CCNP350-401学习笔记(101-150题)
101、Refer to the exhibit

SwitchC connects HR and Sales to the Core switch However, business needs require that no traffic from the Finance VLAN traverse this switch.
Which command meets this requirement?
A. SwitchC(config)#vtp pruning
B. SwitchC(config)#vtp pruning vlan 110
C. SwitchC(config)#interface port-channel 1
SwitchC(config-if)#switchport trunk allowed vlan add 210,310
D. SwitchC(config)#interface port-channel 1
SwitchC(config-if)#switchport trunk allowed vlan remove 110
102、Refer to the exhibit.

Which HTTP JSON response does the python code output give?
A. NameError: name 'json' is not defined
B. KeyError 'kickstart_ver_str'
C. 7.61
D. 7.0(3)I7(4)
103、When a wired client connects to an edge switch in an SDA fabric, which component decides whether the client has access to the network?
A. control-plane node
B. Identity Service Engine
C. RADIUS server
D. edge node
104、Refer to the exhibit.
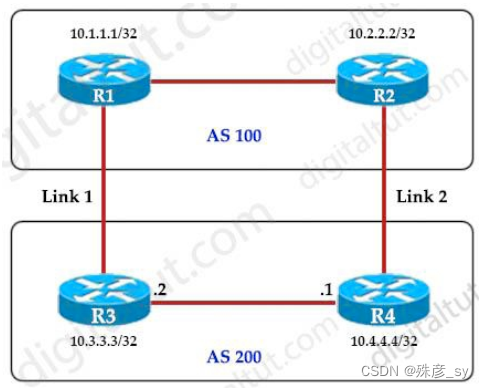
An engineer must ensure that all traffic leaving AS 200 will choose Link 2 as the exit point. Assuming that all BGP neighbor relationships have been formed and that the attributes have not been changed on any of the routers, which configuration accomplish task?
A. R4(config-router)#bgp default local-preference 200
B. R3(config-router)#neighbor 10.1.1.1 weight 200
C. R3(config-router)#bgp default local-preference 200
D. R4(config-router)#neighbor 10.2.2.2 weight 200
105、Which protocol infers that a YANG data model is being used?
A. SNMP
B. REST
C. RESTCONF
D. NX-API
106、Which configuration restricts the amount of SSH that a router accepts to 100 kbps?
A. class-map match-all CoPP_SSH
match access-group name CoPP_SSH
!
Policy-map CoPP_SSH
class CoPP_SSH
police cir 100000
exceed-action drop
! ! !
Interface GigabitEthernet0/1
ip address 209.165.200.225 255.255.255.0
ip access-group CoPP_SSH out
duplex auto
speed auto
media-type rj45
service-policy input CoPP_SSH
!
ip access-list extended CoPP_SSH
permit tcp any any eq 22
!
B. class-map match-all CoPP_SSH
match access-group name CoPP_SSH
!
Policy-map CoPP_SSH
class CoPP_SSH
police cir CoPP_SSH
exceed-action drop
!
Interface GigabitEthernet0/1
ip address 209.165.200.225 255.255.255.0
ip access-group … out
duplex auto
speed auto
media-type rj45
service-policy input CoPP_SSH
!
Ip access-list extended CoPP_SSH
deny tcp any any eq 22
!
C. class-map match-all CoPP_SSH
match access-group name CoPP_SSH
!
Policy-map CoPP_SSH
class CoPP_SSH
police cir 100000
exceed-action drop
!
Control-plane
service-policy input CoPP_SSH
!
Ip access-list extended CoPP_SSH
deny tcp any any eq 22
!
D. class-map match-all CoPP_SSH
match access-group name CoPP_SSH
!
Policy-map CoPP_SSH
class CoPP_SSH
police cir 100000 exceed-action drop
!Control-plane transit
service-policy input CoPP_SSH
!
Ip access-list extended CoPP_SSH
permit tcp any any eq 22
!
107、What NTP stratum level is a server that is connected directly to an authoritative time source?
A. Stratum 0
B. Stratum 1
C. Stratum 14
D. Stratum 15
108、How does QoS traffic shaping alleviate network congestion?
A. It drops packets when traffic exceeds a certain bitrate.
B. It buffers and queue packets above the committed rate.
C. It fragments large packets and queues them for delivery.
D. It drops packets randomly from lower priority queues.
109、n engineer is describing QoS to a client. Which two facts apply to traffic policing? (Choose two)
A. Policing adapts to network congestion by queuing excess trafficB. Policing should be performed as close to the destination as possible
C. Policing drops traffic that exceeds the defined rate
D. Policing typically delays the traffic, rather than drops it
E. Policing should be performed as close to the source as possible
110、What mechanism does PIM use to forward multicast traffic?
A. PIM sparse mode uses a pull model to deliver multicast traffic
B. PIM dense mode uses a pull model to deliver multicast traffic
C. PIM sparse mode uses receivers to register with the RP
D. PIM sparse mode uses a flood and prune model to deliver multicast traffic
111、Which two namespaces does the LISP network architecture and protocol use? (Choose two)
A. TLOC
B. RLOC
C. DNS
D. VTEP
E. EID
112、Which First Hop Redundancy Protocol should be used to meet a design requirements for
more efficient default bandwidth usage across multiple devices?
A. GLBP
B. LCAP
C. HSRP
D. VRRP
113、Refer to the exhibit.

A network engineer is configuring OSPF between router R1 and router R2. The engineer must ensure that a DR/BDR election does not occur on the Gigabit Ethernet interfaces in area 0. Which configuration set accomplishes this goal?
A. R1 (config-if) #interface Gi0/0
R1 (config-if) #ip ospf network point-to-point
R2 (config-if) #interface Gi0/0
R2 (config-if) #ip ospf network point-to-point
B. R1 (config-if) #interface Gi0/0
R1 (config-if) #ip ospf network broadcast
R2(config-if)#interface Gi0/0
R2(config-if)#ip ospf network broadcast
C. R1(config-if)#interface Gi0/0
R1(config-if)#ip ospf database-filter all out
R2(config-if)#interface Gi0/0
R2(config-if)#ip ospf database-filter all out
D. R1(config-if)#interface Gi0/0
R1(config-if)#ip ospf priority 1
R2(config-if)#interface Gi0/0
R2(config-if)#ip ospf priority 1
114、What are two reasons why broadcast radiation is caused in the virtual machine environment? (Choose two)
A. vSwitch must interrupt the server CPU to process the broadcast packet
B. The Layer 2 domain can be large in virtual machine environments
C. Virtual machines communicate primarily through broadcast modeD. Communication between vSwitch and network switch is broadcast based
E. Communication between vSwitch and network switch is multicast based
115、A company plans to implement intent-based networking in its campus infrastructure. Which design facilities a migrate from a traditional campus design to a programmer fabric designer?
A. Layer 2 access
B. three-tier
C. two-tier
D. routed access
116、When a wireless client roams between two different wireless controllers, a network connectivity outage is experience for a period of time. Which configuration issue would cause this problem?
A. Not all of the controllers in the mobility group are using the same mobility group name
B. Not all of the controllers within the mobility group are using the same virtual interface IP address
C. All of the controllers within the mobility group are using the same virtual interface IP address
D. All of the controllers in the mobility group are using the same mobility group name
117、Which algorithms are used to secure REST API from brute attacks and minimize the impact?
A. SHA-512 and SHA-384
B. MD5 algorithm-128 and SHA-384
C. SHA-1, SHA-256, and SHA-512
D. PBKDF2, BCrypt, and SCrypt
118、What is the role of the RP in PIM sparse mode?
A. The RP responds to the PIM join messages with the source of requested multicast group
B. The RP maintains default aging timeouts for all multicast streams requested by the receivers
C. The RP acts as a control-plane node and does not receive or forward multicast packets
D. The RP is the multicast that is the root of the PIM-SM shared multicast distribution tree
119、A network administrator is preparing a Python script to configure a Cisco IOS XE-based device on the network. The administrator is worried that colleagues will make changes to the device while the script is running. Which operation of the client manager in prevent colleague making changes to the device while the script is running?
A. m.lock (config=’running’)
B. m.lock (target=’running’)
C. m.freeze (target=’running’)
D. m.freeze(config=’running’)
120、What are two device roles in Cisco SD-Access fabric? (Choose two)
A. core switch
B. vBond controller
C. edge node
D. access switch
E. border node
121、Drag and drop the LISP components from the left onto the function they perform on the right. Not all options are used.

122、Drag and Drop the descriptions from the left onto the routing protocol they describe on the right.
123、Which component handles the orchestration plane of the Cisco SD-WAN?
A. vBond
B. vSmart
C. vManage
D. vEdge
124、Which two entities are Type 1 hypervisors? (Choose two)
A. Oracle VM Virtual Box
B. Microsoft Hyper-V
C. VMware server
D. VMware ESX
E. Microsoft Virtual PC
125、Which access point mode allows a supported AP to function like a WLAN client would, associating and identifying client connectivity issues?
A. client mode
B. SE-connect mode
C. sensor mode
D. sniffer mode
126、Refer to the exhibit
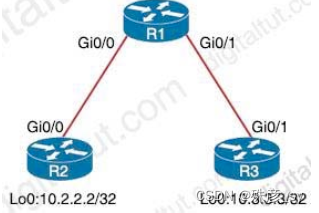
An engineer must deny Telnet traffic from the loopback interface of router R3 to the loopback interface of
router R2 during the weekend hours. All other traffic between the loopback interfaces of routers R3 and R2
must be allowed at all times. Which command accomplish this task?
A. R3(config)#time-range WEEKEND
R3(config-time-range)#periodic Saturday Sunday 00:00 to 23:59
R3(config)#access-list 150 deny tcp host 10.3.3.3 host 10.2.2.2 eq 23 time-range WEEKEND
R3(config)#access-list 150 permit ip any any time-range WEEKENDR3(config)#interface Gi0/1
R3(config-if)#ip access-group 150 out
B. R1(config)#time-range WEEKEND
R1(config-time-range)#periodic Friday Sunday 00:00 to 00:00
R1(config)#access-list 150 deny tcp host 10.3.3.3 host 10.2.2.2 eq 23 time-range WEEKEND
R1(config)#access-list 150 permit ip any any
R1(config)#interface Gi0/1
R1(config-if)#ip access-group 150 in
C. R1(config)#time-range WEEKEND
R1(config-time-range)#periodic weekend 00:00 to 23:59
R1(config)#access-list 150 deny tcp host 10.3.3.3 host 10.2.2.2 eq 23 time-range WEEKEND
R1(config)#access-list 150 permit ip any any
R1(config)#interface Gi0/1
R1(config-if)#ip access-group 150 in
D. R3(config)#time-range WEEKEND
R3(config-time-range)#periodic weekend 00:00 to 23:59
R3(config)#access-list 150 deny tcp host 10.3.3.3 host 10.2.2.2 eq 23 time-range WEEKEND
R3(config)#access-list 150 permit ip any any time-range WEEKEND
R3(config)#interface Gi0/1
R3(config-if)#ip access-group 150 out
127、Which tool is used in Cisco DNA Center to build generic configurations that are able to be applied on device with similar network settings?
A. Command Runner
B. Template Editor
C. Application Policies
D. Authentication Template
128、A client device roams between access points located on different floors in an atrium. The access points joined to the same controller and configuration in local mode. The access points are in different IP addresses, but the client VLAN in the group same. What type of roam occurs?
A. inter-controller
B. inter-subnet
C. intra-VLAN
D. intra-controller
129、What does the LAP send when multiple WLCs respond to the CISCO_CAPWAPCONTROLLER.localdomain hostname during the CAPWAP discovery and join process?
A. broadcast discover request
B. join request to all the WLCs
C. unicast discovery request to each WLC
D. Unicast discovery request to the first WLC that resolves the domain name
130、Refer to the exhibit.

What is the result when a technician adds the monitor session 1 destination remote vlan 233 command?
A. The RSPAN VLAN is replaced by VLAN 223
B. RSPAN traffic is sent to VLANs 222 and 223
C. An error is flagged for configuring two destinations
D. RSPAN traffic is split between VLANs 222 and 223
131、In an SD-Access solution what is the role of a fabric edge node?
A. to connect external Layer 3- network to the SD-Access fabric
B. to connect wired endpoint to the SD-Access fabric
C. to advertise fabric IP address space to external network
D. to connect the fusion router to the SD-Access fabric
132、Refer to the exhibit.
access-list 1 permit 172.16.1.0 0.0.0.255
ip nat inside source list 1 interface gigabitethernet0/0 overload
The inside and outside interfaces in the NAT configuration of this device have been correctly identified.
What is the effect of this configuration?
A. dynamic NAT
B. static NAT
C. PAT
D. NAT64
133、Which component of the Cisco Cyber Threat Defense solution provides user and flow context analysis?
A. Cisco Firepower and FireSIGHT
B. Cisco Stealth watch system
C. Advanced Malware Protection
D. Cisco Web Security Appliance
134、An engineer must protect their company against ransom ware attacks. Which solution allows the engineer to block the execution stage and prevent file encryption?
A. Use Cisco AMP deployment with the Malicious Activity Protection engineer enabled
B. Use Cisco AMP deployment with the Exploit Prevention engine enabled
C. Use Cisco Firepower and block traffic to TOR networks
D. Use Cisco Firepower with Intrusion Policy and snort rules blocking SMB exploitation
135、Refer to the exhibit.
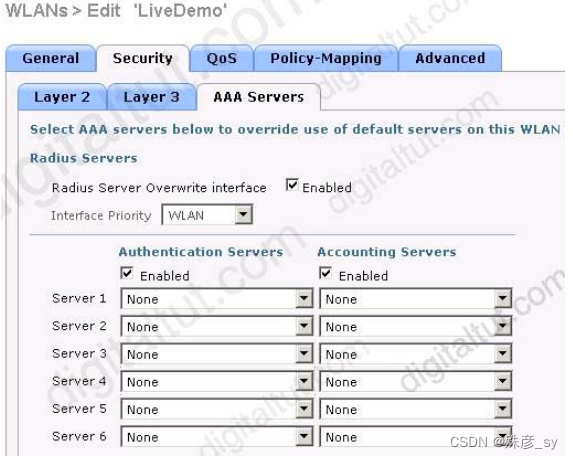
Assuming the WLC’s interfaces are not in the same subnet as the RADIUS server, which interface would the WLC use as the source for all RADIUS-related traffic?
A. the interface specified on the WLAN configuration
B. any interface configured on the WLC
C. the controller management interface
D. the controller virtual interface
136、Which benefit is offered by a cloud infrastructure deployment but is lacking in an on-premises deployment?
A. efficient scalability
B. virtualization
C. storage capacity
D. supported systems
137、Wireless users report frequent disconnections from the wireless network. While troubleshooting a network engineer finds that after the user a disconnect, the connection reestablishes automatically without any input required. The engineer also notices these message logs.

Which action reduces the user impact?
A. increase the dynamic channel assignment interval
B. increase BandSelect
C. increase the AP heartbeat timeout
D. enable coverage hole detection
138、 Which DHCP option helps lightweight APs find the IP address of a wireless LAN controller?
A. Option 43
B. Option 60
C. Option 67
D. Option 150
139、What is the process of password checks when a login attempt is made to the device?
A. A TACACS+ server is checked first. If that check fail, a database is checked
B. A TACACS+ server is checked first. If that check fail, a RADIUS server is checked. If that check fail, a local database is checked
C. A local database is checked first. If that fails, a TACACS+server is checked, if that check fails, a RADIUS server is checked
D. A local database is checked first. If that check fails, a TACACS+server is checked
140、What is the role of the vsmart controller in a Cisco SD-WAN environment?
A. IT performs authentication and authorization
B. It manages the control plane
C. It is the centralized network management system
D. It manages the data plane
141、Why is an AP joining a different WLC than the one specified through option 43?
A. The WLC is running a different software version
B. The API is joining a primed WLC
C. The AP multicast traffic unable to reach the WLC through Layer 3
D. The APs broadcast traffic is unable to reach the WLC through Layer 2
142、Which devices does Cisco Center configure when deploying an IP-based access control policy?
A. All devices integrating with ISE
B. selected individual devices
C. all devices in selected sites
D. all wired devices
143、Which method of account authentication does OAuth 2.0 within REST APIs?
A. username/role combination
B. access tokens
C. cookie authentication
D. basic signature workflow
144、What does the Cisco DNA Center use to enable the delivery of applications through a network and to yield analytics for innovation?
A. process adapters
B. Command Runner
C. intent-based APIs
D. domain adapters
145、Which action is a function of VTEP in VXLAN?
A. tunneling traffic from IPv6 to IPv4 VXLANs
B. allowing encrypted communication on the local VXLAN Ethernet segment
C. encapsulating and de-encapsulating VXLAN Ethernet frames
D. tunneling traffic from IPv4 to IPv6 VXLANs
146、Which type of antenna does the radiation pattern represent?

A. Yagi
B. multidirectional
C. directional patch
D. omnidirectional
147、Refer to the exhibit

Which command set resolves this error?
A. Sw1(config)# interface G0/0
Sw1(config-if)# no spanning-tree bpduguard enable
Sw1(config-if)# shut
Sw1(config-if)# no shut
B. Sw1(config)# interface G0/0
Sw1(config-if)# spanning-tree bpduguard enable
Sw1(config-if)# shut
Sw1(config-if)# no shut
C. Sw1(config)# interface G0/1
Sw1(config-if)# spanning-tree bpduguard enable
Sw1(config-if)# shut
Sw1(config-if)# no shut
D. Sw1(config)# interface G0/0
Sw1(config-if)# no spanning-tree bpdufilter
Sw1(config-if)# shut
Sw1(config-if)# no shut
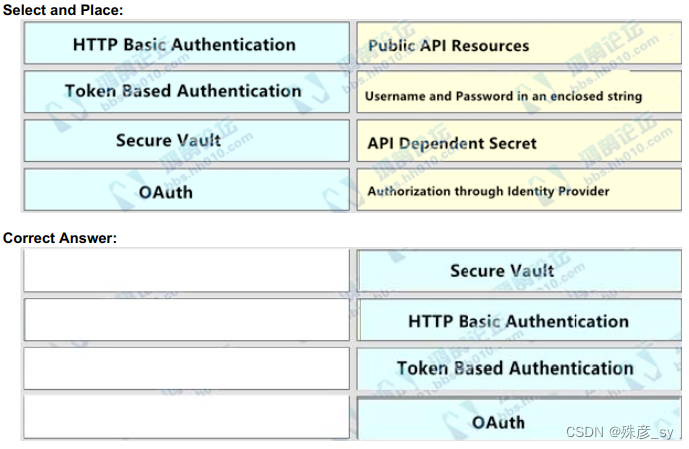
148、Drag and drop the REST API authentication method from the left to the description on the right.
149、Which two security features are available when implementing NTP? (Choose two.)
A. symmetric server passwords
B. dock offset authentication
C. broadcast association mode
D. encrypted authentication mechanism
E. access list-based restriction scheme
150、What is calculated using the numerical values of the transmitter power level, cable loss, and antenna gain?
A. EIRP
B. dBi
C. RSSI
D. SNR
相关文章:

CCNP350-401学习笔记(101-150题)
101、Refer to the exhibit SwitchC connects HR and Sales to the Core switch However, business needs require that no traffic from the Finance VLAN traverse this switch. Which command meets this requirement? A. SwitchC(config)#vtp pruning B. SwitchC(config)#…...

分享112个HTML娱乐休闲模板,总有一款适合您
分享112个HTML娱乐休闲模板,总有一款适合您 112个HTML娱乐休闲模板下载链接:https://pan.baidu.com/s/15uBy1SVSckPPMM55fiudeQ?pwdkqfz 提取码:kqfz Python采集代码下载链接:采集代码.zip - 蓝奏云 Bootstrap视频网站模板 …...
k8s快速入门
文章目录一、Kubernetes(K8S)简介1、概念1.1 Kubernetes (K8S) 是什么1.2 核心特性1.3 部署方案2、Kubernetes 集群架构2.1 架构2.2 重要概念 Pod2.3 Kubernetes 组件二、Kubernetes集群安装1、安装方式介绍2、minikubute安装3、裸机搭建(Bar…...

NG ZORRO知识点总结
NG ZORRO的常用属性,包括但不限于,结合代码 <button nz-button [nzType]"primary" [nzSize]"large" [nzLoading]"loading" [nzDisabled]"disabled" (click)"onClick()">点击我</button>nz-button是一个按钮组件…...

go中的值方法和指针方法
go中的值方法和指针方法1前言2 不同类型的对象调用不同类型的方法2.1 值对象可以调用值方法和指针方法3 指针对象可以调用值方法和指针方法4 !注意:结构体对象实现接口方法1前言 golang中在给结构体对象添加方法时,接收者参数类型可以有两种…...

OKR常见挑战以及应对方法探讨
背景 OKR是大家经常听到的一个词,也有不少团队说自己实行过,但每个实行过的团队都遇到过挑战。很多团队都感觉OKR有些空,很难落地,普通团队成员更是时常感觉无所适从,感觉就像看电影。2022年我们在更大的范围落地了OK…...
SpringAMQP消息队列(SpringBoot集成RabbitMQ)
一、初始配置1、导入maven坐标<!--rabbitmq--><dependency><groupId>org.springframework.boot</groupId><artifactId>spring-boot-starter-amqp</artifactId></dependency>2、yml配置spring:rabbitmq:host: 你的rabbitmq的ipport: …...
DIDL5_数值稳定性和模型初始化
数值稳定性和模型初始化数值稳定性梯度不稳定的影响推导什么是梯度消失?什么是梯度爆炸?如何解决数值不稳定问题?——参数初始化参数初始化的几种方法默认初始化Xavier初始化小结当神经网络变得很深的时候,数值特别容易不稳定。我…...

火狐浏览器推拽开新的窗口
今天我测试的时候,发现我拖拽一下火狐会打开了新的窗口,谷歌就不会,所以我们要阻止一下默认行为const disableFirefoxDefaultDrop () > {const isFirefox navigator.userAgent.toLowerCase().indexOf(firefox) ! -1if (isFirefox) {docu…...

vrrp+mstp+osfp经典部署案例
LSW1和LSW2和LSW3和LSW4上面启用vrrpmstp组网: vlan 10 全走LSW1出再走AR2到外网,vlan 20 全走LSW2出再走AR3到外网 配置注意:mstp实例的根桥在哪,vrrp的主设备就是谁 ar2和ar3上开nat ar2和ar3可以考虑换成两台防火墙来做&…...
AI_News周刊:第二期
2023.02.13—2023.02.17 1.ChatGPT 登上TIME时代周刊封面 这一转变标志着自社交媒体以来最重要的技术突破。近几个月来,好奇、震惊的公众如饥似渴地采用了生成式人工智能工具,这要归功于诸如 ChatGPT 之类的程序,它对几乎任何查询做出连贯&a…...

【C++的OpenCV】第一课-opencv的间接和安装(Linux环境下)
第一课-目录一、基本介绍1.1 官网1.2 git源码1.3 介绍二、OpenCV的相关部署工作2.1 Linux平台下部署OpenCV一、基本介绍 1.1 官网 opencv官网 注意:官网为英文版本,可以使用浏览器自带的翻译插件进行翻译,真心不推荐大家去看别人翻译的&am…...

为什么建议使用你 LocalDateTime ,而不是 Date
为什么建议使用你 LocalDateTime ,而不是 Date? 在项目开发过程中经常遇到时间处理,但是你真的用对了吗,理解阿里巴巴开发手册中禁用static修饰SimpleDateFormat吗 通过阅读本篇文章你将了解到: 为什么需要LocalDate…...
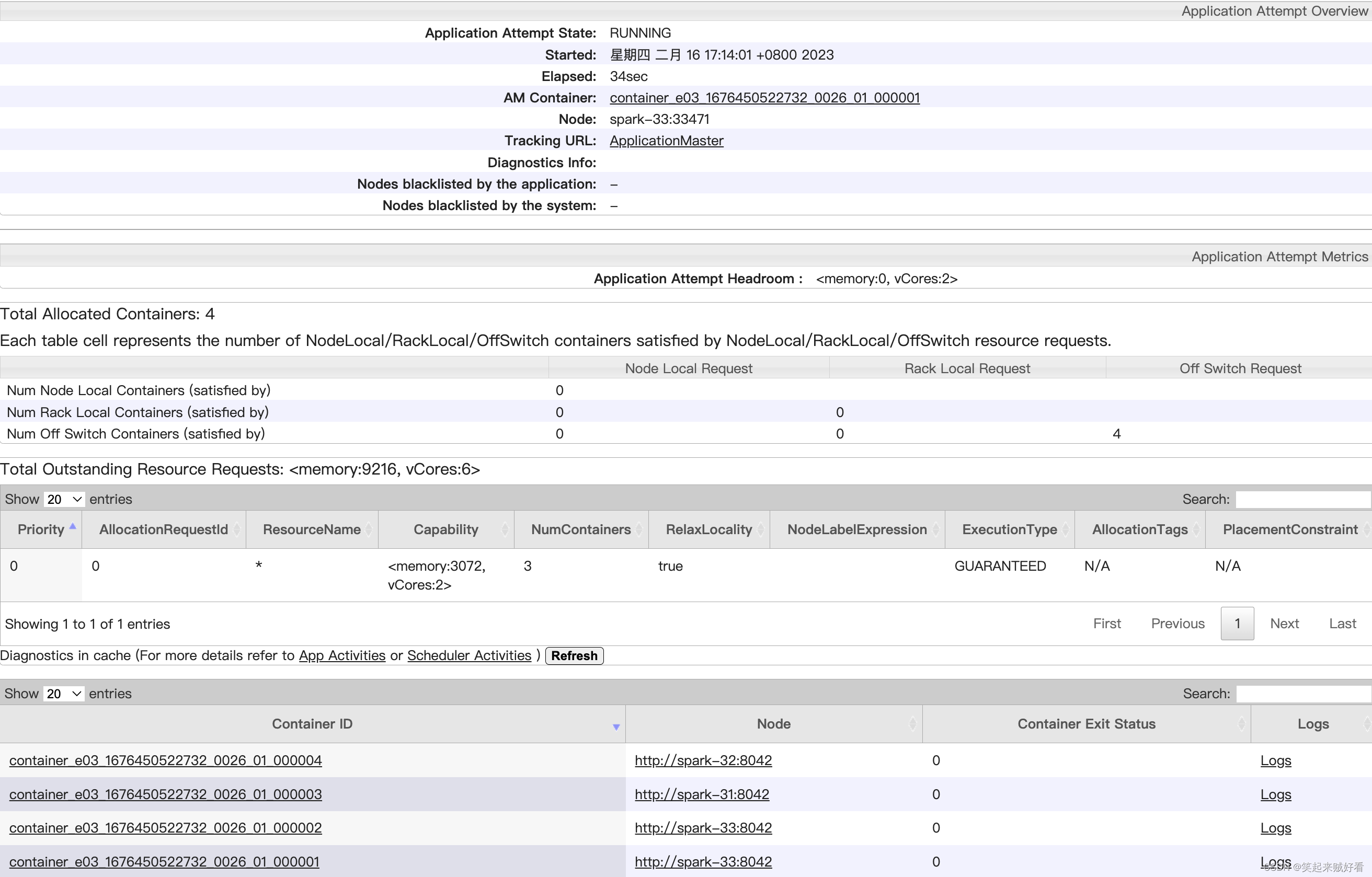
【大数据】HADOOP-YARN容量调度器Spark作业实战
目录需求配置多队列的容量调度器验证队列资源需求 default 队列占总内存的40%,最大资源容量占总资源的60% ops 队列占总内存的60%,最大资源容量占总资源的80% 配置多队列的容量调度器 在yarn-site.xml里面配置使用容量调度器 <!-- 使用容量调度器…...

平面及其方程
一、曲面和交线的定义 空间解析几何中,任何曲面或曲线都看作点的几何轨迹。在这样的意义下,如果曲面SSS与三元方程: F(x,y,z)0(1)F(x,y,z)0\tag{1} F(x,y,z)0(1) 有下述关系: 曲面 SSS 上任一点的坐标都满足方程(1)(1)(1)不在曲…...

7 配置的封装
概述 IPC设备通常有三种配置信息:一是默认配置,存储了设备所有配置项的默认值,默认配置是只读的,不能修改;二是用户配置,存储了用户修改过的所有配置项;三是私有配置,存储了程序内部使用的一些配置项,比如:固件升级的URL、固件升级标志位等。恢复出厂设置的操作,实际…...

03_Docker 入门
03_Docker 入门 文章目录03_Docker 入门3.1 确保 Docker 已经就绪3.2 运行我们的第一个容器3.3 使用第一个容器3.4 容器命名3.5 重新启动已经停止的容器3.6 附着到容器上3.7 创建守护式容器3.8 容器内部都在干些什么3.9 Docker 日志驱动3.10 查看容器内的进程3.11 Docker 统计信…...

Python 为什么要 if __name__ == “__main__“:
各位读者,你们知道以下两个Python文件有什么区别吗? main1.py def main():output Helloprint(output)if __name__ "__main__":main()main2.py output Hello print(output)当我们直接运行 main1.py 与 main2.py 的时候,程序都…...
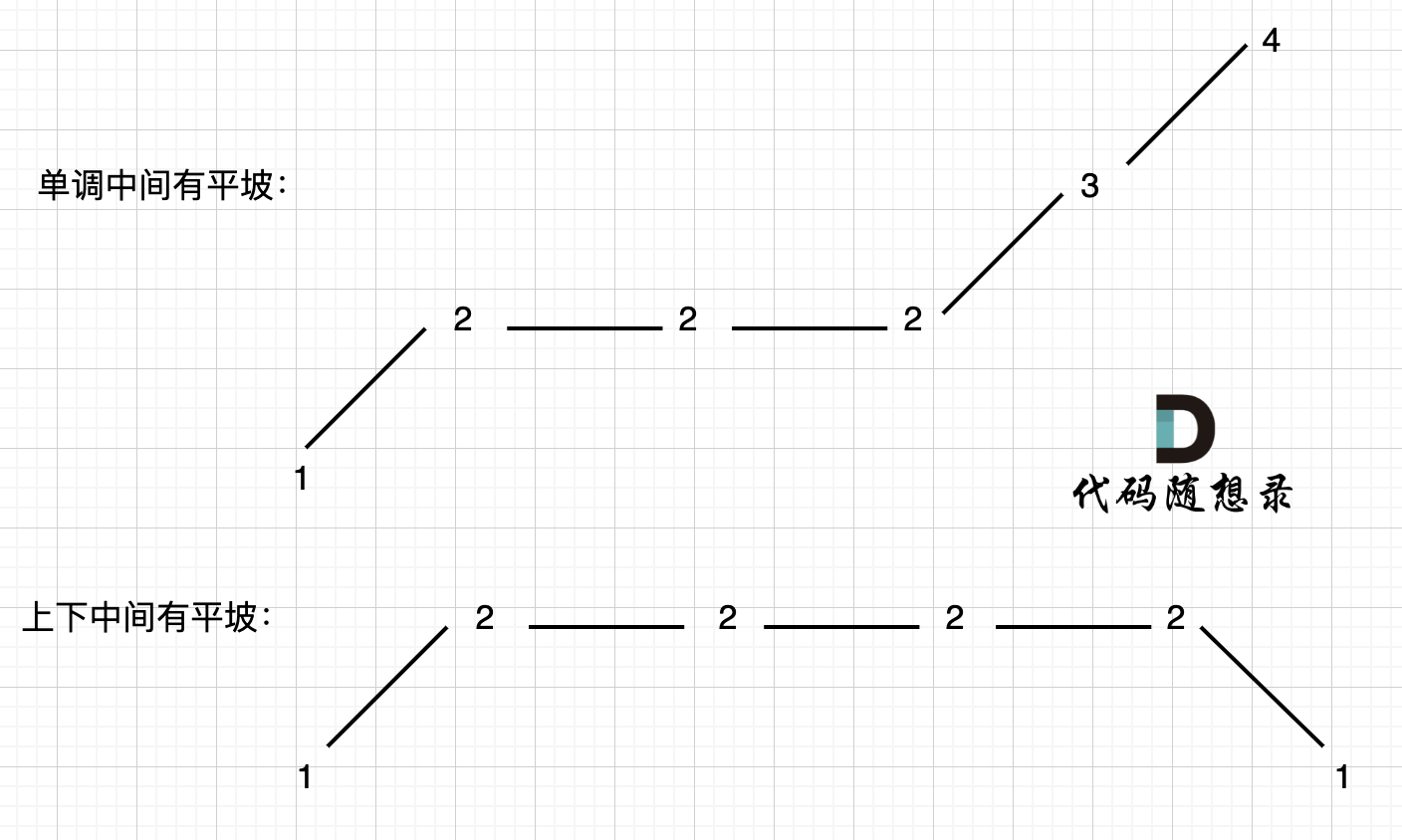
455. 分发饼干、376. 摆动序列、53. 最大子数组和
455.分发饼干 题目描述: 假设你是一位很棒的家长,想要给你的孩子们一些小饼干。但是,每个孩子最多只能给一块饼干。 对每个孩子 i,都有一个胃口值 g[i],这是能让孩子们满足胃口的饼干的最小尺寸;并且每块…...
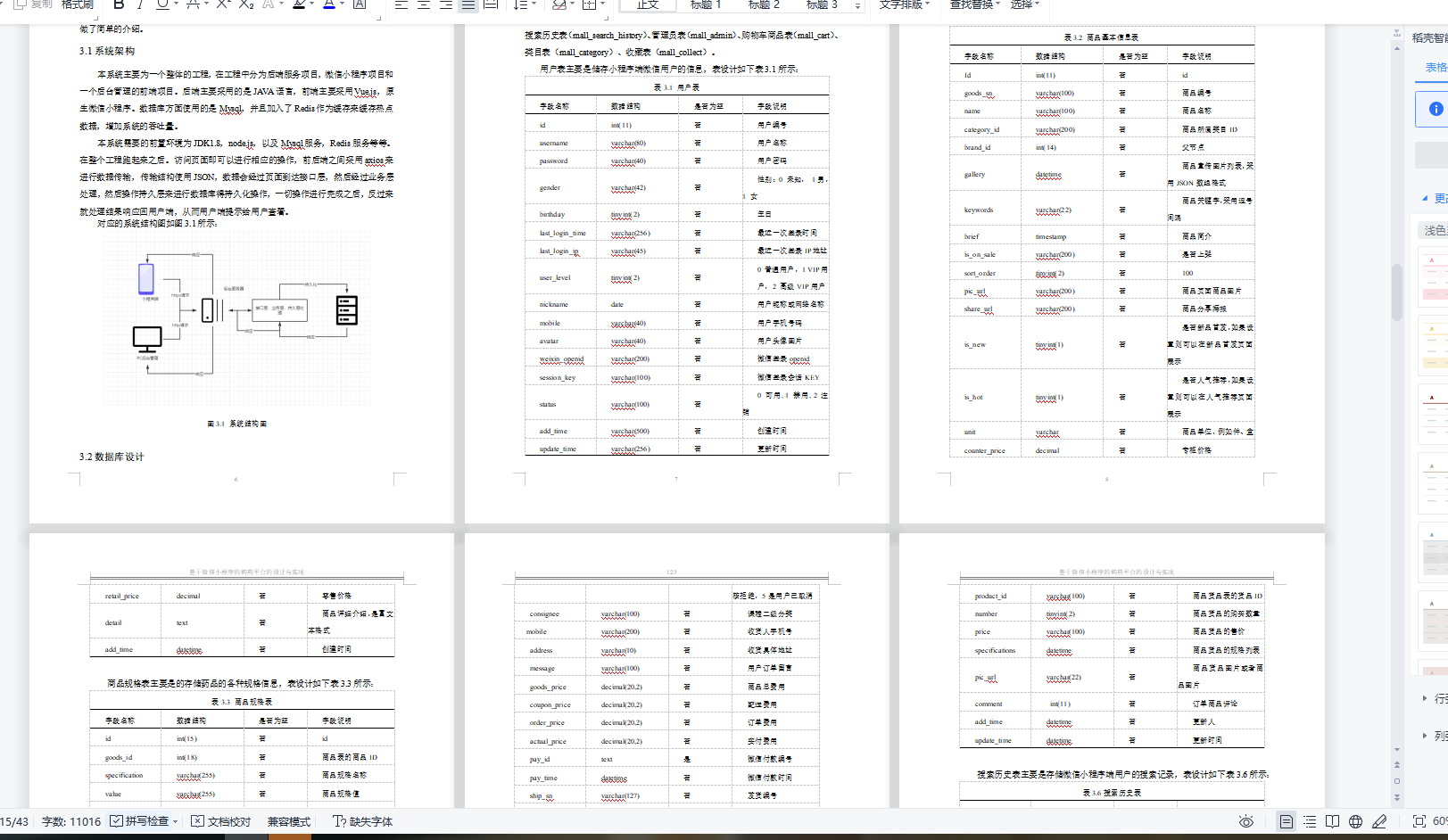
基于Springbot+微信小程序的购药平台的设计与实现
基于Springbot微信小程序的购药平台的设计与实现 ✌全网粉丝20W,csdn特邀作者、博客专家、CSDN新星计划导师、java领域优质创作者,博客之星、掘金/华为云/阿里云/InfoQ等平台优质作者、专注于Java技术领域和毕业项目实战✌ 🍅文末获取项目下载方式🍅 一、…...
网络编程(Modbus进阶)
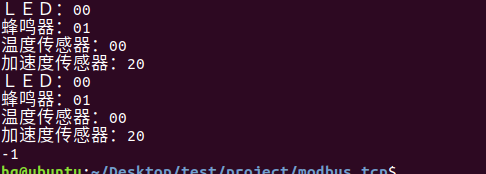
思维导图 Modbus RTU(先学一点理论) 概念 Modbus RTU 是工业自动化领域 最广泛应用的串行通信协议,由 Modicon 公司(现施耐德电气)于 1979 年推出。它以 高效率、强健性、易实现的特点成为工业控制系统的通信标准。 包…...
【Python】 -- 趣味代码 - 小恐龙游戏
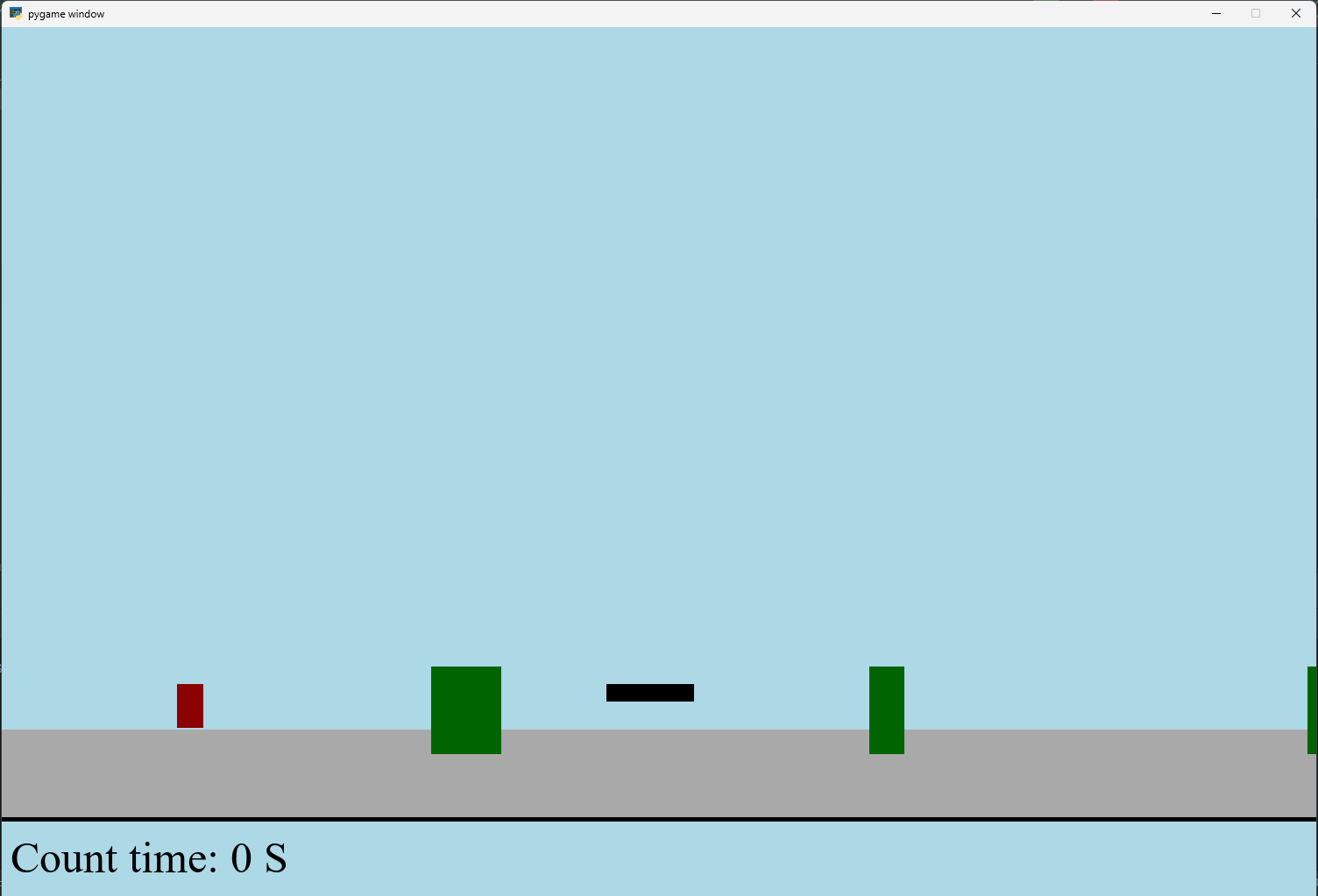
文章目录 文章目录 00 小恐龙游戏程序设计框架代码结构和功能游戏流程总结01 小恐龙游戏程序设计02 百度网盘地址00 小恐龙游戏程序设计框架 这段代码是一个基于 Pygame 的简易跑酷游戏的完整实现,玩家控制一个角色(龙)躲避障碍物(仙人掌和乌鸦)。以下是代码的详细介绍:…...
)
rknn优化教程(二)
文章目录 1. 前述2. 三方库的封装2.1 xrepo中的库2.2 xrepo之外的库2.2.1 opencv2.2.2 rknnrt2.2.3 spdlog 3. rknn_engine库 1. 前述 OK,开始写第二篇的内容了。这篇博客主要能写一下: 如何给一些三方库按照xmake方式进行封装,供调用如何按…...

蓝桥杯 2024 15届国赛 A组 儿童节快乐
P10576 [蓝桥杯 2024 国 A] 儿童节快乐 题目描述 五彩斑斓的气球在蓝天下悠然飘荡,轻快的音乐在耳边持续回荡,小朋友们手牵着手一同畅快欢笑。在这样一片安乐祥和的氛围下,六一来了。 今天是六一儿童节,小蓝老师为了让大家在节…...

江苏艾立泰跨国资源接力:废料变黄金的绿色供应链革命
在华东塑料包装行业面临限塑令深度调整的背景下,江苏艾立泰以一场跨国资源接力的创新实践,重新定义了绿色供应链的边界。 跨国回收网络:废料变黄金的全球棋局 艾立泰在欧洲、东南亚建立再生塑料回收点,将海外废弃包装箱通过标准…...

【碎碎念】宝可梦 Mesh GO : 基于MESH网络的口袋妖怪 宝可梦GO游戏自组网系统
目录 游戏说明《宝可梦 Mesh GO》 —— 局域宝可梦探索Pokmon GO 类游戏核心理念应用场景Mesh 特性 宝可梦玩法融合设计游戏构想要素1. 地图探索(基于物理空间 广播范围)2. 野生宝可梦生成与广播3. 对战系统4. 道具与通信5. 延伸玩法 安全性设计 技术选…...

今日学习:Spring线程池|并发修改异常|链路丢失|登录续期|VIP过期策略|数值类缓存
文章目录 优雅版线程池ThreadPoolTaskExecutor和ThreadPoolTaskExecutor的装饰器并发修改异常并发修改异常简介实现机制设计原因及意义 使用线程池造成的链路丢失问题线程池导致的链路丢失问题发生原因 常见解决方法更好的解决方法设计精妙之处 登录续期登录续期常见实现方式特…...
LLMs 系列实操科普(1)
写在前面: 本期内容我们继续 Andrej Karpathy 的《How I use LLMs》讲座内容,原视频时长 ~130 分钟,以实操演示主流的一些 LLMs 的使用,由于涉及到实操,实际上并不适合以文字整理,但还是决定尽量整理一份笔…...

NPOI Excel用OLE对象的形式插入文件附件以及插入图片
static void Main(string[] args) {XlsWithObjData();Console.WriteLine("输出完成"); }static void XlsWithObjData() {// 创建工作簿和单元格,只有HSSFWorkbook,XSSFWorkbook不可以HSSFWorkbook workbook new HSSFWorkbook();HSSFSheet sheet (HSSFSheet)workboo…...
FFmpeg:Windows系统小白安装及其使用
一、安装 1.访问官网 Download FFmpeg 2.点击版本目录 3.选择版本点击安装 注意这里选择的是【release buids】,注意左上角标题 例如我安装在目录 F:\FFmpeg 4.解压 5.添加环境变量 把你解压后的bin目录(即exe所在文件夹)加入系统变量…...
