C++ 修改防火墙firewall设置(Windows)

文章目录
- 1、简介
- 1.1 防火墙概述
- 1.2 入站,还是出站?
- 1.3 防火墙规则优先级
- 2、系统界面方式
- 3、命令行方式
- 3.1 防火墙基本状态设置
- 3.2 入站出站规则设置
- 3.3 其他设置
- 3.4 telnet检测端口
- 4、C++方式
- 4.1 注册表
- 4.2 COM(Windows XP)
- 4.3 COM(Windows Vista and later)
- 5、VB方式
- 结语
1、简介
防火墙(英语:Firewall)技术是通过有机结合各类用于安全管理与筛选的软件和硬件设备,帮助计算机网络于其内、外网之间构建一道相对隔绝的保护屏障,以保护用户资料与信息安全性的一种技术。
1.1 防火墙概述
所谓“防火墙”是指一种将内部网和公众访问网(如Internet)分开的方法,它实际上是一种建立在现代通信网络技术和信息安全技术基础上的应用性安全技术,隔离技术。越来越多地应用于专用网络与公用网络的互联环境之中,尤其以接入Internet网络为最甚。
1.2 入站,还是出站?
入站是外网的人访问我;出站是我访问外网。
入站开了本机的443端口,意味着外网的人可以通过443端口访问你的HTTPS服务;出站设置一般是允许访问外网IP的443端口。
入站端口:就是别人来访问我的某个端口。比如我设置阻止连接所有站点的入站端口8080,就是所有其他主机不能访问我这台服务器的8080端口。
出站端口:就是我去访问别人的某个端口。比如我设置阻止连接所有站点的出站端口3306,就是我不能访问所有其他网址的3306端口
1.3 防火墙规则优先级
Windows防火墙的规则扫描有它自己特定的顺序,其优先级为:
1、只允许安全连接
2、阻止连接
3、允许连接
4. 默认规则(如果没有设置,那就是默认阻止)
As soon as a network packet matches a rule, that rule is applied, and processing stops. For example, an arriving network packet is first compared to the authenticated bypass rules. If it matches one, that rule is applied and processing stops. The packet is not compared to the block, allow, or default profile rules. If the packet does not match an authenticated bypass rule, then it is compared to the block rules. If it matches one, the packet is blocked, and processing stops, and so on.
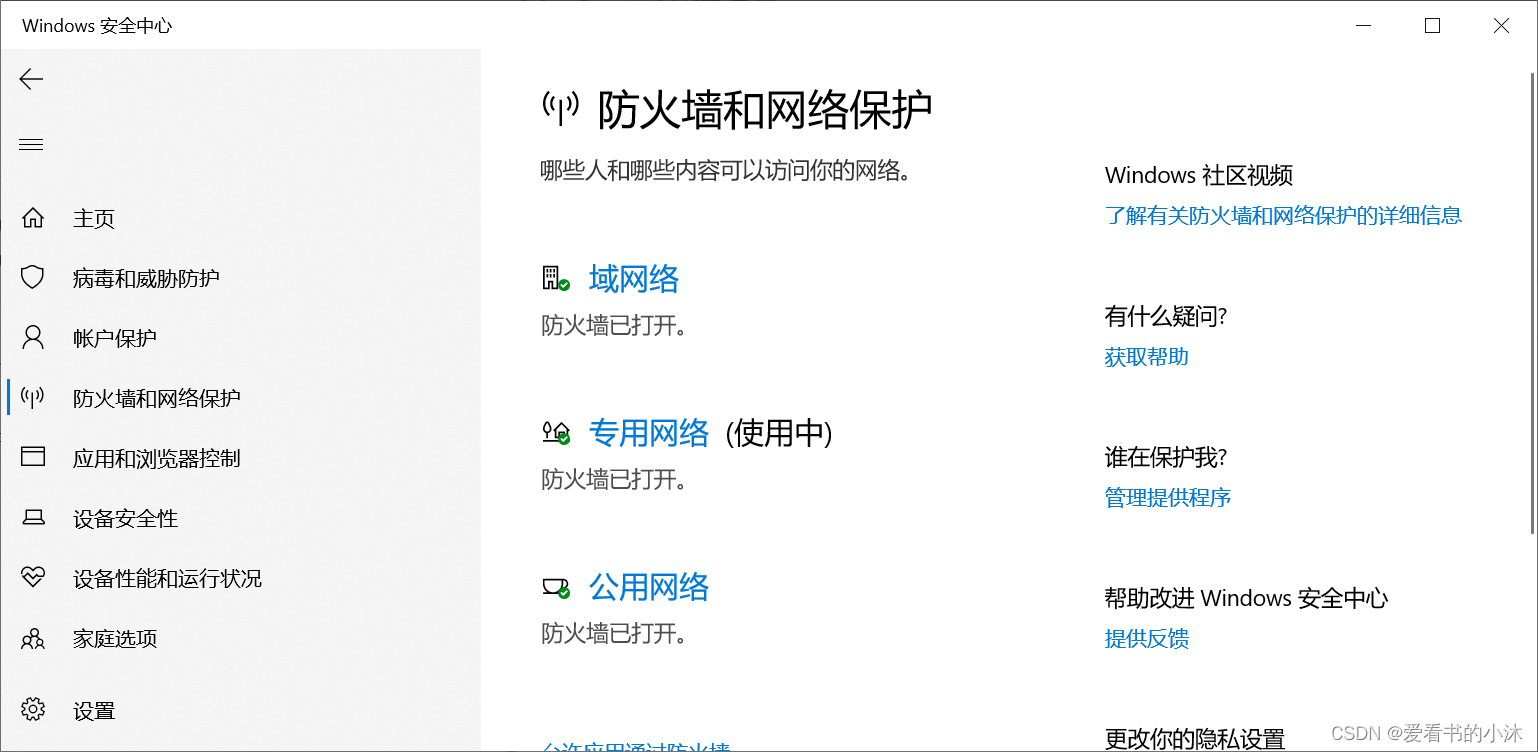
2、系统界面方式
打开控制面板,点击系统和安全。
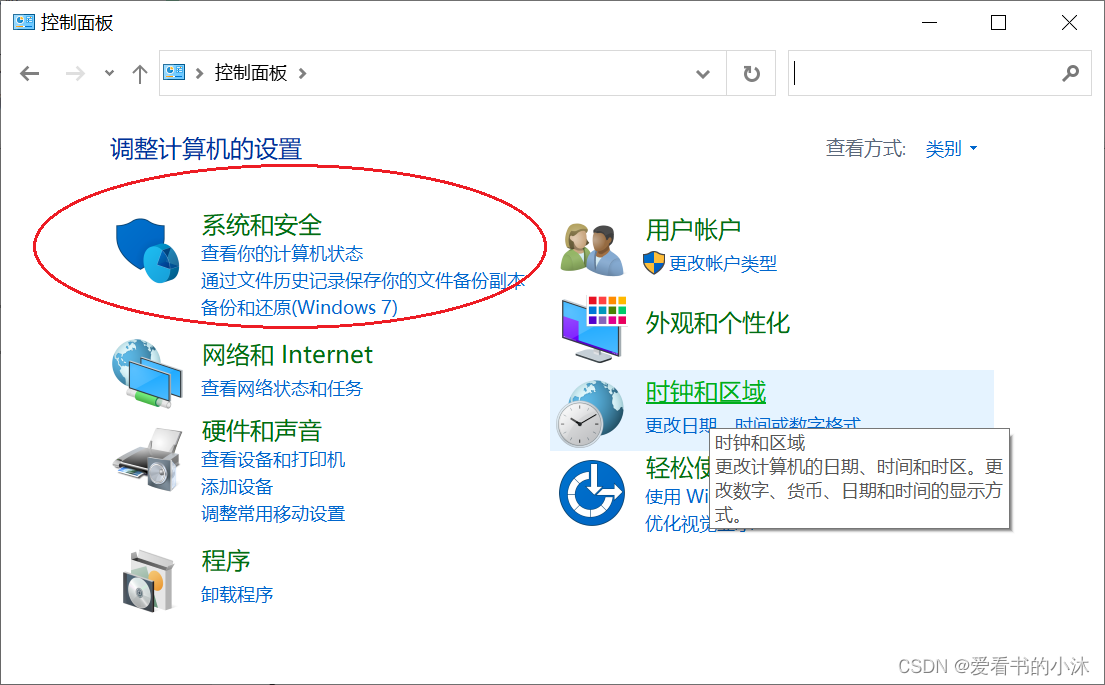
点击Windows Defender防火墙。
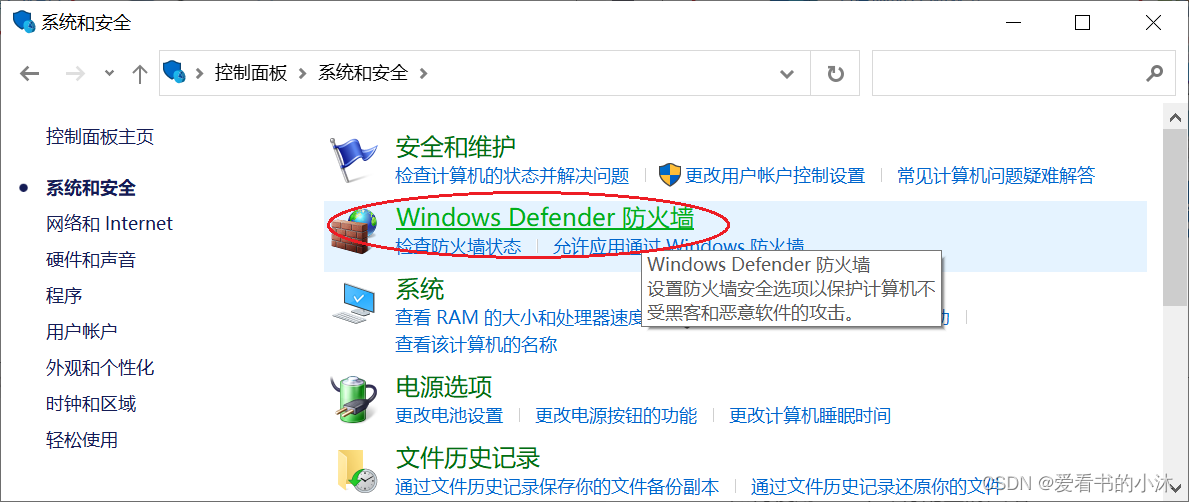
点击右侧的高级设置。
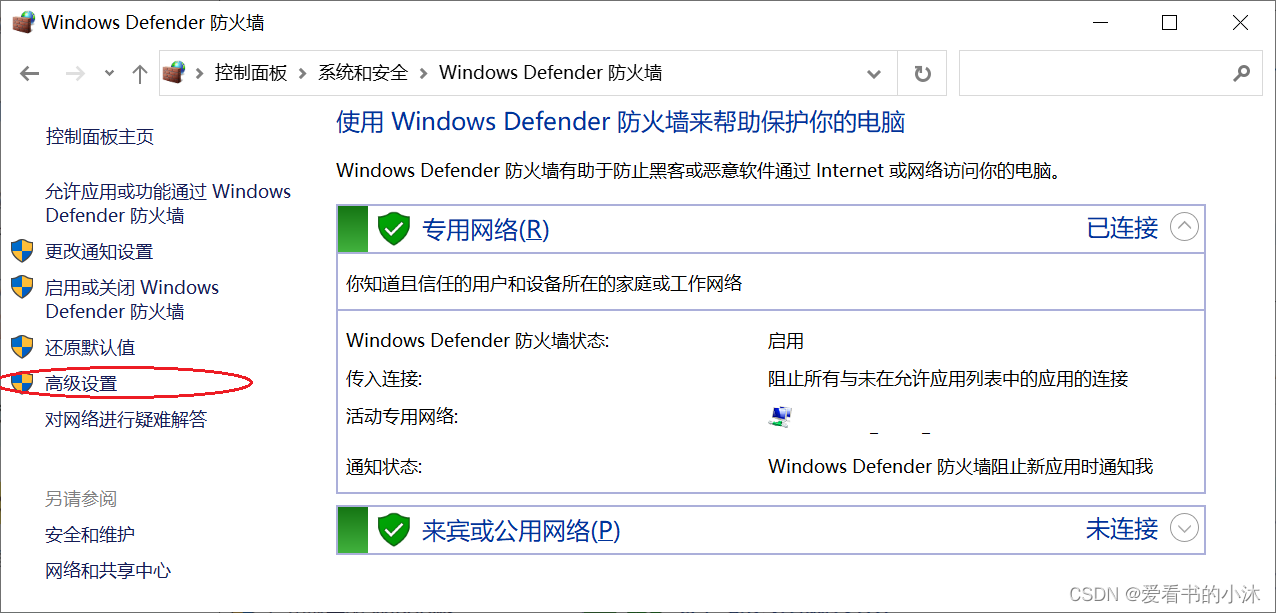
点击入站规则,然后点击右侧的新建规则。
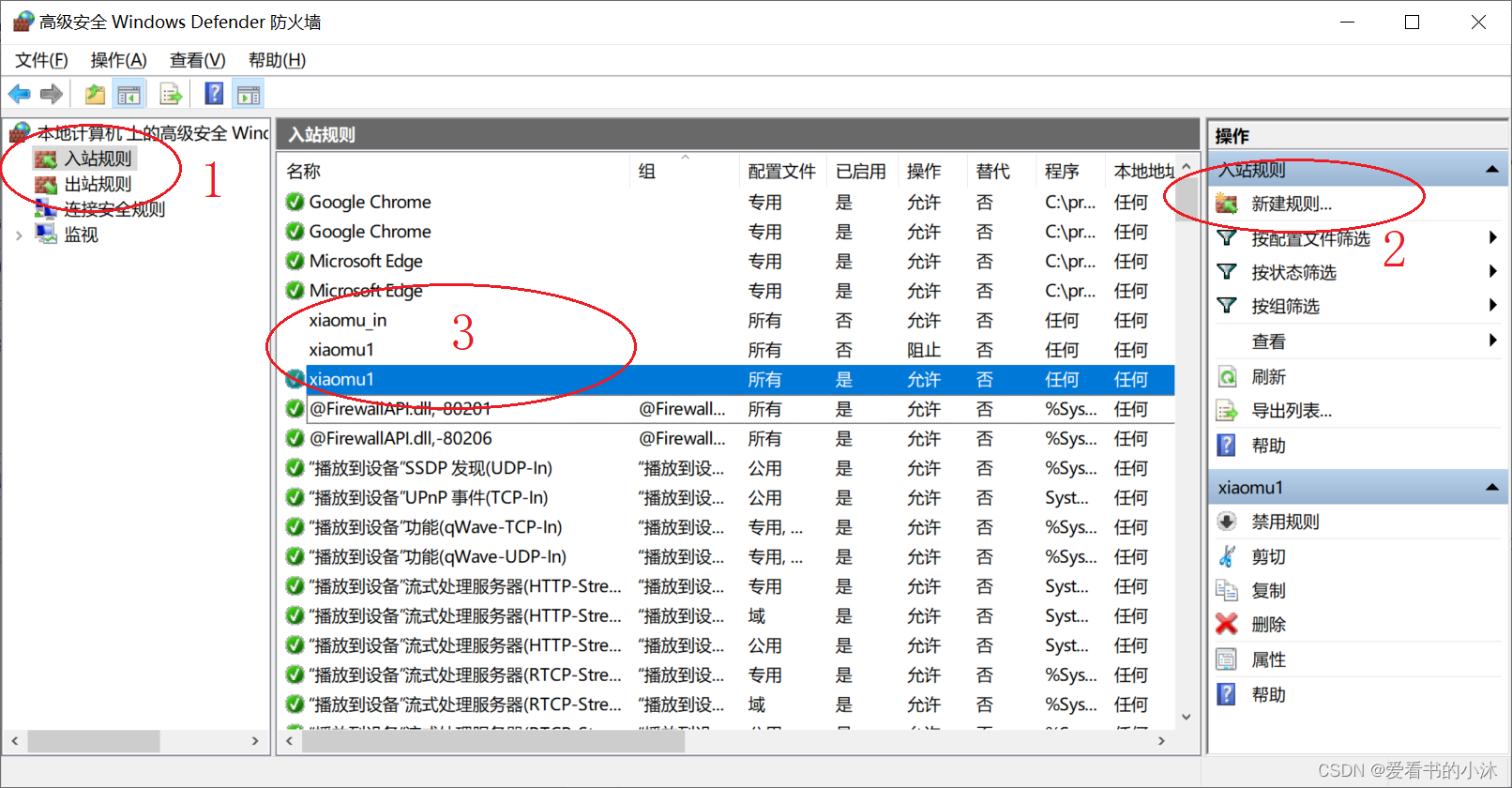
然后勾选端口,点击下一步。
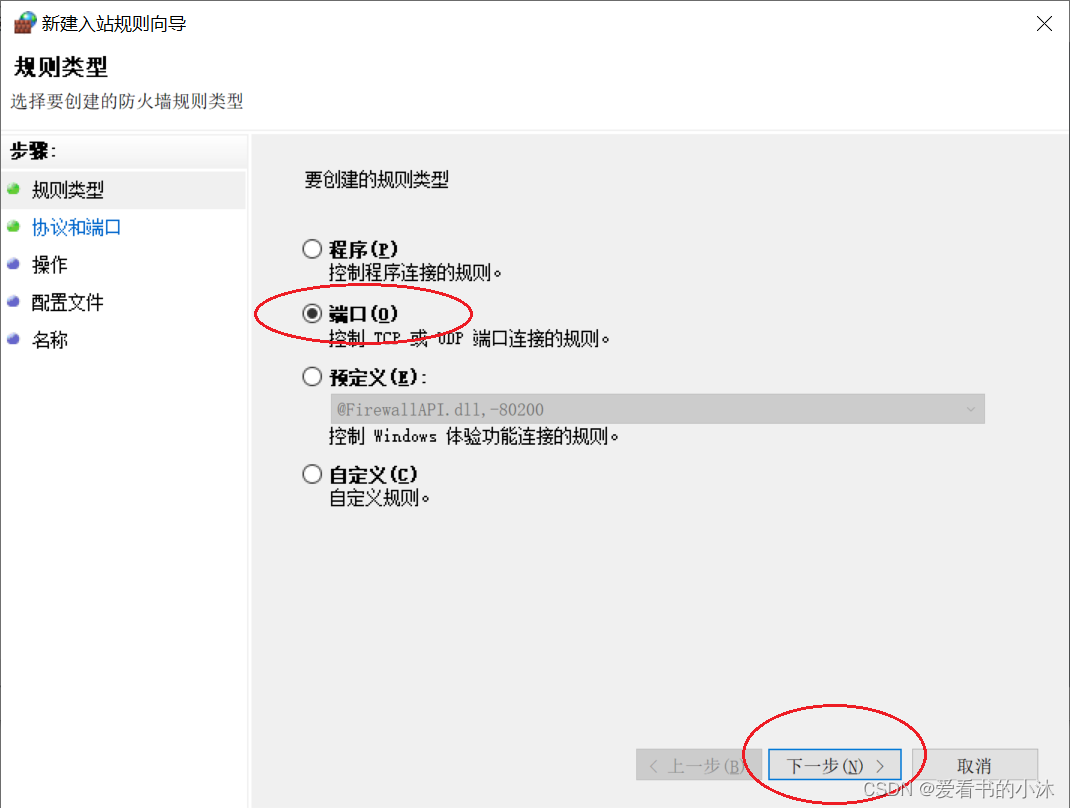
接着填写开放的端口号(如5000)。
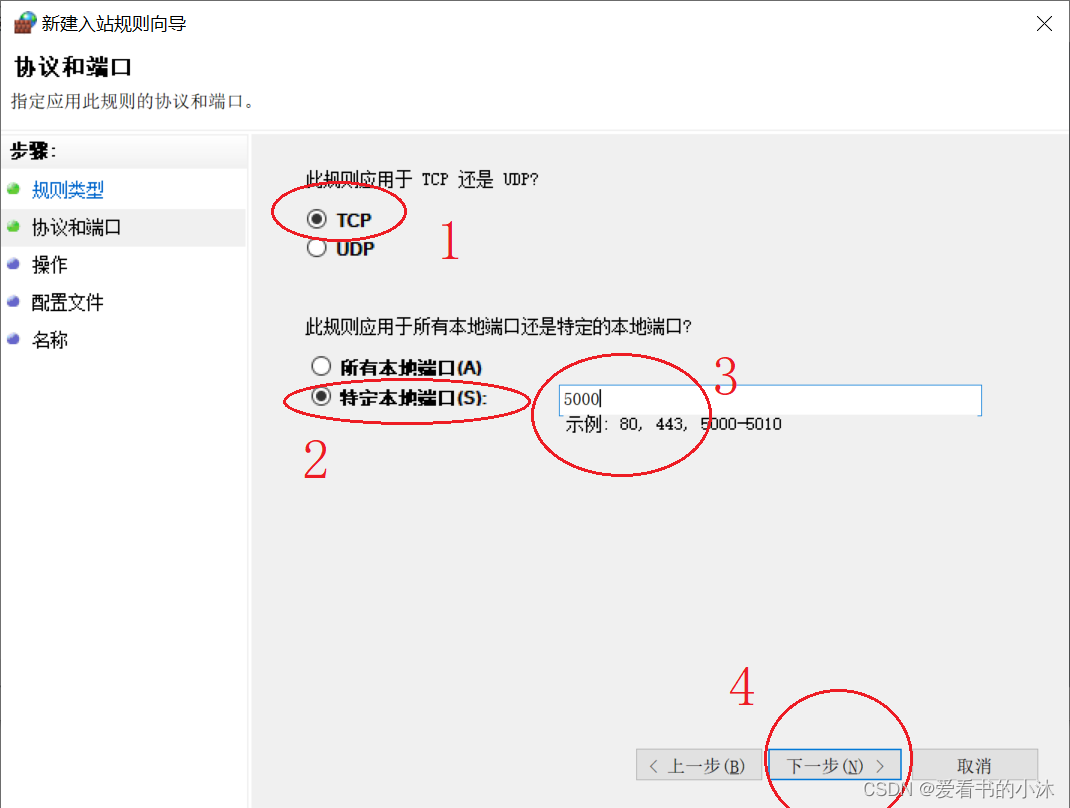
接着如果是允许连接的话,直接点击下一步。
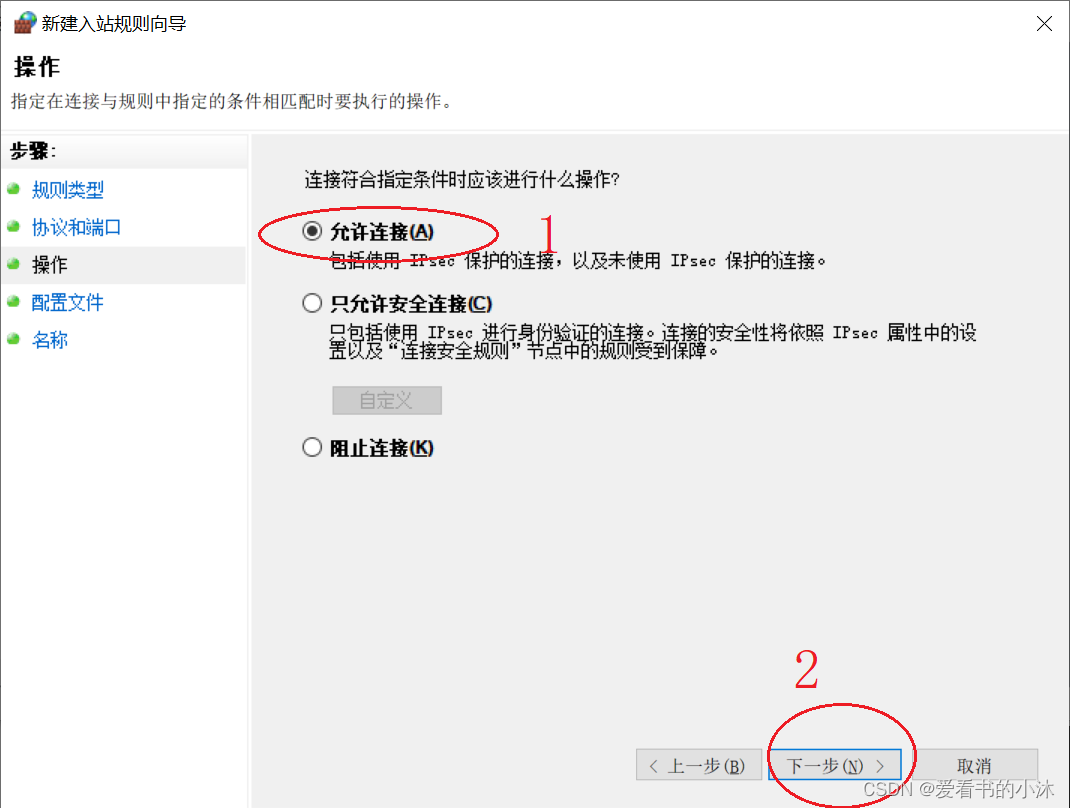
接着直接点击下一步。
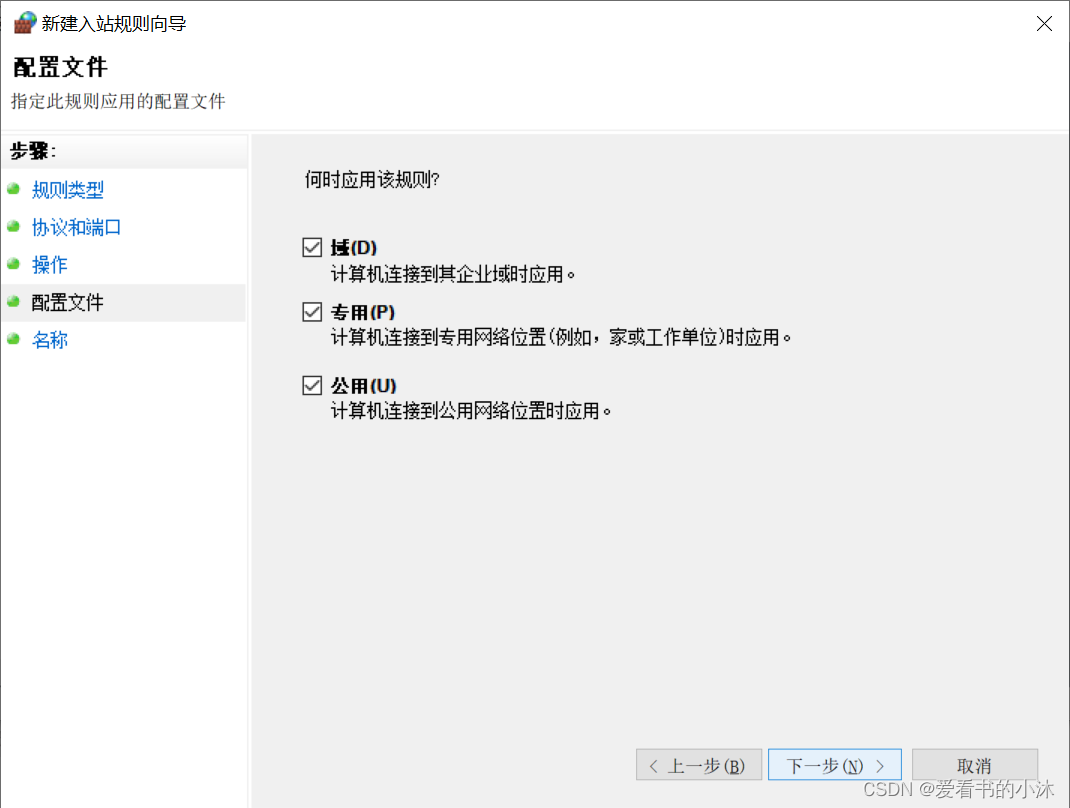
接着填写名字和描述,点击完成。

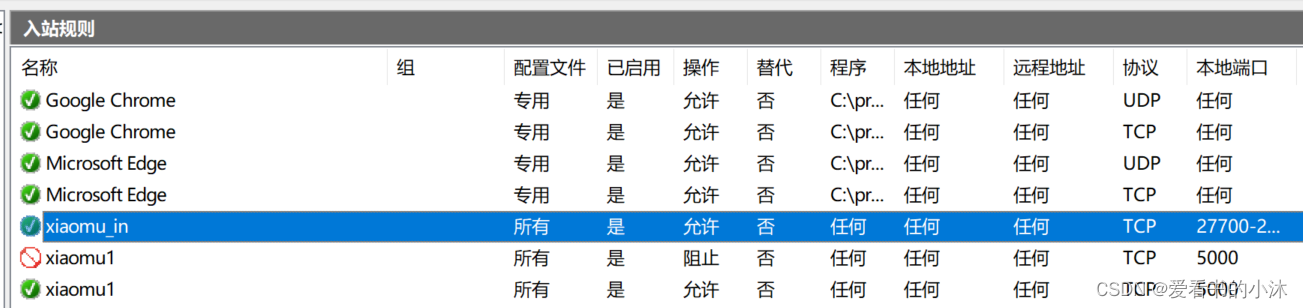
在入站规则中出现了刚才添加的规则。
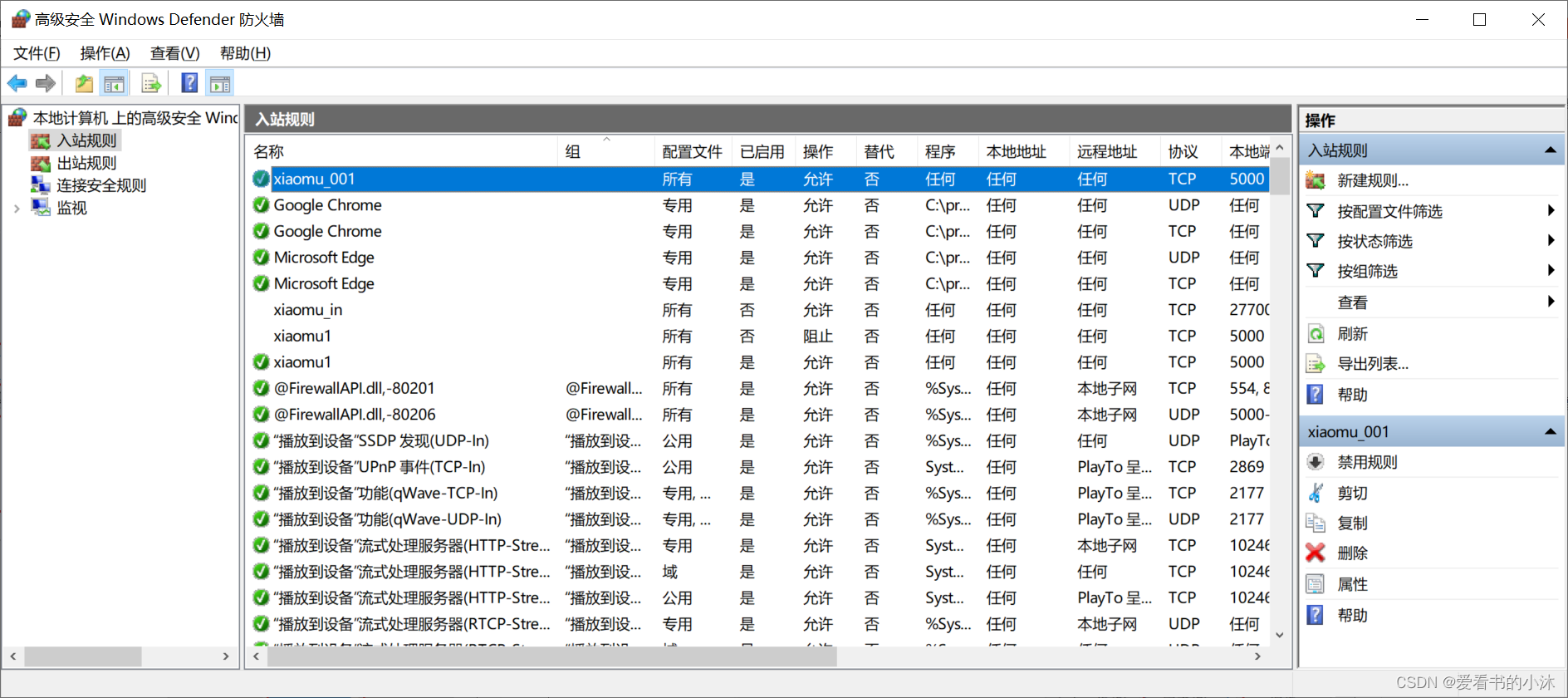
3、命令行方式
Win10 如何使用cmd命令行配置防火墙:
3.1 防火墙基本状态设置
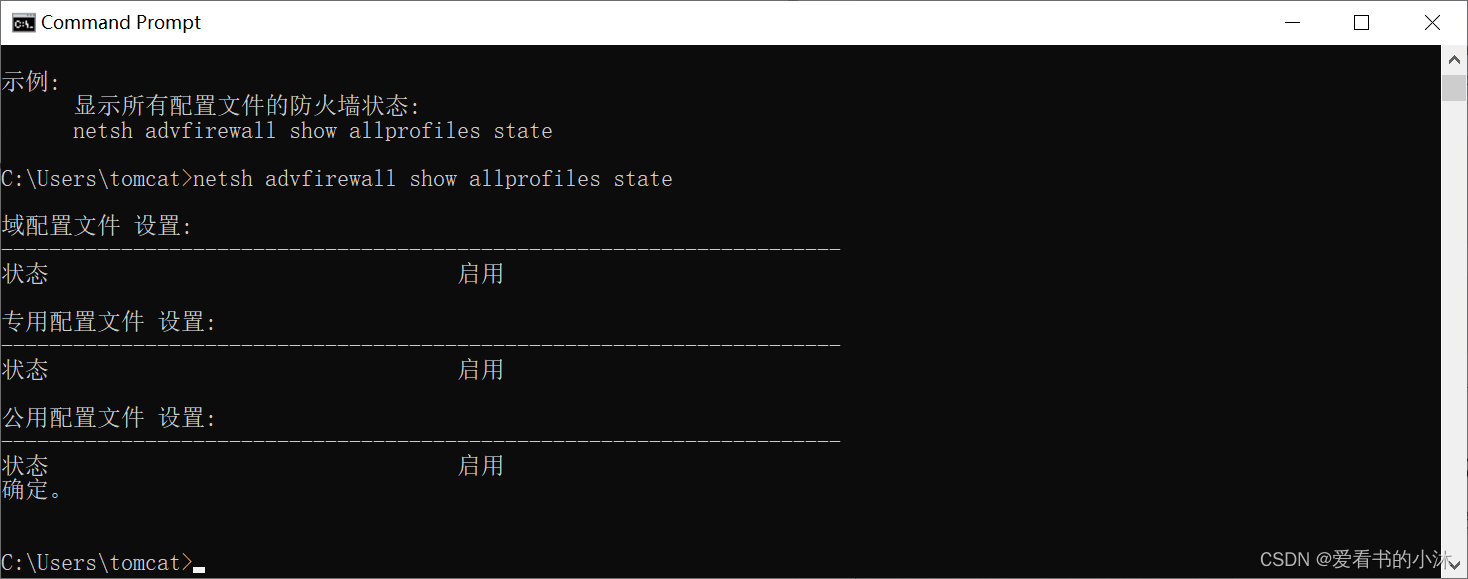
# 查看当前防火墙状态:
netsh advfirewall show allprofiles
netsh advfirewall show allprofiles state
# 恢复初始防火墙设置:
netsh advfirewall reset# 设置默认输入和输出策略:
# 设置为允许
netsh advfirewall set allprofiles firewallpolicy allowinbound,allowoutbound
# 设置为拒绝
netsh advfirewall set allprofiles firewallpolicy blockinbound,blockoutbound
# 显示默认的入站和出站防火墙行为。
netsh advfirewall show allprofiles firewallpolicy


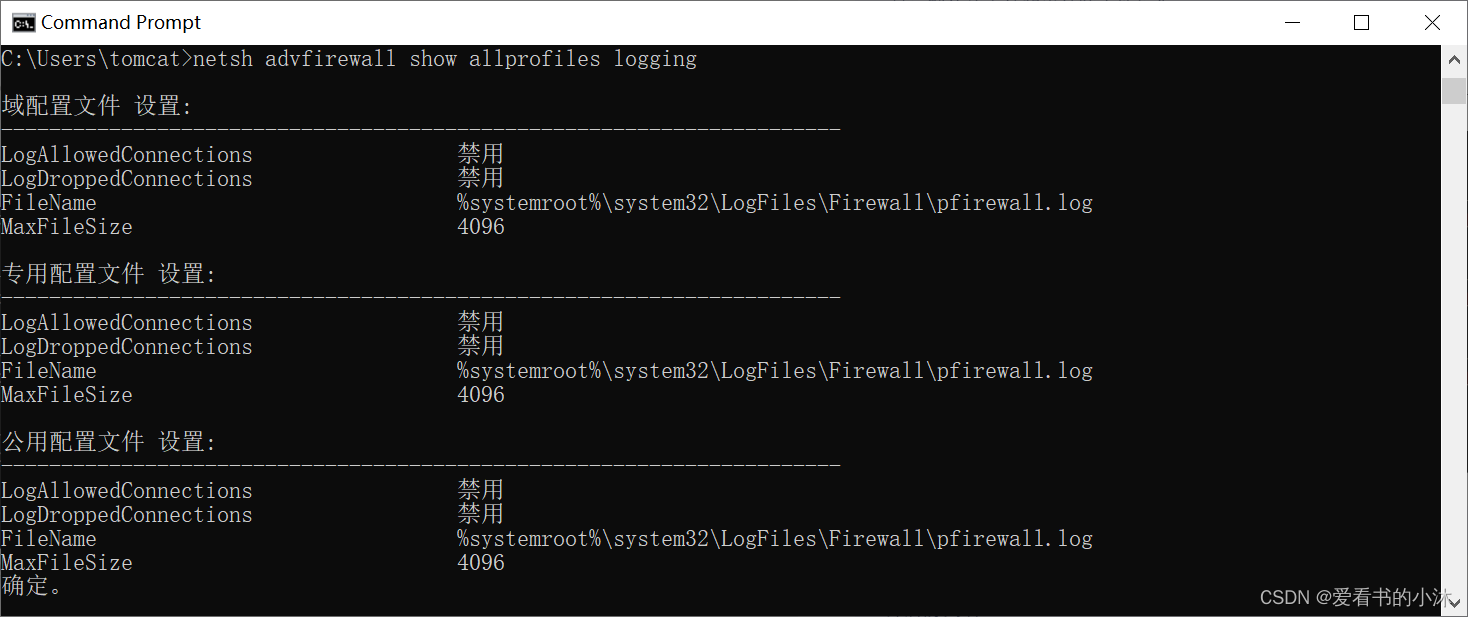
# 显示日志记录设置。
netsh advfirewall show allprofiles logging
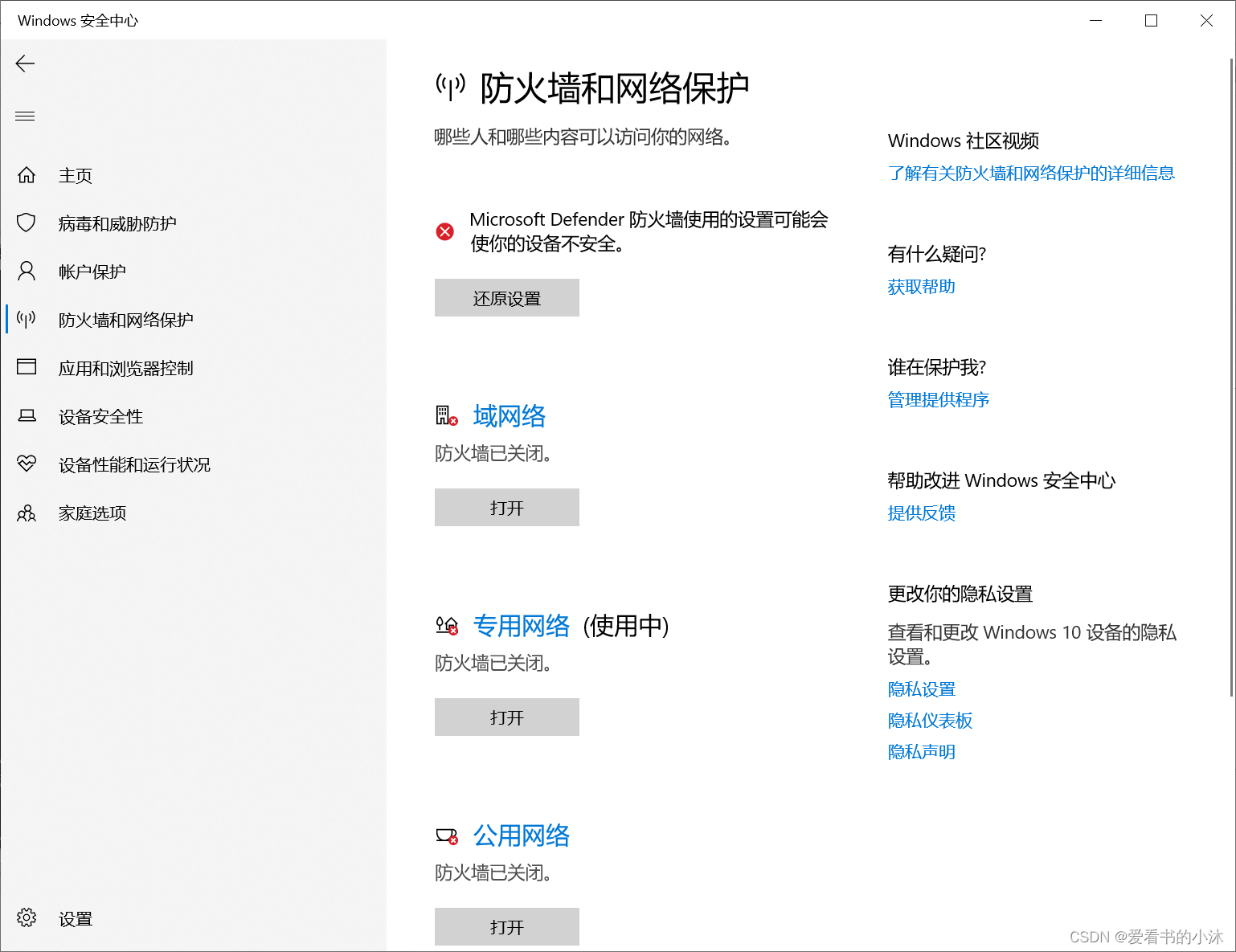
# 开启防火墙:
netsh advfirewall set allprofiles state on
#关闭防火墙:
netsh advfirewall set allprofiles state off
3.2 入站出站规则设置
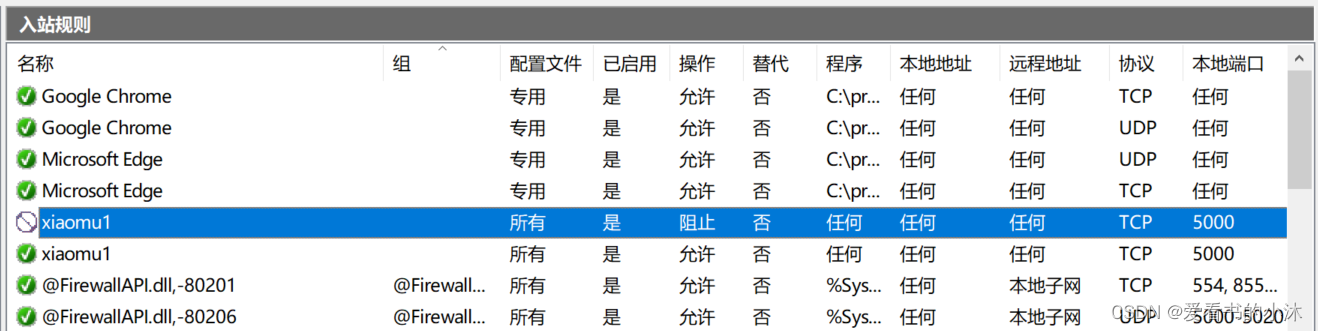
- 添加入站规则
# 允许
netsh advfirewall firewall add rule name=xiaomu1 dir=in action=allow protocol=tcp localport=5000# 阻止
netsh advfirewall firewall add rule name=xiaomu1 dir=in action=block protocol=tcp localport=5000
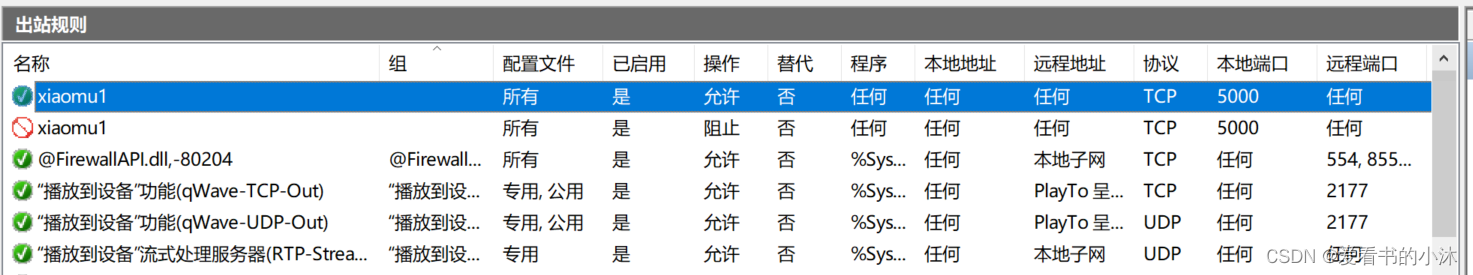
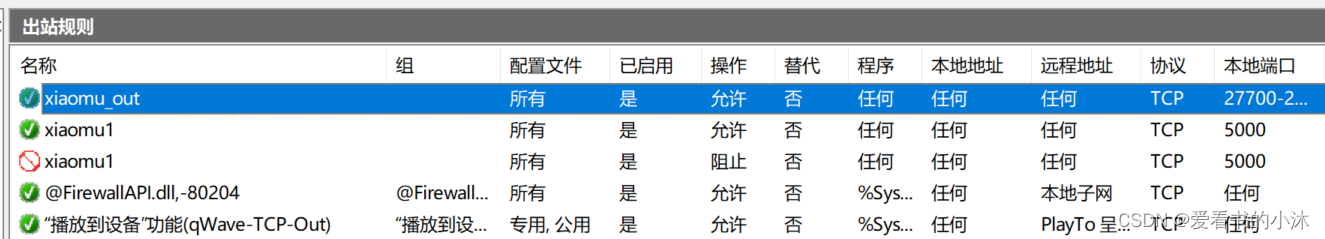
- 添加出站规则
# 允许
netsh advfirewall firewall add rule name=xiaomu1 dir=out action=allow protocol=tcp localport=5000# 阻止
netsh advfirewall firewall add rule name=xiaomu1 dir=out action=block protocol=tcp localport=5000
- 删除入站出站规则
# 删除入站允许
netsh advfirewall firewall delete rule name=test001 dir=in action=allow protocol=tcp localport=445# 删除出站允许
netsh advfirewall firewall delete rule name=test001 dir=out action=allow protocol=tcp localport=445
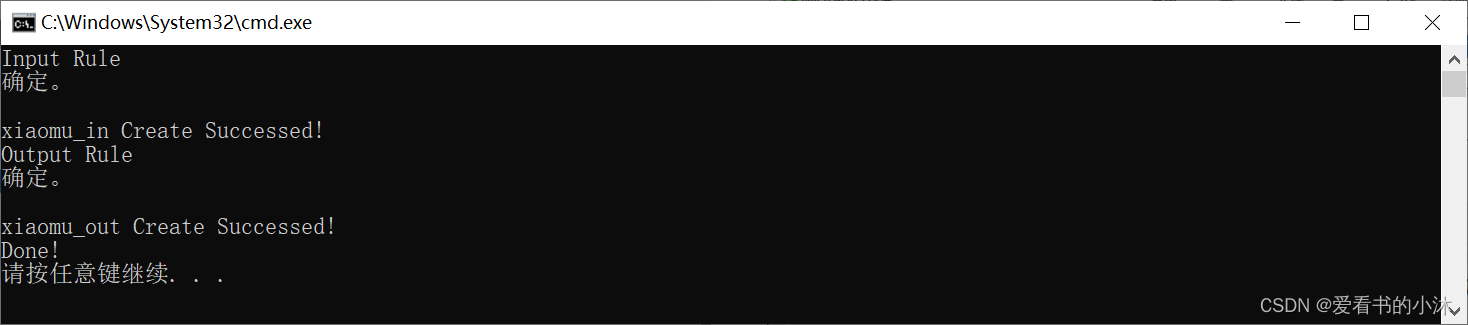
- bat批处理文件实现添加防火墙出入站规则:
@echo offrem 以管理员权限执行命令
%1 mshta vbscript:CreateObject("Shell.Application").ShellExecute("cmd.exe","/c %~s0 ::","","runas",1)(window.close)&&exit
cd /d "%~dp0"rem 设置指定端口变量和出入站规则名称
set INPUT_RULE_NAME=xiaomu_in
set OUT_RULE_NAME=xiaomu_out
set PORT=27700-27702,3316,5000-5010rem 创建入站规则
echo Input Rule
netsh advfirewall firewall show rule name=%INPUT_RULE_NAME% >nul
rem 如果已经存在则先删除
if not ERRORLEVEL 1 (netsh advfirewall firewall delete rule name=%INPUT_RULE_NAME% >nul
)
netsh advfirewall firewall add rule name=%INPUT_RULE_NAME% dir=in action=allow protocol=TCP localport=%PORT%
echo %INPUT_RULE_NAME% Create Successed!rem 创建出站规则
echo Output Rule
netsh advfirewall firewall show rule name=%OUT_RULE_NAME% >nul
rem 如果已经存在则先删除
if not ERRORLEVEL 1 (netsh advfirewall firewall delete rule name=%OUT_RULE_NAME% >nul
)
netsh advfirewall firewall add rule name=%OUT_RULE_NAME% dir=out action=allow protocol=TCP localport=%PORT%
echo %OUT_RULE_NAME% Create Successed!echo Done!
pause
3.3 其他设置
- 允许并阻止ping
您可以使用netsh来控制给定系统如何响应ping请求以及是否响应。以下两个netsh命令显示了如何阻止然后打开Windows防火墙来ping请求:
netsh advfirewall firewall add rule name="All ICMP V4" dir=in action=block protocol=icmpv4
netsh advfirewall firewall add rule name="All ICMP V4" dir=in action=allow protocol=icmpv4
- 启用程序
另一个常见任务是为给定程序打开Windows防火墙。以下示例说明了如何添加使Windows Live Messenger通过Windows防火墙工作的规则:
netsh advfirewall firewall add rule name="Allow Messenger" dir=in action=allow program="C:\programfiles\messenger\msnmsgr.exe"
- 启用远程管理
另一个常见要求(尤其是在设置新系统时)是启用远程管理,以便Microsoft Management Console等工具可以连接到远程系统。要打开Windows防火墙进行远程管理,可以使用以下命令:
netsh advfirewall firewall set rule group="remote administration" new enable=yes
- 启用远程桌面连接
对设置的大多数服务器系统所做的第一件事就是启用远程桌面连接用于轻松的远程系统管理。以下命令显示如何使用netsh打开Windows防火墙进行远程桌面连接:
netsh advfirewall firewall set rule group="remote desktop" new enable=Yes
- 导出和导入防火墙设置文件
配置Windows防火墙后,最好导出设置,以便以后可以轻松地重新应用它们或将其导入另一个系统。
netsh advfirewall export "C:\temp\WFconfiguration.wfw"
netsh advfirewall import "C:\temp\WFconfiguration.wfw"
- 关闭5900端口
netsh advfirewall firewall add rule name= “deny tcp 5900″ dir=in protocol=tcp localport=5900 action=block
- 设置Ip禁止
# remoteip 允许的IP,多个IP用逗号分割
netsh advfirewall firewall add rule name="test" dir=in action=allow protocol=TCP localport=3389,135 remoteip=10.10.12.20,192.168.0.20
3.4 telnet检测端口
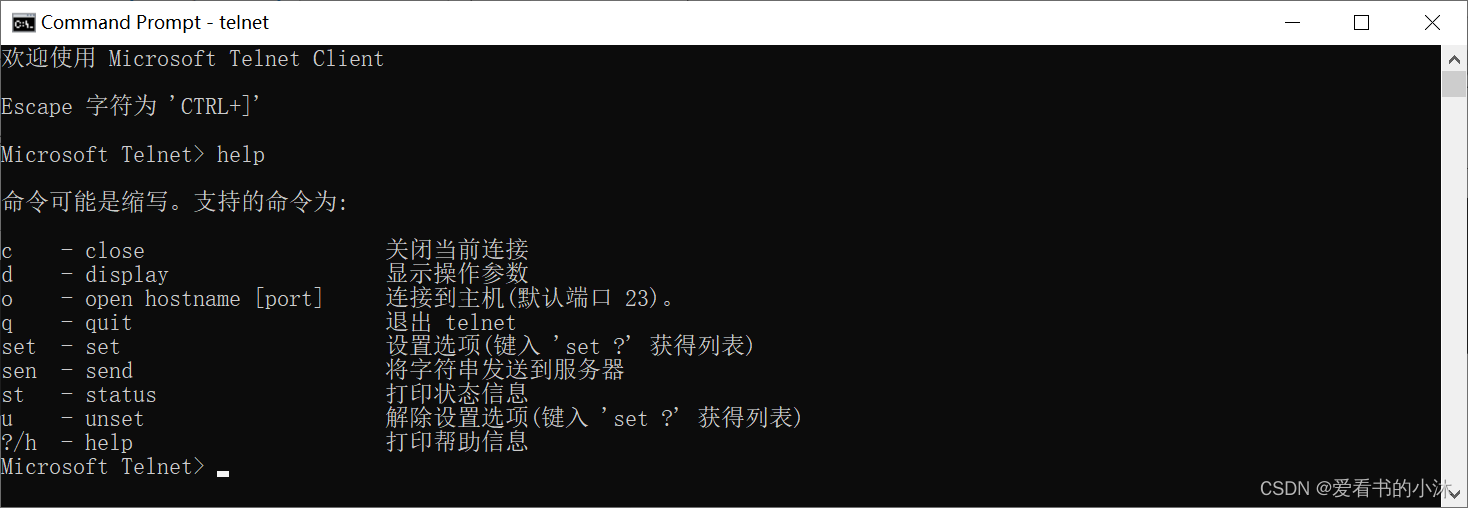
完成之后,可以用telnet测试端口是否开放。
打开命令行窗口,输入命令:telnet 127.0.0.1 5000,如果出现下图的界面就说明该端口已经开放。

如果telnet没有安装的话,请按照如下步骤操作。
使用win+R键打开运行程序,在输入框里输入:OptionalFeatures,点击确定。
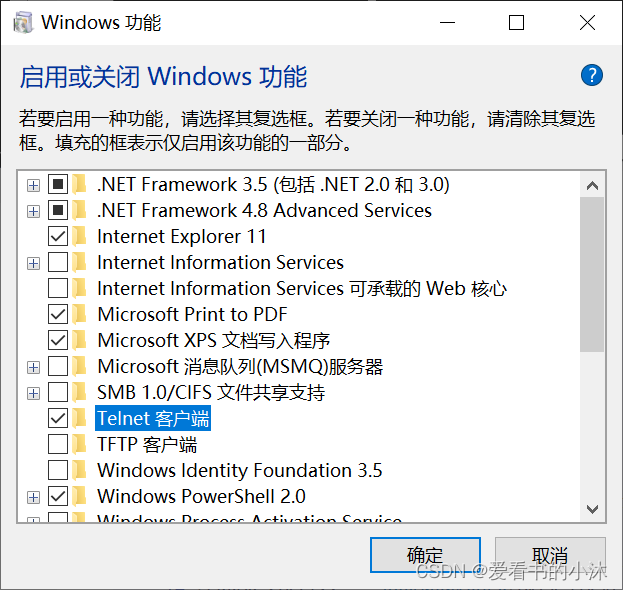
勾选上Telnet客户端并点击确定,就会开始安装telnet客户端。
重新打开一个cmd窗口输入telnet命令,如下所示表明telnet客户端安装成功。
4、C++方式

4.1 注册表
#include <Windows.h>int main(void)
{HKEY hkResult;TCHAR szValueName[MAX_PATH] = { 0 }, szData[1024] = { 0 };DWORD dwValueNameLen = MAX_PATH, dwDataLen = 1024;const TCHAR* lpSubKey = TEXT("SYSTEM\\ControlSet001\\Services\\SharedAccess\\Defaults\\FirewallPolicy\\FirewallRules");if (ERROR_SUCCESS == RegOpenKeyEx(HKEY_LOCAL_MACHINE, lpSubKey, 0, KEY_READ, &hkResult)){for (DWORD i = 0;; i++){if (ERROR_NO_MORE_ITEMS == RegEnumValue(hkResult, i, szValueName, &dwValueNameLen, NULL, NULL, (BYTE*)szData, &dwDataLen)){break;}dwValueNameLen = MAX_PATH;dwDataLen = 1024;}}
}
4.2 COM(Windows XP)
/*Copyright (c) Microsoft CorporationSYNOPSISSample code for the Windows Firewall COM interface.
*/#include <windows.h>
#include <crtdbg.h>
#include <netfw.h>
#include <objbase.h>
#include <oleauto.h>
#include <stdio.h>#pragma comment( lib, "ole32.lib" )
#pragma comment( lib, "oleaut32.lib" )HRESULT WindowsFirewallInitialize(OUT INetFwProfile** fwProfile)
{HRESULT hr = S_OK;INetFwMgr* fwMgr = NULL;INetFwPolicy* fwPolicy = NULL;_ASSERT(fwProfile != NULL);*fwProfile = NULL;// Create an instance of the firewall settings manager.hr = CoCreateInstance(__uuidof(NetFwMgr),NULL,CLSCTX_INPROC_SERVER,__uuidof(INetFwMgr),(void**)&fwMgr);if (FAILED(hr)){printf("CoCreateInstance failed: 0x%08lx\n", hr);goto error;}// Retrieve the local firewall policy.hr = fwMgr->get_LocalPolicy(&fwPolicy);if (FAILED(hr)){printf("get_LocalPolicy failed: 0x%08lx\n", hr);goto error;}// Retrieve the firewall profile currently in effect.hr = fwPolicy->get_CurrentProfile(fwProfile);if (FAILED(hr)){printf("get_CurrentProfile failed: 0x%08lx\n", hr);goto error;}error:// Release the local firewall policy.if (fwPolicy != NULL){fwPolicy->Release();}// Release the firewall settings manager.if (fwMgr != NULL){fwMgr->Release();}return hr;
}void WindowsFirewallCleanup(IN INetFwProfile* fwProfile)
{// Release the firewall profile.if (fwProfile != NULL){fwProfile->Release();}
}HRESULT WindowsFirewallIsOn(IN INetFwProfile* fwProfile, OUT BOOL* fwOn)
{HRESULT hr = S_OK;VARIANT_BOOL fwEnabled;_ASSERT(fwProfile != NULL);_ASSERT(fwOn != NULL);*fwOn = FALSE;// Get the current state of the firewall.hr = fwProfile->get_FirewallEnabled(&fwEnabled);if (FAILED(hr)){printf("get_FirewallEnabled failed: 0x%08lx\n", hr);goto error;}// Check to see if the firewall is on.if (fwEnabled != VARIANT_FALSE){*fwOn = TRUE;printf("The firewall is on.\n");}else{printf("The firewall is off.\n");}error:return hr;
}HRESULT WindowsFirewallTurnOn(IN INetFwProfile* fwProfile)
{HRESULT hr = S_OK;BOOL fwOn;_ASSERT(fwProfile != NULL);// Check to see if the firewall is off.hr = WindowsFirewallIsOn(fwProfile, &fwOn);if (FAILED(hr)){printf("WindowsFirewallIsOn failed: 0x%08lx\n", hr);goto error;}// If it is, turn it on.if (!fwOn){// Turn the firewall on.hr = fwProfile->put_FirewallEnabled(VARIANT_TRUE);if (FAILED(hr)){printf("put_FirewallEnabled failed: 0x%08lx\n", hr);goto error;}printf("The firewall is now on.\n");}error:return hr;
}HRESULT WindowsFirewallTurnOff(IN INetFwProfile* fwProfile)
{HRESULT hr = S_OK;BOOL fwOn;_ASSERT(fwProfile != NULL);// Check to see if the firewall is on.hr = WindowsFirewallIsOn(fwProfile, &fwOn);if (FAILED(hr)){printf("WindowsFirewallIsOn failed: 0x%08lx\n", hr);goto error;}// If it is, turn it off.if (fwOn){// Turn the firewall off.hr = fwProfile->put_FirewallEnabled(VARIANT_FALSE);if (FAILED(hr)){printf("put_FirewallEnabled failed: 0x%08lx\n", hr);goto error;}printf("The firewall is now off.\n");}error:return hr;
}HRESULT WindowsFirewallAppIsEnabled(IN INetFwProfile* fwProfile,IN const wchar_t* fwProcessImageFileName,OUT BOOL* fwAppEnabled
)
{HRESULT hr = S_OK;BSTR fwBstrProcessImageFileName = NULL;VARIANT_BOOL fwEnabled;INetFwAuthorizedApplication* fwApp = NULL;INetFwAuthorizedApplications* fwApps = NULL;_ASSERT(fwProfile != NULL);_ASSERT(fwProcessImageFileName != NULL);_ASSERT(fwAppEnabled != NULL);*fwAppEnabled = FALSE;// Retrieve the authorized application collection.hr = fwProfile->get_AuthorizedApplications(&fwApps);if (FAILED(hr)){printf("get_AuthorizedApplications failed: 0x%08lx\n", hr);goto error;}// Allocate a BSTR for the process image file name.fwBstrProcessImageFileName = SysAllocString(fwProcessImageFileName);if (fwBstrProcessImageFileName == NULL){hr = E_OUTOFMEMORY;printf("SysAllocString failed: 0x%08lx\n", hr);goto error;}// Attempt to retrieve the authorized application.hr = fwApps->Item(fwBstrProcessImageFileName, &fwApp);if (SUCCEEDED(hr)){// Find out if the authorized application is enabled.hr = fwApp->get_Enabled(&fwEnabled);if (FAILED(hr)){printf("get_Enabled failed: 0x%08lx\n", hr);goto error;}if (fwEnabled != VARIANT_FALSE){// The authorized application is enabled.*fwAppEnabled = TRUE;printf("Authorized application %lS is enabled in the firewall.\n",fwProcessImageFileName);}else{printf("Authorized application %lS is disabled in the firewall.\n",fwProcessImageFileName);}}else{// The authorized application was not in the collection.hr = S_OK;printf("Authorized application %lS is disabled in the firewall.\n",fwProcessImageFileName);}error:// Free the BSTR.SysFreeString(fwBstrProcessImageFileName);// Release the authorized application instance.if (fwApp != NULL){fwApp->Release();}// Release the authorized application collection.if (fwApps != NULL){fwApps->Release();}return hr;
}HRESULT WindowsFirewallAddApp(IN INetFwProfile* fwProfile,IN const wchar_t* fwProcessImageFileName,IN const wchar_t* fwName
)
{HRESULT hr = S_OK;BOOL fwAppEnabled;BSTR fwBstrName = NULL;BSTR fwBstrProcessImageFileName = NULL;INetFwAuthorizedApplication* fwApp = NULL;INetFwAuthorizedApplications* fwApps = NULL;_ASSERT(fwProfile != NULL);_ASSERT(fwProcessImageFileName != NULL);_ASSERT(fwName != NULL);// First check to see if the application is already authorized.hr = WindowsFirewallAppIsEnabled(fwProfile,fwProcessImageFileName,&fwAppEnabled);if (FAILED(hr)){printf("WindowsFirewallAppIsEnabled failed: 0x%08lx\n", hr);goto error;}// Only add the application if it isn't already authorized.if (!fwAppEnabled){// Retrieve the authorized application collection.hr = fwProfile->get_AuthorizedApplications(&fwApps);if (FAILED(hr)){printf("get_AuthorizedApplications failed: 0x%08lx\n", hr);goto error;}// Create an instance of an authorized application.hr = CoCreateInstance(__uuidof(NetFwAuthorizedApplication),NULL,CLSCTX_INPROC_SERVER,__uuidof(INetFwAuthorizedApplication),(void**)&fwApp);if (FAILED(hr)){printf("CoCreateInstance failed: 0x%08lx\n", hr);goto error;}// Allocate a BSTR for the process image file name.fwBstrProcessImageFileName = SysAllocString(fwProcessImageFileName);if (fwBstrProcessImageFileName == NULL){hr = E_OUTOFMEMORY;printf("SysAllocString failed: 0x%08lx\n", hr);goto error;}// Set the process image file name.hr = fwApp->put_ProcessImageFileName(fwBstrProcessImageFileName);if (FAILED(hr)){printf("put_ProcessImageFileName failed: 0x%08lx\n", hr);goto error;}// Allocate a BSTR for the application friendly name.fwBstrName = SysAllocString(fwName);if (SysStringLen(fwBstrName) == 0){hr = E_OUTOFMEMORY;printf("SysAllocString failed: 0x%08lx\n", hr);goto error;}// Set the application friendly name.hr = fwApp->put_Name(fwBstrName);if (FAILED(hr)){printf("put_Name failed: 0x%08lx\n", hr);goto error;}// Add the application to the collection.hr = fwApps->Add(fwApp);if (FAILED(hr)){printf("Add failed: 0x%08lx\n", hr);goto error;}printf("Authorized application %lS is now enabled in the firewall.\n",fwProcessImageFileName);}error:// Free the BSTRs.SysFreeString(fwBstrName);SysFreeString(fwBstrProcessImageFileName);// Release the authorized application instance.if (fwApp != NULL){fwApp->Release();}// Release the authorized application collection.if (fwApps != NULL){fwApps->Release();}return hr;
}HRESULT WindowsFirewallPortIsEnabled(IN INetFwProfile* fwProfile,IN LONG portNumber,IN NET_FW_IP_PROTOCOL ipProtocol,OUT BOOL* fwPortEnabled
)
{HRESULT hr = S_OK;VARIANT_BOOL fwEnabled;INetFwOpenPort* fwOpenPort = NULL;INetFwOpenPorts* fwOpenPorts = NULL;_ASSERT(fwProfile != NULL);_ASSERT(fwPortEnabled != NULL);*fwPortEnabled = FALSE;// Retrieve the globally open ports collection.hr = fwProfile->get_GloballyOpenPorts(&fwOpenPorts);if (FAILED(hr)){printf("get_GloballyOpenPorts failed: 0x%08lx\n", hr);goto error;}// Attempt to retrieve the globally open port.hr = fwOpenPorts->Item(portNumber, ipProtocol, &fwOpenPort);if (SUCCEEDED(hr)){// Find out if the globally open port is enabled.hr = fwOpenPort->get_Enabled(&fwEnabled);if (FAILED(hr)){printf("get_Enabled failed: 0x%08lx\n", hr);goto error;}if (fwEnabled != VARIANT_FALSE){// The globally open port is enabled.*fwPortEnabled = TRUE;printf("Port %ld is open in the firewall.\n", portNumber);}else{printf("Port %ld is not open in the firewall.\n", portNumber);}}else{// The globally open port was not in the collection.hr = S_OK;printf("Port %ld is not open in the firewall.\n", portNumber);}error:// Release the globally open port.if (fwOpenPort != NULL){fwOpenPort->Release();}// Release the globally open ports collection.if (fwOpenPorts != NULL){fwOpenPorts->Release();}return hr;
}HRESULT WindowsFirewallPortAdd(IN INetFwProfile* fwProfile,IN LONG portNumber,IN NET_FW_IP_PROTOCOL ipProtocol,IN const wchar_t* name
)
{HRESULT hr = S_OK;BOOL fwPortEnabled;BSTR fwBstrName = NULL;INetFwOpenPort* fwOpenPort = NULL;INetFwOpenPorts* fwOpenPorts = NULL;_ASSERT(fwProfile != NULL);_ASSERT(name != NULL);// First check to see if the port is already added.hr = WindowsFirewallPortIsEnabled(fwProfile,portNumber,ipProtocol,&fwPortEnabled);if (FAILED(hr)){printf("WindowsFirewallPortIsEnabled failed: 0x%08lx\n", hr);goto error;}// Only add the port if it isn't already added.if (!fwPortEnabled){// Retrieve the collection of globally open ports.hr = fwProfile->get_GloballyOpenPorts(&fwOpenPorts);if (FAILED(hr)){printf("get_GloballyOpenPorts failed: 0x%08lx\n", hr);goto error;}// Create an instance of an open port.hr = CoCreateInstance(__uuidof(NetFwOpenPort),NULL,CLSCTX_INPROC_SERVER,__uuidof(INetFwOpenPort),(void**)&fwOpenPort);if (FAILED(hr)){printf("CoCreateInstance failed: 0x%08lx\n", hr);goto error;}// Set the port number.hr = fwOpenPort->put_Port(portNumber);if (FAILED(hr)){printf("put_Port failed: 0x%08lx\n", hr);goto error;}// Set the IP protocol.hr = fwOpenPort->put_Protocol(ipProtocol);if (FAILED(hr)){printf("put_Protocol failed: 0x%08lx\n", hr);goto error;}// Allocate a BSTR for the friendly name of the port.fwBstrName = SysAllocString(name);if (SysStringLen(fwBstrName) == 0){hr = E_OUTOFMEMORY;printf("SysAllocString failed: 0x%08lx\n", hr);goto error;}// Set the friendly name of the port.hr = fwOpenPort->put_Name(fwBstrName);if (FAILED(hr)){printf("put_Name failed: 0x%08lx\n", hr);goto error;}// Opens the port and adds it to the collection.hr = fwOpenPorts->Add(fwOpenPort);if (FAILED(hr)){printf("Add failed: 0x%08lx\n", hr);goto error;}printf("Port %ld is now open in the firewall.\n", portNumber);}error:// Free the BSTR.SysFreeString(fwBstrName);// Release the open port instance.if (fwOpenPort != NULL){fwOpenPort->Release();}// Release the globally open ports collection.if (fwOpenPorts != NULL){fwOpenPorts->Release();}return hr;
}int __cdecl wmain(int argc, wchar_t* argv[])
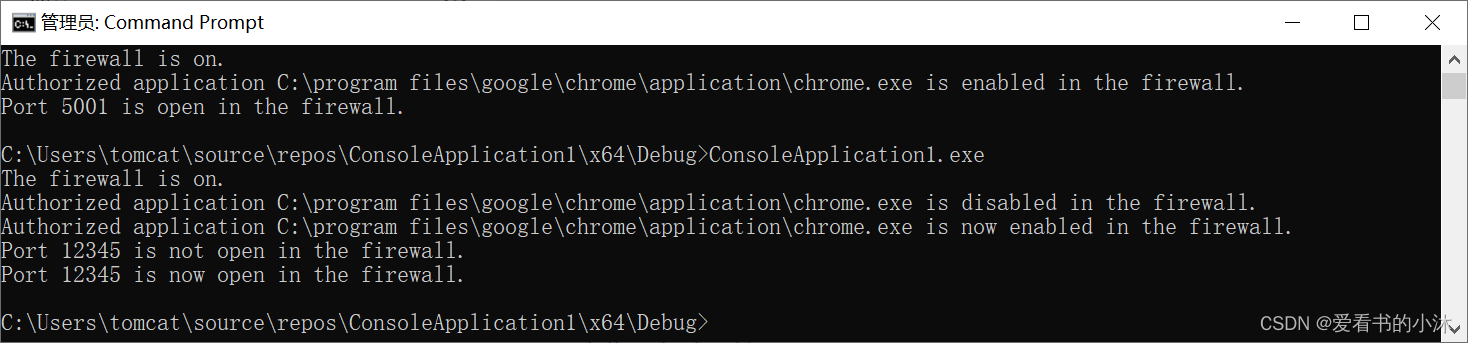
{HRESULT hr = S_OK;HRESULT comInit = E_FAIL;INetFwProfile* fwProfile = NULL;// Initialize COM.comInit = CoInitializeEx(0,COINIT_APARTMENTTHREADED | COINIT_DISABLE_OLE1DDE);// Ignore RPC_E_CHANGED_MODE; this just means that COM has already been// initialized with a different mode. Since we don't care what the mode is,// we'll just use the existing mode.if (comInit != RPC_E_CHANGED_MODE){hr = comInit;if (FAILED(hr)){printf("CoInitializeEx failed: 0x%08lx\n", hr);goto error;}}// Retrieve the firewall profile currently in effect.hr = WindowsFirewallInitialize(&fwProfile);if (FAILED(hr)){printf("WindowsFirewallInitialize failed: 0x%08lx\n", hr);goto error;}// Turn off the firewall./*hr = WindowsFirewallTurnOff(fwProfile);if (FAILED(hr)){printf("WindowsFirewallTurnOff failed: 0x%08lx\n", hr);goto error;}*/// Turn on the firewall.hr = WindowsFirewallTurnOn(fwProfile);if (FAILED(hr)){printf("WindowsFirewallTurnOn failed: 0x%08lx\n", hr);goto error;}// Add Windows Messenger to the authorized application collection.hr = WindowsFirewallAddApp(fwProfile,//L"%ProgramFiles%\\Messenger\\msmsgs.exe",L"C:\\program files\\google\\chrome\\application\\chrome.exe",L"XiaoMu_add_exe");if (FAILED(hr)){printf("WindowsFirewallAddApp failed: 0x%08lx\n", hr);goto error;}// Add TCP::80 to list of globally open ports.hr = WindowsFirewallPortAdd(fwProfile, 12345, NET_FW_IP_PROTOCOL_TCP, L"XiaoMu_add_tcp");if (FAILED(hr)){printf("WindowsFirewallPortAdd failed: 0x%08lx\n", hr);goto error;}error:// Release the firewall profile.WindowsFirewallCleanup(fwProfile);// Uninitialize COM.if (SUCCEEDED(comInit)){CoUninitialize();}return 0;
}
4.3 COM(Windows Vista and later)
高级安全 Windows 防火墙和此处记录的相关防火墙技术使开发人员能够共享 Internet 连接、使用防火墙保护连接并提供网络地址转换 (NAT)。
微软已经发布了几个版本的防火墙产品,每个版本都建立在以前的技术之上。当前版本“高级安全 Windows 防火墙”允许创建极其具体的防火墙规则。
-
具体技术如下(此处从最新到最旧列出):
- 高级安全 Windows 防火墙是最新版本。它最初与Windows Vista一起发布。
- Windows Firewall 最初是作为 Windows XP Service Pack 2 (SP2) 的一个组件发布的。
- IPv6 Internet Connection Firewall 作为 Windows XP 高级网络包的组件发布。它在后续版本的 Windows 中不可用。
- Internet 连接共享和 Internet 连接防火墙最初是在 Windows XP 中发布的,在 Windows Vista 中受支持。它可能在后续版本的 Windows 中被更改或不可用。
-
添加防火墙规则
This C++ file includes sample code that adds a LAN rule to the
currently active profiles using the Microsoft Windows Firewall
APIs.
#include <windows.h>
#include <stdio.h>
#include <netfw.h>#pragma comment( lib, "ole32.lib" )
#pragma comment( lib, "oleaut32.lib" )// Forward declarations
HRESULT WFCOMInitialize(INetFwPolicy2** ppNetFwPolicy2);// Instantiate INetFwPolicy2
HRESULT WFCOMInitialize(INetFwPolicy2** ppNetFwPolicy2)
{HRESULT hr = S_OK;hr = CoCreateInstance(__uuidof(NetFwPolicy2),NULL,CLSCTX_INPROC_SERVER,__uuidof(INetFwPolicy2),(void**)ppNetFwPolicy2);if (FAILED(hr)){printf("CoCreateInstance for INetFwPolicy2 failed: 0x%08lx\n", hr);goto Cleanup;}Cleanup:return hr;
}int main(int argc, TCHAR* argv[])
{HRESULT hrComInit = S_OK;HRESULT hr = S_OK;INetFwPolicy2 *pNetFwPolicy2 = NULL;INetFwRules *pFwRules = NULL;INetFwRule *pFwRule = NULL;long CurrentProfilesBitMask = 0;BSTR bstrRuleName = SysAllocString(L"XiaoMu_0129");BSTR bstrRuleDescription = SysAllocString(L"Allow incoming network traffic over port 2400 coming from LAN interface type");BSTR bstrRuleGroup = SysAllocString(L"Sample Rule Group");BSTR bstrRuleLPorts = SysAllocString(L"2400-2450");BSTR bstrRuleInterfaceType = SysAllocString(L"LAN");// Initialize COM.hrComInit = CoInitializeEx(0,COINIT_APARTMENTTHREADED);// Ignore RPC_E_CHANGED_MODE; this just means that COM has already been// initialized with a different mode. Since we don't care what the mode is,// we'll just use the existing mode.if (hrComInit != RPC_E_CHANGED_MODE){if (FAILED(hrComInit)){printf("CoInitializeEx failed: 0x%08lx\n", hrComInit);goto Cleanup;}}// Retrieve INetFwPolicy2hr = WFCOMInitialize(&pNetFwPolicy2);if (FAILED(hr)){goto Cleanup;}// Retrieve INetFwRuleshr = pNetFwPolicy2->get_Rules(&pFwRules);if (FAILED(hr)){printf("get_Rules failed: 0x%08lx\n", hr);goto Cleanup;}// Retrieve Current Profiles bitmaskhr = pNetFwPolicy2->get_CurrentProfileTypes(&CurrentProfilesBitMask);if (FAILED(hr)){printf("get_CurrentProfileTypes failed: 0x%08lx\n", hr);goto Cleanup;}// When possible we avoid adding firewall rules to the Public profile.// If Public is currently active and it is not the only active profile, we remove it from the bitmaskif ((CurrentProfilesBitMask & NET_FW_PROFILE2_PUBLIC) &&(CurrentProfilesBitMask != NET_FW_PROFILE2_PUBLIC)){CurrentProfilesBitMask ^= NET_FW_PROFILE2_PUBLIC;}// Create a new Firewall Rule object.hr = CoCreateInstance(__uuidof(NetFwRule),NULL,CLSCTX_INPROC_SERVER,__uuidof(INetFwRule),(void**)&pFwRule);if (FAILED(hr)){printf("CoCreateInstance for Firewall Rule failed: 0x%08lx\n", hr);goto Cleanup;}// Populate the Firewall Rule objectpFwRule->put_Name(bstrRuleName);pFwRule->put_Description(bstrRuleDescription);pFwRule->put_Protocol(NET_FW_IP_PROTOCOL_TCP);pFwRule->put_LocalPorts(bstrRuleLPorts);pFwRule->put_Grouping(bstrRuleGroup);pFwRule->put_InterfaceTypes(bstrRuleInterfaceType);pFwRule->put_Profiles(CurrentProfilesBitMask);pFwRule->put_Action(NET_FW_ACTION_ALLOW);pFwRule->put_Enabled(VARIANT_TRUE);// Add the Firewall Rulehr = pFwRules->Add(pFwRule);if (FAILED(hr)){printf("Firewall Rule Add failed: 0x%08lx\n", hr);goto Cleanup;}Cleanup:// Free BSTR'sSysFreeString(bstrRuleName);SysFreeString(bstrRuleDescription);SysFreeString(bstrRuleGroup);SysFreeString(bstrRuleLPorts);SysFreeString(bstrRuleInterfaceType);// Release the INetFwRule objectif (pFwRule != NULL){pFwRule->Release();}// Release the INetFwRules objectif (pFwRules != NULL){pFwRules->Release();}// Release the INetFwPolicy2 objectif (pNetFwPolicy2 != NULL){pNetFwPolicy2->Release();}// Uninitialize COM.if (SUCCEEDED(hrComInit)){CoUninitialize();}printf("OK.\n");getchar();return 0;}

- 遍历所有的防火墙规则
/********************************************************************++
Copyright (C) Microsoft. All Rights Reserved.Abstract:This C++ file includes sample code for enumerating Windows Firewallrules using the Microsoft Windows Firewall APIs.********************************************************************/#include <windows.h>
#include <stdio.h>
#include <comutil.h>
#include <atlcomcli.h>
#include <netfw.h>#pragma comment( lib, "ole32.lib" )
#pragma comment( lib, "oleaut32.lib" )#define NET_FW_IP_PROTOCOL_TCP_NAME L"TCP"
#define NET_FW_IP_PROTOCOL_UDP_NAME L"UDP"#define NET_FW_RULE_DIR_IN_NAME L"In"
#define NET_FW_RULE_DIR_OUT_NAME L"Out"#define NET_FW_RULE_ACTION_BLOCK_NAME L"Block"
#define NET_FW_RULE_ACTION_ALLOW_NAME L"Allow"#define NET_FW_RULE_ENABLE_IN_NAME L"TRUE"
#define NET_FW_RULE_DISABLE_IN_NAME L"FALSE"// Forward declarations
void DumpFWRulesInCollection(INetFwRule* FwRule);
HRESULT WFCOMInitialize(INetFwPolicy2** ppNetFwPolicy2);int __cdecl main()
{HRESULT hrComInit = S_OK;HRESULT hr = S_OK;ULONG cFetched = 0; CComVariant var;IUnknown *pEnumerator;IEnumVARIANT* pVariant = NULL;INetFwPolicy2 *pNetFwPolicy2 = NULL;INetFwRules *pFwRules = NULL;INetFwRule *pFwRule = NULL;long fwRuleCount;// Initialize COM.hrComInit = CoInitializeEx(0,COINIT_APARTMENTTHREADED);// Ignore RPC_E_CHANGED_MODE; this just means that COM has already been// initialized with a different mode. Since we don't care what the mode is,// we'll just use the existing mode.if (hrComInit != RPC_E_CHANGED_MODE){if (FAILED(hrComInit)){wprintf(L"CoInitializeEx failed: 0x%08lx\n", hrComInit);goto Cleanup;}}// Retrieve INetFwPolicy2hr = WFCOMInitialize(&pNetFwPolicy2);if (FAILED(hr)){goto Cleanup;}// Retrieve INetFwRuleshr = pNetFwPolicy2->get_Rules(&pFwRules);if (FAILED(hr)){wprintf(L"get_Rules failed: 0x%08lx\n", hr);goto Cleanup;}// Obtain the number of Firewall ruleshr = pFwRules->get_Count(&fwRuleCount);if (FAILED(hr)){wprintf(L"get_Count failed: 0x%08lx\n", hr);goto Cleanup;}wprintf(L"The number of rules in the Windows Firewall are %d\n", fwRuleCount);// Iterate through all of the rules in pFwRulespFwRules->get__NewEnum(&pEnumerator);if(pEnumerator){hr = pEnumerator->QueryInterface(__uuidof(IEnumVARIANT), (void **) &pVariant);}while(SUCCEEDED(hr) && hr != S_FALSE){var.Clear();hr = pVariant->Next(1, &var, &cFetched);if (S_FALSE != hr){if (SUCCEEDED(hr)){hr = var.ChangeType(VT_DISPATCH);}if (SUCCEEDED(hr)){hr = (V_DISPATCH(&var))->QueryInterface(__uuidof(INetFwRule), reinterpret_cast<void**>(&pFwRule));}if (SUCCEEDED(hr)){// Output the properties of this ruleDumpFWRulesInCollection(pFwRule);}}}Cleanup:// Release pFwRuleif (pFwRule != NULL){pFwRule->Release();}// Release INetFwPolicy2if (pNetFwPolicy2 != NULL){pNetFwPolicy2->Release();}// Uninitialize COM.if (SUCCEEDED(hrComInit)){CoUninitialize();}return 0;
}// Output properties of a Firewall rule
void DumpFWRulesInCollection(INetFwRule* FwRule)
{variant_t InterfaceArray;variant_t InterfaceString; VARIANT_BOOL bEnabled;BSTR bstrVal;long lVal = 0;long lProfileBitmask = 0;NET_FW_RULE_DIRECTION fwDirection;NET_FW_ACTION fwAction;struct ProfileMapElement {NET_FW_PROFILE_TYPE2 Id;LPCWSTR Name;};ProfileMapElement ProfileMap[3];ProfileMap[0].Id = NET_FW_PROFILE2_DOMAIN;ProfileMap[0].Name = L"Domain";ProfileMap[1].Id = NET_FW_PROFILE2_PRIVATE;ProfileMap[1].Name = L"Private";ProfileMap[2].Id = NET_FW_PROFILE2_PUBLIC;ProfileMap[2].Name = L"Public";wprintf(L"---------------------------------------------\n");if (SUCCEEDED(FwRule->get_Name(&bstrVal))){wprintf(L"Name: %s\n", bstrVal);}if (SUCCEEDED(FwRule->get_Description(&bstrVal))){wprintf(L"Description: %s\n", bstrVal);}if (SUCCEEDED(FwRule->get_ApplicationName(&bstrVal))){wprintf(L"Application Name: %s\n", bstrVal);}if (SUCCEEDED(FwRule->get_ServiceName(&bstrVal))){wprintf(L"Service Name: %s\n", bstrVal);}if (SUCCEEDED(FwRule->get_Protocol(&lVal))){switch(lVal){case NET_FW_IP_PROTOCOL_TCP: wprintf(L"IP Protocol: %s\n", NET_FW_IP_PROTOCOL_TCP_NAME);break;case NET_FW_IP_PROTOCOL_UDP: wprintf(L"IP Protocol: %s\n", NET_FW_IP_PROTOCOL_UDP_NAME);break;default:break;}if(lVal != NET_FW_IP_VERSION_V4 && lVal != NET_FW_IP_VERSION_V6){if (SUCCEEDED(FwRule->get_LocalPorts(&bstrVal))){wprintf(L"Local Ports: %s\n", bstrVal);}if (SUCCEEDED(FwRule->get_RemotePorts(&bstrVal))){wprintf(L"Remote Ports: %s\n", bstrVal);}}else{if (SUCCEEDED(FwRule->get_IcmpTypesAndCodes(&bstrVal))){wprintf(L"ICMP TypeCode: %s\n", bstrVal);}}}if (SUCCEEDED(FwRule->get_LocalAddresses(&bstrVal))){wprintf(L"LocalAddresses: %s\n", bstrVal);}if (SUCCEEDED(FwRule->get_RemoteAddresses(&bstrVal))){wprintf(L"RemoteAddresses: %s\n", bstrVal);}if (SUCCEEDED(FwRule->get_Profiles(&lProfileBitmask))){// The returned bitmask can have more than 1 bit set if multiple profiles // are active or current at the same timefor (int i=0; i<3; i++){if ( lProfileBitmask & ProfileMap[i].Id ){wprintf(L"Profile: %s\n", ProfileMap[i].Name);}}}if (SUCCEEDED(FwRule->get_Direction(&fwDirection))){switch(fwDirection){case NET_FW_RULE_DIR_IN:wprintf(L"Direction: %s\n", NET_FW_RULE_DIR_IN_NAME);break;case NET_FW_RULE_DIR_OUT:wprintf(L"Direction: %s\n", NET_FW_RULE_DIR_OUT_NAME);break;default:break;}}if (SUCCEEDED(FwRule->get_Action(&fwAction))){switch(fwAction){case NET_FW_ACTION_BLOCK:wprintf(L"Action: %s\n", NET_FW_RULE_ACTION_BLOCK_NAME);break;case NET_FW_ACTION_ALLOW:wprintf(L"Action: %s\n", NET_FW_RULE_ACTION_ALLOW_NAME);break;default:break;}}if (SUCCEEDED(FwRule->get_Interfaces(&InterfaceArray))){if(InterfaceArray.vt != VT_EMPTY){SAFEARRAY *pSa = NULL;pSa = InterfaceArray.parray;for(long index= pSa->rgsabound->lLbound; index < (long)pSa->rgsabound->cElements; index++){SafeArrayGetElement(pSa, &index, &InterfaceString);wprintf(L"Interfaces: %s\n", (BSTR)InterfaceString.bstrVal);}}}if (SUCCEEDED(FwRule->get_InterfaceTypes(&bstrVal))){wprintf(L"Interface Types: %s\n", bstrVal);}if (SUCCEEDED(FwRule->get_Enabled(&bEnabled))){if (bEnabled){wprintf(L"Enabled: %s\n", NET_FW_RULE_ENABLE_IN_NAME);}else{wprintf(L"Enabled: %s\n", NET_FW_RULE_DISABLE_IN_NAME);}}if (SUCCEEDED(FwRule->get_Grouping(&bstrVal))){wprintf(L"Grouping: %s\n", bstrVal);}if (SUCCEEDED(FwRule->get_EdgeTraversal(&bEnabled))){if (bEnabled){wprintf(L"Edge Traversal: %s\n", NET_FW_RULE_ENABLE_IN_NAME);}else{wprintf(L"Edge Traversal: %s\n", NET_FW_RULE_DISABLE_IN_NAME);}}
}// Instantiate INetFwPolicy2
HRESULT WFCOMInitialize(INetFwPolicy2** ppNetFwPolicy2)
{HRESULT hr = S_OK;hr = CoCreateInstance(__uuidof(NetFwPolicy2), NULL, CLSCTX_INPROC_SERVER, __uuidof(INetFwPolicy2), (void**)ppNetFwPolicy2);if (FAILED(hr)){wprintf(L"CoCreateInstance for INetFwPolicy2 failed: 0x%08lx\n", hr);goto Cleanup; }Cleanup:return hr;
}
5、VB方式
' This VBScript file includes sample code that enumerates
' Windows Firewall rules using the Microsoft Windows Firewall APIs.Option ExplicitDim CurrentProfiles
Dim InterfaceArray
Dim LowerBound
Dim UpperBound
Dim iterate
Dim rule' Profile Type
Const NET_FW_PROFILE2_DOMAIN = 1
Const NET_FW_PROFILE2_PRIVATE = 2
Const NET_FW_PROFILE2_PUBLIC = 4' Protocol
Const NET_FW_IP_PROTOCOL_TCP = 6
Const NET_FW_IP_PROTOCOL_UDP = 17
Const NET_FW_IP_PROTOCOL_ICMPv4 = 1
Const NET_FW_IP_PROTOCOL_ICMPv6 = 58' Direction
Const NET_FW_RULE_DIR_IN = 1
Const NET_FW_RULE_DIR_OUT = 2' Action
Const NET_FW_ACTION_BLOCK = 0
Const NET_FW_ACTION_ALLOW = 1' Create the FwPolicy2 object.
Dim fwPolicy2
Set fwPolicy2 = CreateObject("HNetCfg.FwPolicy2")CurrentProfiles = fwPolicy2.CurrentProfileTypes'// The returned 'CurrentProfiles' bitmask can have more than 1 bit set if multiple profiles
'// are active or current at the same timeif ( CurrentProfiles AND NET_FW_PROFILE2_DOMAIN ) thenWScript.Echo("Domain Firewall Profile is active")
end ifif ( CurrentProfiles AND NET_FW_PROFILE2_PRIVATE ) thenWScript.Echo("Private Firewall Profile is active")
end ifif ( CurrentProfiles AND NET_FW_PROFILE2_PUBLIC ) thenWScript.Echo("Public Firewall Profile is active")
end if' Get the Rules object
Dim RulesObject
Set RulesObject = fwPolicy2.Rules' Print all the rules in currently active firewall profiles.
WScript.Echo("Rules:")For Each rule In Rulesobjectif rule.Profiles And CurrentProfiles thenWScript.Echo(" Rule Name: " & rule.Name)WScript.Echo(" ----------------------------------------------")WScript.Echo(" Description: " & rule.Description)WScript.Echo(" Application Name: " & rule.ApplicationName)WScript.Echo(" Service Name: " & rule.ServiceName)Select Case rule.ProtocolCase NET_FW_IP_PROTOCOL_TCP WScript.Echo(" IP Protocol: TCP.")Case NET_FW_IP_PROTOCOL_UDP WScript.Echo(" IP Protocol: UDP.")Case NET_FW_IP_PROTOCOL_ICMPv4 WScript.Echo(" IP Protocol: UDP.")Case NET_FW_IP_PROTOCOL_ICMPv6 WScript.Echo(" IP Protocol: UDP.")Case Else WScript.Echo(" IP Protocol: " & rule.Protocol)End Selectif rule.Protocol = NET_FW_IP_PROTOCOL_TCP or rule.Protocol = NET_FW_IP_PROTOCOL_UDP thenWScript.Echo(" Local Ports: " & rule.LocalPorts)WScript.Echo(" Remote Ports: " & rule.RemotePorts)WScript.Echo(" LocalAddresses: " & rule.LocalAddresses)WScript.Echo(" RemoteAddresses: " & rule.RemoteAddresses)end ifif rule.Protocol = NET_FW_IP_PROTOCOL_ICMPv4 or rule.Protocol = NET_FW_IP_PROTOCOL_ICMPv6 thenWScript.Echo(" ICMP Type and Code: " & rule.IcmpTypesAndCodes)end ifSelect Case rule.DirectionCase NET_FW_RULE_DIR_IN WScript.Echo(" Direction: In")Case NET_FW_RULE_DIR_OUT WScript.Echo(" Direction: Out")End SelectWScript.Echo(" Enabled: " & rule.Enabled)WScript.Echo(" Edge: " & rule.EdgeTraversal)Select Case rule.ActionCase NET_FW_ACTION_ALLOW WScript.Echo(" Action: Allow")Case NET_FW_ACTION_BLOCk WScript.Echo(" Action: Block")End SelectWScript.Echo(" Grouping: " & rule.Grouping)WScript.Echo(" Edge: " & rule.EdgeTraversal)WScript.Echo(" Interface Types: " & rule.InterfaceTypes)InterfaceArray = rule.Interfacesif IsEmpty(InterfaceArray) thenWScript.Echo(" Interfaces: All")elseLowerBound = LBound(InterfaceArray)UpperBound = UBound(InterfaceArray)WScript.Echo(" Interfaces: ")for iterate = LowerBound To UpperBoundWScript.Echo(" " & InterfaceArray(iterate))Nextend ifWScript.Echo("")end if
Next
flask默认开启的网站是本地的127.0.0.1:5000
现在把已经有的本机访问改成局域网访问:app.run(host=’0.0.0.0’,port=8080)
结语
如果您觉得该方法或代码有一点点用处,可以给作者点个赞,或打赏杯咖啡;╮( ̄▽ ̄)╭
如果您感觉方法或代码不咋地//(ㄒoㄒ)//,就在评论处留言,作者继续改进;o_O???
如果您需要相关功能的代码定制化开发,可以留言私信作者;(✿◡‿◡)
感谢各位大佬童鞋们的支持!( ´ ▽´ )ノ ( ´ ▽´)っ!!!
相关文章:

C++ 修改防火墙firewall设置(Windows)
文章目录1、简介1.1 防火墙概述1.2 入站,还是出站?1.3 防火墙规则优先级2、系统界面方式3、命令行方式3.1 防火墙基本状态设置3.2 入站出站规则设置3.3 其他设置3.4 telnet检测端口4、C方式4.1 注册表4.2 COM(Windows XP)4.3 COM&…...

Spring 入门教程详解
✅作者简介:2022年博客新星 第八。热爱国学的Java后端开发者,修心和技术同步精进。 🍎个人主页:Java Fans的博客 🍊个人信条:不迁怒,不贰过。小知识,大智慧。 💞当前专栏…...
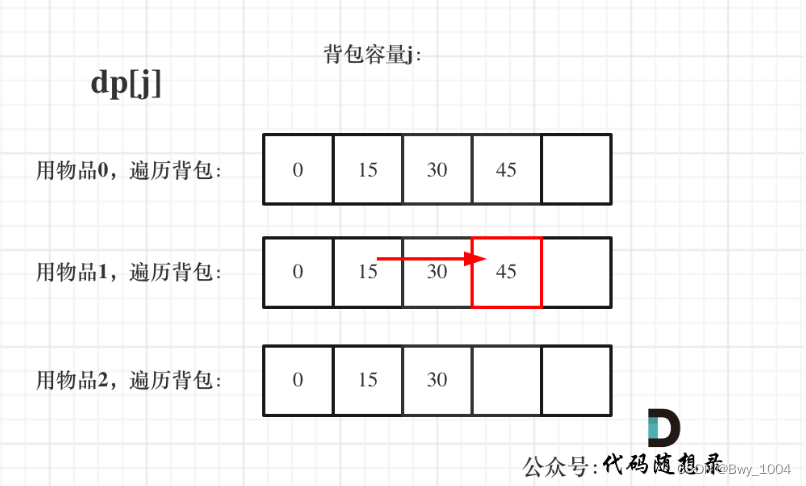
day43【代码随想录】动态规划之一和零、完全背包理论基础
文章目录前言一、一和零(力扣474)二、完全背包前言 1、一和零 2、完全背包理论基础 一、一和零(力扣474) 求装满这个背包最多有多少个物品 给你一个二进制字符串数组 strs 和两个整数 m 和 n 。 请你找出并返回 strs 的最大子集…...
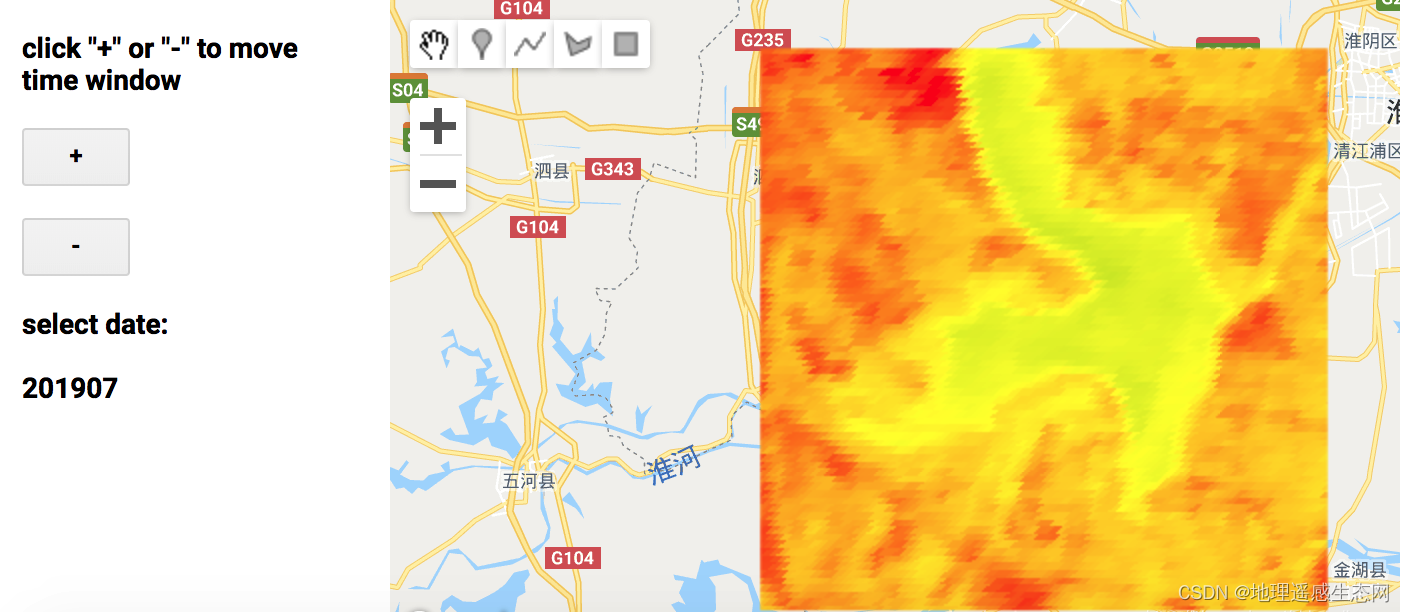
GEE学习笔记 七十八:干涸的洪泽湖
今天看了一篇报道直击60年一遇气象干旱:洪泽湖缩小近一半,鱼蟹受灾严重!_新华报业网(直击60年一遇气象干旱:洪泽湖缩小近一半,鱼蟹受灾严重!),既然玩GEE那就要玩出点花样…...

双指针【灵神基础精讲】
来源0x3f:https://space.bilibili.com/206214 文章目录同向双指针[209. 长度最小的子数组](https://leetcode.cn/problems/minimum-size-subarray-sum/)[713. 乘积小于 K 的子数组](https://leetcode.cn/problems/subarray-product-less-than-k/)[3. 无重复字符的最…...

tushare量化数据库模块怎么分析?
tushare量化数据其实包含的数据库有些是需要收费的,也有些会免费提供,不过tushare量化数据库整个库就很大很大,涉及的范围也广,挖掘这些数据还得从量化股票接口说起,就比如说在股票量化领域,tushare量化数据…...

模型转换 PyTorch转ONNX 入门
前言 本文主要介绍如何将PyTorch模型转换为ONNX模型,为后面的模型部署做准备。转换后的xxx.onnx模型,进行加载和测试。最后介绍使用Netron,可视化ONNX模型,看一下网络结构;查看使用了那些算子,以便开发部署…...
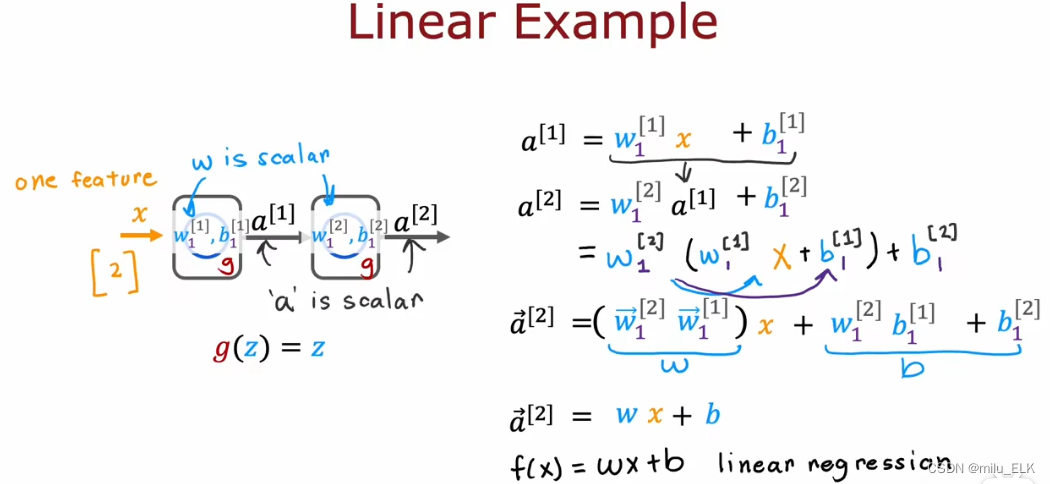
【深度学习】激活函数
上一章——认识神经网络 新课P54介绍了强人工智能概念,P55到P58解读了矩阵乘法在代码中的应用,P59,P60介绍了在Tensflow中实现神经网络的代码及细节,详细的内容可以自行观看2022吴恩达机器学习Deeplearning.ai课程,专…...
)
【新2023】华为OD机试 - 数字的排列(Python)
华为 OD 清单查看地址:blog.csdn.net/hihell/category_12199275.html 数字的排列 题目 小华是个很有对数字很敏感的小朋友, 他觉得数字的不同排列方式有特殊的美感。 某天,小华突发奇想,如果数字多行排列, 第一行1个数, 第二行2个, 第三行3个, 即第n行n个数字,并且…...

[oeasy]python0085_ASCII之父_Bemer_COBOL_数据交换网络
编码进化 回忆上次内容 上次 回顾了 字符编码的 进化过程 IBM 在数字化过程中 作用 非常大IBM 的 BCDIC 有 黑历史 😄 6-bit的 BCDIC 直接进化成 8-bit的 EBCDIC补全了 小写字母 和 控制字符 在ibm就是信息产业的年代 ibm的标准 怎么最终 没有成为 行业的标准 呢…...

volatile,内存屏障
volatile的特性可见性: 对于其他线程是可见,假设线程1修改了volatile修饰的变量,那么线程2是可见的,并且是线程安全的重排序: 由于CPU执行的时候,指令在后面的会先执行,在指令层级的时候我们晓得volatile的特性后,我们就要去volatile是如何实现的,这个很重要!&#…...

【ESP 保姆级教程】玩转emqx MQTT篇① —— 系统主题、延迟发布、服务器配置预算、常见问题
忘记过去,超越自己 ❤️ 博客主页 单片机菜鸟哥,一个野生非专业硬件IOT爱好者 ❤️❤️ 本篇创建记录 2023-02-18 ❤️❤️ 本篇更新记录 2023-02-18 ❤️🎉 欢迎关注 🔎点赞 👍收藏 ⭐️留言📝🙏 此博客均由博主单独编写,不存在任何商业团队运营,如发现错误,请…...
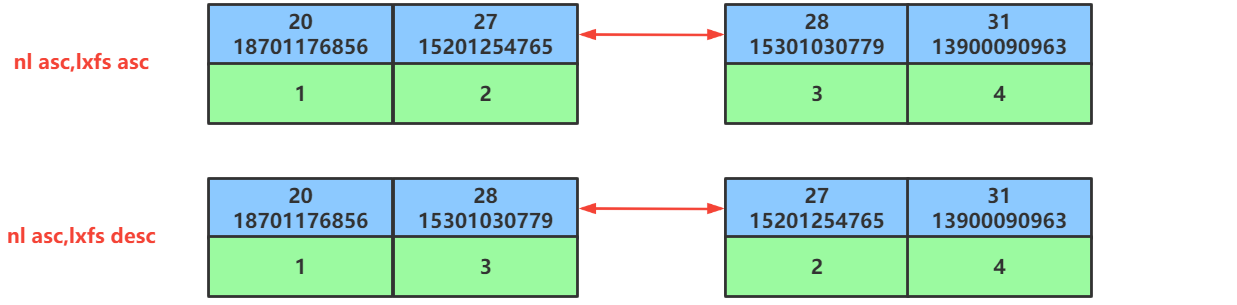
第48讲:SQL优化之ORDER BY排序查询的优化
文章目录1.ORDEY BY排序查询优化方面的概念2.ORDER BY排序的优化原则3.ORDER BY排序优化的案例3.1.准备排序优化的表以及索引3.2.同时对nl和lxfs字段使用升序排序3.3.同时对nl和lxfs字段使用降序排序3.4.排序时调整联合索引中字段的位置顺序3.5.排序时一个字段使用升序一个字段…...
[Datawhale][CS224W]图机器学习(三)
目录一、简介与准备二、教程2.1 下载安装2.2 创建图2.2.1 常用图创建(自定义图创建)1.创建图对象2.添加图节点3.创建连接2.2.2 经典图结构1.全连接无向图2.全连接有向图3.环状图4.梯状图5.线性串珠图6.星状图7.轮辐图8.二项树2.2.3 栅格图1.二维矩形栅格…...

2023版最新最强大数据面试宝典
此套面试题来自于各大厂的真实面试题及常问的知识点,如果能理解吃透这些问题,你的大数据能力将会大大提升,进入大厂指日可待!目前已经更新到第4版,广受好评!复习大数据面试题,看这一套就够了&am…...

CSS 中的 BFC 是什么,有什么作用?
BFC,即“块级格式化上下文”(Block Formatting Context),是 CSS 中一个重要的概念,它指的是一个独立的渲染区域,让块级盒子在布局时遵循一些特定的规则。BFC 的存在使得我们可以更好地控制文档流࿰…...
总结在使用 Git 踩过的坑
问题一: 原因 git 有两种拉代码的方式,一个是 HTTP,另一个是 ssh。git 的 HTTP 底层是通过 curl 的。HTTP 底层基于 TCP,而 TCP 协议的实现是有缓冲区的。 所以这个报错大致意思就是说,连接已经关闭,但是此时有未处理…...

从 HTTP 到 gRPC:APISIX 中 etcd 操作的迁移之路
罗泽轩,API7.ai 技术专家/技术工程师,Apache APISIX PMC 成员。 原文链接 Apache APISIX 现有基于 HTTP 的 etcd 操作的局限性 etcd 在 2.x 版本的时候,对外暴露的是 HTTP 1 (以下简称 HTTP)的接口。etcd 升级到 3.x…...
【C语言每日一题】——倒置字符串
【C语言每日一题】——倒置字符串😎前言🙌倒置字符串🙌总结撒花💞😎博客昵称:博客小梦 😊最喜欢的座右铭:全神贯注的上吧!!! 😊作者简…...

Native扩展开发的一般流程(类似开发一个插件)
文章目录大致开发流程1、编写对应的java类服务2、将jar包放到对应位置3、配置文件中进行服务配置4、在代码中调用5、如何查看服务调用成功大致开发流程 1、编写服务,打包为jar包2、将jar包放到指定的位置3、在配置文件中进行配置,调用对应的服务 1、编…...
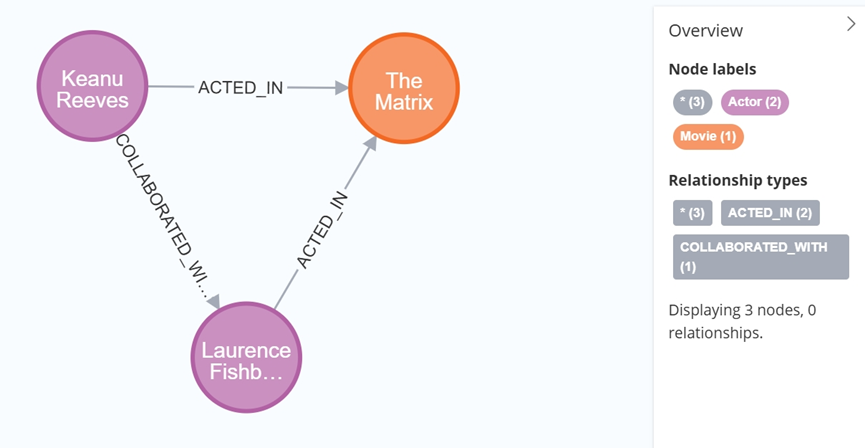
大数据学习栈记——Neo4j的安装与使用
本文介绍图数据库Neofj的安装与使用,操作系统:Ubuntu24.04,Neofj版本:2025.04.0。 Apt安装 Neofj可以进行官网安装:Neo4j Deployment Center - Graph Database & Analytics 我这里安装是添加软件源的方法 最新版…...

<6>-MySQL表的增删查改
目录 一,create(创建表) 二,retrieve(查询表) 1,select列 2,where条件 三,update(更新表) 四,delete(删除表…...

ubuntu搭建nfs服务centos挂载访问
在Ubuntu上设置NFS服务器 在Ubuntu上,你可以使用apt包管理器来安装NFS服务器。打开终端并运行: sudo apt update sudo apt install nfs-kernel-server创建共享目录 创建一个目录用于共享,例如/shared: sudo mkdir /shared sud…...

基于服务器使用 apt 安装、配置 Nginx
🧾 一、查看可安装的 Nginx 版本 首先,你可以运行以下命令查看可用版本: apt-cache madison nginx-core输出示例: nginx-core | 1.18.0-6ubuntu14.6 | http://archive.ubuntu.com/ubuntu focal-updates/main amd64 Packages ng…...
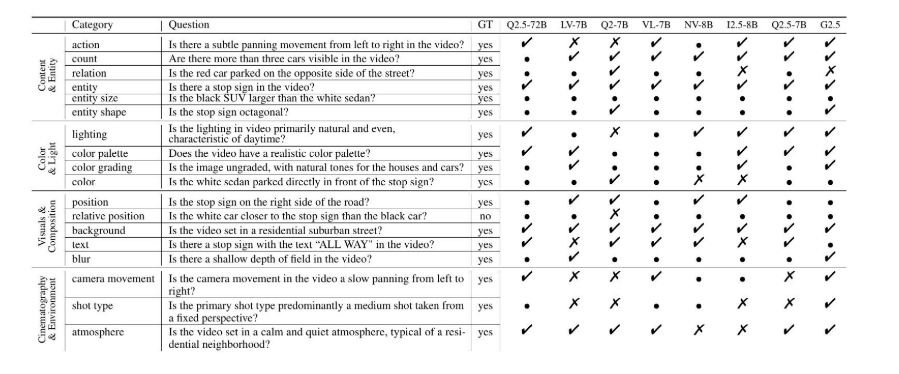
视频字幕质量评估的大规模细粒度基准
大家读完觉得有帮助记得关注和点赞!!! 摘要 视频字幕在文本到视频生成任务中起着至关重要的作用,因为它们的质量直接影响所生成视频的语义连贯性和视觉保真度。尽管大型视觉-语言模型(VLMs)在字幕生成方面…...
)
WEB3全栈开发——面试专业技能点P2智能合约开发(Solidity)
一、Solidity合约开发 下面是 Solidity 合约开发 的概念、代码示例及讲解,适合用作学习或写简历项目背景说明。 🧠 一、概念简介:Solidity 合约开发 Solidity 是一种专门为 以太坊(Ethereum)平台编写智能合约的高级编…...

Pinocchio 库详解及其在足式机器人上的应用
Pinocchio 库详解及其在足式机器人上的应用 Pinocchio (Pinocchio is not only a nose) 是一个开源的 C 库,专门用于快速计算机器人模型的正向运动学、逆向运动学、雅可比矩阵、动力学和动力学导数。它主要关注效率和准确性,并提供了一个通用的框架&…...
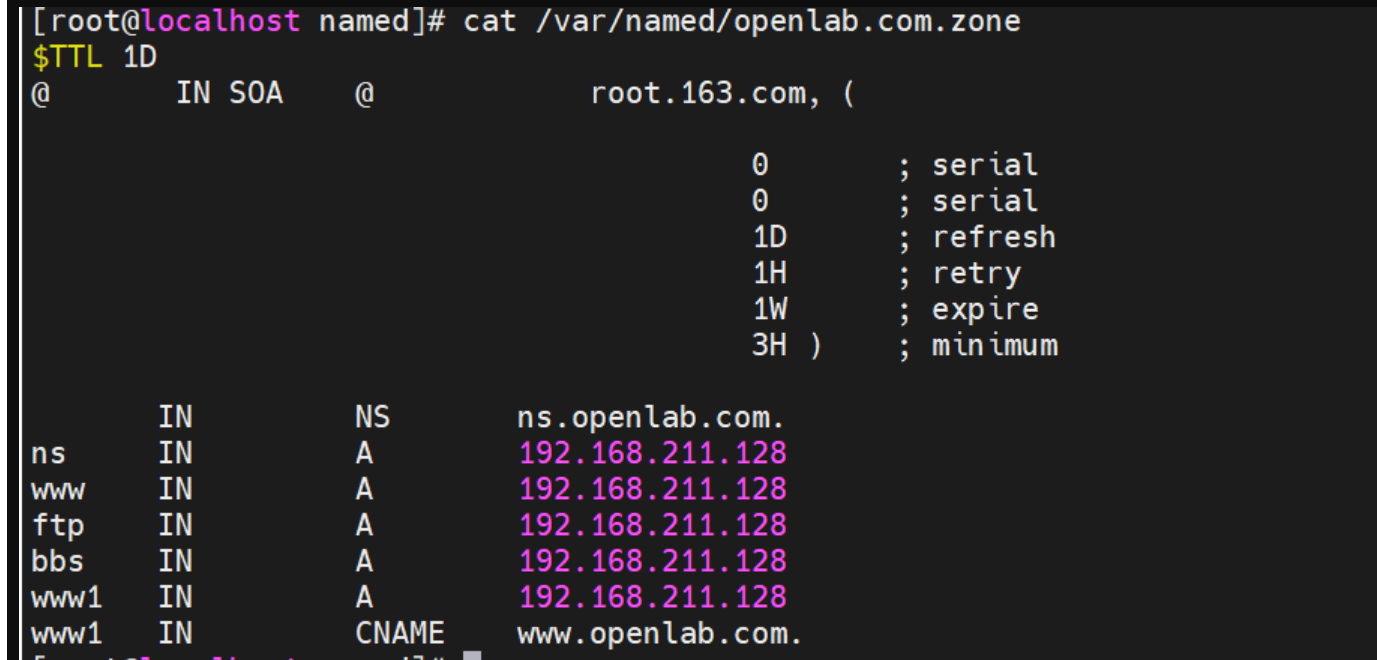
搭建DNS域名解析服务器(正向解析资源文件)
正向解析资源文件 1)准备工作 服务端及客户端都关闭安全软件 [rootlocalhost ~]# systemctl stop firewalld [rootlocalhost ~]# setenforce 0 2)服务端安装软件:bind 1.配置yum源 [rootlocalhost ~]# cat /etc/yum.repos.d/base.repo [Base…...

4. TypeScript 类型推断与类型组合
一、类型推断 (一) 什么是类型推断 TypeScript 的类型推断会根据变量、函数返回值、对象和数组的赋值和使用方式,自动确定它们的类型。 这一特性减少了显式类型注解的需要,在保持类型安全的同时简化了代码。通过分析上下文和初始值,TypeSc…...
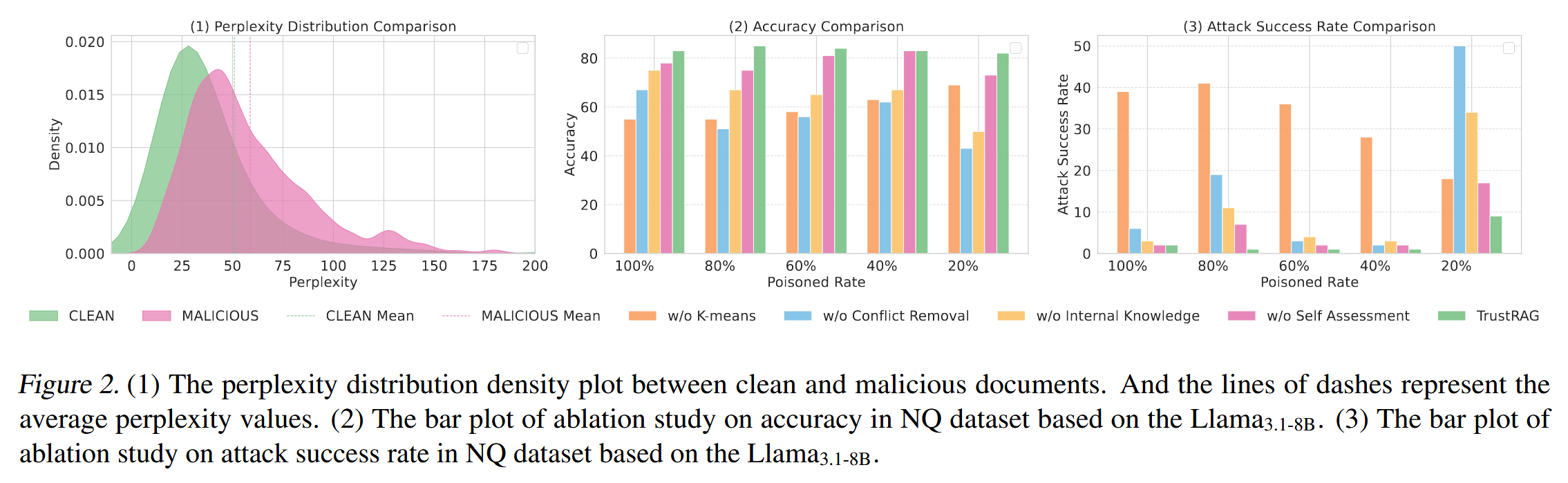
[论文阅读]TrustRAG: Enhancing Robustness and Trustworthiness in RAG
TrustRAG: Enhancing Robustness and Trustworthiness in RAG [2501.00879] TrustRAG: Enhancing Robustness and Trustworthiness in Retrieval-Augmented Generation 代码:HuichiZhou/TrustRAG: Code for "TrustRAG: Enhancing Robustness and Trustworthin…...
