CCNP350-401学习笔记(易错题合集)
CCNP350-401学习笔记(1-50题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.17)https://blog.csdn.net/shuyan1115/article/details/129088574?spm=1001.2014.3001.5502CCNP350-401学习笔记(51-100题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.18)
https://blog.csdn.net/shuyan1115/article/details/129092241?spm=1001.2014.3001.5502CCNP350-401学习笔记(101-150题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.18)
https://blog.csdn.net/shuyan1115/article/details/129098277?spm=1001.2014.3001.5502CCNP350-401学习笔记(151-200题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.19)
https://blog.csdn.net/shuyan1115/article/details/129104174?spm=1001.2014.3001.5502CCNP350-401学习笔记(201-250题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.20)
https://blog.csdn.net/shuyan1115/article/details/129117806?spm=1001.2014.3001.5502CCNP350-401学习笔记(251-300题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.20)
https://blog.csdn.net/shuyan1115/article/details/129121130?spm=1001.2014.3001.5502CCNP350-401学习笔记(301-350题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.20)
https://blog.csdn.net/shuyan1115/article/details/129127643?spm=1001.2014.3001.5502CCNP350-401学习笔记(351-400题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.21)
https://blog.csdn.net/shuyan1115/article/details/129135454?spm=1001.2014.3001.5502CCNP350-401学习笔记(401-450题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2022.2.21)
https://blog.csdn.net/shuyan1115/article/details/129136750?spm=1001.2014.3001.5502CCNP350-401学习笔记(451-500题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.22)
https://blog.csdn.net/shuyan1115/article/details/129159127?spm=1001.2014.3001.5502CCNP350-401学习笔记(501-550题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.22)
https://blog.csdn.net/shuyan1115/article/details/129159898?spm=1001.2014.3001.5502CCNP350-401学习笔记(551-600题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.22)
https://blog.csdn.net/shuyan1115/article/details/129161397?spm=1001.2014.3001.5502
1、Which component handles the orchestration plane of the Cisco SD-WAN?
A. vBond
B. vSmart
C. vManage
D. vEdge
2、What is a Type 1 hypervisor?
A. runs directly on a physical server and depends on a previously installed operating system
B. runs directly on a physical server and Includes its own operating system
C. runs on a virtual server and depends on an already installed operating system
D. runs on a virtual server and includes its own operating system
3、Which two LISP infrastructure elements are needed to support LISP to non-LISP internetworking? (Choose two.)
A. PETR
B. PITR
C. MR
D. MS
E. ALT
4、
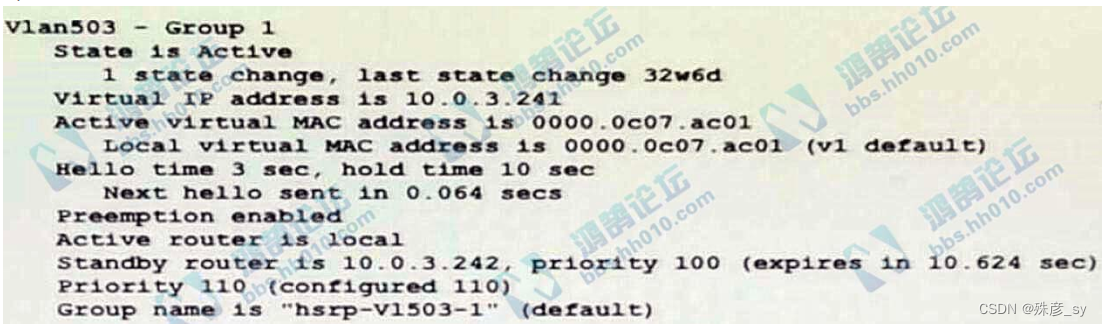
Refer to the exhibit. Which two facts does the device output confirm? (Choose two.)
A. The device's HSRP group uses the virtual IP address 10.0.3.242
B. The device is configured with the default HSRP priority.
C. The standby device is configured with the default HSRP priority.
D. The device is using the default HSRP hello timer.
E. The device sends unicast messages to its peers
5、Which two statements about VRF-lite are true? (Choose two)
A. It can support multiple customers on a single switch
B. It supports most routing protocols, including EIGRP, ISIS, and OSPF
C. It should be used when a customer’s router is connected to an ISP over OSPF
D. It can increase the packet switching rate
E. It supports MPLS-VRF label exchange and labeled packets
6、Which statement about agent-based versus agentless configuration management tools is true?
A. Agentless tools use proxy nodes to interface with slave nodes.
B. Agentless tools require no messaging systems between master and slaves.
C. Agent-based tools do not require a high-level language interpreter such as Python or Ruby on slave nodes.
D. Agent-based tools do not require installation of additional software packages on the slave nodes
7、Which two namespaces does the LISP network architecture and protocol use? (Choose two)
A. TLOC
B. RLOC
C. DNS
D. VTEP
E. EID
8、What is the fact about Cisco EAP-FAST?
A. It requires a client certificate.
B. It is an IETF standard.
C. It does not require a RADIUS server certificate.
D. It operates in transparent mode
9、
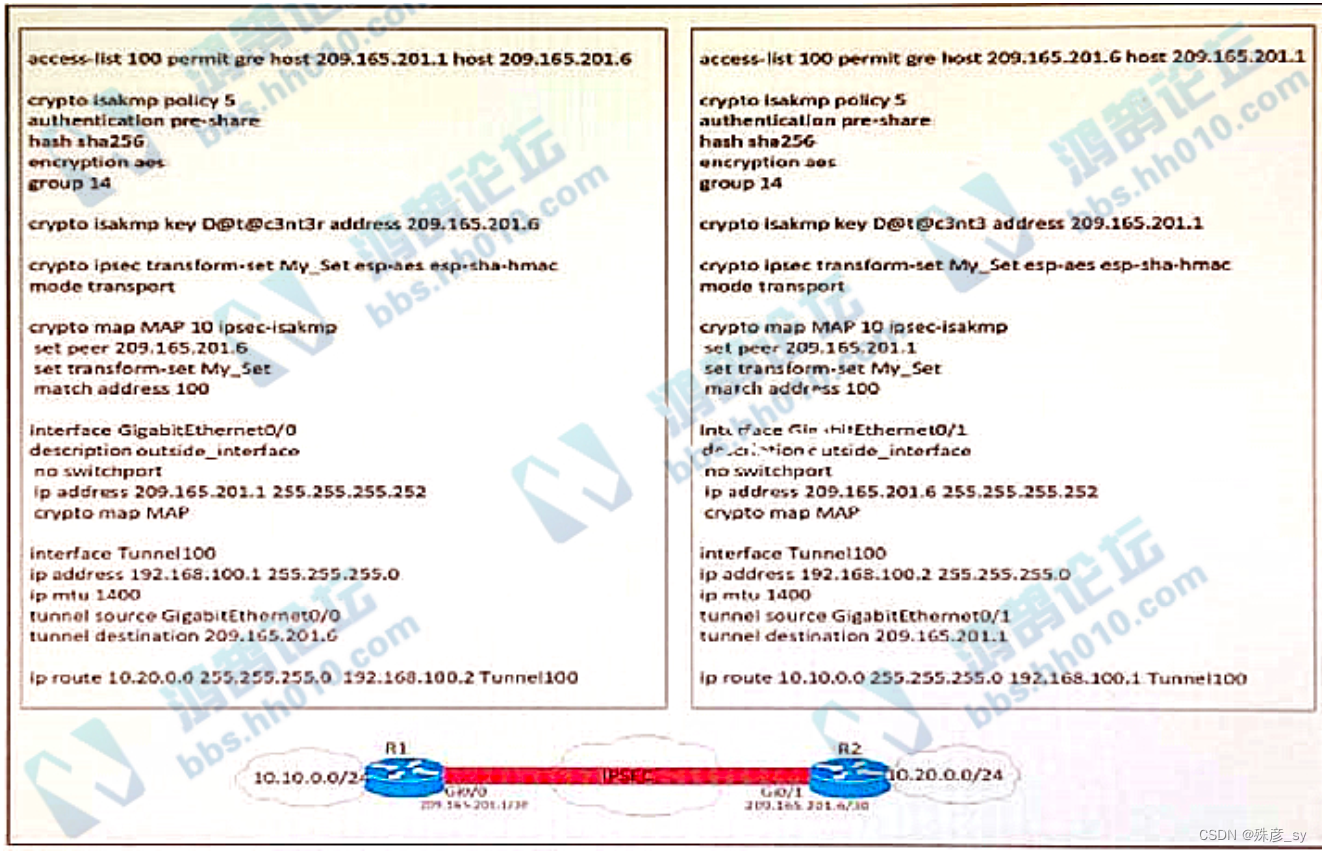
Refer to the exhibit. A network engineer must simplify the IPsec configuration by enabling IPsec over GRE
using IPsec profiles. Which two configuration changes accomplish this? (Choose two).
A. Remove the crypto map and modify the ACL to allow traffc between 10.10.0.0/24 to 10.20.0.0/24.
B. Create an IPsec profile, associate the transform-set ACL, and apply the profile to the tunnel interface.
C. Apply the crypto map to the tunnel interface and change the tunnel mode to tunnel mode ipsec ipv4
D. Remove all configuration related to crypto map from R1 and R2 and eliminate the ACL
E. Create an IPsec profile, associate the transform-set, and apply the profile to the tunnel interface.
10、 A GRE tunnel is down with the error message %TUN-5-RECURDOWN:
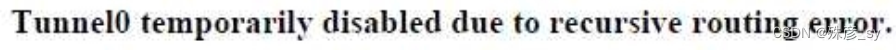
Which two options describe possible causes of the error? (Choose two.)
A. Incorrect destination IP addresses are configured on the tunnel.
B. There is link flapping on the tunnel
C. There is instability in the network due to route flapping
D. The tunnel mode and tunnel IP address are misconfigured
E. The tunnel destination is being routed out of the tunnel interface
11、 Which router is elected the IGMP Querier when more than one router is in the same LAN segment?
A. The router with the longest uptime
B. The router with the shortest uptime.
C. The router with the highest IP address
D. The router with the lowest IP address
12、How do agent-based versus agentless configuration management tools compare?
A. Agent-based tools do not require a high-level language interpreter such as Python or Ruby on slave nodes
B. Agentless tools require no messaging systems between master and slaves.
C. Agent-based tools do not require instaltation of additional software packages on the slave nodes
D. Agentless tools use proxy nodes to interface with slave nodes
13、In a traditional 3 tier topology, an engineer must explicitly configure a switch as the root bridge and exclude it from any further election process for the spanningtree domain. Which action accomplishes this task?
A. Configure the spanning-tree priority to 32768
B. Configure root guard and portfast on all access switch ports
C. Configure BPDU guard in all switch-to-switch connections
D. Configure the spanning-tree priority equal to 0
14、Which two statements about EIGRP load balancing are true? (Choose two)
A. Cisco Express Forwarding is required to load-balance across interfaces
B. A path can be used for load balancing only if it is a feasible successor
C. EIGRP supports unequal-cost paths by default
D. Any path in the EIGRP topology table can be used for unequal-cost load balancing
E. EIGRP supports 6 unequal-cost paths
15、What does the LAP send when multiple WLCs respond to the CISCO_CAPWAPCONTROLLER.localdomain hostname during the CAPWAP discovery and join process?
A. broadcast discover request
B. join request to all the WLCs
C. unicast discovery request to each WLC
D. Unicast discovery request to the first WLC that resolves the domain name
16、Refer to the exhibit. An engineer must establish eBGP peering between router R3 and router R4. Both routers should use their loopback interfaces as the BGP router ID.
Which configuration set accomplishes this task?
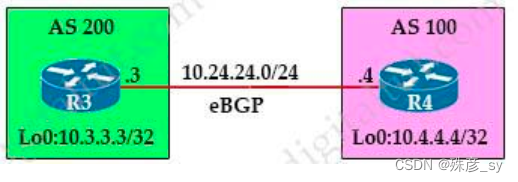
A. R3(config)#router bgp 200
R3(config-router)#neighbor 10.24.24.4 remote-as 100
R3(config-router)#bgp router-id 10.3.3.3
R4(config)#router bgp 100
R4(config-router)#neighbor 10.24.24.3 remote-as 200
R4(config-router)#bgp router-id 10.4.4.4
B. R3(config)#router bgp 200
R3(config-router)#neighbor 10.4.4.4 remote-as 100
R3(config-router)#neighbor 10.4.4.4 update-source loopback0
R4(config)#router bgp 100
R4(config-router)#neighbor 10.3.3.3 remote-as 200
R4(config-router)#neighbor 10.3.3.3 update-source loopback0
C. R3(config)#router bgp 200
R3(config-router)#neighbor 10.24.24.4 remote-as 100
R3(config-router)#neighbor 10.24.24.4 update-source loopback0
R4(config)#router bgp 100
R4(config-router)#neighbor 10.24.24.3 remote-as 200
R4(config-router)#neighbor 10.24.24.3 update-source loopback0
17、
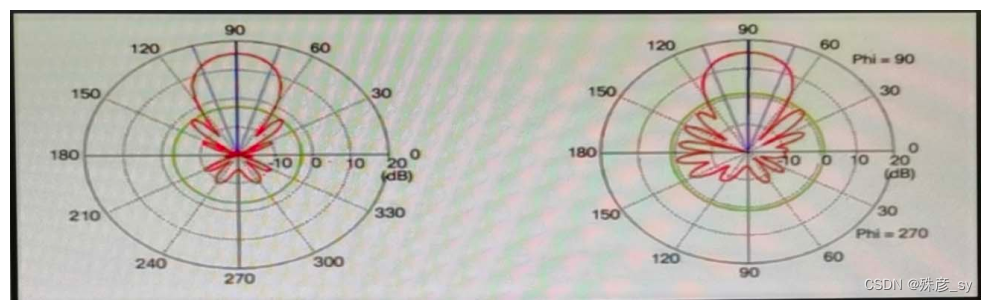
Refer to the exhibit. Which type of antenna is shown on the radiation patterns?
A. Yagi
B. dipole
C. patch
D. omnidirectional
18、Which behavior can be expected when the HSRP version is changed from 1 to 2?
A. No changes occur because the standby router is upgraded before the active router.
B. No changes occur because version 1 and 2 use the same virtual MAC OUI.
C. Each HSRP group reinitializes because the virtual MAC address has changed.
D. Each HSRP group reinitializes because the multicast address has changed.
19、
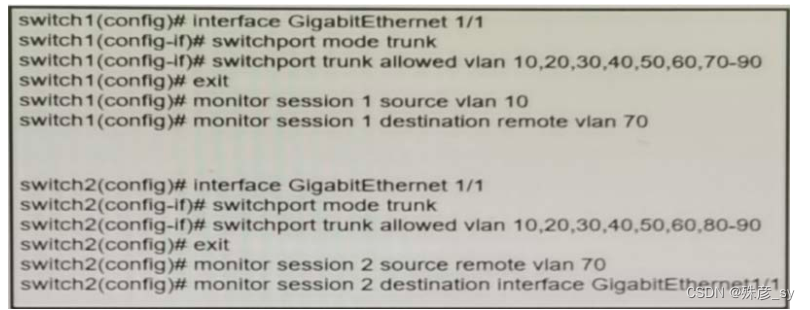
Refer to the exhibit A network administrator confiqured RSPAN to troubleshoot an issue between switch1 and switch2. The switches are connected using interface GigabitEthernet 1/1. An external packet capture device is connected to swich2 interface GigabitEthernet1/2. Which two commands must be added to complete this confiquration? (Choose two.)
A. switch2(config)# monitor session 2 destination vlan 10
B. switch1(config)# interface GigabitEthernet 1/1
switch1(confia-if# switchport mode access
switch1(config-if)# switchport access vlan 10
switch2(config)# interface GigabitEthernet 1/1
switch2(config-if)# switchport mode access
switch2(config-if)# switchport access vlan 10
C. switch2(config)# monitor session 1 source remote vlan 70
switch2(config)# monitor session 1 destination interface GigabitEthernet1/1
D. switch2(config-if)# switchport trunk allowed vlan 10,20,30,40,50,60,70-80
E. switch2(config)# monitor session 1 source remote vlan 70
switch2(confia)# monitor session 1 destination interface GigabitEthernet1/2
20、 What is the responsibility of a secondary WLC?
A. It enables Layer 2 and Layer 3 roaming between itself and the primary controller.
B. It shares the traffic load of the LAPs with the primary controller
C. It avoids congestion on the primary controller by sharing the registration load on the LAPs.
D. It registers the LAPs if the primary controller fails.
21、Which LISP infrastructure device provides connectivity between non-LISP sites and LISP sites by receiving non-LISP traffic with a LISP site destination?
A. PITR
B. map resolver
C. map server
D. PETR
22、A network administrator applies the following configuration to an IOS device.
aaa new-model
aaa authentication login default local group tacacs+
What is the process of password checks when a login attempt is made to the device?
A. A TACACS+ server is checked first. If that check fail, a database is checked
B. A TACACS+ server is checked first. If that check fail, a RADIUS server is checked. If that check fail, a
local database is checked
C. A local database is checked first. If that fails, a TACACS+server is checked, if that check fails, a RADIUS server is checked
D. A local database is checked first. If that check fails, a TACACS+server is checked
23、Which two statements about IP SLA are true? (Choose two)
A. It uses NetFlow for passive traffic monitoring
B. It can measure MOS
C. The IP SLA responder is a component in the source Cisco device
D. It is Layer 2 transport-independent
E. It uses active traffic monitoring
F. SNMP access is not supported
24、which antenna type should be used for a site-to-site wireless connection?
A. path
B. omnidirectional
C. dipole
D. Yagi
25、Refer to the exhibit.
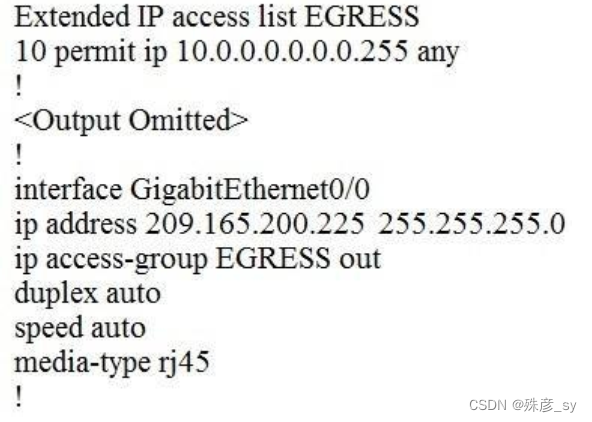
An engineer must block all traffic from a router to its directly connected subnet 209.165.200.0/24. The engineer applies access control list EGRESS in the outbound direction on the GigabitEthernet0/0 interface of the router. However, the router can still ping hosts on the 209.165.200.0/24 subnet.
Which explanation of this behavior is true?
A. Access control lists that are applied outbound to a router interface do not affect traffic that is sourced from the router.
B. After an access control list is applied to an interface, that interface must be shut and no shut for the access control list to take effect.
C. Only standard access control lists can block traffic from a source IP address.
D. The access control list must contain an explicit deny to block traffic from the router.
26、A customer has several small branches and wants to deploy a Wi-Fi solution with local management using CAPWAP.
Which deployment model meets this requirement?
A. local mode
B. autonomous
C. SD-Access wireless
D. Mobility Express
27、Which two actions provide controlled Layer 2 network connectivity between virtual machines running on the same hypervisor? (Choose two.)
A. Use a virtual switch running as a separate virtual machine.
B. Use a virtual switch provided by the hypervisor
C. Use a single trunk link to an external Layer2 switch.
D. Use a single routed link to an external router on stick.
E. Use VXLAN fabric after installing VXLAN tunneling drivers on the virtual machines.
28、Refer to exhibit. What are two reasons for IP SLA tracking failure? (Choose two )
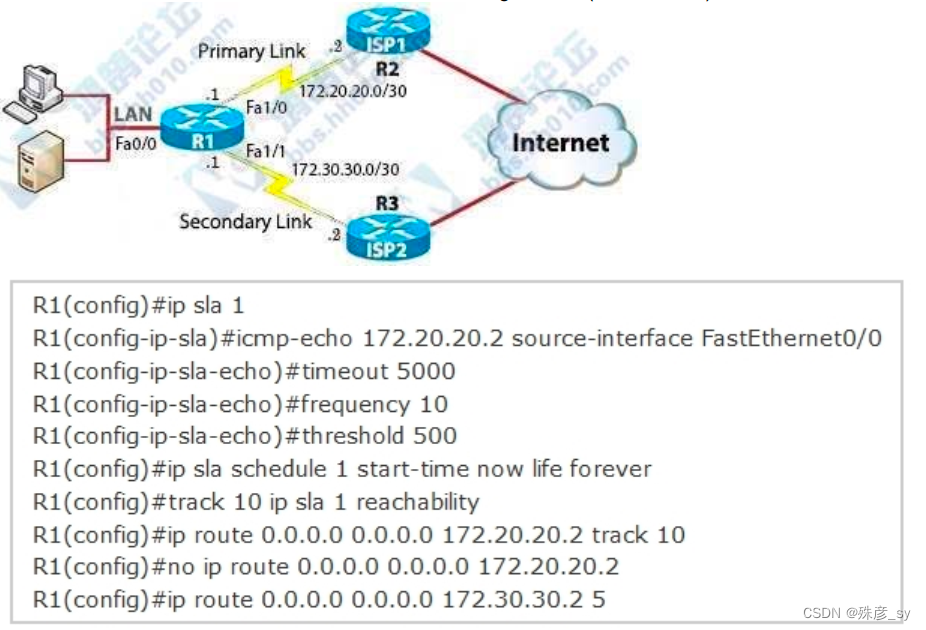
A. The source-interface is configured incorrectly
B. The destination must be 172.30.30.2 for icmp-echo
C. A route back to the R1 LAN network is missing in R2
D. The default route has wrong next hop IP address
E. The threshold value is wrong
29、In a Cisco SD- Access fabric, which control plane protocol is used for mapping and resolving endpoints?
A. DHCP
B. VXLAN
C. SXP
D. LISP
30、Which method should an engineer use to deal with a long-standing contention issue between any two VMs on the same host?
A. Adjust the resource reservation limits
B. Live migrate the VM to another host
C. Reset the VM
D. Reset the host
31、
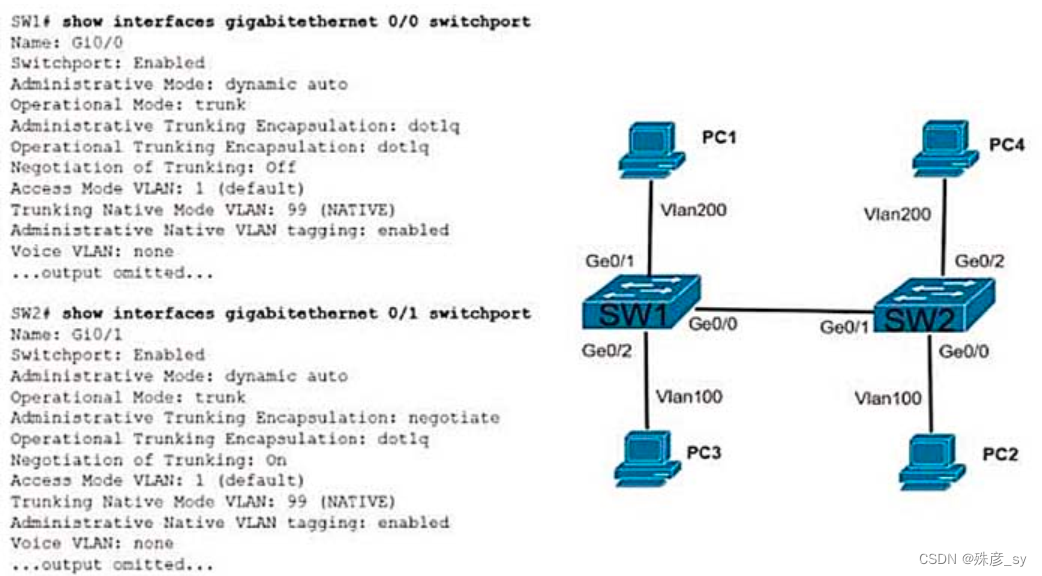
Refer to the exhibit.The connection between SW1 and SW2 is not operational.which two actions resolve the issue ?
A. configure switchport nonegotiate on SW1
B. configure switchport nonegotiate on SW2
C. configure switchport mode trunk on SW2
D. condigure switchport mode dynamic desirable on SW2
E. configure switchport mode access on SW2
32、What is a characteristic of a virtual machine?
A. It must be aware of other virtual machines, in order to allocate physical resource for
them
B. It is deployable without a hypervisor to host it
C. It must run the same operating system as its host
D. It relies on hypervisor to allocate computing resources for it
相关文章:

CCNP350-401学习笔记(易错题合集)
CCNP350-401学习笔记(1-50题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.17)https://blog.csdn.net/shuyan1115/article/details/129088574?spm1001.2014.3001.5502CCNP350-401学习笔记(51-100题)…...
喀秋莎Camtasia2023最新版本电脑录屏剪辑软件
录屏软件的鼻祖是techSmith 的喀秋莎(Techsmith Camtasia Studio),视频编辑软件Camtasia 2023发布,十大新功能放出!作为一个自媒体人,每天都要录制编辑视频,选择一个好的视频编辑工具就是大家首先面临的一个…...
「考研算法」
考研算法 前言 本系列文章涉及的算法内容,针对的是哈尔滨工业大学854科目。在本文中通过具体的算法题进行讲解相应算法。 今天涉及的算法主要有线性筛,十大排序中快速排序和归并排序。 后续会有动态规划的相关算法以及尝试模型的总结,如果…...

Android Framework-操作系统基础
最近在看《深入理解Android内核设计思想(第2版)》,个人感觉很不错,内容很多,现将书里个人认为比较重要的内容摘录一下,方便后期随时翻看。 计算机体系结构 硬件是软件的基石,所有的软件功能最…...
美国最新调查显示 50% 企业已在用 ChatGPT,其中 48% 已让其代替员工,你怎么看?
美国企业开始使用ChatGPT,我认为这不是什么新闻。 如果美国的企业现在还不使用ChatGPT,那才是个大新闻。 据新闻源显示,已经使用chatGPT的企业中,48%已经让其代替员工工作。 ChatGPT的具体职责包括:客服、代码编写、招…...
[Java·算法·中等]LeetCode17. 电话号码的字母组合
每天一题,防止痴呆题目示例分析思路1题解1分析思路2题解2题目 给定一个仅包含数字 2-9 的字符串,返回所有它能表示的字母组合。答案可以按 任意顺序 返回。 给出数字到字母的映射如下(与电话按键相同)。注意 1 不对应任何字母。…...

C#7/C#8/C#9 与dotnetSDK 以及dotnet framework对应关系
语言版本 对应的.net framework版本 对应的.net sdk版本 推荐使用的vs studio C#7.3 3.5、 4.0、 4.5 、4.5.1、 4.5.2 、4.6 、4.6.1、 4.6.2 4.7.1、 4.7.2 .netcore 2.0、.netcore2.1、 .netcore2.2 C#8.0 / F#4.7 不支持 .netcore 3.0、.netcore 3.1 C# 9.0 …...

jvm调优经验总结
最近一段时间很忙,忙到每天10点多11点下班还是感觉有很多事没有做完,不过倒也没有什么太过低落的情绪,有时候只安静的看一个视频,简单看点文字,或者平静的坐着,并没有太多想法。短时间的工作压力是可以接受…...

等保合规知识常见问题解答
Q1:什么是等级保护? 答:等级保护是指对国家重要信息、法人和其他组织及公民的专有信息以及公开信息和存储、传输、处理这些信息的信息系统分等级实行安全保护,对信息系统中使用的信息安全产品实行按等级管理,对信息系统…...

分享5款Windows同类软件中的翘楚
今天要给大家推荐的是5款软件,每个都是同类软件中的个中翘楚,请大家给我高调地使用起来,不用替我藏着掖着。1.沙盒工具——Sandboxie Sandboxie是一个电脑必备的沙盘工具,对于从网上下载的软件安装包、文件、视频、图片等等一切不…...

记--springboot-工具类中使用@Component、@Resource与@Value失效
写一个工具类 需要使用Resource注入RedisTemplate 使用Value获取application.properties配置文件中配置 并使用Component将该工具类交个spring管理 调试的时候RedisTemplate以及所有的变量全是是null 看了网上的各种解决方式五花八门 有的说出现问题的原因:Compon…...

手写一个react,看透react运行机制
适合人群 本文适合0.5~3年的react开发人员的进阶。 讲讲废话: react的源码,的确是比vue的难度要深一些,本文也是针对初中级,本意让博友们了解整个react的执行过程。 写源码之前的必备知识点 JSX 首先我们需要了解什么是JSX。…...

JS判断输入值是否为正整数,判断变量是否为数字
这篇文章将讨论如何确定一个变量是否代表 JavaScript 中的有效数字。 1.JS中的test是原来是JS中检测字符串中是否存在的一种模式,JS输入值是否为判断正整数代码: <script type”text/javascript”> function test() { var num document.getElem…...
Android开发八股文,Android也有自己的八股文了
前言别的行业都有自己的八股文,凭什么Android没有。2023春招即将来临,很多同学会问 Android开发的面试题有必要背吗?我的回答是:很有必要。你可以讨厌这种模式,但你一定要去背,因为不背你就进不了大厂。国内…...
你需要同款“Unreal项目自动化编译、打包和部署”方案吗?
在过往几期的UWA Pipeline最佳实践案例中,我们分享了如何通过Pipeline实现性能优化、性能管理、游戏内容验收和云真机系统的应用(实现批量真机设备的自动化测试,以及针对特效性能优化的方式),其实这些高效的方法并不局…...
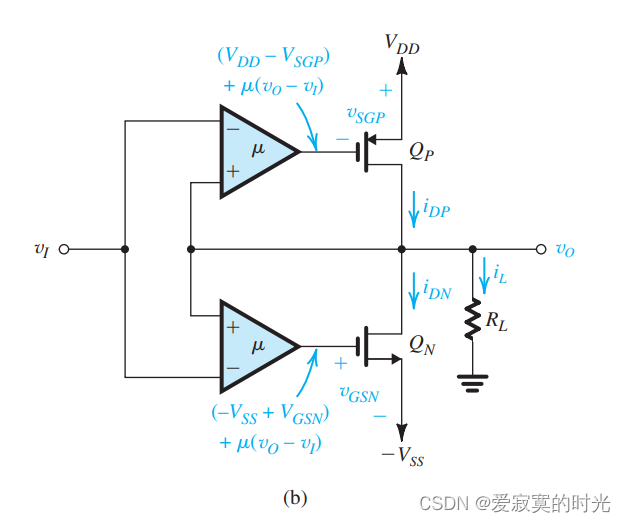
电子技术——CMOS-AB类输出阶
电子技术——CMOS-AB类输出阶 本节我们研究CMOS-AB类输出阶。 经典配置 下图展示了一个经典的CMOS-AB类输出阶: 这个很像BJT二极管偏置版本的AB类输出阶,在这里二极管偏置变成了 Q1Q_1Q1 和 Q2Q_2Q2 偏置。不想BJT的情况,这里 QNQ_NQN…...

2023王道考研数据结构笔记第二章线性表
第二章 线性表 2.1 线性表的定义 2.1.1 线性表的基本概念 线性表是具有相同数据类型的n(n>0)个数据元素的有限序列,其中n为表长,当n0时线性表是一个空表。若用L命名线性表,则其一般表示为: L(a1,a2,...,ai,ai1,...,an)L(a_1…...
[chapter 11][NR Physical Layer][Layer Mapping]
前言:这里参考Curious Being系列 ,简单介绍一下NR 5G 物理层核心技术层映射.我们主要讲了一下what is layer Mapping, why need layer Mapping, how layer Mapping 参考文档:3GPP 38.211- 6.3.1.3 Layer mapping《5G NR Physical Layer | Cha…...

什么是工业物联网(IIoT)?
什么是工业物联网(IIoT)?工业物联网(IIoT) 被定义为一组设备和应用,允许大企业创建从核心到边缘的端到端连接环境。其还包括传统的物理基础设施,如集装箱和物流卡车,以收集数据,对事件做出反应,并在智能设备的帮助下做…...
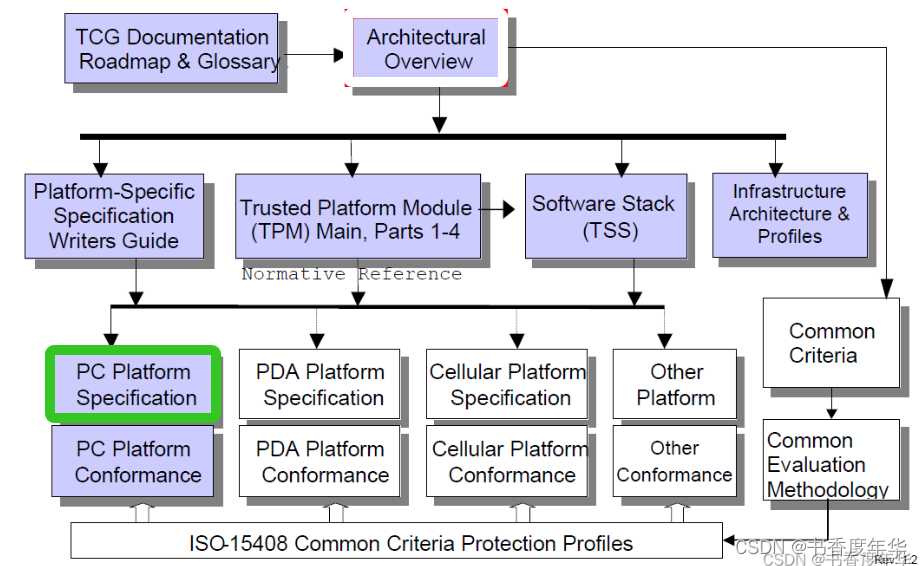
「TCG 规范解读」PC 平台相关规范(4)
可信计算组织(Ttrusted Computing Group,TCG)是一个非盈利的工业标准组织,它的宗旨是加强在相异计算机平台上的计算环境的安全性。TCG于2003年春成立,并采纳了由可信计算平台联盟(the Trusted Computing Platform Alli…...

逻辑回归:给不确定性划界的分类大师
想象你是一名医生。面对患者的检查报告(肿瘤大小、血液指标),你需要做出一个**决定性判断**:恶性还是良性?这种“非黑即白”的抉择,正是**逻辑回归(Logistic Regression)** 的战场&a…...

Caliper 配置文件解析:config.yaml
Caliper 是一个区块链性能基准测试工具,用于评估不同区块链平台的性能。下面我将详细解释你提供的 fisco-bcos.json 文件结构,并说明它与 config.yaml 文件的关系。 fisco-bcos.json 文件解析 这个文件是针对 FISCO-BCOS 区块链网络的 Caliper 配置文件,主要包含以下几个部…...
相比,优缺点是什么?适用于哪些场景?)
Redis的发布订阅模式与专业的 MQ(如 Kafka, RabbitMQ)相比,优缺点是什么?适用于哪些场景?
Redis 的发布订阅(Pub/Sub)模式与专业的 MQ(Message Queue)如 Kafka、RabbitMQ 进行比较,核心的权衡点在于:简单与速度 vs. 可靠与功能。 下面我们详细展开对比。 Redis Pub/Sub 的核心特点 它是一个发后…...

代码随想录刷题day30
1、零钱兑换II 给你一个整数数组 coins 表示不同面额的硬币,另给一个整数 amount 表示总金额。 请你计算并返回可以凑成总金额的硬币组合数。如果任何硬币组合都无法凑出总金额,返回 0 。 假设每一种面额的硬币有无限个。 题目数据保证结果符合 32 位带…...

JS手写代码篇----使用Promise封装AJAX请求
15、使用Promise封装AJAX请求 promise就有reject和resolve了,就不必写成功和失败的回调函数了 const BASEURL ./手写ajax/test.jsonfunction promiseAjax() {return new Promise((resolve, reject) > {const xhr new XMLHttpRequest();xhr.open("get&quo…...
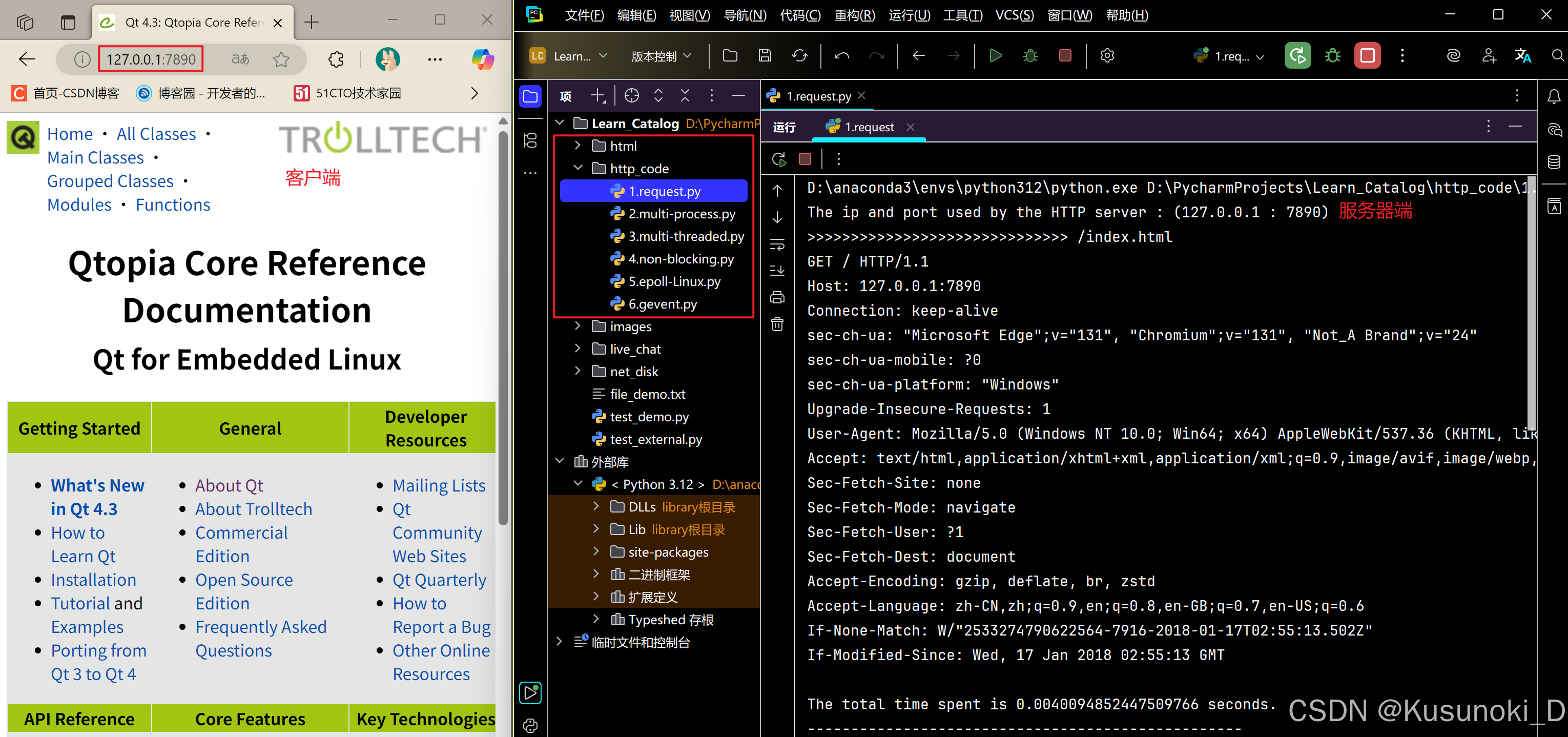
Python 实现 Web 静态服务器(HTTP 协议)
目录 一、在本地启动 HTTP 服务器1. Windows 下安装 node.js1)下载安装包2)配置环境变量3)安装镜像4)node.js 的常用命令 2. 安装 http-server 服务3. 使用 http-server 开启服务1)使用 http-server2)详解 …...

MySQL 主从同步异常处理
阅读原文:https://www.xiaozaoshu.top/articles/mysql-m-s-update-pk MySQL 做双主,遇到的这个错误: Could not execute Update_rows event on table ... Error_code: 1032是 MySQL 主从复制时的经典错误之一,通常表示ÿ…...
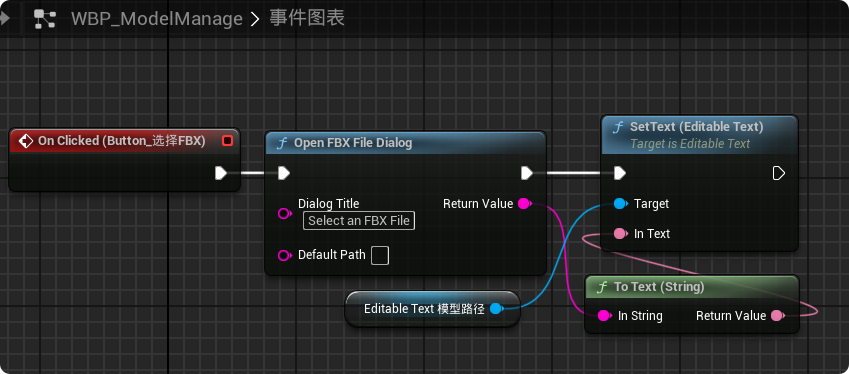
【UE5 C++】通过文件对话框获取选择文件的路径
目录 效果 步骤 源码 效果 步骤 1. 在“xxx.Build.cs”中添加需要使用的模块 ,这里主要使用“DesktopPlatform”模块 2. 添加后闭UE编辑器,右键点击 .uproject 文件,选择 "Generate Visual Studio project files",重…...

热烈祝贺埃文科技正式加入可信数据空间发展联盟
2025年4月29日,在福州举办的第八届数字中国建设峰会“可信数据空间分论坛”上,可信数据空间发展联盟正式宣告成立。国家数据局党组书记、局长刘烈宏出席并致辞,强调该联盟是推进全国一体化数据市场建设的关键抓手。 郑州埃文科技有限公司&am…...
ZYNQ学习记录FPGA(一)ZYNQ简介
一、知识准备 1.一些术语,缩写和概念: 1)ZYNQ全称:ZYNQ7000 All Pgrammable SoC 2)SoC:system on chips(片上系统),对比集成电路的SoB(system on board) 3)ARM:处理器…...
