CCNP350-401学习笔记(51-100题)
51、Which statement about a fabric access point is true?
A. It is in local mode and must be connected directly to the fabric edge switch.
B. It is in local mode and must be connected directly to the fabric border node
C. It is in FlexConnect mode and must be connected directly to the fabric border node.
D. It is in FlexConnect mode and must be connected directly to the fabric edge switch.
52、Which First Hop Redundancy Protocol maximizes uplink utilization and minimizes the amount of configuration that is necessary?
A. GLBP
B. HSRP v2
C. VRRP
D. HSRP v1
53、Which standard access control entry permits traffic from odd-numbered hosts in the 10.0.0.0/24 subnet?
A. permit 10.0.0.0 0.0.0.1
B. permit 10.0.0.1 0.0.0.254
C. permit 10.0.0.1 0.0.0.0
D. permit 10.0.0.0 255.255.255.254
54、Refer to the exhibit
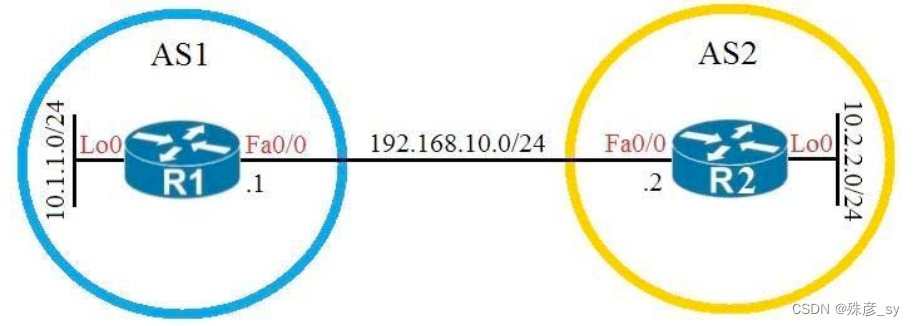
Which configuration establishes EBGP connected neighborship between these two directly connected neighbors and exchanges the loopback network of the two routers through BGP?
A. R1(config)#router bgp 1
R1(config-router)#neighbor 192.168.10.2 remote-as 2
R1(config-router)#network 10.1.1.0 mask 255.255.255.0
R2(config)#router bgp 2
R2(config-router)#neighbor 192.168.10.1 remote-as 1
R2(config-router)#network 10.2.2.0 mask 255.255.255.0
B. R1(config)#router bgp 1
R1(config-router)#neighbor 10.2.2.2 remote-as 2
R1(config-router)#network 10.1.1.0 mask 255.255.255.0
R2(config)#router bgp 2
R2(config-router)#neighbor 10.1.1.1 remote-as 1
R2(config-router)#network 10.2.2.0 mask 255.255.255.0
C. R1(config)#router bgp 1
R1(config-router)#neighbor 192.168.10.2 remote-as 2
R1(config-router)#network 10.0.0.0 mask 255.0.0.0
R2(config)#router bgp 2
R2(config-router)#neighbor 192.168.10.1 remote-as 1
R2(config-router)#network 10.0.0.0 mask 255.0.0.0
D. R1(config)#router bgp 1
R1(config-router)#neighbor 10.2.2.2 remote-as 2
R1(config-router)#neighbor 10.2.2.2 update-source |o0
R1(config-router)#network 10.1.1.0 mask 255.255.255.0
R2(config)#router bgp 2
R2(config-router)#neighbor 10.1.1.1 remote-as 1
R2(config-router)#neighbor 10.1.1.1 update-source |o0
R2(config-router)#network 10.2.2.0 mask 255.255.255.0
55、Refer to the exhibit.
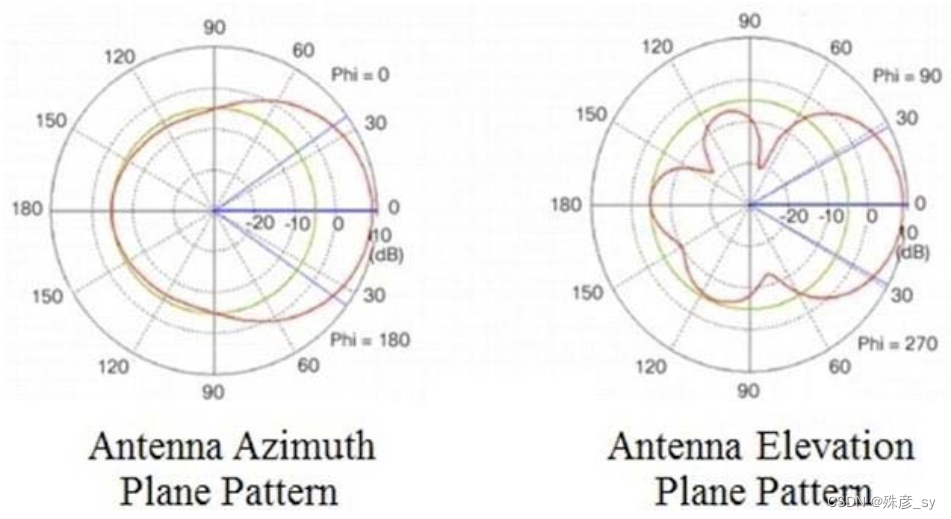
Which type of antenna do the radiation patterns present?
A. Yagi
B. patch
C. omnidirectional
D. dipole
56、Which method creates an EEM applet policy that is registered with EEM and runs on demand or manually?
A. event manager applet ondemand
event none
action 1.0 syslog priority critical msg ‘This is a message from ondemand’
B. event manager applet ondemand
action 1.0 syslog priority critical msg ‘This is a message from ondemand’
C. event manager applet ondemand
event register
action 1.0 syslog priority critical msg ‘This is a message from ondemand’
D. event manager applet ondemand
event manual
action 1.0 syslog priority critical msg ‘This is a message from ondemand’
57、An engineer is configuring local web authentication on a WLAN. The engineer chooses the Authentication radio button under the Layer 3 Security options for Web Policy.
Which device presents the web authentication for the WLAN?
A. ISE server
B. RADIUS server
C. anchor WLC
D. local WLC
58、Which controller is the single plane of management for Cisco SD-WAN?
A. vBond
B. vSmart
C. vManage
D. vEdge
59、A network is being migrated from IPv4 to IPv6 using a dual-stack approach. Network management is already 100% IPv6 enabled.
In a dual-stack network with two dual-stack NetFlow collectors, how many flow exporters are needed per network device in the flexible NetFlow configuration?
A. 1
B. 2
C. 4
D. 8
60、Which statement about TLS is true when using RESTCONF to write configurations on network devices?
A. It is used for HTTP and HTTPS requests.
B. It requires certificates for authentication.
C. It is provided using NGINX acting as a proxy web server.
D. It is not supported on Cisco devices.
61、Which reason could cause an OSPF neighborship to be in the EXSTART/EXCHANGE state?
A. mismatched OSPF link costs
B. mismatched OSPF network type
C. mismatched areas
D. mismatched MTU size
62、Which LISP device is responsible for publishing EID-to-RLOC mappings for a site?
A. ETR
B. MR
C. ITR
D. MS
63、Which method does the enable secret password option use to encrypt device passwords?
A. MD5
B. PAP
C. CHAP
D. AES
64、Which statement about agent-based versus agentless configuration management tools is true?
A. Agentless tools use proxy nodes to interface with slave nodes.
B. Agentless tools require no messaging systems between master and slaves.
C. Agent-based tools do not require a high-level language interpreter such as Python or Ruby on slave nodes.
D. Agent-based tools do not require installation of additional software packages on the slave nodes.
65、Which statement about Cisco Express Forwarding is true?
A. The CPU of a router becomes directly involved with packet switching decisions.
B. It uses a fast cache that is maintained in a router data plane.
C. It maintains two tables in the data plane: the FIB and adjacency table.
D. It makes forwarding decisions by a process that is scheduled through the IOS scheduler.
66、Refer to the exhibit.

What are two effects of this configuration? (Choose two.)
A. It establishes a one-to-one NAT translation.
B. The 209.165.201.0/27 subnet is assigned as the outside local address range.
C. The 10.1.1.0/27 subnet is assigned as the inside local addresses.
D. Inside source addresses are translated to the 209.165.201.0/27 subnet.
E. The 10.1.1.0/27 subnet is assigned as the inside global address range.
67、When configuring WPA2 Enterprise on a WLAN, which additional security component configuration is required?
A. PKI server
B. NTP server
C. RADIUS server
D. TACACS server
68、What is the structure of a JSON web token?
A. three parts separated by dots: header, payload, and signature
B. three parts separated by dots: version, header, and signature
C. header and payload
D. payload and signature
69、A response code of 404 is received while using the REST API on Cisco DNA Center to POST to this URI: /dna/intent/api/v1/template-programmer/project
What does the code mean?
A. The POST/PUT request was fulfilled and a new resource was created. Information about the resourceis in the response body.
B. The request was accepted for processing, but the processing was not completed.
C. The client made a request for a resource that does not exist.
D. The server has not implemented the functionality that is needed to fulfill the request.
70、What is a benefit of deploying an on-premises infrastructure versus a cloud infrastructure deployment?
A. ability to quickly increase compute power without the need to install additional hardware
B. less power and coding resources needed to run infrastructure on-premises
C. faster deployment times because additional infrastructure does not need to be purchased
D. lower latency between systems that are physically located near each other
71、A customer has several small branches and wants to deploy a Wi-Fi solution with local management using CAPWAP.
Which deployment model meets this requirement?
A. local mode
B. autonomous
C. SD-Access wireless
D. Mobility Express
72、Which two operations are valid for RESTCONF? (Choose two.)
A. PULL
B. PUSH
C. PATCH
D. REMOVE
E. ADD
F. HEAD
73、Refer to the exhibit
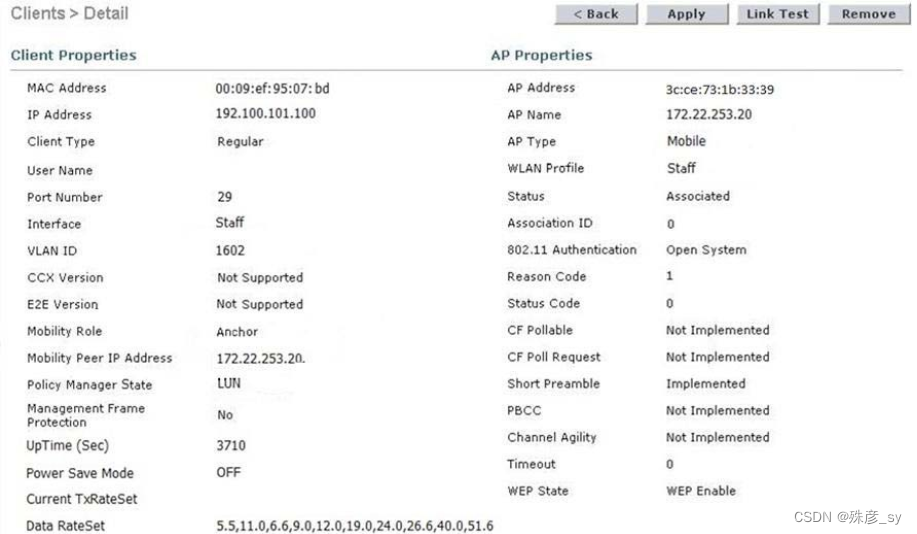
The WLC administrator sees that the controller to which a roaming client associates has Mobility Role Anchor configured under Clients > Detail.
Which type of roaming is supported?
A. indirect
B. Layer 3 intercontroller
C. intracontroller
D. Layer 2 intercontroller
74、In which part of the HTTP message is the content type specified?
A. HTTP method
B. body
C. header
D. URI
75、Which statement about VXLAN is true?
A. VXLAN encapsulates a Layer 2 frame in an IP-UDP header, which allows Layer 2 adjacency across router boundaries.
B. VXLAN uses the Spanning Tree Protocol for loop prevention.
C. VXLAN extends the Layer 2 Segment ID field to 24-bits, which allows up to 4094 unique Layer 2 segments over the same network.
D. VXLAN uses TCP as the transport protocol over the physical data center network.
76、What is the fact about Cisco EAP-FAST?
A. It requires a client certificate.
B. It is an IETF standard.
C. It does not require a RADIUS server certificate.
D. It operates in transparent mode.
77、What do Cisco DNA southbound APIs provide?
A. interface between the controller and the consumer
B. RESTful API interface for orchestrator communication
C. interface between the controller and the network devices
D. NETCONF API interface for orchestrator communication
78、Which DNS lookup does an access point perform when attempting CAPWAP discovery?
A. CISCO-CONTROLLER.local
B. CAPWAP-CONTROLLER.local
C. CISCO-CAPWAP-CONTROLLER.local
D. CISCO-DNA-CONTROLLER.local
79、Which TCP setting is tuned to minimize the risk of fragmentation on a GRE/IP tunnel?
A. MSS
B. MTU
C. MRU
D. window size
80、Which statement about an RSPAN session configuration is true?
A. Only one session can be configured at a time.
B. A special VLAN type must be used as the RSPAN destination.
C. A filter must be configured for RSPAN sessions.
D. Only incoming traffic can be monitored.
81、Refer to the exhibit.

An engineer must modify the access control list EGRESS to allow all IP traffic from subnet 10.1.10.0/24 to 10.1.2.0/24. The access control list is applied in the outbound direction on router interface GigabitEthernet 0/1.
Which configuration commands can the engineer use to allow this traffic without disrupting existing traffic flows? D
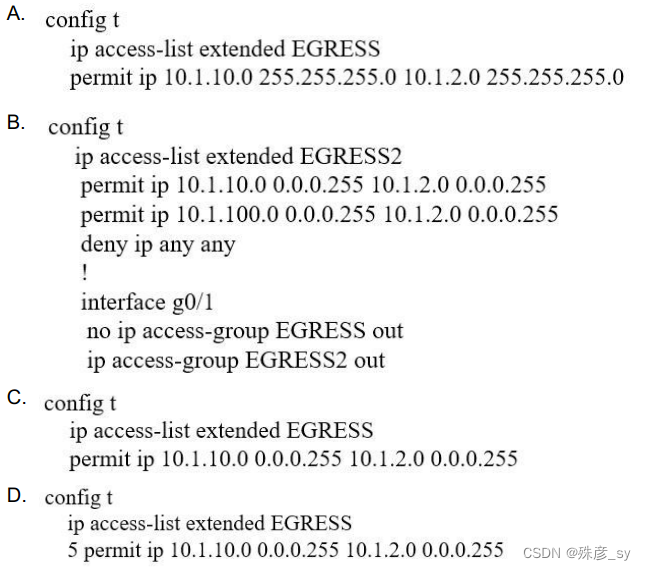
82、What is the role of a fusion router in an SD-Access solution?
A. acts as a DNS server
B. provides additional forwarding capacity to the fabric
C. performs route leaking between user-defined virtual networks and shared services
D. provides connectivity to external networks
83、Refer to the exhibit.
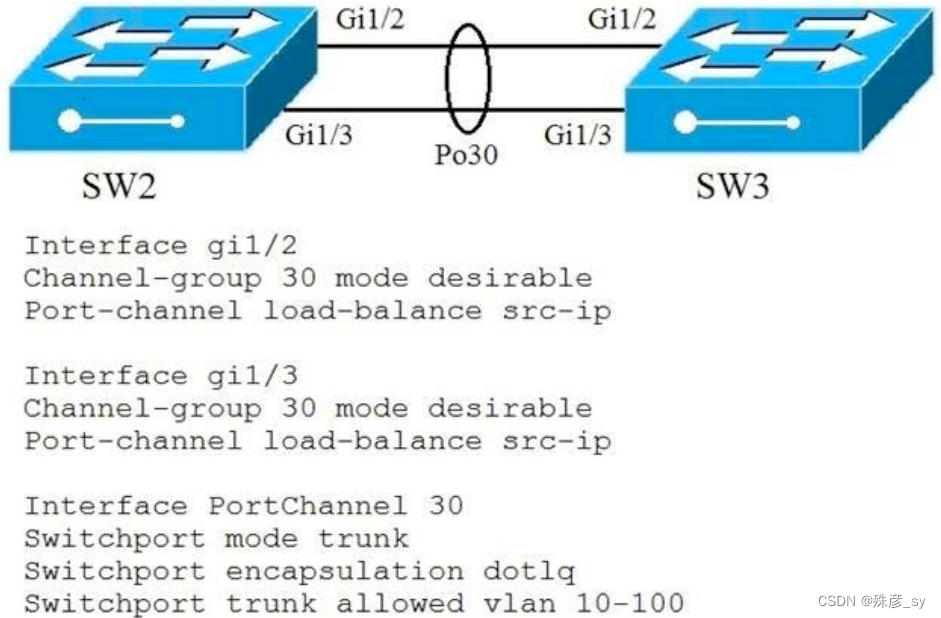
A port channel is configured between SW2 and SW3. SW2 is not running a Cisco operating system. When all physical connections are made, the port channel does not establish.
Based on the configuration except of SW3, what is the cause of the problem?
A. The port-channel mode should be set to auto.
B. The port channel on SW2 is using an incompatible protocol.
C. The port-channel trunk is not allowing the native VLAN.
D. The port-channel interface load balance should be set to src-mac.
84、What does this EEM applet event accomplish?
"event snmp oid 1.3.6.1.3.7.0.9.5.3.1.2.9 get-type next entry-op gt entry-val 75 poll-interval 5"
A. Upon the value reaching 75%, a SNMP event is generated and sent to the trap server.
B. It reads an SNMP variable, and when the value exceeds 75%, it triggers an action.
C. It issues email when the value is greater than 75% for five polling cycles.
D. It presents a SNMP variable that can be interrogated.
85、Which method displays text directly into the active console with a synchronous EEM applet policy?
A. event manager applet boom
event syslog pattern ‘UP’
action 1.0 syslog priority direct msg ‘logging directly to console’
B. event manager applet boom
event syslog pattern ‘UP’
action 1.0 gets ‘logging directly to console’
C. event manager applet boom
event syslog pattern ‘UP’
action 1.0 string ‘logging directly to console’
D. event manager applet boom
event syslog pattern ‘UP’
action 1.0 puts ‘logging directly to console’
86、Which two GRE features are configured to prevent fragmentation? (Choose two.)
A. TCP window size
B. IP MTU
C. TCP MSS
D. DF bit clear
E. MTU ignore
87、Which action is the vSmart controller responsible for in an SD-WAN deployment?
A. onboard vEdge nodes into the SD-WAN fabric
B. gather telemetry data from vEdge routers
C. distribute security information for tunnel establishment between vEdge routers
D. manage, maintain, and gather configuration and status for nodes within the SD-WAN fabric
88、what is fact about Cisco SD-access wireless network infrastructure deployments?
A. The access point is part of the fabric overlay.
B. The wireless client is part of the fabric overlay.
C. The access point is part of the fabric underlay.
D. The WLC is part of the fabric underlay.
89、Which feature is supported by EIGRP but is not supported by OSPF?
A. route filtering
B. unequal-cost load balancing
C. route summarization
D. equal-cost load balancing
90、What is the correct EBGP path attribute list, ordered from most preferred to least preferred, that the BGP best-path algorithm uses?
A. local preference, weight, AS path, MED
B. weight, local preference, AS path, MED
C. weight, AS path, local preference, MED
D. local preference, weight, MED, AS path
91、At which layer does Cisco DNA Center support REST controls?
A. session layer
B. northbound APIs
C. EEM applets or scripts
D. YAML output from responses to API calls
92、On which protocol or technology is the fabric data plane based in Cisco SD-Access fabric?
A. VXLAN
B. LISP
C. Cisco TrustSec
D. IS-IS
93、What is the difference between the enable password and the enable secret password when service password encryption is enabled on an IOS device?
A. The enable secret password is protected via stronger cryptography mechanisms.
B. The enable password cannot be decrypted.
C. The enable password is encrypted with a stronger encryption method.
D. There is no difference and both passwords are encrypted identically.
94、Which access control list allows only TCP traffic with a destination port range of 22-443, excluding port 80?
A. deny tcp any any eq 80
permit tcp any any gt 21 lt 444
B. permit tcp any any range 22 443
deny tcp any any eq 80
C. permit tcp any any eq 80
D. deny tcp any any eq 80permit tcp any any range 22 443
95、Which statement describes the IP and MAC allocation requirements for virtual machines on Type 1 hypervisors?
A. Virtual machines do not require a unique IP or unique MAC. They share the IP and MAC address of the physical server.
B. Each virtual machine requires a unique IP address but shares the MAC address with the physical server.
C. Each virtual machine requires a unique IP and MAC addresses to be able to reach to other nodes.
D. Each virtual machine requires a unique MAC address but shares the IP address with the physical server.
96、A local router shows an EBGP neighbor in the Active state.
Which statement is true about the local router?
A. The local router is attempting to open a TCP session with the neighboring router.
B. The local router is receiving prefixes from the neighboring router and adding them in RIB-IN.
C. The local router has active prefixes in the forwarding table from the neighboring router.
D. The local router has BGP passive mode configured for the neighboring router.
97、Which feature must be configured to allow packet capture over Layer 3 infrastructure?
A. RSPAN
B. ERSPAN
C. VSPAN
D. IPSPAN
98、Drag and drop the descriptions from the left onto the correct QoS components on the right.


99、Drag and drop the characteristics from the left onto the correct infrastructure deployment types on the right.


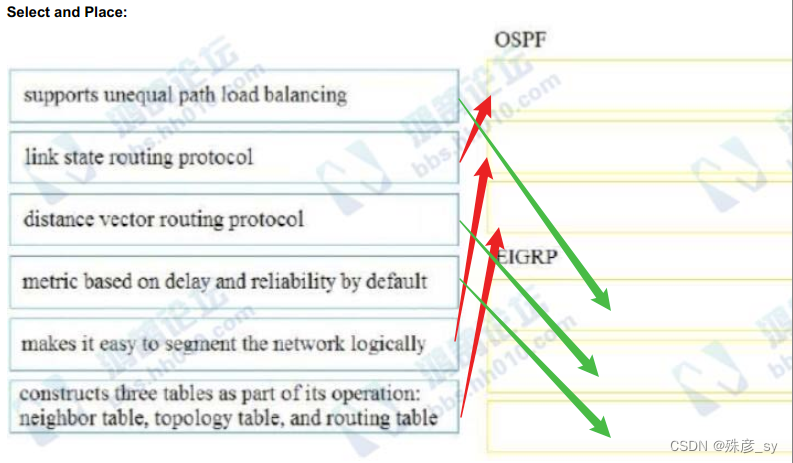
100、Drag and drop the characteristics from the left onto the correct routing protocol types on the right.

相关文章:

CCNP350-401学习笔记(51-100题)
51、Which statement about a fabric access point is true?A. It is in local mode and must be connected directly to the fabric edge switch. B. It is in local mode and must be connected directly to the fabric border node C. It is in FlexConnect mode and must …...
C语言学习_DAY_4_判断语句if_else和分支语句switch_case【C语言学习笔记】
高质量博主,点个关注不迷路🌸🌸🌸! 目录 1.案例引入 2.if判断语句的语法与注意事项 3.switch多分支语句的语法与注意事项 前言: 书接上回,我们已经学习了所有的数据类型、运算符,并且可以书写…...
)
实验07 赫夫曼编码及综合2022(带程序填空)
A. 【程序填空】赫夫曼编码题目描述给定n个叶子的权值,根据这些权值构造huffman树,并输出huffman编码参考课本第6.6节的算法6.12,注意算法中数组访问是从位置1开始赫夫曼构建中,默认左孩子权值不大于右孩子权值如果遇到两个孩子权…...
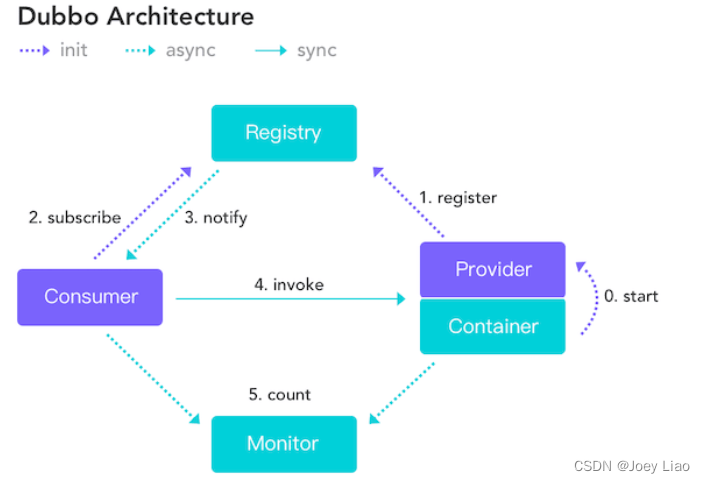
分布式 CAP BASE理论
文章目录CAP简介不是所谓的“3 选 2”CAP 实际应用案例BASE简介BASE 理论的核心思想总结CAP 简介 在理论计算机科学中,CAP 定理(CAP theorem)指出对于一个分布式系统来说,当设计读写操作时,只能同时满足以下三点中的…...

三调地类筛选器,Arcgis地类筛选
三调地类在使用是,需要分类统计,这个可以用于筛选; 标准地类筛选 农用地: DLBM IN(0303,0304,0306,0402,0101,0102,0103,0201,0201K,0202,0202K,0203,0203K,0204,0204K,0301,0301K,0302,0302K,0305,0307,0307K,0401,0403,0403K…...
)
华为OD机试 - 密室逃生游戏(Python)
密室逃生游戏 题目 小强增在参加《密室逃生》游戏,当前关卡要求找到符合给定 密码 K(升序的不重复小写字母组成) 的箱子, 并给出箱子编号,箱子编号为 1~N 。 每个箱子中都有一个 字符串 s ,字符串由大写字母、小写字母、数字、标点符号、空格组成, 需要在这些字符串中…...

白话C#之委托
一、什么是委托? 书本上是这样来定义委托的: 委托是一种动态调用方法的类型,属于引用型。委托是对方法的抽象和封装。委托对象实质上代表了方法的引用(即内存地址)。委托通常是委托某个方法来实现具体的功能。当我们调…...
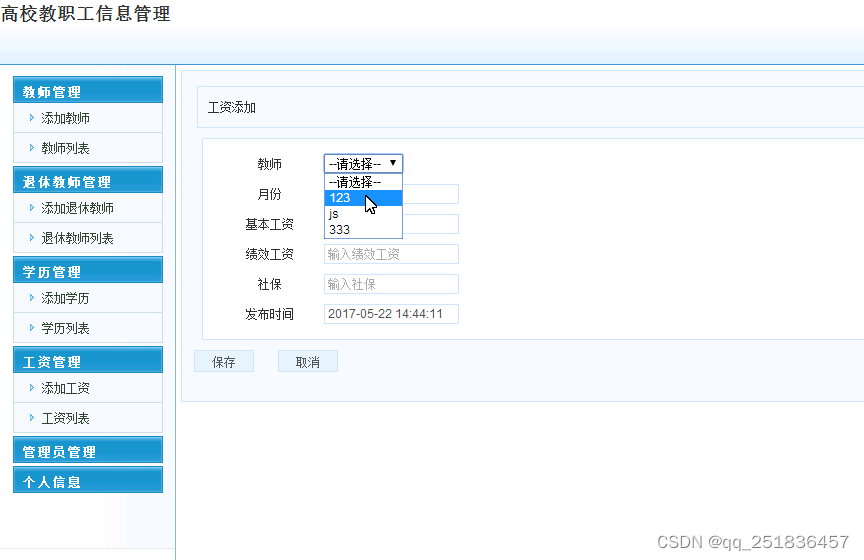
jsp高校教职工管理系统Myeclipse开发mysql数据库web结构java编程计算机网页项目
一、源码特点 jsp 高校教职工管理系统 是一套完善的web设计系统,对理解JSP java编程开发语言有帮助mvc模式 serlvetdaobean方式开发,系统具有完整的源代码和数据库,系统主要采用B/S模式 开发。开发环境为TOMCAT7.0,Myeclipse8.5开发&#…...

2023年数学建模美赛A题(A drought stricken plant communities)分析与编程
2023年数学建模美赛A题(A drought stricken plant communities)分析与编程 2023年数学建模美赛D题(Prioritizing the UN Sustainability Goals)分析与编程 特别提示: 1 本文介绍2023年美赛题目,进行深入分析…...
Delphi 中自定义鼠标指针图像
Dephi中的鼠标指针是可以自由定义的,如果是使用系统提供的图标,那么直接通过可视控件的Cursor属性赋值就可以。例如设置Form的鼠标为 crHourGlass 沙漏:Form1.Cursor : crHourGlass;也可以在设计期(IDE环境中)直接更改…...

【计算机网络】物理层
文章目录物理层的基本概念传输媒体同轴电缆双绞线光纤电力线电磁波红外线可见光传输方式串行传输和并行传输同步传输和异步传输单工,半双工以及全双工通信编码与调制常用编码不归零编码归零编码曼彻斯特编码差分曼彻斯特编码基本调制混合调制信道的极限容量奈氏准…...
)
华为OD机试 - 最少停车数(Python)
最少停车数 题目 特定大小的停车场 数组cars表示 其中1表示有车0表示没车 车辆大小不一,小车占一个车位(长度1) 货车占两个车位(长度2) 卡车占三个车位(长度3) 统计停车场最少可以停多少辆车 返回具体的数目 输入 整型字符串数组cars 其中1表示有车0表示没车 数组长度 <…...
)
面试题-前端开发JavaScript篇上(答案超详细)
文章目录 闭包说一下类的创建和继承如何解决异步回调地狱说说前端中的事件流如何让事件先冒泡后捕获说一下事件委托说一下图片的懒加载和预加载mouseover 和 mouseenter 的区别JS 的 new 操作符做了哪些事改变函数内部 this 指针的指向函数(bind,apply,call 的区别)JS 的各种…...
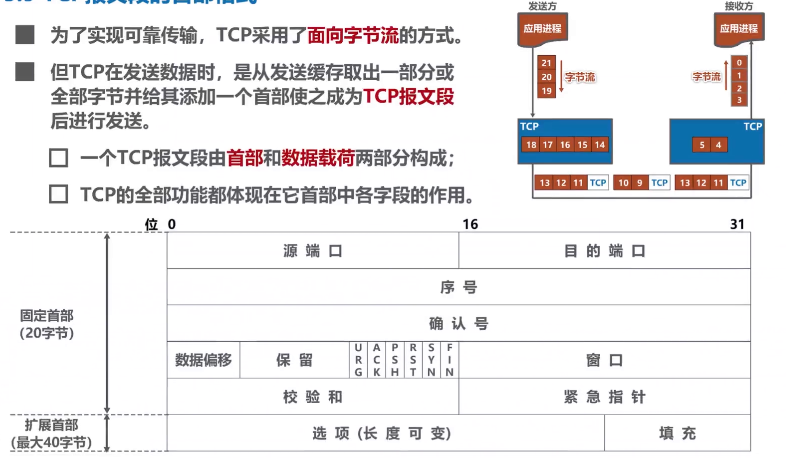
【计算机网络】运输层
文章目录运输层概述运输层端口号、复用与分用的概念UDP和TCP的对比TCP的流量控制TCP的拥塞控制TCP超时重传时间的选择TCP可靠传输的实现TCP的运输连接管理TCP的连接建立(3次握手)TCP的连接释放(4次挥手)TCP报文段的首部格式运输层概述 这里我们对运输层进行概述,之…...
)
20222023华为OD机试 - 基站维修工程师(Python)
基站维修工程师 题目 小王是一名基站维护工程师,负责某区域的基站维护。 某地方有 n 个基站( 1<n<10 ),已知各基站之间的距离 s( 0<s<500 ), 并且基站 x 到基站 y 的距离,与基站 y 到 基站 x 的距离并不一定会相同。 小王从基站 1 出发,途经每个基站 1 …...
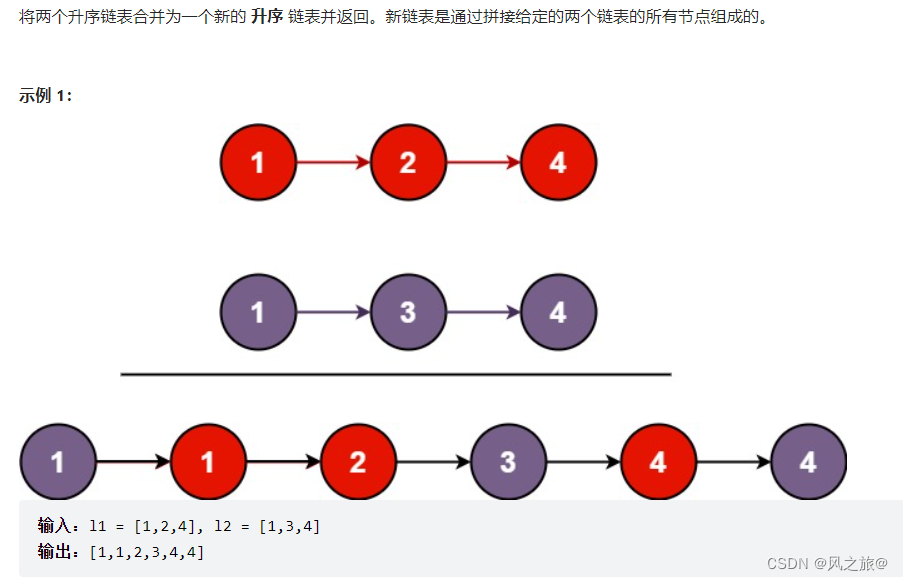
21. 合并两个有序链表
题目链接:解题思路:遍历,双指针:因为两个链表有序,所以只需要依次比较两个元素的大小,然后添加到新的链表中即可first指针指向第一个链表l1,second指针指向第二个链表l2,answer保存合…...

产品经理知识体系:5.如何做好产品数据分析?
数据分析 思考 笔记 数据分析 思路 基于用户路径:用户的活动路径,操作流程等行为数据。 基于产品节点:转化率、占比 分析类型 先定性:先抛出问题、提出假设 再定量:数据验证问题、验证假设 先定性、再定量、最后得…...
详解垃圾回收算法,优缺点是什么?|金三银四系列
本文详细介绍了在 JVM 中如何判断哪些对象是需要回收的,以及不同的垃圾回收算法以及优缺点。点击上方“后端开发技术”,选择“设为星标” ,优质资源及时送达上篇文章详细介绍了 JVM 的结构以及其内存结构,需要阅读请移步。本文主要…...
 SnapshotManager 之标识文件)
Android 虚拟 A/B 详解(七) SnapshotManager 之标识文件
本文为洛奇看世界(guyongqiangx)原创,转载请注明出处。 原文链接:https://blog.csdn.net/guyongqiangx/article/details/129098176 Android 虚拟 A/B 分区《Android 虚拟 A/B 分区》系列,更新中,文章列表: Android 虚拟 A/B 详解(一) 参考资料推荐Android 虚拟 A/B 详解(二…...

LA@生成子空间@范数@衡量矩阵大小@正交化
文章目录线性组合与线性方程组生成子空间范数LpL^pLp范数向量点积用范数表示ref衡量矩阵大小特殊类型矩阵和向量对角阵向量长度性质单位向量向量单位化(正规化)正交向量正交正交向量组标准正交基正交化(schmidt)正交矩阵矩阵是正交矩阵的充要条件对称矩阵正交相似概念区分&…...
)
浏览器访问 AWS ECS 上部署的 Docker 容器(监听 80 端口)
✅ 一、ECS 服务配置 Dockerfile 确保监听 80 端口 EXPOSE 80 CMD ["nginx", "-g", "daemon off;"]或 EXPOSE 80 CMD ["python3", "-m", "http.server", "80"]任务定义(Task Definition&…...
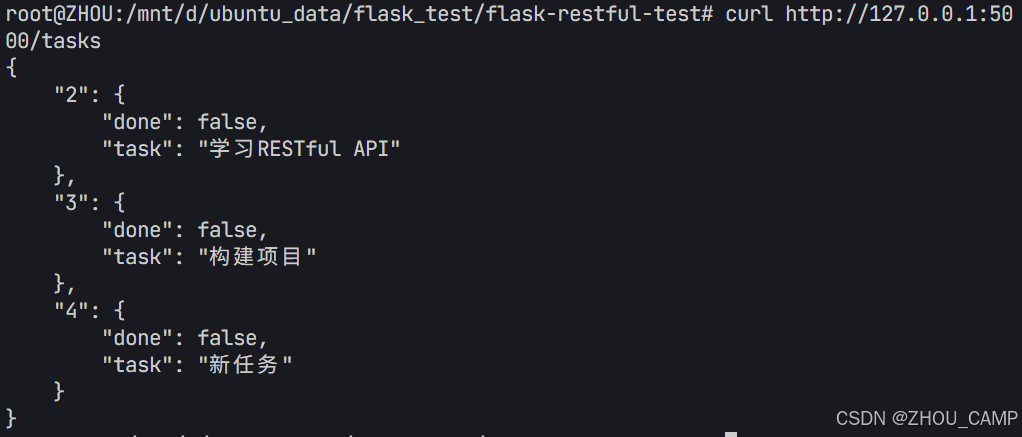
Flask RESTful 示例
目录 1. 环境准备2. 安装依赖3. 修改main.py4. 运行应用5. API使用示例获取所有任务获取单个任务创建新任务更新任务删除任务 中文乱码问题: 下面创建一个简单的Flask RESTful API示例。首先,我们需要创建环境,安装必要的依赖,然后…...
label-studio的使用教程(导入本地路径)
文章目录 1. 准备环境2. 脚本启动2.1 Windows2.2 Linux 3. 安装label-studio机器学习后端3.1 pip安装(推荐)3.2 GitHub仓库安装 4. 后端配置4.1 yolo环境4.2 引入后端模型4.3 修改脚本4.4 启动后端 5. 标注工程5.1 创建工程5.2 配置图片路径5.3 配置工程类型标签5.4 配置模型5.…...

【Java学习笔记】Arrays类
Arrays 类 1. 导入包:import java.util.Arrays 2. 常用方法一览表 方法描述Arrays.toString()返回数组的字符串形式Arrays.sort()排序(自然排序和定制排序)Arrays.binarySearch()通过二分搜索法进行查找(前提:数组是…...

【解密LSTM、GRU如何解决传统RNN梯度消失问题】
解密LSTM与GRU:如何让RNN变得更聪明? 在深度学习的世界里,循环神经网络(RNN)以其卓越的序列数据处理能力广泛应用于自然语言处理、时间序列预测等领域。然而,传统RNN存在的一个严重问题——梯度消失&#…...

论文浅尝 | 基于判别指令微调生成式大语言模型的知识图谱补全方法(ISWC2024)
笔记整理:刘治强,浙江大学硕士生,研究方向为知识图谱表示学习,大语言模型 论文链接:http://arxiv.org/abs/2407.16127 发表会议:ISWC 2024 1. 动机 传统的知识图谱补全(KGC)模型通过…...

基于Docker Compose部署Java微服务项目
一. 创建根项目 根项目(父项目)主要用于依赖管理 一些需要注意的点: 打包方式需要为 pom<modules>里需要注册子模块不要引入maven的打包插件,否则打包时会出问题 <?xml version"1.0" encoding"UTF-8…...

【Web 进阶篇】优雅的接口设计:统一响应、全局异常处理与参数校验
系列回顾: 在上一篇中,我们成功地为应用集成了数据库,并使用 Spring Data JPA 实现了基本的 CRUD API。我们的应用现在能“记忆”数据了!但是,如果你仔细审视那些 API,会发现它们还很“粗糙”:有…...
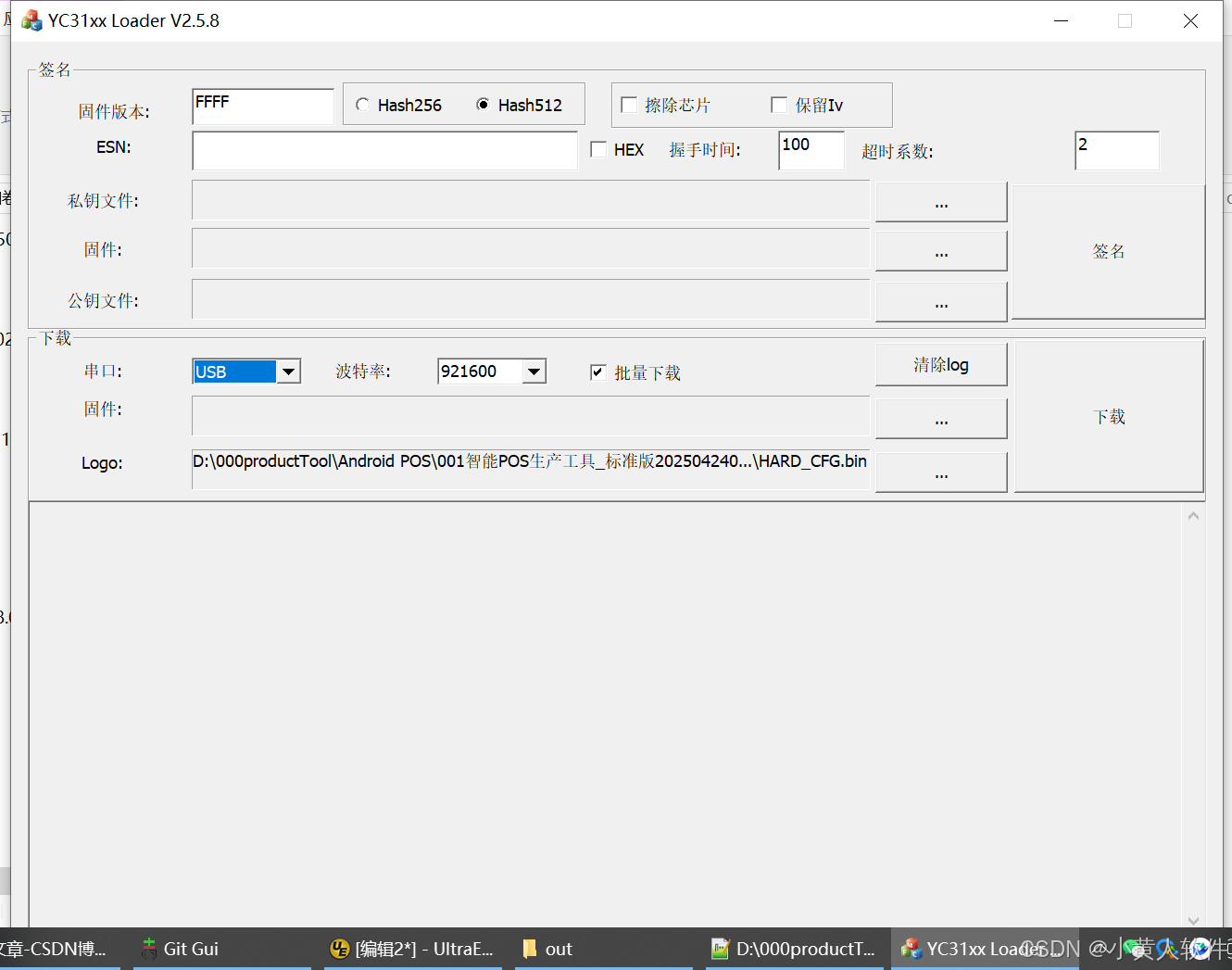
C++ Visual Studio 2017厂商给的源码没有.sln文件 易兆微芯片下载工具加开机动画下载。
1.先用Visual Studio 2017打开Yichip YC31xx loader.vcxproj,再用Visual Studio 2022打开。再保侟就有.sln文件了。 易兆微芯片下载工具加开机动画下载 ExtraDownloadFile1Info.\logo.bin|0|0|10D2000|0 MFC应用兼容CMD 在BOOL CYichipYC31xxloaderDlg::OnIni…...
中的KV缓存压缩与动态稀疏注意力机制设计)
大语言模型(LLM)中的KV缓存压缩与动态稀疏注意力机制设计
随着大语言模型(LLM)参数规模的增长,推理阶段的内存占用和计算复杂度成为核心挑战。传统注意力机制的计算复杂度随序列长度呈二次方增长,而KV缓存的内存消耗可能高达数十GB(例如Llama2-7B处理100K token时需50GB内存&a…...
