link:
https://dl.acm.org/doi/10.1145/3597503.3639140
11
Title:
SCVHunter: Smart Contract Vulnerability Detection Based on Heterogeneous Graph Attention Network
SCVHunter:基于异构图注意力网络的智能合约漏洞检测
Authors:

Key words:
Blockchain, Smart Contract, Vulnerability Detection
区块链、智能合约、漏洞检测
Abstract:
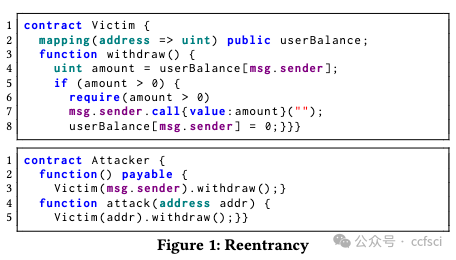
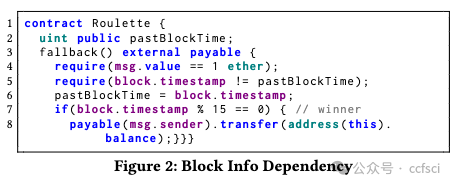
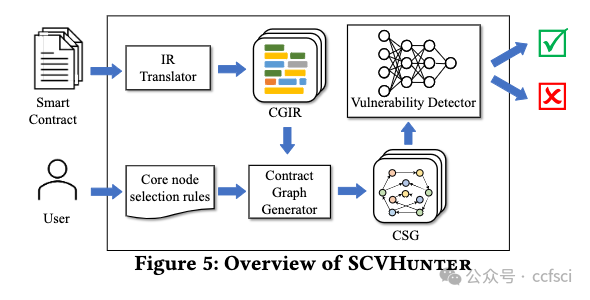
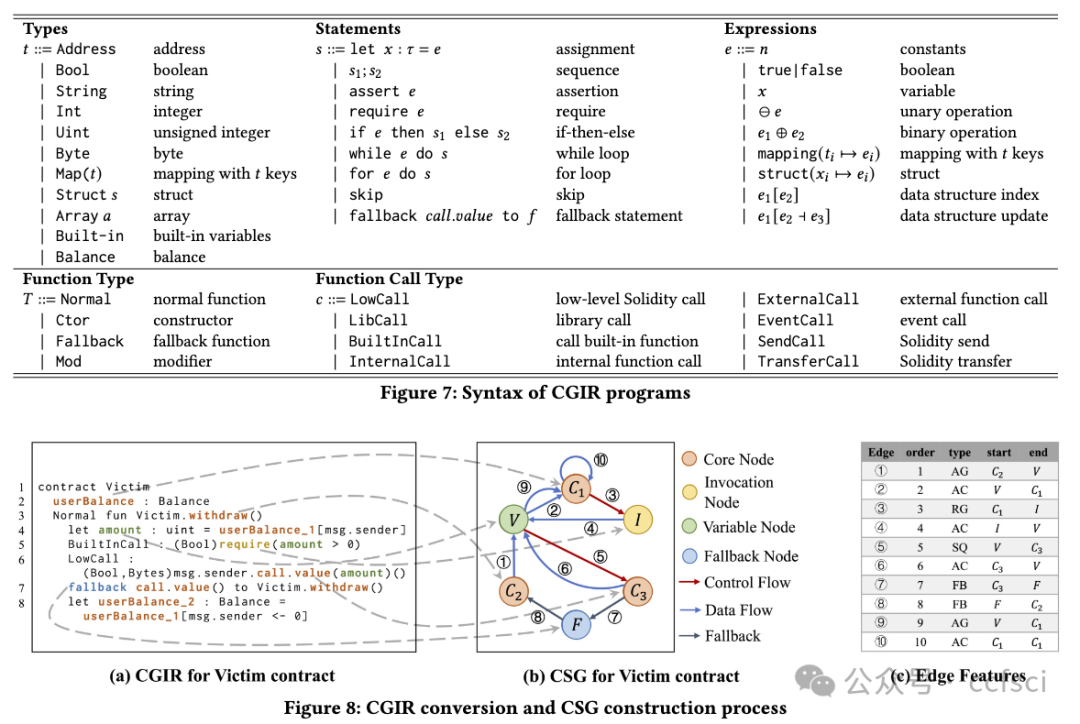
Smart contracts are integral to blockchain's growth, but their vulnerabilities pose a significant threat. Traditional vulnerability detection methods rely heavily on expert-defined complex rules that are labor-intensive and dificult to adapt to the explosive expansion of smart contracts. Some recent studies of neural network-based vulnerability detection also have room for improvement. Therefore, we propose SCVHunter, an extensible framework for smart contract vulnerability detection. Specifically, SCVHunter designs a heterogeneous semantic graph construction phase based on intermediate representations and a vulnerability detection phase based on a heterogeneous graph attention network for smart contracts. In particular, SCVHunter allows users to freely point out more important nodes in the graph, leveraging expert knowledge in a simpler way to aid the automatic capture of more information related to vulnerabilities. We tested SCVHunter on reentrancy, block info dependency, nested call, and transaction state dependency vulnerabilities. Results show remarkable performance, with accuracies of 93.72%, 91.07%, 85.41%, and 87.37% for these vulnerabilities, surpassing previous methods.
智能合约是区块链发展不可或缺的一部分,但其漏洞却带来了巨大的威胁。传统的漏洞检测方法严重依赖专家定义的复杂规则,这些规则需要大量人力,难以适应智能合约的爆炸式增长。近期一些基于神经网络的漏洞检测研究也存在改进空间。因此,我们提出了一个可扩展的智能合约漏洞检测框架SCVHunter。具体来说,SCVHunter为智能合约设计了一个基于中间表示的异构语义图构建阶段和一个基于异构图注意力网络的漏洞检测阶段。特别地,SCVHunter允许用户自由地指出图中更重要的节点,以更简单的方式利用专家知识来帮助自动捕获更多与漏洞相关的信息。我们在可重入、块信息依赖、嵌套调用和交易状态依赖漏洞上测试了SCVHunter。结果显示其性能卓越,对这些漏洞的准确率分别为93.72%、91.07%、85.41%和87.37%,超越了之前的方法。



Pdf link:
https://dl.acm.org/doi/10.1145/3597503.3639213
12
Title:
Safeguarding DeFi Smart Contracts against Oracle Deviations
保护 DeFi 智能合约免受预言机偏差的影响
Authors:

Key words:
Blockchain, Decentralized Finance, Smart Contracts, Oracle Deviation, Static Program Analysis, Code Summary, Parameter Optimization
区块链、去中心化金融、智能合约、预言机偏差、静态程序分析、代码汇总、参数优化
Abstract:
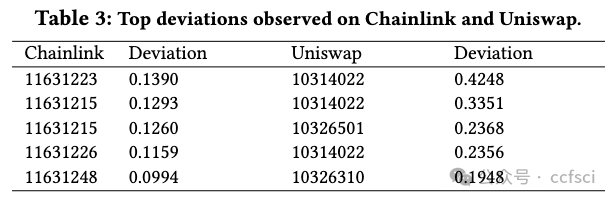
This paper presents OVer, a framework designed to automatically analyze the behavior of decentralized finance (DeFi) protocols when subjected to a "skewed" oracle input. OVer firstly performs symbolic analysis on the given contract and constructs a model of constraints. Then, the framework leverages an SMT solver to identify parameters that allow its secure operation. Furthermore, guard statements may be generated for smart contracts that may use the oracle values, thus effectively preventing oracle manipulation attacks. Empirical results show that OVer can successfully analyze all 10 benchmarks collected, which encompass a diverse range of DeFi protocols. Additionally, this paper illustrates that current parameters utilized in the majority of benchmarks are inadequate to ensure safety when confronted with significant oracle deviations. It shows that existing ad-hoc control mechanisms such as introducing delays are often in-sufficient or even detrimental to protect the DeFi protocols against the oracle deviation in the real-world.
本文介绍了一个框架,OVer,用于自动分析去中心化金融 (DeFi) 协议在受到“倾斜”预言机输入时的行为。OVer 首先对给定的合约进行符号分析,并构建约束模型。然后,该框架利用 SMT 求解器来识别允许其安全运行的参数。此外,可以为可能使用预言机值的智能合约生成保护语句,从而有效防止预言机操纵攻击。实证结果表明,OVer 可以成功分析收集到的所有 10 个基准,这些基准涵盖了多种 DeFi 协议。此外,本文还指出,大多数基准中使用的当前参数不足以确保在面临重大预言机偏差时的安全。它表明,现有的临时控制机制(例如引入延迟)通常不足以甚至有害于保护 DeFi 协议免受现实世界中的预言机偏差的影响。
Pdf link:
https://dl.acm.org/doi/10.1145/3597503.3639225
13
Title:
Verifying Declarative Smart Contracts
验证声明式智能合约
Authors:

Key words:
permissioned blockchains, throughput, latency
许可区块链、吞吐量、延迟
Abstract:
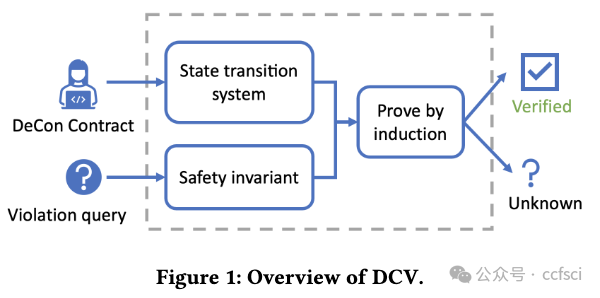
Smart contracts manage a large number of digital assets nowadays. Bugs in these contracts have led to significant financial loss. Verifying the correctness of smart contracts is, therefore, an important task. This paper presents an automated safety verification tool, DCV, that targets declarative smart contracts written in De-Con, a logic-based domain-specific language for smart contract implementation and specification. DCV proves safety properties by mathematical induction and can automatically infer inductive invariants using heuristic patterns, without annotations from the developer. Our evaluation on 23 benchmark contracts shows that DCV is effective in verifying smart contracts adapted from public repositories, and can verify contracts not supported by other tools. Furthermore, DCV significantly outperforms baseline tools in verification time.
如今,智能合约管理着大量数字资产。这些合约中的错误已导致重大的财务损失。因此,验证智能合约的正确性是一项重要任务。本文介绍了一种自动化安全验证工具 DCV,该工具针对用 De-Con 编写的声明式智能合约,De-Con 是一种用于智能合约实现和规范的基于逻辑的领域特定语言。DCV 通过数学归纳法证明安全属性,并可以使用启发式模式自动推断归纳不变量,而无需开发人员的注释。我们对 23 个基准合约的评估表明,DCV 可有效验证从公共存储库改编的智能合约,并可验证其他工具不支持的合约。此外,DCV 在验证时间方面明显优于基线工具。

Pdf link:
https://dl.acm.org/doi/10.1145/3597503.3639203

关注我们,持续接收区块链最新论文
洞察区块链技术发展趋势
Follow us to keep receiving the latest blockchain papers
Insight into Blockchain Technology Trends
相关文章:

最新区块链论文速读--CCF A会议 ICSE 2024 共13篇 附pdf下载 (2/2)
Conference:International Conference on Software Engineering (ICSE) CCF level:CCF A Categories:Software Engineering/System Software/Programming Languages Year:2024 Num:13 第1~7篇区块链文章请点击此处…...
C++ 34 之 单例模式
#include <iostream> #include <string.h> using namespace std;class King{// 公共的函数,为了让外部可以获取唯一的实例 public:// getInstance 获取单例 约定俗成static King* getInstance(){return true_king;}private: // 私有化// 构造函数设置为…...

SAP BW:传输转换源系统-源系统映射关系
最近有朋友再问问我源系统映射关系怎么配置,想着写一个怕以后忘了。 简单说下这个是干嘛的,其实就是配置一个源系统到目标系统的一个映射,这样传输的时候才知道传过来的数据源要变成目标系统的数据源。 比如下图,在开发环境&…...
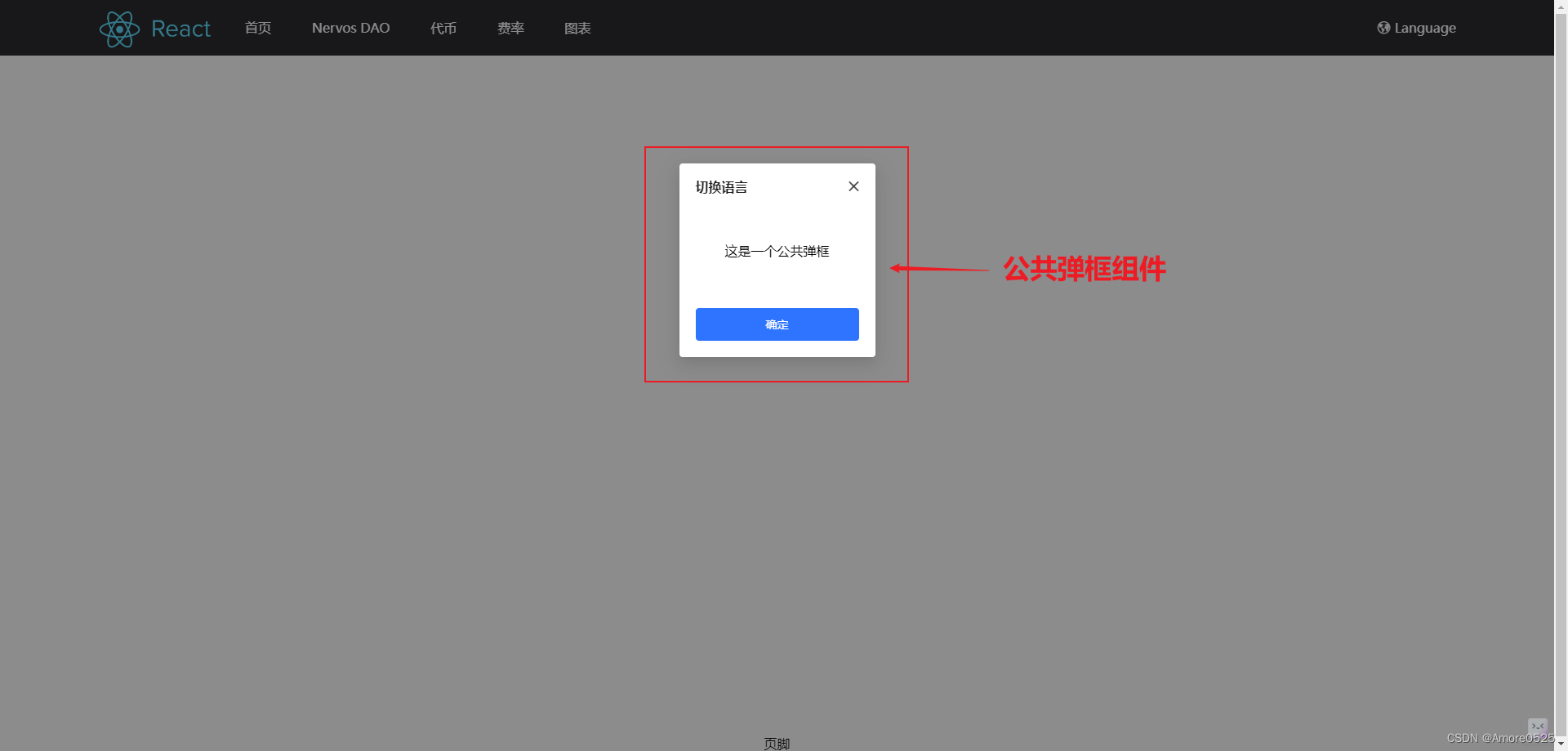
React+TS前台项目实战(九)-- 全局常用组件弹窗Dialog封装
文章目录 前言Dialog公共弹窗组件1. 功能分析2. 代码详细注释3. 使用方式4. 效果展示 总结 前言 今天这篇主要讲全局公共弹窗Dialog组件封装,将用到上篇封装的模态框Modal组件。有时在前台项目中,偶尔要用到一两个常用的组件,如 弹窗&#x…...

利用视觉分析技术提升水面漂浮物、水面垃圾检测效率
随着城市化进程的加速和工业化的发展,水体污染问题日益严重,水面漂浮物成为水环境治理的一大难题。传统的水面漂浮物检测方法主要依赖人工巡查和简单的传感器检测,存在着效率低、准确率不高等问题。为了提升水面漂浮物检测的效率和准确性&…...

NFT 智能合约实战-快速开始(1)NFT发展历史 | NFT合约标准(ERC-721、ERC-1155和ERC-998)介绍
文章目录 NFT 智能合约实战-快速开始(1)NFT发展历史国内NFT市场国内NFT合规性如何获得NFT?如何查询NFT信息?在 OpenSea 上查看我们的 NFT什么是ERC721NFT合约标准ERC-721、ERC-1155和ERC-998 对比ERC721IERC721.sol 接口内容关于合约需要接收 ERC721 资产 onERC721Received…...

Linux知识整理说明
最近学校Linux课程刚刚结课,但还是有其他课程在继续。 所以接下来我会抽时间,根据笔记以及网络资料,整理和Linux相关的知识文档,各位可以后续留意. 完整的章目录我会先发出来,后续补充完整。 所有的内容会在 下周三(6…...

诊所管理系统哪家会好一点
随着医疗行业的快速发展和信息化进程的加速,诊所作为医疗服务的重要基层单位,其运营管理效率与服务质量的提升愈发依赖于现代化的管理工具。诊所管理系统应运而生,旨在通过集成化、智能化的技术手段,帮助诊所实现诊疗流程优化、资…...

前端根据权限生成三级路由
三级菜单和后端返回数组对比获取有权限的路由 数组: //后端返回的数组 const arr1 [sale.management, sale.order, sale.detail]; //前端路由 const arr2 [{path: "/sale-manage",redirect: "/sale-manage/sale-order/sale-list",name: sale…...

Databricks超10亿美元收购Tabular;Zilliz 推出 Milvus Lite ; 腾讯云支持Redis 7.0
重要更新 1. Databricks超10亿美元收购Tabular,Databricks将增强 Delta Lake 和 Iceberg 社区合作,以实现 Lakehouse 底层格式的开放与兼容([1] [2])。 2. Zilliz 推出 Milvus Lite 轻量级向量数据库,支持本地运行;Milvus Lite 复…...

算法day29
第一题 695. 岛屿的最大面积 本题解法:采用bfs的算法; 本题使用象限数组的遍历方法和定义布尔数组vis来遍历每一个元素的上下左右元素,防治被遍历的元素被二次遍历; 本题具体分析如上题故事,但是由于要求区域的最大面…...

车牌识别(附源代码)
完整项目已上传至github:End-to-end-for-chinese-plate-recognition/License-plate-recognition at master duanshengliu/End-to-end-for-chinese-plate-recognition GitHub 整体思路: 1.利用u-net图像分割得到二值化图像 2.再使用cv2进行边缘检测获得车牌区域坐…...
在VSCode中安装python
引言 Python 是一种广泛使用的高级编程语言,因其易学、易用、强大而受到欢迎。它由 Guido van Rossum 于 1991 年首次发布,并以简洁的语法和丰富的库生态系统而著称。 以下是 Python 的一些关键特点和优势: 关键特点 易于学习和使用&#x…...

StarkNet架构之L1-L2消息传递机制
文章目录 StarkNet架构之L1-L2消息传递机制L2 → L1消息L2 → L1消息结构L2 → L1消息哈希L1 → L2消息L1 → L2消息取消L1 → L2报文费用L1 → L2哈希额外资源StarkNet架构之L1-L2消息传递机制 原文地址:https://docs.starknet.io/architecture-and-concepts/network-archit…...

19.2 HTTP客户端-定制HTTP请求、调试HTTP、响应超时
1. 定制HTTP请求 如果需要对向服务器发送的HTTP请求做更多超越于默认设置的定制化。 client : http.Client{} 使用net/http包提供的导出类型Client,创建一个表示客户端的变量。request, err : http.NewRequest("GET", "https://ifconfig.io/ip&quo…...
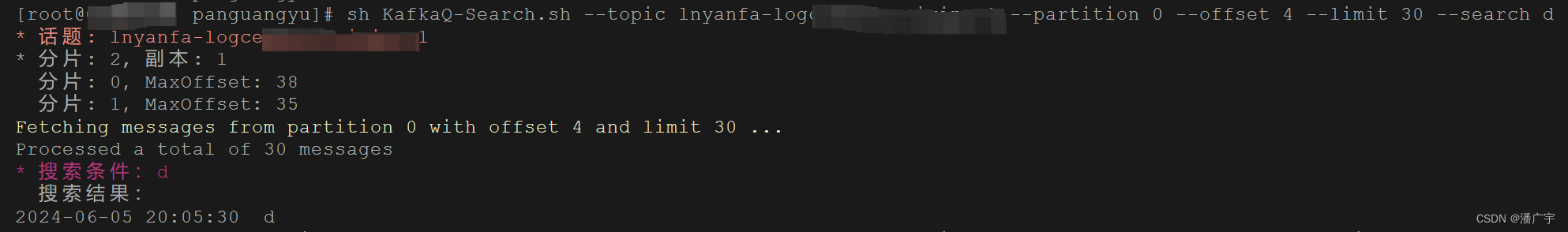
KafkaQ - 好用的 Kafka Linux 命令行可视化工具
软件效果前瞻 ~ 鉴于并没有在网上找到比较好的linux平台的kafka可视化工具,今天为大家介绍一下自己开发的在 Linux 平台上使用的可视化工具KafkaQ 虽然简陋,主要可以实现下面的这些功能: 1)查看当前topic的分片数量和副本数量 …...

不愧是字节,图像算法面试真细致
这本面试宝典是一份专为大四、研三春招和研二暑假实习生准备的珍贵资料。 涵盖了图像算法领域的核心知识和常见面试题,包括卷积神经网络、实例分割算法、目标检测、图像处理等多个方面。不论你是初学者还是有经验的老手,都能从中找到实用的内容。 通过…...

14、C++中代码重用
1、C模板的主要作用是允许编写通用代码,即能够在不同数据类型或数据结构上工作而无需重复编写代码。通过模板,可以实现代码的复用性和灵活性,从而提高开发效率和程序的可维护性。 typename关键字: 在C中,typename关键…...
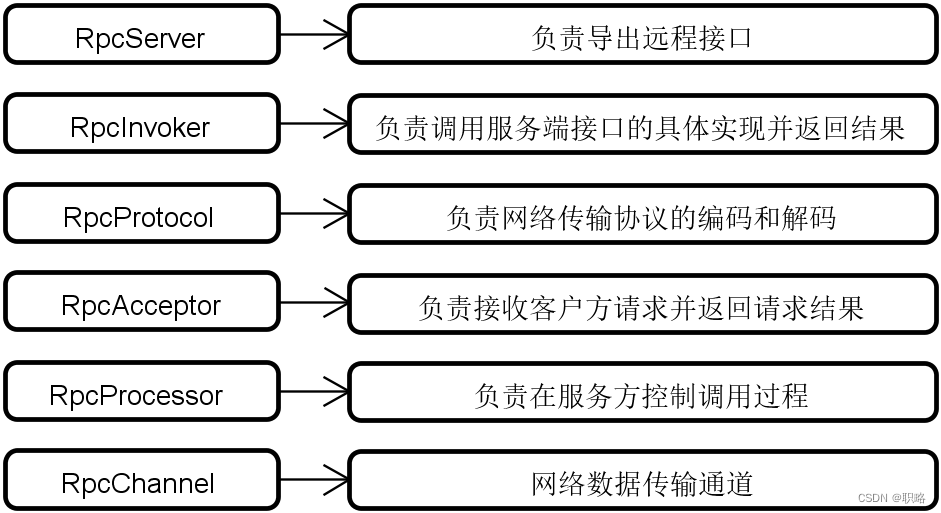
剖析框架代码结构的系统方法(下)
当面对Dubbo、Spring Cloud、Mybatis等开源框架时,我们可以采用一定的系统性的方法来快速把握它们的代码结构。这些系统方法包括对架构演进过程、核心执行流程、基础架构组成和可扩展性设计等维度的讨论。 在上一讲中,我们已经讨论了架构演进过程和核心执行流程这两个系统方法…...
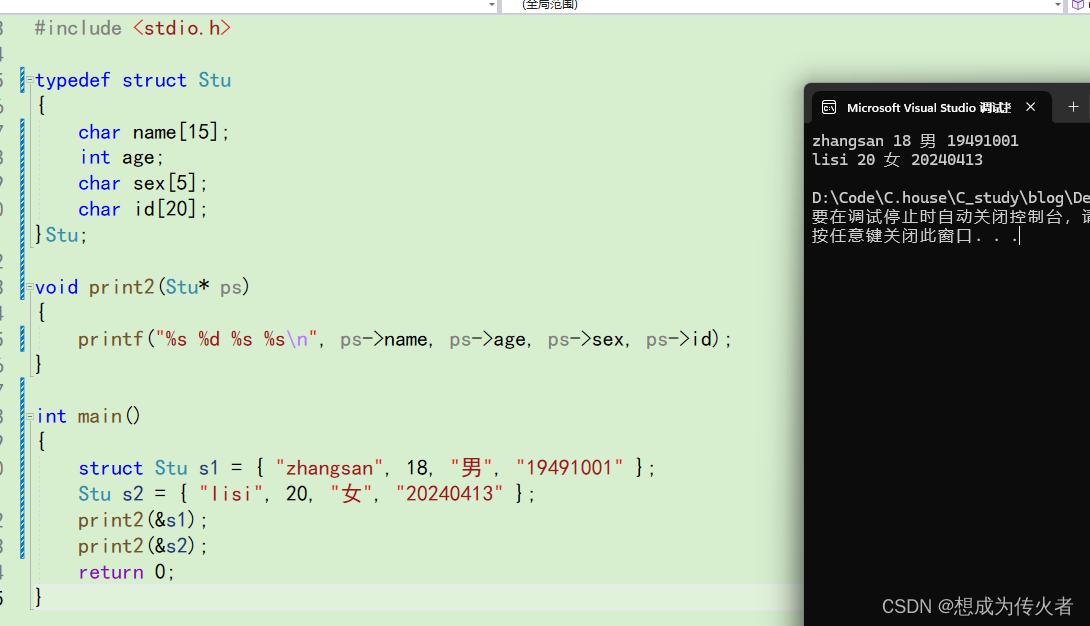
C语言学习笔记之结构体(一)
目录 什么是结构体? 结构体的声明 结构体变量的定义和初始化 结构体成员的访问 结构体传参 什么是结构体? 在现实生活中的很多事物无法用单一类型的变量就能描述清楚,如:描述一个学生,需要姓名,年龄&a…...
详解)
后进先出(LIFO)详解
LIFO 是 Last In, First Out 的缩写,中文译为后进先出。这是一种数据结构的工作原则,类似于一摞盘子或一叠书本: 最后放进去的元素最先出来 -想象往筒状容器里放盘子: (1)你放进的最后一个盘子(…...
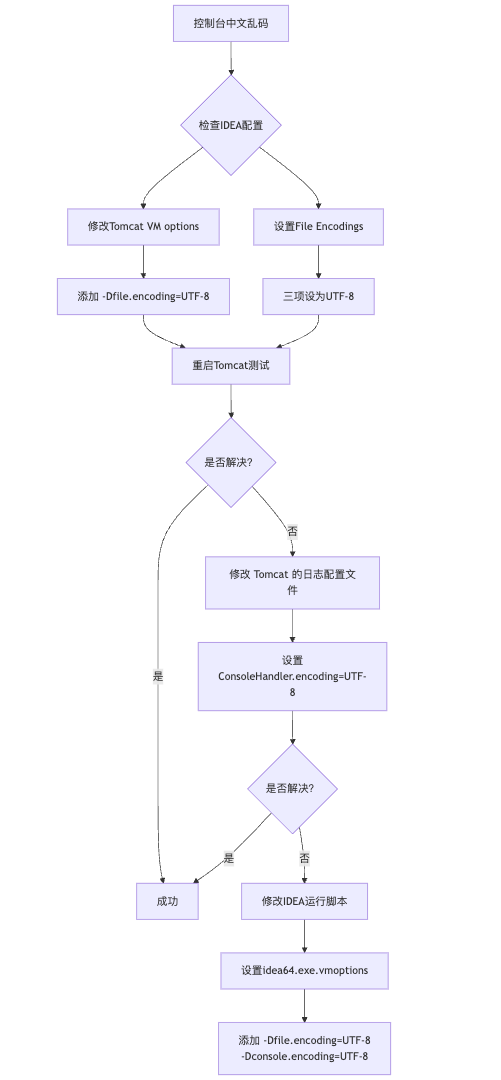
IDEA运行Tomcat出现乱码问题解决汇总
最近正值期末周,有很多同学在写期末Java web作业时,运行tomcat出现乱码问题,经过多次解决与研究,我做了如下整理: 原因: IDEA本身编码与tomcat的编码与Windows编码不同导致,Windows 系统控制台…...
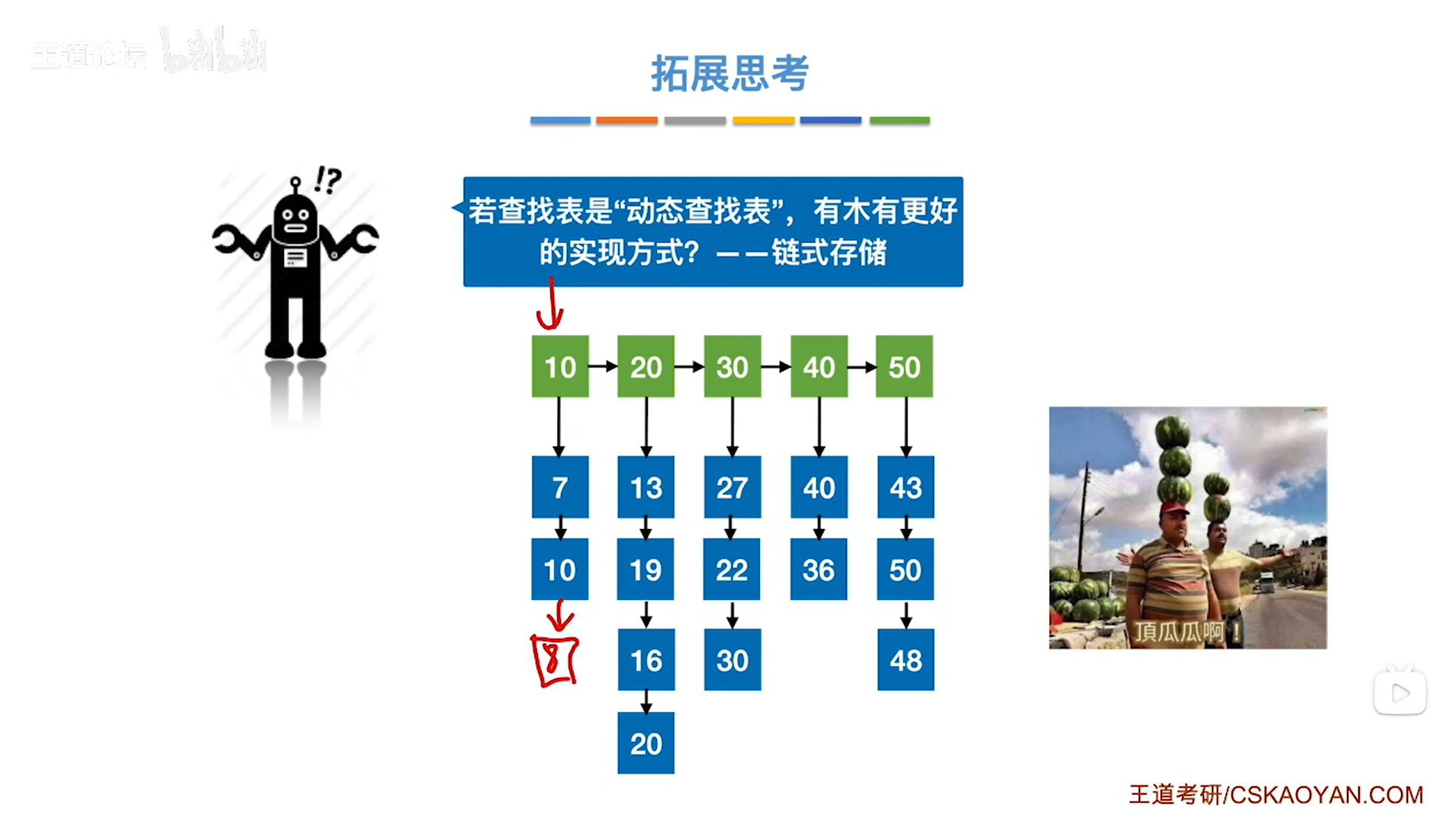
7.4.分块查找
一.分块查找的算法思想: 1.实例: 以上述图片的顺序表为例, 该顺序表的数据元素从整体来看是乱序的,但如果把这些数据元素分成一块一块的小区间, 第一个区间[0,1]索引上的数据元素都是小于等于10的, 第二…...

超短脉冲激光自聚焦效应
前言与目录 强激光引起自聚焦效应机理 超短脉冲激光在脆性材料内部加工时引起的自聚焦效应,这是一种非线性光学现象,主要涉及光学克尔效应和材料的非线性光学特性。 自聚焦效应可以产生局部的强光场,对材料产生非线性响应,可能…...

golang循环变量捕获问题
在 Go 语言中,当在循环中启动协程(goroutine)时,如果在协程闭包中直接引用循环变量,可能会遇到一个常见的陷阱 - 循环变量捕获问题。让我详细解释一下: 问题背景 看这个代码片段: fo…...
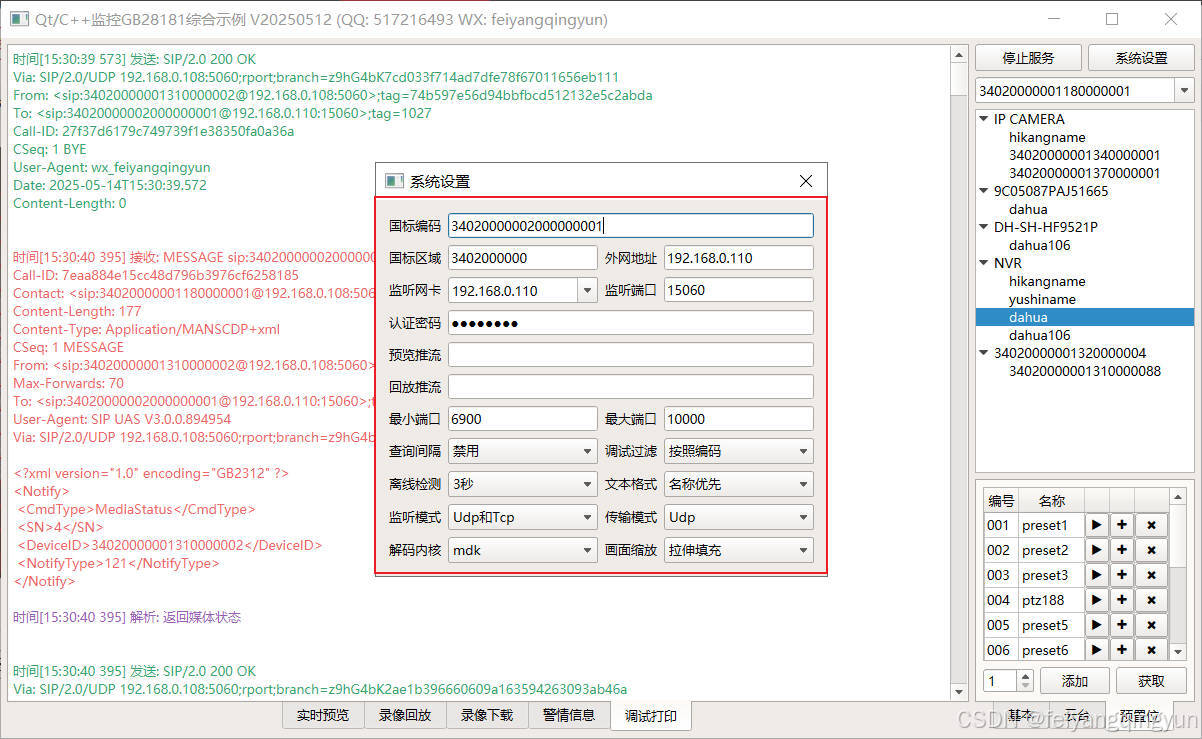
Qt/C++开发监控GB28181系统/取流协议/同时支持udp/tcp被动/tcp主动
一、前言说明 在2011版本的gb28181协议中,拉取视频流只要求udp方式,从2016开始要求新增支持tcp被动和tcp主动两种方式,udp理论上会丢包的,所以实际使用过程可能会出现画面花屏的情况,而tcp肯定不丢包,起码…...
:にする)
日语学习-日语知识点小记-构建基础-JLPT-N4阶段(33):にする
日语学习-日语知识点小记-构建基础-JLPT-N4阶段(33):にする 1、前言(1)情况说明(2)工程师的信仰2、知识点(1) にする1,接续:名词+にする2,接续:疑问词+にする3,(A)は(B)にする。(2)復習:(1)复习句子(2)ために & ように(3)そう(4)にする3、…...
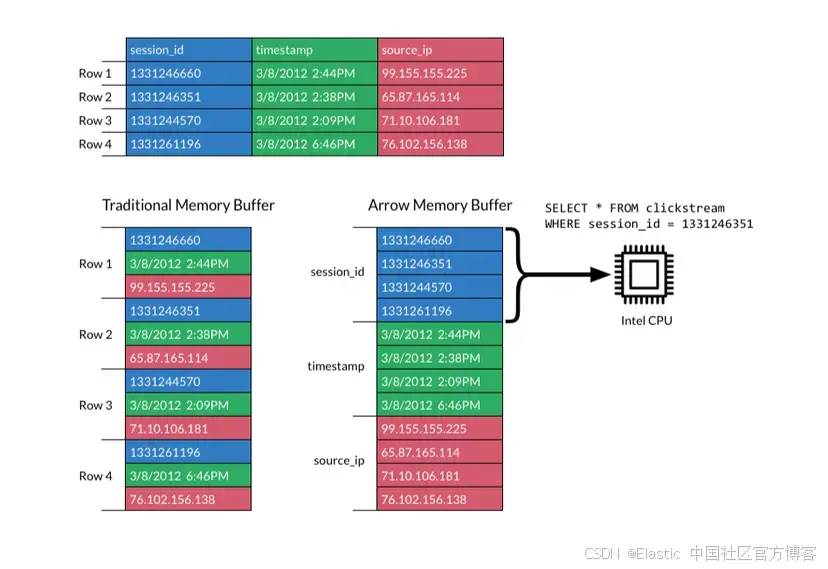
JavaScript 中的 ES|QL:利用 Apache Arrow 工具
作者:来自 Elastic Jeffrey Rengifo 学习如何将 ES|QL 与 JavaScript 的 Apache Arrow 客户端工具一起使用。 想获得 Elastic 认证吗?了解下一期 Elasticsearch Engineer 培训的时间吧! Elasticsearch 拥有众多新功能,助你为自己…...
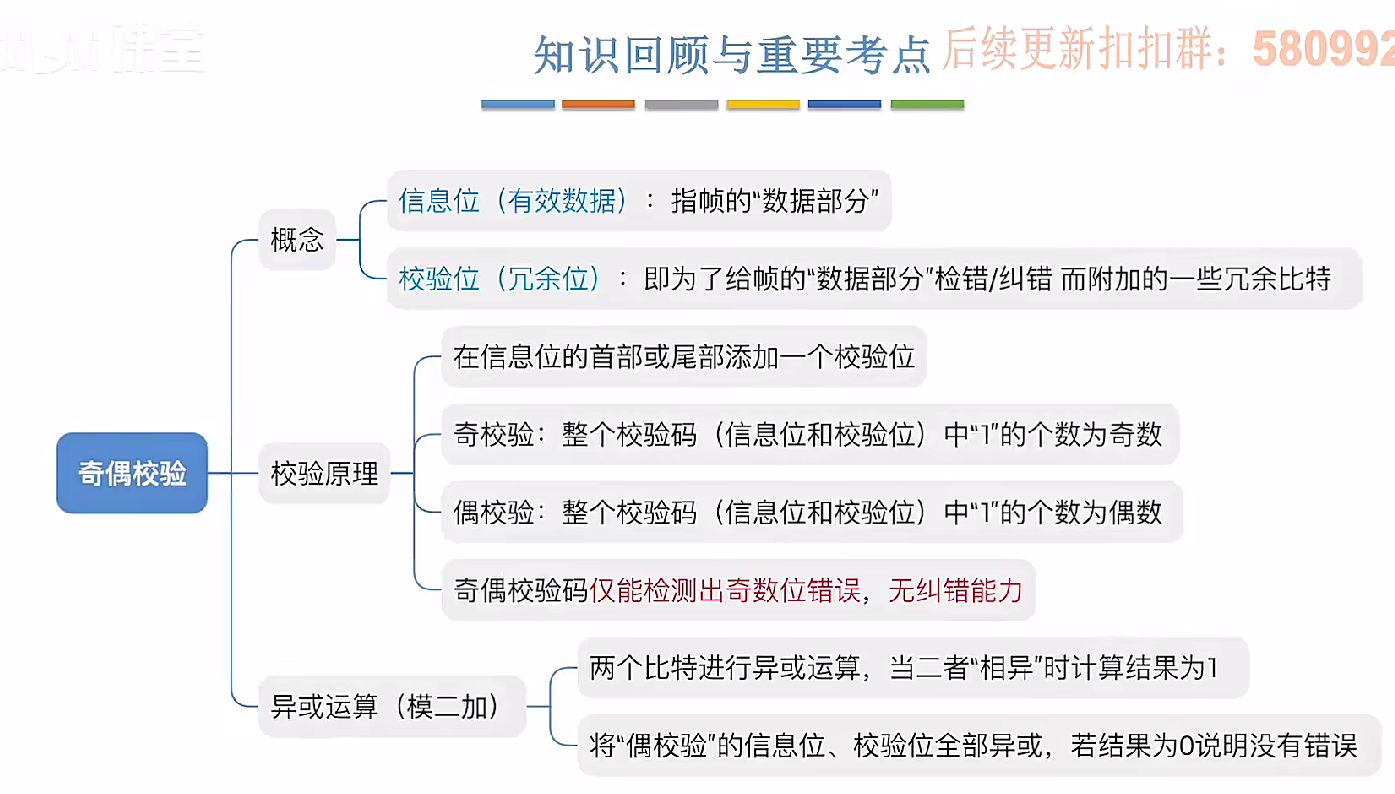
3.3.1_1 检错编码(奇偶校验码)
从这节课开始,我们会探讨数据链路层的差错控制功能,差错控制功能的主要目标是要发现并且解决一个帧内部的位错误,我们需要使用特殊的编码技术去发现帧内部的位错误,当我们发现位错误之后,通常来说有两种解决方案。第一…...
2025 后端自学UNIAPP【项目实战:旅游项目】6、我的收藏页面
代码框架视图 1、先添加一个获取收藏景点的列表请求 【在文件my_api.js文件中添加】 // 引入公共的请求封装 import http from ./my_http.js// 登录接口(适配服务端返回 Token) export const login async (code, avatar) > {const res await http…...
